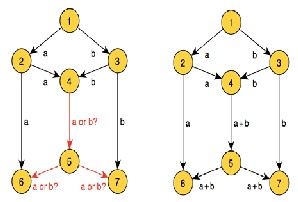
Figure1: The Buttery Network.
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 128
ISSN 2229-5518
The impact of different MAC protocols for
Network Coding in Adhoc Network
Ibrahim Khider,Khalid Hamid and Hoyda Elwaseelar
Abstract— Network coding has been shown to be an effective way to achieve the maximum flow capacity of network. In this paper the study performance of network coding using different types of MAC leads to gathering different results and comparing them with respect to performance. The results revealed malfunctioning current of realistic MAC layer .The study showed that this methodology might be the promising solution to gradually eliminate the variety of drawbacks of the system as a whole.
Index Terms— Network Coding, Adhoc Network, MAC protocols, Simulation
—————————— ——————————
Network coding is a hot research topic that may have in-
teresting applications in practical networking systems. With
network coding, intermediate nodes may send out packets that are linear combinations of previously received infor- mation.The concept of network coding was first introduced by R. W. Yeung and Z. Zhang in2000 [1] as an alternative to rout- ing. In a traditional packet-switched network, data flows is defined, discrete "pieces" from the source to the destination at the transmitting station, the outgoing message is broken into packets, each of which contains some of the message data in- tact. The packets do not necessarily all travel along the same route but they all eventually arrive at the same destination, where the receiving computer reassembles them into the orig- inal message. The main problem with this method is that when the overall network traffic volume is high, resulting in long delays. Packets tend to bunch up at certain nodes, some- times in excess of the nodes' ability to process them. Other routes and nodes may remain under-utilized.
In network coding, routers and switches are replaced
by devices called coders. Instead of directing the packets to- ward their ultimate destination, the coders transmit metadata in the form of digital evidence about the message along multi- ple paths simultaneously. Conversely, the metadata arriving from two or more sources may be combined into a single packet. This distribution method can increase the effective capacity of a network. The improvement is most pronounced
when network traffic volume is near the maximum capacity
obtainable with traditional routing. When a receiver has enough digital evidence, it can compute the intended mes- sage/packet. Even if some packets on some of the routes are lost or mutilated, the original message gets through if the re- ceived digital evidence is sufficient. In network coding, the data does not depend only on one transmitted message but also on the contents of other messages that happen to be shar- ing the route at the time of transmission. For this reason, net- work coding is more resistant to hacking, eavesdropping and other forms of attack than traditional data transmission. The extent of throughput improvement that network coding can provide depends on the network topology and on the fre- quency and severity of bottlenecks. In no event does network coding reduce the throughput compared with the routing method. [2]The basic idea behind network coding is illustrated in Figure below. Suppose that node 1 aims at sending bits (a and b) simultaneously (i.e. multicast) to sinks 6 and 7. It is not difficult to see that the link between nodes 4 and 5 results in a bottleneck in the sense that either bit a is forwarded (in which case node 6 does not receive bit b), or bit b is sent (in which case node 7 will receive incomplete information). It follows that although the capacity of the network is 2 bits per trans- mission (because the min-cut to each destination equals 2), this capacity cannot be achieved unless node 4 jointly encodes a and b, for example, through an XOR operation that allows perfect recovery at the sinks.[3] As shown in figure 1
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 129
ISSN 2229-5518

Figure1: The Buttery Network.
Wireless multiple accesses can be categorized into random access (e.g., CSMA and CSMA with Collision Detection [CSMA/CD]) and controlled access (e.g., TDMA and token- based schemes). Random access will be suitable for ad hoc networks because of lack of infrastructure support. In addi- tion, the IEEE 802.11 (WLAN) committee as the basis for its standards selected the CSMA/CA scheme. The use of IEEE
802.11 is not optimized in a multi hop environment. These
technologies are used for single-hop WLANs. The design of MAC protocols for a multi hop ad hoc environment is a hot research issue [4]. There are four different MAC protocols based on CSMA:
. the basic access provided by IEEE 802.11b which, in the broadcast case, does not use any acknowledgment mecha- nism. As a consequence, in case of a collision, no retransmis- sion occurs and the packet is lost, resulting in high inefficiency and low packet delivery ratio.
————————————————
• Khalid hamid was born 1967.He got PhD in communication engineering. Work at University of science and Technology, sudan . E-mail: drkhalidbilal@hotmail.com
• Hoyda elwaseela,MSc holder ,work atGarden City college,sudan
. This scheme is an improvement of the basic IEEE
802.11b, where an acknowledgment mechanism is implement- ed. According to the idea proposed in [6], a given node first broadcasts a packet to its neighbors, by randomly picking one of them and including its address in the packet header. Only the node whose address matches the one contained in the header sends an acknowledgment to the sending device. This is done according to the basic IEEE 802.11b unicast communi- cation (no RTS/CTS). All other neighbors overhear/decode the transmission but do not respond to the sending node. The packet is retransmitted in case there is no acknowledgment. Note that, using this mechanism, only collisions at the ad- dressed receiver can be detected, while collisions occurring at any of the remaining neighbors are ignored. Also, this strategy does not solve the hidden node problem.
. This scheme Improve the packet delivery ratio with ad- ditional RTS/CTS handshake. These control messages are in- troduced to alleviate the hidden node problem. The CTS is only transmitted by the node addressed in the packet header. The delay introduced by this technique is expected to be high- er, due to the additional control packets. Moreover, as for the previous schemes, it can not detect collisions at all overhearing nodes.
• With the term ideal MAC refer to a very simple mechanism where transmitted packets are only affected by the transmis- sion delay. a node sends a packet, all its neighbors success- fully receive the message after a (fixed) transmission delay. The transmission delay is computed using the same rate and packet size of the above MAC protocols. This scheme, which is not feasible in practice [7]
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 130
ISSN 2229-5518
We start our investigation with wireless ad hoc in circular network topology each node has exactly two neighbors as shown in figure.2. We consider four different MAC protocols in the simulation IEEE 802.11b, IEEE 802.11b with pseudo broadcast, IEEE 802.11 with pseudo broadcast and RTS/CTS handshaking and Ideal MAC.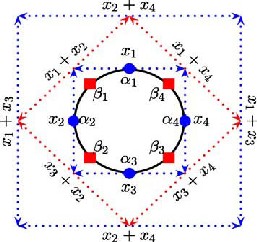
Figure2: Circular Network topology
We applied different types of Mac protocols used S=1 in
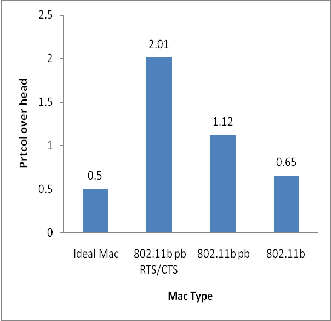
circular topology and collected data during simulation time and results was plotted .Referring figure. 3 it had been noted that IEEE 802.11b achieves ��� ≈ 0.73, whereas an ideal MAC achieves ��� ≈ 0.91, which corre- sponds to a decrease in performance of about 18%. Note that an ideal MAC does not provide full reliability as it still schedules transmissions according to CSMA and does not use. Also The MAC pseudo broadcast (IEEE 802.11 pb and pseudo broadcast with RTS/CTS (IEEE 802.11 pb RTS/CTS) is also improvement PDR ≈ 16 %due to effec- tive in decreasing the number of collisions. The observed decrease in performance is due to the use of an actual MAC layer IEEE 802.11b.From figure5 the Mac IEEE
802.11 with pseudo broadcast and RTS/CTS handshake improve but also increase the overhead. This is due to the
MAC retransmissions in case of collisions and to the con-
trol traffic (i.e., ACK, RTS and CTS packets). Figure 4 de- picted the increase of delay. Hence collision avoidance policies gave little improvement in terms of, while leading to poor overhead and delay performance.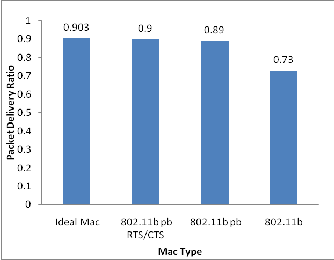
Figure.3,Packet Delivery Ratio: Performance for Different
MAC 802.11 protocol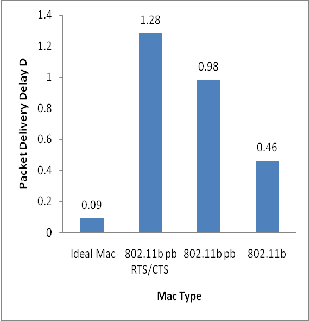
Figure 4,Packet Delivery Delay: Performance for Differ- ent MAC 802.11 Protocol
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 131
ISSN 2229-5518
[4] Sarkar, S. K. et al.;.Ad Hoc Mobile Wireless Networks Principles, Protocols, and Applications,2008.
[5] S. Katti, H. Rahul, W. Hu, D. Katabi, M. Médard and J. Crowcroft,
,XORs in the Air: Practical Wireless Network Coding, IEEE/ACM
Transactions on Networking, pages 497-510,.2008.
[6] V. Bhargava and S. Wicker,.Reed-Solomon Codes and Their Applica- tions, IEEE Press, ISBN 0-7803-5391-9, 1994.
[7] E. Fasolo, M. Rossi, J. Widmer, and M. Zorzi, ,On MAC scheduling
and packet combination strategies for random network coding, in
Proc. IEEE ICC, Glasgow, UK, , pp. 3582–3589,2007.
Figure.5, Protocol Overhead: Performance for Different
MAC 802.11 Protocol
5 We used a broadcasting schemes based on network cod- ing for wireless ad hoc networks. Through simulation analysis, Firstly discussed the impact of different MAC protocols under circular network topology through the network simulator ns-2.This shows with comparison of the techniques the realistic Mac protocol is low PDR.There are many potentially interesting network settings to be in- vestigated in the future.The work that has been covered so far was within what the time allotted to this work permit- ted. No doubt, that father work in this area can be rec- ommended. However, it is has been noted the NS2 is a cumbersome procedure. It is strongly recommended that an alternative tool is to be considered for future practicing
[1] R. Ahlswede, N. Cai, S.-Y. R. Li,R. W. Yeung, ,Network information flow, IEEE Trans. Information Theory, IT- 46(4):1204-1216,july 2000
[2] http://searchnetworking.techtarget.com/definition/networkcoding[
Accessed 9July 2011]
[3] Diogo Ferreira, Lu´ısa Lima, Jo˜ao Barros .NECO: NEtwork COding
simulator.pp.1-3,2005
IJSER © 2013 http://www.ijser.org