International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 265
ISSN 2229-5518
Securing patient data in the cloud using Attribute
Based Encryption
Chiedza Hwata, R.Subburaj Professor, Gladman Jekese
Abstract — Cloud computing has attracted attention worldwide in all industries, including the medical field leading to the rise of electronic healthcare systems. Although it has brought about an improvement in the provision of healthcare in terms of information management, it also poses a lot of security and privacy concerns to the patients. This is due to the fact that personal and highly sensitive data is outsourced to a third party (Cloud Service Provider) for processing and storage. This paper seeks to improve security of cloud-based patient data in healthcare organizations by employing a Ciphertext Policy Attribute Based Encryption (CP-ABE) scheme. The proposed scheme provides data confidentiality and allows the patient to control who accesses her personal health data by encrypting it under a specified access policy alongside with her key. It also provides collusion-resistance, flexible and immediate revocation of users who are no longer allowed to access a patient’s data.
Index Terms— cloud computing, electronic healthcare, security, encryption, revocation, privacy, attribute based encryption
—————————— ——————————
lot of healthcare organizations are on the move to adopt electronic healthcare systems, the case for cloud data storage which is compelling for deploying
Electronic Healthcare systems: not only is it inexpensive but it also provides the flexible, wide-area mobile access that is increasingly needed in the modern world. It has become essential to support individual process activities and to satisfy collaboration and coordination needs by providing ready access to patient and operational information regardless of location and time. Filling this information gap by enabling the provision of the right information, to the right people, at the right time fosters new challenges, including the specification of a common information format, the interoperability among heterogeneous institutional information systems or the development of new, ubiquitous trans-institutional systems [1]. In the cloud, computing resources including storage is provided by a third party service provider [2] and [3].
With healthcare providers looking at automating processes of health information manipulation at lower cost and higher gains, cloud computing has been viewed as an appropriate platform to deploy standard medical information systems for its scalable and cost-effective services delivered by cloud service providers [4], [5]. Despite the increased usage of cloud- based data sharing platforms, the privacy and security related problems have prevented their adoption in the healthcare domain [6],[ 7].
————————————————
• Chiedza Hwata is an M.Tech student in Information Technology at SRM University, Chennai, India, E-mail: chiedza11@gmail.com
• Dr. R Subburaj is a Professor and Consultant in the Department of
Information Technology at SRM University, Chennai., India. E- mail: subburaj.spr@gmail.com
• Gladman Jekese is an M.Tech student in Information Technology at SRM University, Chennai, India, E-mail: jgman86@gmail.com
Lately there has been a high rate of cloud-based healthcare systems deployment yet a lot of patients’ health information has continually leaked in the past years [8]. Considering sensitivity of health data, patients start to worry because they realize that they would completely lose control over their personal information once it enters the cyberspace. On the other hand, the healthcare organizations also become skeptical of the security offered by Cloud Service providers.
There are good reasons to be cautious in keeping medical data private and limiting the access because some employer may decide not to hire someone with a certain disease [9]. The proposed secure patient healthcare system is inspired by the need for revocation flexibility, fine-grained access control, and cost efficiency of the cloud-based patient data outsourcing paradigm. The Ciphertext Policy Attribute Based Encryption variation, proposed in this paper allows revocation of users who are no longer entitled to access patient data due to various reasons for example a medical doctor who has been let go by the health organization. It also allows a patient to selectively revoke a physician based on attributes, such that they can continue to access some less sensitive data after revocation. CP-ABE has been said to have the key escrow problem as described in [10], [11], the system proposed in this paper is collusion resistant by using a minimally trusted party for storage provision and computations.
The rest of the paper is organized as follows; Section 2 discusses the background, section 3 presents the proposed system, section 4 outlines the preliminaries of this design while section 5 defines the system design and finally 6 concludes the study.
Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 266
ISSN 2229-5518
provisioned and released with minimal management effort or service provider interaction [12]. It conveys all resources and services as a service over the internet based on user demand with the adoption of public cloud services, a large part of the network, system, applications, and data will move under third-party provider control [13]. In the healthcare environment it may just be outsourcing storage, i.e. databases. Since these databases are often filled with valuable data, they are high value targets for attackers and security breaches in such systems are not uncommon, especially by insiders. In addition, organizations with access to extremely sensitive data might not want to give an outside server any access to their information at all [14]. Also cloud data typically resides in a shared environment, users will neither know the exact location of their data nor the other sources of the data collectively stored with theirs [6], [7] and [15]. Therefore, in this Internet-based computing paradigm, users are universally required to accept the underlying premise of trust [5] and [7]. However, when considering standards such as HIPAA (Health Insurance Portability and Accountability in Act) [16], it is crucial for health-related data to be kept confidential from anyone unless authorized by the patient or some emergency regulations.
The Cloud is generally susceptible to many privacy and security attacks. [17], discusses some of the legal and ethical issues that ought to be followed in Medical health data handling, together with consequences of breaches. As a result, many hospitals and health organizations are reluctant to adopt Cloud technology as a privacy breach in regards to its patient information can be devastating, especially in terms of cost [18]. This has led to researches and publications of the possible attacks and a number of solutions have been proposed. Cloud Security Alliance describes some of the top threats that are associated with adopting cloud computing [19]. Some of the threats include; Abuse and nefarious use of cloud computing, Insecure interfaces and APIs, Malicious insiders, Shared technology issues, Data loss or leakage, Account or service hijacking and Unknown risk profile. Some service providers may not provide a clear Service Level Agreement, which provides services at different levels [20], [21]. For health organizations it is very crucial to provide privacy and confidentiality since it involves personal information which is sensitive when revealed. An employer may decide not to hire someone with certain diseases. An insurance company may refuse to provide life insurance knowing the disease history of a patient. In healthcare, data leaks risk patients’ health as well as their identity [22]. Some other problems with cloud data are associated with access control [23]. Due to the fact that the data can be accessed from anywhere at any time, it is of utmost importance that the level of access be monitored because not everyone will have the right intentions always. In cases where data is protected from the outside world, even the insiders need to be controlled. Imagine a situation where situation where a dentist can easily retrieve HIV and AIDS patient’s data, they can publish it without much suspicion. Or a case where a heart surgeon that has been let go, they may still try to access patient data that they were able to retrieve when they were still employed
there. They may also try to access data that was added after their access was revoked, whether encrypted or not. Users, out curiosity or with a malicious intend can collude with a trusted party or some other users that are compromised in the system so that they can access information that they are not privileged for.
There have been numerous publications in relation to security and privacy of cloud-assisted healthcare dating back to Medical Information Privacy Assurance (MIPA) [24]. MIPA was one of the early works done in electronic health which pointed out the importance and unique challenges of medical information privacy, and the devastating privacy breach facts that resulted from insufficient supporting technology and implemented a system that allows users to protect their data. Since then, a number of asymmetric schemes have been put to use including Public-key cryptography, that uses a pair of keys for encryption where a private key is kept secret and a public key is widely distributed. If Alice wants to send a confidential message to Bob, she can encrypt the message with the public key of Bob and only Bob can decrypt the message using his private key. The problem in Public-Key Infrastructure (PKI) is that a public key must be obtained from, or at least be certified by the Trusted Third Party (TTP) of the PKI. As an improvement to PKI, Identity-Based Encryption (IBE), with its variations, was introduced. In IBE any string can be used to generate a public key without involving the TTP, thus creating a degree of flexibility. It basically allows any pair of users to communicate securely without exchanging any key (public or private) but based on the recipient’s identity is used to encrypt the message. However if Alice does not fully know Bob’s identity, except for his few attributes, then neither a PKI nor IBE will work. Sahai and Waters [25] introduced Attribute-Based Encryption (ABE) as a means for encrypted access control. Later on, a fine- grained access control ABE scheme propose by Goyal et al. [26] and Bethencourt et al. [27] further enhanced ABE practicality. Two categories of attribute-based encryption are distinguished in [28], where Key-Policy Attributed-Based Encryption (KP-ABE) , a ciphertext is associated with a set of attributes while a private key is issued as per a certain access control policy while Ciphertext-Policy Attribute-Based Encryption (CP-ABE) a ciphertext is generated according to some access control policies while private keys are issued in association with attributes. A secure and privacy preserving opportunistic computing framework termed CAM is proposed in [29]. The paper discusses about attribute-based access control and a new privacy preserving scalar product computation (PPSPC) technique. CAM promotes a user-centric access control by allowing each medical user to decide who can participate in the opportunistic computing, among the qualified helpers but its security model does not consider the possible side-channel attack due to the co-residency on shared resources either because it could be mitigated with either system level protection or leakage resilient cryptography.
In [30], a solution for patient data collection, which delivers an integrated telemedicine service that, automates the process
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 267
ISSN 2229-5518
from data collecting to information deliver as a computing utility is developed. Sun et.al studied a Privacy-preserving health data storage system, where patients would have to encrypt their personal health data and get it stored it on a third-party server [31]. Tu and Niu [32] make use of CP-ABE in the context of enterprise applications and developed a revocation mechanism that simultaneously allows high adaptability, fine-grained access control and revocation. When a user is revoked access rights, the data is reencrypted in the Cloud rendering the revoked user’s key useless. Even though, the re-encryption process is delegated to the Cloud, this is not efficient when considering very large data sizes. In [11], a scheme to do away with the key escrow problem that is found in CP-ABE was proposed, where two parties would be assigned the role to issue keys so that not one authority will get access to all the sensitive data. In [33], [34], [35], revocation schemes are proposed and proved to be efficient but required re-encryption of ciphertexts, which is computationally expensive. A proposal is made in [36], with fine-grained access control and flexible revocation scheme in MSNs. That CP-ABE scheme with revocation defined for MSNs is proposed healthcare environment in this paper.
To achieve a fine-grained access control, data confidentiality, flexible and immediate revocation, the proposed system will employ the concept of ciphertext-policy attribute-based encryption (CP-ABE) as a basis for the encryption construction. In the CP-ABE scheme, a ciphertext is encrypted with an access policy chosen by an encryptor and a corresponding decryption key is created with respect to a set of attributes. As long as the set of attributes associated with a decryption key satisfies the access policy associated with a given ciphertext, the key can be used to decrypt the ciphertext. Due to the fact that patient health data consists of private and personal data, an access structure is defined first before a patient can share their information in the system. Therefore, based on the credentials assigned to each professional, they will be allowed access to patient information. For example anyone with the credentials of a medical doctor will be allowed to view a patient’s medical history, past medications, family history and patient’s diseases. On the other hand a pharmacist may just need to be allowed to view a patient’s prescription because that is sufficient for him to provide the patient with the required medication.
The patient initializes the system, generates a master key for the patient and sends the public key to the other physicians who are meant to access patient data. Prior to storing their data on the cloud, a patient will encrypt their data, alongside the defined access structure. For the purpose of user revocation, she creates the revocation list, generates the corresponding revocation keys, and sends them to the service provider who will help her enforce access policy using these revocation keys. Whenever a physician wants to access the patient data, he first sends his transformation key to the service provider, which is part of his private key. Unless his
private key has been regenerated, the physician only sends it once. The provider checks the revocation key, if the physician is not on the revocation list, transforms the encrypted data CT
to 𝐶𝐶 ′, and transfers it to the physician, provided his attribute
set S satisfies the access structure A. Receiving the
transformed ciphertext CT’, the physician can efficiently
retrieve the plaintext using his secret value γ by executing
only one exponent operation.
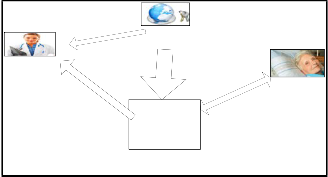
There are four parties involved in this scheme: the Cloud Service Provider (or simply the cloud), the patient (data owner), physician (includes doctors and all the related medical staff), and a trusted authority (TA). In this paper an attempt is made to utilize the CP-ABE scheme in [36], making use of these four entities;
Cloud Service Provider (CSP): It is a minimally trusted entity which is responsible for storing patients’ (encrypted) data in a database and performing searches for the physicians. It is basically a third-party service provider that offers the on- demand storage and computing services for the health organization. The CSP is not fully trusted by users in the domain, in this paper we assume that the service provider is honest-but-curious; that is, it will try to find out as much secret information from the outsourced data as possible, but it will honestly execute the tasks assigned to it by legitimate parties in the system.
Patient: This entity is the person who is being treated at the health organization, who wishes to securely store and share her private data with her doctors selectively. In this system, she can define the access policy by herself based on the physician’s attributes and a specific access structure; enforce it by encrypting it under the policy before outsourcing it to the Cloud Service Provider.
Physicians: This is the group that includes all the hospital staff that will be handling patient data, for example the doctor who is treating a certain patient. The physicians obtain their private keys based on their professional responsibilities, and need to access the patient records for providing medical care.
Trusted Authority: This entity is in charge of cryptographically initializing each user’s registration into the system. The TA assigns a Global identity called the Master Key as well as a global public key, which is published to all the other users to allow them to use it for encrypting or decrypting data relative to that user. Each patient and physician is assigned a key pair which is used to perform security operations such as authentication in this domain.
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 268

ISSN 2229-5518
Physician
Figure. 1
Trusted
Authority
Cloud Service
Provider
Patient
considered one of the most suitable schemes for data access in cloud storage because it provides data owners with more direct control and flexibility on access policies. In a ciphertext- policy attribute-based encryption scheme, ciphertexts are associated with access structures over the subsets of at most n attributes of the attributes set, for some specified n ϵ N.
Decryption works only if the attribute set ω associated with a
certain secret key is authorized in the access structure A (i.e.,
ω ∈ A) [21]. Bethencourt et al.’s CP-ABE scheme consists of
the following four algorithms: Setup, KeyGen, Encrypt, and
Decrypt, as shown in Figure. 4. These algorithms are described
in detail in [28].
This section gives formal definitions for access structures and relevant background on Linear Secret Sharing Schemes (LSSS), followed by the definitions of Ciphertext Policy Attribute Based Encryption (CP-ABE) then a brief description on revocation.
In our context, the role of the parties described in Figure.2 is taken by the attributes. Thus, the access structure A will contain the authorized sets of attributes S and if a set of attributes is not in A then the owner is an unauthorized user.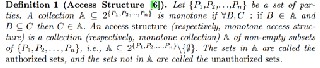

Figure. 2
Figure. 3
It is shown in [34] that every linear secret sharing-scheme, according to the Figure. 3, definition also enjoys the linear reconstruction property, defined as follows:
Suppose that Π is an LSSS for the access structure A. Let S
∈ A be any au thori zed set, and let I ⊂{ 1, 2,..., l } be d efi ned asI

= {i ∶ ρ(i) ∈ S}. Then, there exist constants {ωi ∈ Zp }i∈I such that, if {λi }are valid shares of any secrets according to Π, then ωiλi = 𝒔. ∑i∈I ωi λi = s. Furthermore, it is shown in [34] that
these constants {ωi } can be found in time polynomial in the
size of the share-generating matrix M [32].
Proposed by Bethencourt et al. in 2007, CP-ABE is a variation of Attribute Based Encryption in [27] that makes use of encrypted data (ciphertext) for its access policy. It is
Figure. 4

Motivated by the fact that the professionals handling the patient data or the people in the social circles of the patient may change and the need for access control in cloud storage, the need for revocation arose. This was meant to address cases such as; how to disqualify a user and prevent him to access ciphertexts that were encrypted while the user still had rights and also ensuring that a newly encrypted data is not decryptable by a user whose key has been revoked already. The paradigm of revocation is categorized into two designs namely the central-control and another one is user-control. In a central-control design, system manager or a trusted third parties T centrally maintains revocation lists and this is the one that was incorporated by Fatos et.al. To implement revocation, an additional algorithm; PubUpdate is used which is periodically run such that using publicly available information, ciphertexts stored on the system can be updated periodically [37]. This will ensure that as soon as a user U has been revoked, all files become inaccessible to them, regardless of how old each file is. The algorithm is shown in Figure. 5.
Figure 5
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 269
ISSN 2229-5518
The proposed system, using the CP-ABE as the underlying primitive, includes;
𝑟𝑚1 = �〈ui , Px (ui )⟩∀
∈RL 〉�
,
∀x∈U′
![]()
System setup: it is basically an initialization of the system. It is used to generate the master secret key and public
𝑟𝑚2 = �〈𝑥i , Px (𝑥i )⟩∀ ∈{1,...,𝑡 〉�
∀x ∈U −U′
, (3)
parameters from an input of the security parameter K and the
attribute universe 𝑈.
Key generation: the patient generates her private key and the
revocation key for the physician which has to be revoked.
Data storage: data is to be stored in the cloud, but prior to its
transmission to the Cloud Service Provider, it has to be
encrypted.
Data access: for a physician to be able to access a patient’s
data, he sends a request message and his transformation key tk![]()
to the Cloud Service Provider, which will return the
transformed ciphertext 𝐶𝐶 ′ or a reject response.
Decryption: If the physician has received a ciphertext from
the Cloud Service Provider, then he can apply his secret key sk
to decrypt the ciphertext.
![]()
To initialize the system, the patient runs the following steps:
(1) Set the security parameter K and the attribute universe
description U = {1,2, . . . , |U|} and choosing two multiplicative cyclic groups G and GT of prime
order p with an admissible bilinear map
e: G × G → GT and a hash function H: {0,1}∗ → G;
(2) Randomly choosing ∝, β, a ∈ ZP and a polynomial Px of
degree t x (t x is the maximum number of revoked
physicians for attribute x at a given time) over ZP , for
each attribute x such that Px(0) = β. The public
parameters are published as
params = {G, g, e(g, g)α, g 𝑎 , H}, (1)
Where, g is a generator of G. The master secret key is
set as 𝑚𝑚𝑚 = (gα, β, {Px}∀ ).
The patient generates her private key and the revocation key in the following steps:
(1) The private key generation process for patient involves
taking as input the 𝑚𝑚𝑚 and calculating uk ′s
transformation key 𝑡𝑚 as follows:
K = g (∝/y gatβ , L = g tβ, (2)
Where; {xi } are chosen from Zp and they are different from
any user’s identity.
Lastly, the patient sends the private key sk to the user uk
through a secure communication channel and updates the
revocation key rk to the Cloud Service Provider.
{Kx = H(x)t}∀ ∈S , {K′ = H(x)
tPx(uk )
′
}∀x ∈S .
Then, set sk = (γ, tk) = �γ, �K, L, {Kx , Kx}∀x ∈S ��.
(2) Take as input msk and {RLx }∀x ∈U′ , where U
⊂ U is the set
of attributes that the patient decides to revoke and RLx is a list of physicians {u1 , . . . , utx }whose attribute x will be
revoked by the patient. Then, create the revocation key
rk = (rk1, rk2 ) as follows:
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 270
ISSN 2229-5518
e(C′, K)
TC1 =![]()
′ µ ′ ω′
A patient’s data includes his personal details, medical history
and current diagnosis that are to be sent for storage in the
cloud and have to be encrypted first. Encryption has to be
done before the data is uploaded to protect it while in transit
as well as at rest on the Cloud Service Provider’s premises. The encryption process for the health data is done as follows.
As input parameters, a message m, and an access structure (M, ρ), are taken, with M denoting a matrix of l rows and n columns and the function ρ associating rows of M to the
∏i∈I′(e(L, Ci )e(Di , Kρ(i) ) ρ(i),𝑘 e�Di , Kρ(i) �) 𝑖![]()
e(C′,K)
= ′
ω𝑖
∏ (e(g,g)atλiβ e�g,H(ρ(i)))−triβ �
![]()
1
. ′
∏ ( e�g, H(ρ(i)))triµρ(i),𝑘Pρ(i)(uk ) �ω𝑖
![]()
. 1
attribute universe U.
n
∏i∈I′( e�g,H�ρ(i)�)
tρ(I)
tr Σ
j=1
′
𝑖
µρ(I),𝑗Pρ(i) �uj��
A random vector v = (s, γ2 , . . . , γn ) ϵ Zp
is firstly chosen, where
the values γ2 , . . . , γn will be used to share the encryption
exponent s, and then calculate λi = vMi for i = 1 to l, where![]()
e(C′,K)
=![]()
(∝/γ)s atβs
′β atβΣ
(7)
Mi is the ith row of M.
Randomly choose r1 , . . . , rl ∈ Zn at first, and then compute the
∏i∈I′
e(g,g)atλiω𝑖
e(g,g)
iϵI′λiωi
ciphertext CT as follows:
C = m ∙ e (g, g)αs , C′ = g s ,
= e(g, g)(∝s/γ) .
In the end the Cloud Service Provider sends back the
transformed ciphertext to the physician.
(Ci = g aλi H (ρ(i))−ri , Di = g ri )∀i∈{1,...,l} . (4)
Finally, the patient uploads the encrypted data;
CT = ((M, ρ), C, C′ , (Ci , Di )∀i∈{1,...,l} ) to the Cloud Service
Provider.
When a physician wants to access a patient’s data, he sends the request message and his transformation key tk to the CSP.
Then, the CSP transforms the encrypted data CT to CT′ as
follows.
(1) It takes as input rk, tk, uk and CT and outputs ⊥, if uk’s attribute set S′ after revocation does not satisfy the access structure (M, ρ) . Otherwise, let I′ ⊂ {1, . . . , l} be defined as I′ ⊂ {i ∶ ρ(i) ∈ S′ } and let {ω′ ϵZ } ′ be a
Decryption is associated with patient data access. When a doctor, for example a heart surgeon wants to access a patient’s medical history, they first have to download the file which will be in a ciphertext format. Depending on whether he has the right privileges, he can access the file. The decryption is a success if and only if; the attribute set S associated
with the CT satisfies the access policy given by A, and the physician’s identity specified by the secret key has not been revoked according to the revocation list
Receiving the transformed ciphertext CT′, the authorized physician uk can easily retrieve the patient’s data in the
following way:
set of constants, such that ∑i∈I′ ω′λ
= s if {λi} are valid
(1) Take as input the transformed ciphertext CT ′ and his
shares of any secret s according to M. First calculate
D′ as follows:
tρ(i)
j=1
private key sk associated with an attribute set S which satisfies the access structure enforced on the encrypted data.
(2) Retrieve the message m by simply computing
D′ = D
ρ(i),jPρ(i)uj
, ∀i ∈ I′, (5)
un
![]()
TC0
γ
TC1
![]()
𝑚∙𝑒(𝑔,𝑔)∝𝑠
𝑒(𝑔,𝑔)∝𝑠
= 𝑚. (8)![]()
Where µρ(i),j = �uk /�uk − uj �� Πn ≠j �
un − uj
�, for all
j, n ∈ �1, . . . , t ρ(i) �, k ∉ �1, . . . , tρ(i) �, and then
compute µρ(i),k:![]()
µ = ∏ un , ∀n ∈ �1, . . . , t �, k ∉ �1, . . . , t �. (6)
un − uk
(2) Terminate the transformation process if the output in
step (1) is ⊥. Otherwise, let I ⊂ {1, . . . , l} be defined as
I = {i: ρ(i) ∈ S} and let {ωi ϵZp}i∈I be a set of constants,
such that ∑i∈I′ ωi λi = s if {λi} are valid shares of any
secret s according to M (there could be different ways
to choose the values to satisfy this). Then, calculate
TC1 as follows:
The proposed system prevents unauthorised who have attributes that do not satisfy the access policy from learning the content of the private data encrypted under the policy. Revoked users should also be prevented from accessing
patient data unless their remaining attributes satisfy the access policy.
For an unauthorized physician who has an attribute set S
which does not satisfy the access policy, he cannot recover the
desired value e(g, g)∝s, which is needed for decryption in both
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 271
ISSN 2229-5518
physician and attribute revocation. While trying to retrieve
e(g, g)atβs from pieces e(g, g)at λiβ during the decryption
process, the physician is required to have a secret key
associated to an attribute set satisfying the access structure
(M,ρ) but when revoked, he cannot decrypt the ciphertext in
the user revocation case. This is due to the fact that his secret
key would be completely revoked; that is, e(g, H(ρ(i)))triβ
cannot be retrieved using Lagrange interpolation for every
attribute(i), i ∈ I. For the attribute revocation case, if the
partial secret key corresponding to some attributes that satisfy
the access policy is revoked, the physician cannot decrypt the
ciphertext (unless the rest of his attributes still satisfy the
policy). This is because e(g, H(ρ(i)))triβcannot be obtained for the revoked attributes ρ(i), i ∈ I′ . Therefore, in both cases the physician cannot access e(g, g)∝s. Because the CSP is not fully
trusted, it cannot decrypt any ciphertext, thought it possesses
the revocation keys since it will not be having secret keys
assigned to it. On the other hand, even if the service provider
can help some physician transform the ciphertext CT to CT′
and obtain e(g, g)∝s using the user’s transformation key tk, he
still cannot decrypt the ciphertext, because he does not know
the secret key. Hence, data confidentiality against the service
Attack from multiple physicians who cannot decrypt the
ciphertext alone: Colluding physicians can retrievee(g, g)at λiβ , as they try to recover the required value e(g, g)at βsfor decryption purposes. With enough shares e(g, g)at λiβ of
exponent S, according to LSSS it is quite easy to obtain
e(g, g)as however, the value t is a random and unique
exponent for each physician, so the reconstruction of s is
prevented by the distinct exponents. Hence, attribute collusion
attack can be precluded in the proposed schemes.
In the healthcare environment, a patient will have to revoke a physician who is no longer providing her healthcare, for example if a patient had fever a week and Physician A was their doctor. After the fever is gone the patient can revoke Physician A because there is no reason for him to still continue accessing her data, concerning that sickness. If a patient
revokes a physician uk , the patient creates and sends a revocation list (RL) including the physician uk that has to be
revoked, and generates a revocation key rk to the CSP. The
CSP cannot cancel the appearance of the random part
e(g, H(ρ(i)))−triβin the transformation process because the CSP
cannot calculate µk and Di k k
′for u
since u
belongs to the
provider is also guaranteed.
Even if a group of physicians that are not entitled to access a specific ciphertext collude together by combining their attributes, the y still cannot decrypt the ciphertext. The proposed scheme is collusion-resistant, considering attacks from Cloud Service Provider (CSP), users who cannot decrypt ciphertext alone and users that are authorized but revoked.
Attack from the CSP: An authorized yet revoked physician
uk tries to decrypt a selected ciphertext by colluding with the
CSP. However, the service provider just keeps the latest
revocation key in its memory and the old one is erased each
time the revocation takes place. Therefore, D′ and µ cannot be
calculated hence the revoked user fails to decrypt the
ciphertext even though his attributes meet the specified access
policy. The proposed system is thus collusion-resistant from
the revocation and CSP attack.
Attack from unrevoked yet unauthorized physician or revoked yet authorized physician: In the case of an authorized but revoked physician, their attribute set S meets the access structure but still cannot decrypt the ciphertext because his secret key is revoked completely. Due to the fact that he cannot get the
coefficient µk and D′ from the CSP, he cannot obtain
e(g, H�ρ(i)�)triβ . Therefore he cannot retrieve e(g, g)at λiβ
neither can he reconstruct the required value e(g, g)at βsfor
decryption. Even in a case where the authorized and revoked
physician colludes with the unauthorized but unrevoked
physician, he cannot retrieve e(g, g)at λiβ , since t is a random
and unique exponent for each user. Furthermore, the latter can
only obtain finite e(g, H�ρ(i)�)triβ for his attribute set which
does not satisfy the policy. For the same reasons, the former
cannot help the latter retrieve e(g, g)at βs as well.
revocation list. Therefore the physician’s secret key would be
completely revoked and will not have access to the plaintext of
subsequent data uploaded afterwards. For attribute
revocation, the CSP would be unable to compute µρ(i),k and D′
if u′ s attributeρ(i) is revoked, hence it will not be able to
cancel e(g, H�ρ(i)�)−triβ . Therefore the physician will be in no
position to access the plain text of subsequent data, unless his
remaining attributes can still satisfy the access structure, for
example if he is also a specialist in another department.
With regards to backward secrecy, a revoked physician
who wants to access the previous data will transmit uk and tk to the CSP. However it cannot calculate µk/ µρ(i),k and Di for uk , since the revocation key rk is updated and uk is included in
the revocation list. Therefore the physician will not be able to
access the previous data, except his remaining attributes still
satisfy the access policy (in the case of attribute revocation).
Even when µk/ µρ(i),k for the revocation list RL/RLρ(i) and Di
for the ciphertext Di have been calculated before his attributes
were revoked, they will not be sufficient to decrypt
subsequent or previous data, because rk is updated and D′ for the new Di needs to be calculated.
This paper discusses the challenges that are faced in the healthcare industry due to the adoption of cloud computing, CP-ABE and its variation with revocation. It proposes a secure healthcare system that inherits ciphertext policy attribute based encryption, with the aim to improve privacy, confidentiality and security by improving revocability at the same time ensuring collusion-resistance together with forward and backward secrecy.
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 272
ISSN 2229-5518
1 M. Poulymenopoulou & F. Malamateniou & G. Vassilacopoulos, Emergency Healthcare Process Automation Using Mobile Computing and Cloud Services Department of Digital Systems University of Piraeus, Greece, Springer Science and Business Media, 2011.
2 L. Wang, D. Chen, Y. Hu, Y. Ma, J. Wang, Towards enabling cyber infrastructure as a service in clouds, Computer. Electrical. Engineering, vol. 1, pp. 3–14, 2013.
3 L. Wang, G. Laszewski, A.J. Younge, X. He, M. Kunze, J. Tao, C. Fu, Cloud computing: a perspective study, New Generation. Computing, vol. 28 no.2, pp. 137–146, 2010.
4 Mu-Hsing Kuo, Opportunities and challenges of cloud computing to improve health care services, Journal of Medical Internet Research, 2011.
5 Syed A. Ahson, Mohammad Ilyas, Cloud Computing and Software Services
Theory and Techniques, CRC Press, 2010.
6 L.M. Kaufman, Data security in the world of cloud computing, IEEE Security and Privacy. vol. 7, no. 4, pp. 61–64, 2009.
7 D. Zissis, D. Lekkas, Addressing cloud computing security issues, Future
Generation Computer. Systems, pp. 583–592, 2012.
8 Managing cyber risks in an interconnected world Key findings from The Global State of Information Security Survey 2015, www.pwc.com/gsiss2015 , www.pwc.com/cybersecurity , 2014
9 Yue Tong, Jinyuan Sun, Sherman S. M. Chow, and Pan Li, Cloud-Assisted Mobile-Access of Health Data With Privacy and Auditability, IEEE Journal of Biomedical and Health Informatics, vol. 18, no. 2, 2014.
10 S. Vimercati, S. Foresti, S. Jajodia, S. Paraboschi, P. Samarati, A data outsourcing architecture combining cryptography and access control, Computer security architecture, ACM, pp. 63-69, 2007.
11 Junbeom Hur, Dongyoung Koo, Seong Oun Hwang, Kyungtae Kang, Removing escrow from ciphertext policy attribute-based encryption, School of Computer Science and Engineering, Chung-Ang University, Department of Computer Science, KAIST, Department of Computer and Information Communications Engineering Hongik University, Department of Computer Science and Engineering, Hanyang University, Computers and Mathematics with Applications, Elsevier, 2012.
12 Peter Mell & Timothy Grance, The NIST Definition of Cloud Computing, Computer Security Division Information Technology Laboratory, National Institute of Standards and Technology Gaithersburg, NIST Special Publication
800-145, 2011.
13 Tim Mather, Subra Kumaraswamy, and Shahed Latif, Cloud Security and
Privacy, O’Reilly Media, Inc., First Edition, September 2009.
14 Amit Sahai , Hakan Seyalioglu, Brent Waters, Dynamic Credentials and Ciphertext Delegation for Attribute-Based Encryption, UCLA, University of Texas at Austin, 2012.
15 J. Zhao, L. Wang, J. Tao, J. Chen, W. Sun, R. Ranjan, J. Kolodziej, A. Streit, D.
Georgakopoulos , A security framework in G-Hadoop for big data computing across distributed cloud data centers, Journal of Computer and Systems Sciences, vol. 80, no.5, pp. 994–1007, 2014.
16 HIPAA. U.S. Department of Health and Human Services.
http://www.hhs.gov/ocr/privacy/index.html.
17 Kathryn A. Booth, Leesa G. Whicker, Terri D. Wyman, Donna J. Pugh, Sharon Thompson, Medical Assisting: Administrative and Clinical Procedures, Legal and Ethical Issues in Medical Practice, Including HIPAA, , McGraw-Hill Higher Education, 2009.
18 Juha Saarinen, UK health trust fined for privacy breach. Information Technology News, Aug 7, 2012. http://www.itnews.com.au/News/311079,uk-health-trust-fined-for-
privacy-breach.aspx .
19 M. Li, S. Yu, Y. Zheng, K. Ren, and W. Lou, “Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption, IEEE Transactions, Parallel Distributed Systems., vol. 24, no. 1, pp. 131–143,
2013.
20 Bruce Jennings, Mary Ann Baily, Melissa Bottrell, Joanne Lynn, HealthCare Quality improvement: ethical and regulatory issues, The Hastings Center Garrison, New York, 2007.
21 Brussels, Cloud Service Level Agreement Standardisation Guidelines, ISO/IEC JTC 1/SC 38- http://www.iso.org/iso/home/store/catalogue_tc/catalogue_detail.htm?cs number=63902 , 2014.
22 M. Eric Johnson and Nicholas D. Willey, Usability Failures and Healthcare Data Hemorrhages, Dartmouth College, IEEE Computer and Reliability Societies, 2011.
23 Dan Hubbard, Michael Sutton, Zscaler, Top Threats to Cloud Computing, Websence, Cloud Security Alliance, 2010.
24 Ateniese, R. Curtmola, B. de Medeiros, and D. Davis, Medical information privacy assurance: Cryptographic and system aspects, 3rd Security in Communication Networks Conference, Amalfi, Italy, 2002.
25 A. Sahai and B. Waters. Fuzzy Identity Based Encryption. In Advances in
Cryptology – Eurocrypt, Springer, vol. 3494 of LNCS, pp. 457–473, 2005.
26 V. Goyal, O. Pandey, A. Sahai, B.Waters, “Attribute -based encryption for fine-grained access control of encrypted data”, ACMCCS 2006, pp. 89 -98,
2006.
27 Bethencourt J, Sahai A, et al. Ciphertext-Policy attribute-Based Encryption, IEEE, Security and Privacy, pp.321-334, 2007.
28 Cheng-Chi Lee, Pei-Shan Chung, and Min-Shiang Hwang, A Survey on Attribute-based Encryption Schemes of Access Control in Cloud Environments, Department of Library and Information Science, Fu Jen Catholic University, Department of Management Information Systems, National Chung Hsing University, Department of Computer Science and Information Engineering, Asia Universtiy, International Journal of Network Security, vol.15, no.4, pp. 231-240, 2013.
29 Huang Lin, Jun Shaoy, Chi Zhangz, and Yuguang Fang,Fellow, “CAM: Cloud-Assisted Privacy Preserving Mobile Health Monitoring, IEEE Tranasctions on image processing, vol 8, no. 6, 2013.
30 Carlos Oberdan Rolim, Fernando Luiz Koch, Carlos Becker Westphall, Jorge Werner, Armando Fracalossi, Giovanni Schmitt Salvador, A Cloud Computing Solution for Patient’s Data Collection in Health Care Institutions, Network and Management Laboratory - LRG Federal University of Santa Catarina Florianopolis, Telemedicine, and Social Medicine, eTELEMED, 2010.
31 J. Sun, X. Zhu, C. Zhang, and Y. Fang, HCPP: Cryptography based secure EHR system for patient privacy and emergency healthcare, IEEE International Conference Distributed Computing Systems, pp. 373–382, 2011.
32 Tu S, Niu S, Li H, Xiao-ming Y, Li M (2012): “Fine-grained access control and revocation for sharing data on clouds”, IEEE 26th international parallel and distributed processing symposium workshops and PhD forum (IPDPSW), pp. 2146–2155, 2012.
33 CHENG, Zhi-ying WANG, Jun MA, Jiang-jiang WU, Song-zhu MEI, Jiang-
chun, “Efficient revocation in ciphertext-policy attribute-based encryption based cryptographic cloud storage”, Yong, School of Computer, National University of Defense Technology, Changsha, China, Zhejiang University and Springer-Verlag Berlin Heidelberg, Computer and Electronics, vol. 14, no. 2, pp. 85-97, 2013.
34 D. Boneh, X. Ding, G. Tsudik, and C. Wong, “A method for fast revocation of
public key certificates and security capabilities,” in Proceedings of the 10th conference on USENIX Security Symposium, vol. 10. USENIX Association, p.
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 273
ISSN 2229-5518
22, 2001.
35 Danan Thilakanathan, Shiping Chen, Surya Nepal, Rafael Calvo, Leila Alem, A platform for secure monitoring and sharing of generic health data in the Cloud, The University of Sydney, Australia, Future Generation Computer Systems, Elsevier, 2013.
36 Shi-Feng Sun, Chen Lyu,1 Dawu Gu, Yuanyuan Zhang, and Yanli Ren, Towards Efficient, Secure, and Fine-Grained Access Control System in MSNs with Flexible Revocations, Department of Computer Science & Engineering, Shanghai Jiao Tong University, School of Communication and Information Engineering, Shanghai University, China, International Journal of Distributed Sensor Networks Volume 2015, 2015.
37 Fatos Xhafa, Jingwei Li, Gansen Zhao, Jin Li, Xiaofeng Chen, Duncan S.
Wong, Designing cloud-based electronic health record system with attribute- based encryption, Springer Science and Business Media New York, 2014.
IJSER © 2015 http://www.ijser.org