International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 547
ISSN 2229-5518
Secure Strategy for High Speed Transmission
& Efficient Collection of Data in WSN Research
Kamal Kr. Gola1, Bhumika Gupta2, Zubair Iqbal3
Abstract— W ireless Sensor Networks (W SNs) consist of small nodes with sensing, computation and wireless communications capabilities. W ireless sensor networks utilize large numbers of wireless sensor nodes to collect information from their sensing terrain. Once they are deployed, it becomes impossible to replace or recharge its battery. So the battery power of the sensor node is very important. As we know that Energy efficient routing is one of the key issues in wireless sensor network because all the nodes are battery powered, so failure of one node affects the entire network that’s why Energy saving is always crucial to the lifetime of a wireless sensor network. Many routing protocols have been proposed to maximize the network lifetime and decrease the energy consumption. But these algorithms do not provide any security at that time when the data has to be sent to the node as well as to the base station and also do not define how to collect high speed data in efficient way. We proposed an algorithm to provide these two services. The main purpose of the proposed algorithm is to reducing the time in the collection process of data in the wireless sensor networks and also provide the security at the time of transmission(among the node and node to base station) using.
Index Terms— W SN, energy efficient, cluster head, data aggregation, shortest path algorithm, Base station, Security Algorithm, QOS Parameters, RDM, Re-Clustering.
1 INTRODUCTION
—————————— ——————————
ireless sensor network (WSN) is widely considered as one of the most important technologies for the twenty-first century.[1] In the past decades, it has re-
ceived tremendous attention from both academia and industry all over the world. A WSN typically consists of a large number of low-cost, low-power, and multifunctional wireless sensor nodes, with sensing, wireless communications and computa- tion capabilities.[2][3] These sensor nodes communicate over short distance via a wireless medium and collaborate to accomplish a common task, for example, environment monitoring, military surveillance, and industrial process control.[4] The basic philosophy behind WSNs is that, while the capability of each individual sensor node is limited, the aggregate power of the entire network is sufficient for the required mission. In many WSN applications, the deploy- ment of sensor nodes is performed in an ad hoc fashion without careful planning and engineering. Once deployed, the sensor nodes must be able to autonomously organize themselves into a wireless communication network. Sensor nodes are battery-powered and are expected to operate with- out attendance for a relatively long period of time. Due to the severe energy constraints of large number of densely de- ployed sensor nodes, it requires a suite of network proto- cols to implement various network control and management functions such as synchronization, node localization, and net- work security. The traditional routing protocols have several shortcomings when applied to WSNs, which are mainly due to
————————————————
• 1Kamal Kumar Gola is currently pursuing masters degree program in com- puter science & engineering in Uttarakhand Technical University, India, PH-9456893676. E-mail: kk_gola1503@gmail.com
• 2Bhumika Gupta is currently working as Assistant Professor in Department of Computer science & Engineering GB Pant Engineering College, Pauri Garhwal, Uttarakhand, India.
• 3Zubair Iqbal is currently working as Assistant Professor in Department of
Computer science & Engineering Moradabadad Institute of Technology, Moradabad, Uttar Pradesh,India, PH-9997869683.
E-mail: zubairiqbal17@gmail.com
the energy-constrained nature of such networks.[4] Further- more, these inconveniences are highlighted when the number of nodes in the network increases. A large number of research activities have been carried out to explore and overcome the constraints of WSNs and solve design and application issues.
2 ENERGY EFFICIENT ROUTING PROTOCOLS IN WS
2.1 Low-energy adaptive clustering hierarchy (LEACH)
LEACH [5] is the first and most popular energy-efficient hier- archical clustering algorithm for WSNs that was proposed for reducing power consumption. In LEACH, the clustering task is rotated among the nodes, based on duration. Direct com- munication is used by each cluster head (CH) to forward the data to the base station (BS). It uses clusters to prolong the life of the wireless sensor network. LEACH is based on an ag- gregation (or fusion) technique that combines or aggre- gates the original data into a smaller size of data that carry only meaningful information to all individual sensors. LEACH divides the a network into several cluster of sen- sors, which are constructed by using localized coordination and control not only to reduce the amount of data that are transmitted to the sink, but also to make routing and data dissemination more scalable and robust. LEACH uses a randomize rotation of high-energy CH position rather than selecting in static manner, to give a chance to all sensors to act as CHs and avoid the battery depletion of an indi- vidual sensor and dieing quickly. The operation of LEACH is divided into rounds having two phases each namely (i) a set- up phase to organize the network into clusters, CH advertise- ment, and transmission schedule creation and (ii) a steady- state phase for data aggregation, compression, and transmis- sion to the sink.
IJSER © 2014
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 548
ISSN 2229-5518
2.2 Power-Efficient Gathering in Sensor Information
Systems (PEGASIS)
PEGASIS [6] is an extension of the LEACH protocol, which forms chains from sensor nodes so that each node transmits and receives from a neighbor and only one node is selected from that chain to transmit to the base station (sink). The data is gathered and moves from node to node, aggregated and eventually sent to the base station. The chain construction is performed in a greedy way. Unlike LEACH, PEGASIS avoids cluster formation and uses only one node in a chain to transmit to the BS (sink) instead of using multiple nodes. A sensor transmits to its local neighbors in the data fusion phase instead of sending directly to its CH as in the case of LEACH. In PEGASIS routing protocol, the construction phase assumes that all the sensors have global knowledge about the network, particularly, the positions of the sensors, and use a greedy approach. When a sensor fails or dies due to low battery power, the chain is constructed using the same greedy approach by bypassing the failed sensor. In each round, a randomly chosen sensor node from the chain will transmit the aggregated data to the BS, thus reducing the per round energy expenditure compared to LEACH.
2.3 Hybrid Energy-Efficient Distributed Clustering
(HEED)
HEED [7] extends the basic scheme of LEACH by using re- sidual energy and node degree or density as a metric for cluster selection to achieve power balancing. It operates in multi-hop networks, using an adaptive transmission power in the inter-clustering communication. HEED was proposed with four primary goals namely (i) prolonging network lifetime by distributing energy consumption, (ii) terminat- ing the clustering process within a constant number of iterations, (iii) minimizing control overhead and (iv) pro- ducing well-distributed CHs and compact clusters. In HEED, the proposed algorithm periodically selects CHs according to a combination of two clustering parameters. The primary parameter is their residual energy of each sensor node (used in calculating probability of becoming a CH) and the secondary parameter is the intra-cluster communi- cation cost as a function of cluster density or node degree (i.e. number of neighbors).
2.4 Power Efficient Data Gathering and Aggregation
Protocol
Power Efficient Data Gathering and Aggregation Protocol [8] based on idea of minimum spanning tree. It minimized the long distance transmission among the sensor node and base station as well as minimized the distance between the sensor nodes. It is also a clustering algorithm, but it is more efficient as compare to LEACH and PEGASIS in terms of energy saving in sensor nodes. Another advantage is it enhances the life time of network even if base station is inside the field where as this condition can not applicable to either LEACH or PEGASIS.
2.5 Top down Approach
A Delay-aware data collection was done by Cheng et al. 2011 [9]. In their work they gave two approaches for data collection, one is Top-down and another one is bottom up approach. In
bottom up approach the network structure is not that much energy efficient while transmitting the data to base station because in their network structure large numbers of nodes are involve in transmit their data to a longer distance so large amount of energy is consumed. In our research work we try to overcome this problem by reducing the transmission distance among nodes by forming a different network structure among the nodes and to transmit data as fast as possible as well.
3 ATTACKS ON ROUTING
Since the concept of sensor networks originates from the wireless ad-hoc networks, many attacks on wireless ad- hoc Networks can be adapted for sensor networks. Sybil at- tack is such an example.[10] Karlof and Wagner[11] show another types of attacks and furthermore they propose two novel attacks – HELLO floods and sinkholes. Denial of Service attacks on sensor networks are studied by Stankovic and Wood.[12] We present a brief summary of major attack Classes here.
3.1 Bogus routing information
The basic method how to influence routing is to change the routing information. An Adversary spoofs, alters or replays routing information. By these methods he can create loops in routing, increase Latency, extend the paths or attract the traffic to the chosen node.
3.2 Selective forwarding
Selective forwarding is a variant of the DoS attack. Malicious node forwards only chosen packets and drops the rest. At- tacker has to be included in the path of the data flow to mount selective forwarding. To do so, he can use can use Sybil attack or sinkhole attack. The ultimate variant of this attack is called a Black hole attack. In such case, all the packets are dropped. However node behaving like a Black hole can be easily detect- ed by the neighboring nodes, considered as dead and ex- cluded from the routing path. Therefore dropping only some messages may be more beneficial for the attacker.
3.3 Sinkhole attack
The goal of the sinkhole attack is to attract as much of the traf- fic as possible to the malicious node. The principle of this at- tack is that the malicious node tries to look very attractive for other nodes with respect to the routing algorithm. This goal can be achieved, for example, by spoofing the route ad- vertisement or by providing a high-quality path to the base station using wormhole attack. Sinkhole can be further used for selective forwarding, which is very efficient and easy in that case.
3.4 HELLO flood attack
In some protocols, nodes announce themselves to the neighbors by broadcasting the HELLO packets. Node receiv- ing such packet concludes that the broadcasting node is his neighbor and is within the normal radio range. A laptop class attacker can use a powerful radio to send HELLO packets to nodes, which are far more distant than the normal radio range from him. These nodes will send their messages to oblivion trying to reach the neighbor, which is not in their radio range.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 549
ISSN 2229-5518
3.5 Wormhole attack
Wormhole is a low-latency out-of-band channel used to con- nect two distant part of the network. Wormhole attack exploits the routing race conditions. This means that message, which should normally traverse multiple nodes, traverse only single one and hence is delivered in a much less time. Time of the delivery can be important for the routing scheme, especially if the influenced message contains routing information. The at- tacker can send replayed packets through the wormhole to persuade two distant nodes that they are neighbors. He can, for example, create wormhole between the base station and a node at the opposite side of network, thus instead of multiple hops the node appears to be only single hop from the base station. Therefore it becomes a sinkhole for his neigh- bors providing low-latency route to the base station.
3.6 Acknowledgement spoofing
Acknowledgement spoofing focus on the algorithms using link layer acknowledgements. An attacker spoofs these acknowledgements to persuade the node, that its dead neighbor is alive or that the weak link is reliable. The impact is similar to selective forwarding; chosen packets are lost with high probability.
3.7 Sybil attack
In the Sybil attack, the attacker simulates multiple nodes and advertises multiple identities to the rest of the network. By this, he can cripple even the robust multipath routing algo- rithms, because the bulk of the paths (even all) may pass through him. In geographic routing, attacker’s node can be virtually at more locations simultaneously and thus influ- ence routing algorithm. Sybil attack in general means serious threat not only for routing, but also for other algorithms such as voting algorithm or distributed storage.
3.8 Denial of Service
Denial of Service represents more or less general class of at- tacks, which can be mounted on several ISO/OSI layers of wireless sensor network, including the network layer. Almost all above attacks, especially selective forwarding and HELLO floods, can result in the denial of service.
4 THE SYSTEM MODEL
4.1 Network Model
The protocol assumes that 40 sensor nodes are distributed randomly in the network area of diameter 100m. In addition to data aggregation, each node of the network has the capability to transmit data to other sensor nodes as well as to BS. The aim is to transmit the aggregated data to base station with minimum loss of energy which in fact increase system life time in terms of rounds. In this paper we consider sensor net- work environment where:
i) Each node periodically senses its nearby environment &
likes to send this data to BS.
ii) Base Station is placed at a fix location.
iii) Sensor nodes are homogeneous & energy constrained.
iv) Sensor nodes are dynamic & are uniquely identified time to
time.
v) Data fusion & aggregation is used to reduce the size of mes-
sage in the network. We assume that combining n packets of
size k results in one packet of size k instead of size nk.
4.2 Radio Model
We use the same radio model as discussed in [13]. In this model, a radio dissipates Eelec = 50 nJ/bit to run the trans- mitter or receiver circuitry and Eamp = 100 pJ/bit/m2 for the transmitter amplifier. The radios have power control and can expend the minimum required energy to reach the intended recipients. The radios can be turned off to avoid receiving un- intended transmissions. An r2 energy loss is used due to channel transmission [14]. The equations used to calculate transmission costs and receiving costs for a k-bit message and a distance d are shown below:
Transmitting
Etr (k,d) = Eelec(k) +Eamp (k,d)
= kEelec+kEampd2
Receiving
ERx(k) = ERx-elec(k) ERx(k) = Eelec*k
Receiving is also a high cost operation, therefore, the number of receives and transmissions should be minimal. LEACH and PEGASIS use the same constants (Eelec, Eamp, and k) for cal- culating energy costs; therefore the proposed protocol achieves energy savings by minimizing the distance and the number of transmissions and receives for each node. In our simulations, we used a packet length k of 2000 bits. It is as- sumed that the radio channel is symmetric so that the energy required to transmit a message from node i to node j is the same as energy required to transmit a message from node j to node i for a given signal to noise ratio (SNR).
5 PROBLEM STATEMENT
In this work, our main focus is to provide Security in WSN (wireless sensor networks) as well as to provide the strategy to collect the high speed data in efficient manner so that we can increase the network lifetime and decrease the energy con- sumption. As we know that all the sensor node are in direct communication range of each other and can transmit to and receive data from the other sensor node as well as to and re- ceive the data from base station. The nodes periodically sense the environment and have always data to send in each round of communication. At the time of transmission of data, an at- tacker may change the whole data or can hack the data which create the problem. To overcome this problem we are using the concept of public and private key (Modified RSA Digital Signature Scheme). [15]
Sensor Node Information
X | Y | C_id | N_i d | RE | Energy | TH | Distance |
| TE | LOC | PU | PR | DS | RD M | RT |
Where x and y are coordinates that represents the location of
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 550
ISSN 2229-5518
the node in the network.
C_id=Cluster _id, N_id=Node_id, RE=Residual Energy
TH=ThresholdValue,TE=Transmission Energy, LOC=Location
of the nearest node to which data will be transmitted,
PU=Public Key, PR=Private Key, DS=Digital Signature, RDM=
Route discovery message, RT=Route Table.
6 PROPOSED ALGORITHM
Cluster Head Selection and Cluster Formation
1- All nodes will broadcast a message which contains node_id, transmission range, location and energy sta- tus in the network. With the help of this message each node must know about the node _id, transmission range and energy status of all other node in the net- work. Threshold will be defined by base station.
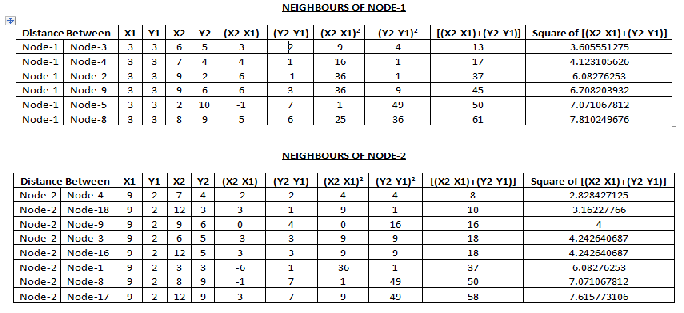
2- FFind the neighbor of each node that is come under
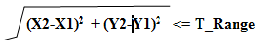
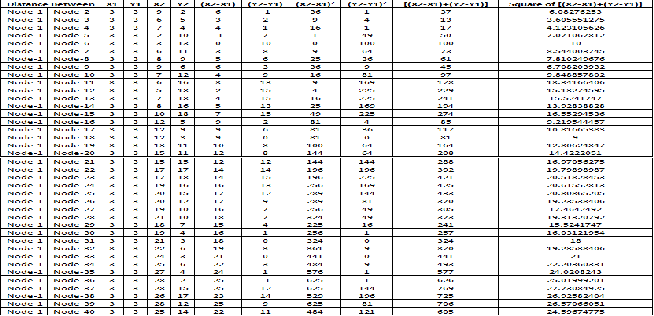
transmission range. Distance between Node is calcu- lated by given formula
part in the election procedure. Now cluster head broadcast message of its selection within the cluster.
9-
Repeat step 1 to 8 for all the remaining nodes till the
Cluster and Cluster Head get forms.
Data Transmission within Cluster
10-
After cluster formation, node having lowest location value will transmit their data to its nearest node with the condition that nearest node should be in same cluster, if the nearest node is in the other clus- ter then it will find the next nearest node in the same cluster. This process will continue till all the data reaches at cluster head and sensor node also maintain route table for future use.
11-
Where T_Range=8
3-
Find the degree of node (ND) for each node that is calculated by total number of neighbours.
12-
Repeat step 10 for the entire cluster.
The nodes that already sent their data will be kept in sleep mode so that their energy level doFes not de- crease.
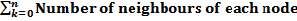
ND=
Data Transmission From Cluster Head to Base Station
13-
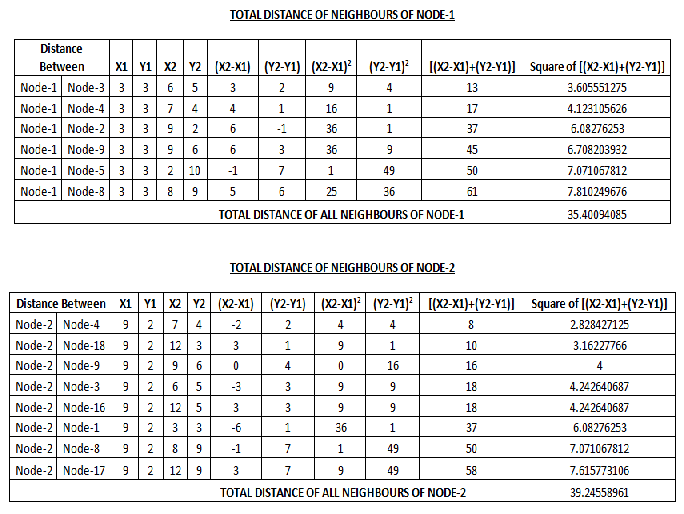
4- FFor every node, compute the sum of distances with all its neighbors using given formula.
SV=
Route discovery message, RDM is initialized by the base station to all the cluster head nodes. The base station starts a multiple path discovery phase to cre- ate a set of neighbors that are able to forward data to the base station. In this case it may be possible
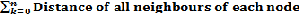
the data to
5- that multiple path will be saved to send C
Compute the average energy of every node using given formula. Initially EEAV=1J
EEAV=1/NV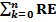
6-
Where, RE is the residual energy of all the neighbor- ing nodes.
7-
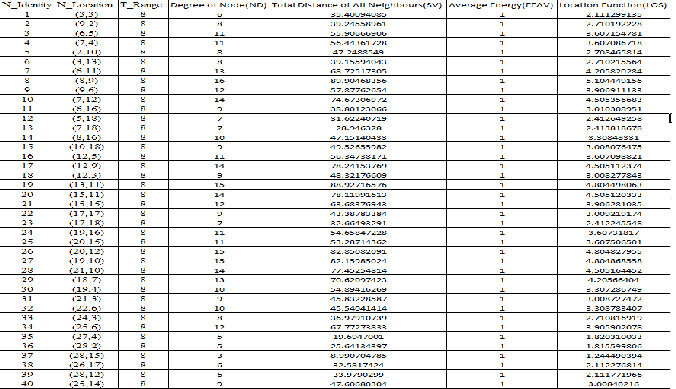
Calculate the value of location function LOS, for each node using given equation.
LOS= [(α*ND) + (β*EEAV) + (γ*(1/SV))]
Where α + β + γ =1
14-
the base station in their respective route table for fu-
ture use.
In order to avoid collision, a TDM schedule will be followed in which each path will be actHive for a particular time quanta , in which cluster heads forward aggregates data to the next cluster head and ultimately to the base station. The prCocess will start from the farthest cluster head. Meanwhile clus- ter heads in alternate paths will be busy in intra cluster communication i.e. collecting data from their
member nodes in a cluster. This process will contin-
α =0.3, β=0.3 and γ=0.3 are the weighting factors for the
corresponding system parameters.
ue in a round robin fashion. Thus, inter cluster and intra cluster transmission will go hand in hand.
8- S
Select the node with the highest LOS as the cluster Head with the condition that all the neighbours of the selected Cluster Head are not allowed to take
Re-Clustering Process
15-
If the cluster head energy level becomes less, then
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 551
ISSN 2229-5518
16-
17-
re-clustering procedure will be called. In this, old CH broadcast re-clustering message with in the cluster with its remaining energy level message. The member nodes compare the value of location func- tion within the cluster.
Member node having maximum value of location function and maximum energy will be elected as new cluster head.
New cluster head broadcast message of its selection. And then repeat step 10 to 16.
iv) Select integer e gcd(Ø(n),e)=1; 1<e<Ø(n)
v) Calculate d e*d=1modØ(n)
vi) Public key (e , n)
vii) Private key(d , n)
b) Signing Process (By Member Node and Cluster
Head)
i) Sensor node (sender node) create signature using own private key S=Md mod n where M is sensed data.
c) Encryption Process (By Member Node aNnd Cluster
Head)
i) Before sending the data and signature to sensor
18-
Data aggregation function will be implemented at
node (sender node) encrypt the
K=M(e*d)mod n
Ddata using
19-
each level by each node cluster head.
The same process will be applied again until the nodes in WSN are died.
ii) Now sensor node sends the encrypted data and
signature to the nearest node (ReceiveTr node).
d) Decryption and Verifying Process (By Member
Node and Cluster Head)
i) Nearest node (Receiver Node) receive the data
and signature and perform the decryption and
7 MODIFIED RSA DIGITAL SIGNATURE SCHEME
a) Key Generation Process (By Cluster Head)
i) Select p and q with the condition that p and q both prime and p does not equal to q.
ii) Calculate n=p*q
iii) Calculate Ø(n)=(p-1)*(q-1)
Protocol Description:
i) Find The Distance Between Each Node
verifying process P=Ke mod n if P = S then it verify the signature.
Calculate M= Pe mod n or M= Se mod n
ii) Find the Neighbors of Each Node
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 552
ISSN 2229-5518
iii) Find the Total Distance of Neighbors of Each Node
iv) Find the value of location function
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 553
ISSN 2229-5518
v) Formation of Cluster
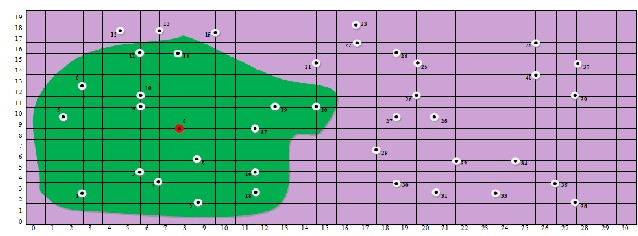
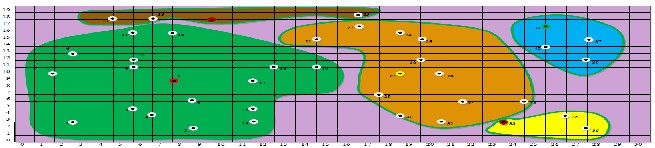
vi) Transmission of Data From Member Node to Cluster Head
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 554
ISSN 2229-5518
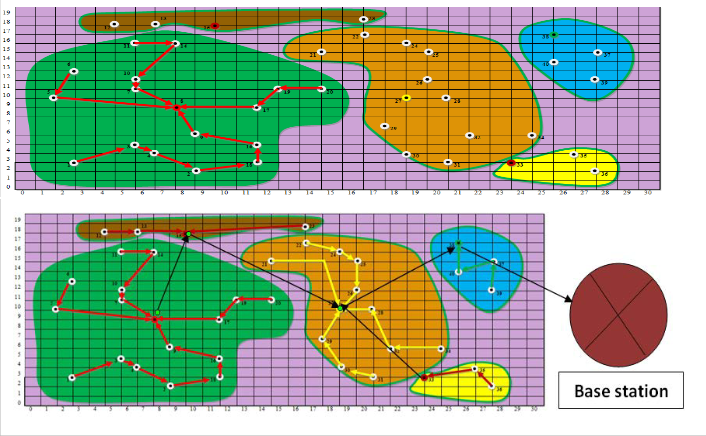
8 RESULT AND CONCLUSION
In this paper a secure strategy for high speed data transmis- sion and efficient data collection based on dijkstra algorithm for shortest path and selection of cluster head as well as clus- ter formation is proposed. Proposed technique also provide the security at the time of transmission .In order to evaluate the performance of technique, we will simulate it on 40 node network. The simulations will do in c++. The BS is located at (0,-100) in a field of diameter 100m. We will run the simulation to determine the round in which every node is died. Parame- ters using will be same as that of [12]. Once a node dies it is considered dead for the rest of simulation, and our results ex- pected to show much better system stable lifetime (period when all nodes of network are alive) because it balances ener- gy dissipation among sensor nodes by using all nodes as clus- ter head with equal priority (highest energy node and highest location value will serve as cluster head) thus maximizing sta- ble life time & achieves better results. We will implement in C++ to show the performance of our scheme.
REFERENCES
[1] “21 ideas for the 21st century”, Business Week, Aug. 30 1999, pp. 78-
167.
[2] S.K. Singh, M.P. Singh, and D.K. Singh, “A survey of Energy-Efficient Hierarchical Cluster-based Routing in Wireless Sensor Networks”, International Journal of Advanced Networking and Application (IJANA), Sept.–Oct. 2010, vol. 02, issue 02, pp. 570–580.
[3] S.K. Singh, M.P. Singh, and D.K. Singh, "Energy-efficient Homogene- ous Clustering Algorithm for Wireless Sensor Network", Internation- al Journal of Wireless & Mobile Networks (IJWMN), Aug.2010, vol. 2, no. 3, pp. 49-61.
[4] Jun Zheng and Abbas Jamalipour, “Wireless Sensor Networks: A
Networking Perspective”, a book published by A John & Sons, Inc, and IEEEE, 2009.
[5] W.R. Heinzelman, A. Chandrakasan, and H. Balakrishnan, “An Application-Specific Protocol Architecture for Wireless Microsen- sor Networks” in IEEE Tmnsactions on Wireless Communications (October 2002), vol. 1(4), pp. 660-670.
[6] S. Lindsey and C.S. Raghavendra, “PEGASIS: Power-efficient Gath- ering in Sensor Information System”, Proceedings IEEE Aerospace Conference, vol. 3, Big Sky, MT, Mar. 2002, pp. 1125-1130.
[7] Ossama Younis and Sonia Fahmy” Heed: A hybrid, Energy- efficient, Distributed Clustering Approach for Ad-hoc Networks”, IEEE Transactions on Mobile Computing, vol. 3, no. 4, Oct.-Dec. 2004, pp. 366-369.
[8] HO. Tan, “Power efficient data gathering and aggregation in wireless sensor networks,” SIGMOD Record, 2003, 32(4): 66 -71.
[9] Chi-Tsun Cheng, Chi K Tse, and Francis CM Lau. A delay-aware data collection network structure for wireless sensor networks. Sen- sors Journal, IEEE, 11(3):699–710, 2011.
[10] Chris Karlof and David Wagner. Secure routing in wireless sensor networks: Attacks and countermeasures. Elsevier’s AdHoc Net- works Journal, Special Issue on Sensor Network Applications and Protocols, vol. 1, issue 2-3, pages 293–315, September 2003.
[11] James Newsome, Elaine Shi, Dawn Song, and Adrian Perrig. The
sybil attack in sensor networks: analysis & defenses.In IPSN’04:
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 9, September-2014 555
ISSN 2229-5518
Proceedings of the third international symposium on Information processing in sensor networks, pages 259–268, New York, NY, USA,
2004. ACM Press.
[12] Anthony D. Wood and John A. Stankovic. Denial of service in sensor networks. IEEE Computer, vol. 35, issue 10, pages 54–62, 2002.
[13] T. S. Rappaport. Wireless Communications. Prentice-Hall, 1996.
[14] R. Steele. Mobile Radio Communications. Pentech Press, London,
1992.
[15] Vaibhav Sharma, Gulista Khan, Kamal Kr. Gola and Rahul Rathore “SECURITY STRATEGY FOR DYNAMIC HOMOGENEOUS WSN”IJARCSSE 3 (4),March - 2014,pp. 1-8
IJSER © 2014 http://www.ijser.org






