Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3 , Marc h -2012 1
ISSN 2229-5518
Recognition of mischievous data packets
In the networking
G.Bala Venkata Kishore, B.Purnaiah, B.kishore Babu, A.Siddharatha Reddy
Inde x Terms : Mobile ad hoc netw ork, Security Goals, eff icient scheme, security, public-key, cryptography, Traff ic validation, responses
—————————— ——————————
1 INTRODUCTION
TCP has pr ovided the pr imary means to transfer data r elia- bly acr oss the Inter net; how ever TCP has imposed limita- tions on several applications. Measur ement and estimation of packet loss char acteristics ar e challenging due to the r ela- tively r ar e occurr ence and typically shor t duration of pac k- et loss episodes. While active pr obe tools ar e commonly used to measur e packet loss on end-to end paths, ther e has been little analysis of the accuracy of these tools or their impact on the networ k. The main obj ective is to under stand the pr oblem of detecting whether a compr omised r outer is maliciously manipulating its str eam of packets. In partic u- lar to this concer n a simple yet effective attack in which a r outer selectively dr ops packets destined for some Victim. Unfor tunately, it is quite challenging to attr ibute a missing packet to a malicious action because nor mal networ k con- gestion can pr oduce the same effect .Such attacks ar e not mer e theor etical curiosities, but they ar e actively employed in pr actice. Attacker s have r epeatedly demonstrated their ability to compr omise r outers, thr ough combinations of social engineer ing and exploitation of w eak passwor ds and latent software vulner abilities . One networ k oper ator r e- cent ly documented Over 5,000 compr omised r outers as well as an under gr ound mar ket for tr ading Access to them sever al r esearchers has developed
Distr ibuted pr otocols. Detect such tr affic manipula
Tions typically by validating that tr affic transmitTed by one r outer is r eceived unmodified by another. How ever, all of these schemes including our own struggle in inter pr eting
the absence of traffic. Too many dr opped packets imply malicious intent How ever , this heuristic is fundamentally unsound; setting this thr eshold is, at best, an art and will certainly cr eate unnecessary false pos itives or mask highly focused attacks Inter net r outing is based on a distr ibuted system composed of many r outer s, gr ouped into manage- ment domains called Aut onomous Systems (ASes). Routing information is exchanged betw een A Ses in Bor der Gateway Pr otocol (BGP) [1] UPDATE messages. BGP has pr oven to be highly vulnerable to a variety of attacks [2], due to the lack of a scalable means of ver ifying the authenticity and legitimacy of BGP control tr affic. In Apr il 1997, we began wor k on the secur ity ar chitectur e described in this paper. In this section w e describe the pr oblem –how the pr otocol wor ks, the natur e of ob served BGP traffic in the Inter net, the corr ect operation of BGP, the thr eat model and BGP vulnerabilities, and the goals, constraints and assumptions that apply to the pr oposed countermeasur es.
2 B ack Ground
In the backgr ound we have ther e ar e tw o thr eats posed by a compr omised r outer. The attacker may subvert the networ k contr ol plane (e.g., by manipulating the r outing pr otocol into false r oute updates) or may subvert the networ k data plane and forward individual packets incorr ectly. The first sets of attacks have seen the widest inter est and the most activity lar gely due to their catastr ophic potential. By v i- olating the r outing pr otocol itself, an attacker may cause lar ge portions of the netw or k to become inoperable At the time that we began this wor k, pr eviously published wor k on impr oving the secur ity of BGP, and mor e genera lly dis- tance-vector pr otocols, included pr oposals for adding s e- quence number s to BGP messages authentic ation of BGP messages [1,5,6], neighbor-to-neighbor encryption of BGP messages [4], and adding information to UPDATE messa g-
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3 , Marc h -2012 2
ISSN 2229-5518
es to pr otect against tampering as the UPDATE pr opagates ar ound the Internet [4,5,7].None of this w or k pr oposed a compr ehensive solution to the BGP secur ity pr oblems de- scr ibed above; each focused on one or mor e a spects of the pr oblem w it hout considering the full range of issues that ar e cr itical to a viable solution. For example, none a d- dr essed issues associated with the generation and distrib u- tion of public key cer tificates and cer tificate r evocation lists (CRLs) needed to suppor t validation of signed UPDATEs. Some pr oposals made changes to BGP that ar e inconsistent with the pr otocol standards, a r easonable a ppr oach only if one w er e pr esented with a "clean slate." None of the prior wor k examined the statistics of BGP operating in the Inter- net; this sometimes led author s to focus on per formance concerns that ar e not the major impediment to deploying viable solutions. Some of the w or k developed solutions for distance vector pr otocols, but erroneously claimed applica- bility to BGP, w hich is descr ibed as a path vector pr otocol. In contrast, the BGP secur ity architectur e r eported in this paper is compr ehensive, including a design for the infra- structur e needed to establish and maintain the system. The optional transitive path attribute it employs is consistent with BGP standards and can be safely carried through r ou- ter s not implementing S-BGP. This ar chitectur e incorpor ates the notion of an addr ess attestation, which establishes that a "first hop" BGP speaker is authorized to advertise a r oute to a destination. No pr ior wor k includes an equivalent no- tion. Finally, the per formance of the design pr esented her e has been modeled based on actual BGP statistics. No other wor k has been so rigor ously analyzed fr om a per formance perspective.
In building a traffic validation pr otocol, it is necessary to explicitly r esolve the ambiguity ar ound packet losses. Should the absence of a given packet be seen as malicious or In practice ther e ar e thr ee appr oaches for addr essing this issue:
.
tion pr ot ocols, including WATCHERS Secur e Trace r oute [12], and our own w or k described in [4], analyzes aggr egate traffic over some per iod of time in or der to amortize mon i- tor ing over head over many packets. For example, one val i- dation pr otocol descr ibed in [4] maintains packet counters in each r outer to detect if traffic flow is not conserved fr om sour ce to destination. When a packet arr ives at r outer r and is forwarded to a destination that w ill tr averse a path seg- ment ending at r outer x, r incr ements an outb ound counter associated w ith r outer x. Convers ely, when a packet arr ives at r outer r, via a path segment beginning with r outer x, it incr ements its inbound counter associated with r outer x. periodically, router x sends a copy of its outbound cou nters to the associated r outers for validation. Then, a given r outer r can compar e the number of packets that x claims to have sent to r w ith the number of Packets it counts as being r e- ceived fr om x, and it can detect the number of packet losses. Thus, over some time w indow, a r outer simply knows that out of m packets sent, n wer e successfully r e- ceived. To addr ess congestion ambiguity, all of these sys- tems employ a pr edefined thr eshold: if mor e than this number is dr opped in a time interval, then one assumes that some r outer is compr omised. How ever , this heur istic is fundamentally flawed: how does one choose the thr eshold? In or der to avoid false positives, the thr eshold must be lar ge enough to include the maximum number of possible congestive legitimate packet losses over a measur ement interval. Thus, any compr omised r outer can dr op that many packets without being detected. Unfortunately, given the natur e of the dominant TCP, even small numbers of losses can have significant impacts. Subtle attackers can selectively tar get the tr affic flows of a single victim and within these flows only dr op those packets that cause the most har m. For example, losing a TCP SYN packet used in connection establishment has a dispr opor tionate impact on a host because the r etr ansmission time-out must necessarily be ver y long (typically 3 seconds or mor e). Other seemin gly minor attacks that cause TCP time-outs can have similar effects a class of attacks All things consider ed, it is clear that the static thr eshold mechanism is inadequate since it allows an attacker to mount vigor ous attacks without being de- tected. Instead of using a static thr eshold,then one could r esolve ambiguities by compar ing measur ed loss r ates to the r ates pr edicted by the model. One a pproach for doing this is to pr edict congestion analytically as a function of individual traffic flow parameter s, since TCP explicitly r e- sponds to congestion. Indeed, the behavior of TCP has been excessively studied A simplified1 stochastic model of TCP congestion contr ol.
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3 , Marc h -2012 3
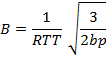
ISSN 2229-5518
Sending r eceiving
Packets Packets
pr otocol to pr ovide each node w ith a global view of the curr ent netw or k topology. Finally, we assume the adminis- trative ability to assign and distr ibute cryptogr aphic keys to sets of nearby r outer s. This overall model is consistent w ith the typical construction of lar ge enterpr ise IP networ ks or the inter nal str uctur e of single ISP backbone networ ks but is not well suited for netw or ks that ar e composed of mu l- tiple administrative domains using BGP. At this level of
abstraction, w e can assume a synchr onous netw or k mod-
Sourc
e
Receiving
Rou- ter
Desti- nation
el.W e defin of adj acent r outers. Operationally, a path de- fines a sequence of r outers a packet can follow . We call the first r outer of the path the source and the last r outer its sink; together , these ar e called terminal r outers. A path might consist of only one r outer , in wh ich case the sour ce and sink ar e the same. Terminal r outer s ar e leaf r outers:
Acknowledgement sending
Acknow ledgement
Fig 1: f low of data f rom source to destination
they ar e never in the middle of any path.
Rs1
Rs2
The Pr otocol x detects tr affic faulty r outer s by validating the queue of each output inter face for each r outer . Given the buffer size and the rate at which tra ffic enters and exits
Q a queue, the behavior of the queue is deterministic. If the
actual behavior deviates fr om the pr edicted behavior , then Rd a failur e has occurr ed. W e pr esent the failur e detection pr o- tocol in ter ms of the solutions of the distinct sub pr oblems:
R traffic validation, distr ibuted detection, and r esponse.and the corr ectness of the pr otocol
Rsn
Fig 2: validating of queue of the output interf ace
4 Network Model
We have to consider a networ k to consist of individual h o- mogeneous r outers interconnected via dir ectional point- topoint links. This model is an intentional simplification of r eal netw or ks (e.g., it does not include br oadcast channels or independently failing netw or k inter faces) but is suffi- ciently gener al to encompass such details if necessary. Un- like our ear lier w or k, w e assume that the bandwidth, the delay of each link, and the queue limit for each inter face ar e all known publicly. W ithin a networ k, w e pr esume that packets ar e forwarded in a hop-by-hop fashion, based on a local forwar ding table. These forwarding tables ar e u p- dated via a distr ibuted link-state r outing pr ot ocol such as OSPF or IS-IS. This is critical, as w e depend on the r outing
The packet with fingerpr int fp and size ps is dr opped at time ts when the pr edicted queue length is q then w e raise an alarm with a confidence value csingle, which is the pr obability of the packet being dr opped maliciously. Csin- gle is the mean and standard deviation of X can be deter- mined by monitor ing dur ing a lear ning period. W e do not expect and to change much over time, b ecause they ar e in turn deter mined by va lues that those selves do not change much over time. Hence, the learning period need not be done very often. A malicious r outer is detected if the confi- dence value csingle is at least as lar ge as a tar get signific- ance level slevel single.
The Traffic validation of the failur e of detecting malicious attack by TV r esults in a false negative, and any misdetec-
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3 , Marc h -2012 4
ISSN 2229-5518
tion of legitimate behavior by TV r esults in a false posi- tive.W ithin the given system model of Section the example TV pr edicate is corr ect. How ever , the system model is still simplistic. In a r eal r outer , packets may be legitimately dr opped due to r easons other than congestion err ors in hardwar e, softwar e or memory, and transient link err ors. Classifying these as arising fr om a r outer being compr o- mised might be a pr oblem, especially if they ar e infr equent enough that they w ould be best ignor ed rather than war- ranting r epairs the r outer or link. A lar ger concern is the simple way that a r outer isModeled in how it i nternally multiplexes packets. This model is used to compute time stamps. If the time stamps ar e incorr ect, then TV could de- cide incorr ectly. We hypothesize that a sufficiently accurate timing model of a r outer is attainable but have yet to show this to be the case. A third concern is with clock synchr on i- zation. This version of TV r equir es that all the r outers feed- ing a queuehave synchr onized clocks. This r equir ement is needed in or der to ensur e that the packets ar e inter leaved corr ectly by the model of the router .The synchr onization r equir ement is not necessar ily Daunting; the tight synchr o- nization is only r equir ed by r outers adjacent to the same r outer . W ith low-level time stamping of packets and r e- peated exchanges of time it should be straightforwar d to synchr onize the clocks sufficiently tightly. Other r epr esen- tations of collected traffic information and TV that we have consider ed has their own pr oblems with false positives and false negatives. It is an open question as to the best way to r epr esent TV. W e suspect any r epr esentation will admit some false positives or false negatives.
This paper pr esent to differ ence betw een a r outer dr op- ping packets maliciously and a r outer dr opping packets due to congestion this issue using a static user-defined thr e- shold, which is fundamentally limiting. The same fr am e- wor k as our ear lier wor k which is based on a static user- defined thr eshold a compromised r outer detection pr ot ocol that dy namically infer s based on measur ed tr affic r ates and buffer sizes. The number of congestive packet losses that
will occur. Subsequent packet losses can be attr ibuted to malicious actions. Because of non determinism intr oduced by imper fectly synchronized clocks and scheduling delays, pr otocol uses user-defined significance levels but these le- vels ar e independent of the pr operties of the tr affic.
[1] R. Tho mas, ISP Security BOF, NANOG 28, http://w ww .nanog org/mtg-0306/pdf /thomas.pdf , June 2003.
[2] K.A. Bradley, S. Cheung, N. Puketza, B. Mukherjee, and R.A. Ols- son, “Detecting Disruptive Routers: A Distributed Netw ork Monitoring Approach,” Proc. IEEE Symp. Security and Pr ivacy (S&P ’98), pp. 115-
124, May 1998.
[3] A.T. Mizrak, Y.-C. Cheng, K. Marzullo, and S. Savage, “Detecting and Isolating Malicious Routers,” IEEE Trans. Dependable and Se- cure Computing, vol. 3, no. 3, pp. 230-244, July-Sept. 2006.
[4] L. Subramanian, V. Roth, I. Sto ica, S. Shenker, and R. Katz, “ Listen and Whisper: Security Mechanisms f or BGP,” Proc. First Symp.Netw orked Systems Design and Imple mentation (NSDI ’04), Mar. 2004.
[5] S. Kent, C. Lynn, J. Mikkelson, and K. Seo, “Secure Border Gate- w ay Protocol (Secure-BGP),” IEEE J. Se lected Areas in Comm.,vol.
18, no. 4, pp. 582-592, Apr. 2000.
[6] Y.-C. Hu, A. Perrig, and D.B. Johnson, “Ariadne: A Secure On-
De mand Routing Protocol f or Ad Hoc Netw orks,” Proc. ACM MobiCo m
’02, Sept. 2002.
[7] B.R. Smith and J. Garcia-Luna-Aceves, “Securing the BorderGate-
w ay Routing Protocol,” Proc. IEEE Global Internet, Nov. 1996.
[8] S. Cheung, “An Eff icient Message Authentication Scheme f or LinkState Routing,” Proc. 13th Ann. Computer Security Applications Conf .(ACSAC ’97), pp. 90-98, 1997.
[9] M.T. Goodrich, Ef f icient and Secure Netw ork Routing Algorithms, provisional patent f iling, Jan. 2001.
[10] R. Perlman, “Netw ork Layer Protocols w ith Byzantine Robust-
ness,”PhD dissertation, MIT LCS TR-429, Oct. 1988.
[11] V.N. Padmanabhan and D. Simon, “Secure Traceroute to Detect Faulty or Malicious outing,” SIGCOMM Co mputer Co mm. Rev.,vol. 33, no. 1, pp. 77-82, 2003.
[12] I. Avramopoulos and J. Rexf ord, “Stealth Probing: Ef f icient DataP-
lane Security f or IP Routing,” Proc. USENIX Ann. Tecnical
Conf .(USENIX ’06), June 2006.
IJSER © 2012