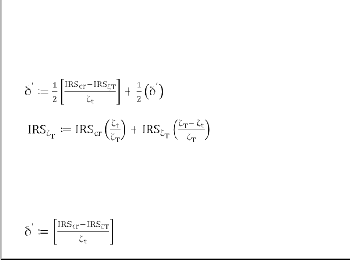The research paper published by IJSER journal is about QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach 1
ISSN 2229-5518
QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach
K.Swathi, M.Vijaya Lakshmi, Ch.Ganapathy Reddy
Abstract:- Here in this paper a MAC layer level overcrowding detection system has been projected. The planned model aims to distribute an energy efficient mechanism to compute the degree of congestion at victim node with maximal accuracy. This congestion detec tion apparatus is integrated with a Two-Step Cross Layer Congestion Control Routing Protocol. The proposed model involves controlling of congestion in two steps with effective energy capable blocking detection and optimal consumption of resources. Packet loss in network routing is primarily due to link failure and congestion. Most of the existing congestion control solutions do not have the ability to distinguish between packet loss due to link collapse and packet loss due to congestion. As a result these solution s aim towards action against packet drop due to link malfunction which is an unnecessary effort and may product in loss of resources. The other limit in most of the accessible solution is the utilization of energy and resources to detect blockage state, degree of conge stion and alert the source node about blocking in routing path. Here in this paper we suggest cross layered model of congestion recognition an control mechanism that incl ude energy efficient congestion detection, Intra level Congestion Evaluation Algorit hm [ICEA] and Intra level Egress Regularization Algorithm [IERA], which is a hierarchical cross layer based blocking detection and control model in short we refer this protocol as CDC -CPF(Congestion Detection and organize with Control Plane Functionality). This paper is supported by the investigational and simulation results show that better store utilization, energy efficiency in congestion detection and congestion control is possible by the proposed protoc ol.
Index Terms— Ad-hoc networks, MANETS, congestion,cross-layer design, optimization, random access, wireless network
—————————— ——————————
1 INTRODUCTION
he regular TCP jamming control mostly adapted for internet is not an apposite for MANETs because MA-
NETs are known to affect protocol and protocol stacks
of control mechanisms .also the MANETs are environmen-
tally irreconcilable with standard TCP [17].
The packet rescue delays and losses in MANETs are pri-
marily due to their node mobility combined with intrinsi- cally unexpected medium which is a direct consequence of the common wireless multi hop channel cannot be construe as congestion losses [17].
The primary individuality of a wireless multi hop
channel is that within interfering range of one node only a single data is transmitted .In MANETs‘ networks in an complete area are congested due to shared standard where as internet congestion is single router[17].A note valuable point is that in a MANET the nodes are not over- crowded[17].The main reason for the incompatible of a regular TCP and a MANET is the fact that package losses in MANET may not always be due to network congestion and the transmission times (including the round trip times) vary highly making the package losses quite difficult to observe
It is difficult to find the source of congestion in a multi hop network because a single user has the capability to produce a congestion resulting in comparatively lower bandwidth of mobile ad-hoc networks .The wireless networks are more susceptible to congestion problems when compared with the traditional wire line network.

K.Swathi, is currently pursuing M.Tech degree in Digital Electronics
& Communication Engineering from GNITS (affiliated College to

Jawaharlal Nehru Technological University, Hyderabad), India.
M.Vijaya Lakshmi, is working as associate professor
GNITS,(affiliated College to Jawaharlal Nehru Technological Univer-

sity, Hyderabad), India.
Ch.Ganapathy Reddy, HOD, ECE, GNITS,Hyderabad,India
Therefore a balanced congestion control system is to be
employed compulsorily for the stability and superior per-
formance [17] of a wireless network. The non homogene-
ous nature of the application protocols in the multihop
wireless networks, a single and unified solution for the congestion related problems cannot be obtained .Instead a suitable congestion control depending upon the properties and functions of the related network[17] can be designed
.As a result ,these proposal majorly form a subset of solu-
tions for the identified problems rather than a complete
,instantly used protocol . They pose as a parent for ap-
plication-tailored protocol stacks. Exceptionally , few of
the protocol properties serve wide range of applica- tions[17].
The recent years have witness a much more focus on the congestion control methods directed on the model- ing, analysis, algorithm development of closed loop control schemes (e.g. TCP) making them sympathetic for adaption to the mobile hoc networks .under the provision of con- straints of routing path and bandwidth algorithms possess- ing the ability to unify and stabilize operation have been evolved .Another major constraint to be painstaking in a wireless hoc network is due to the MAC[Media access Con- trol) layer [17].Majority of wireless MACs possess a time constriction permitting a single user to access a physical channel at a given time.
The sections in the paper are organized to provide the following details as regards. The section2 explores the most cited works in the area of text .section3 gives a detail dis-
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach 2
ISSN 2229-5518
cussion of the projected protocol and section 4 relies on the simulation and their results to be consummate by conclu- sion and references.
1.1 Related Work
QoS centric jamming control solution can be found in [1]. Metrics based solution for blockage aware routing was proposed in[4]. Et al., [2] introduced metrics to evaluate data-rate, MAC transparency and buffer delay, which helps to identify and deal the blocking contention area in network. Hongqiang Zhai, et al., [3] planned a solution by arguing that congestion and severe medium debate is in- terrelated. Yung Yi et al., [4] proposed a hop level blockage control model. Tom Goff, Nael et al., [5] discussed a set of algorithms that initiates different path usage when the quality of a path in use becomes suspect. Xuyang et al., [6] present a cross-layer hop-by-hop congestion control scheme planned to improve TCP performance in multihop wireless networks. Dzmitry et al [7] presents the impact blocking on transport layer that decreases the performance. Duc et al.[8] proposed that current designs for routing are not adjustable to congestion.
The existing models aim at identify congestion
losses in routing path .The packet loss generate a link fail-
ure. Making efforts to manage the packet losses that cause
link failure are in effective. Another exclusive approach is
regularizing the egress at all nodes participating in routing. In majority of cases of control the congestion at hop level [4][15]. Henceforth egress regularization at each node of the network involves operation of expensive wealth.. Here in this paper we argue that it is a important to identify the reason for packet loss. Hence we can avoid the blockage control process via egress regularization under the status of link failure. And also we continue the spat that hop lev- el blocking control alone is not plenty when the hop levels are unable to normalize themselves. The egress load to con- trol the blocking by utilizing the same resources can be done as in spring level egress regularization models. In this situation in our previous work we proposed a Two- Step Cross Layer blocking Control Routing Protocol [18].
Here we propose a new energy efficient cross
layer based blocking control routing protocol that contains
Congestion detection and congestion control models.
2 CROSS LAYER DESIGN WITH CONTROL PLANE FUNCTIONALITY IN MULTI HOP WIRELESS NETWORKS FOR EFFECTIVE BLOCKING CONTROL
2.1 Energy resourceful Congestion detection mechanism
The aim of the proposed congestion detection device is to capture degree of congestion at relay hop level node with maximal accuracy. In proposed model, the detection me- chanism is decoupled from other activities of the MAC layer such as link consistency analysis and buffer size analysis. The recognition model extended to detect the congestion at traffic level, which is based on the degree of
congestion quantity at relay hop level node.
2.2 Measuring degree of blockage at Relay hop level node
Unlike conventional networks, nodes in the ad hoc net- work exhibit a high degree of heterogeneity in terms of both hardware and software configurations. The hetero- geneity of the relay hop nodes can reflect as varied radio range, maximum retransmission counts, and barrier capac- ity. Hence the degree of waterway loading, packet drop rate, and degree of buffer consumption at relay hop level node is minimum combination to find the degree of con- gestion. The usage of these three purposeful values sup- ports to decouple the congestion measure process from other MAC layer behavior.
The degree of channel load, packet drop rate and
degree of buffer operation together provide a scope to en-
visage the blocking due to inappropriate ratio between
collision and retransmission count. When retransmissions compared to collision rate are significantly low then egress delay of relay hop node will increase proportionally, which leads to congestion and reflected as congestion due to buf- fer overflow.
2.3 Measuring degree of congestion at path level traffic
The degree of congestion at each relay hop together helps to identify the degree of congestion at path level traffic from source to goal node. Each relay hop level node rece- ives the degree of congestion from its doorway architect. Since the destination node, which is last node of the course-plotting path is not egress the emptiness status. Hence the destination node initiates to assess the degree of congestion at path level traffic. The interrupted updates of congestion status at each relay hop level node to it‘s heir in routing path is significantly energy consuming activity. Hence to conserve the energy, the congestion update strat- egy considers two conditional activities, which follows:
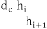
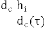
1. Degree of blocking ( ) at relay hop level node hi will be sent to its successor if the ( ) is greater than
the node level blockage threshold . Hence the energy conserves due to conditional transmission.
2. If degree of blocking at path level traffic 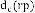 that re- ceived by node from its doorway initiator
that re- ceived by node from its doorway initiator 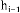 is smaller than
is smaller than  ( ) then it update the
( ) then it update the 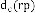 else it re- mains same, hence energy conserve due to prevention of
else it re- mains same, hence energy conserve due to prevention of 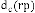 update.
update.
3 CROSS LAYER CONGESTION CONTROL MODEL

The packet dipping often occurs in Manets. The reasons for this packet plummeting are as below
Transmission Link failure.
Inferred Transmission due to weighed down Ingress that leads Ingress getting strength to low. This also can claim as packet dropping due to blocking at routing.
The congestion control can be evaluated in two stages by
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach 3
ISSN 2229-5518

turning over of the zonal head with the network parti- tioned into Cells as follows
The Status of blocking at intra Cell level
For each Cell i, where i
of Cells)

1.. | Z | ; (| Z | is entirety number
The status of jamming at inter Cell level
This helps in minimization of source level egress regula- tion cost and balances the power consumption.
TABLE 1
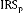
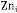
NOTATIONS USED IN PROPOSED MODEL
o Select Cell-head for each Cell i
o Find spread load threshold ζn for each Cell i.
By using ζn of each Cell spread load threshold for entire network can be measured.
3.2 Splitting the network into Cells:
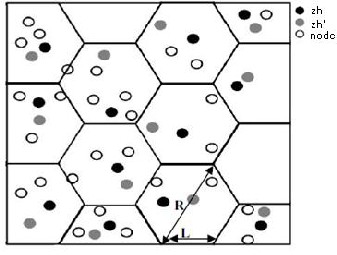
We opt to the approach described by Mohammad M. Qa- bajeh et al[8]. With the knowledge of the presented nodes the region is divided into equal partitions. Hexagon is mostly chased for the zonal shape because it covers a high- est surface and also provides the improvement of commu- nicating with more neighbors as they have near circular shape of the transmitter. The availability of small, econom- ical low power GPS receiver makes it possible to apply position-based in MANETs. The communication range of node is denote as R and the side of hexagon as L.As the nodes should be able to correspond with each other the R and L are related as L=R/2.
Each Cell has a Cell characteristics (Zid), Cell Header (Zh) and Cell Leader Backup (Zh'). The Zh node maintains in sequence about all the nodes in a Cell with their positions and IDs. Also, maintain information about the Zh of the neighboring Cells as shown in the figure 1. The CLB node keeps a copy of the data stored at the Zh so that it is not lost when the Zh node is off or touching the Cell. By knowing the coordinates of a node position, nodes can perform our self-mapping algorithm of their physical locations onto the current Cell and calculate its Zid easily. Figure 1.shows the general overview of the network archi- tecture.
3.3 Selecting Cell-Heads
A Cell-Head selection occur under the pressure of the
Following metrics:
a. Node positions: A node with a position p that is close
to the centre is more likely to act as a Cell head.
b. Optimum energy available: a node with higher ener-
gy e more probably acts as a Cell head.
c. Computational ability: the node with high computa-
tional ability c is more possible to act as a Cell Head.
d. Low mobility: the mobility m of a node is inversly
proportional to its selection as a Cell head.
Each node of the Cell broadcasts its (p,e,c,m). The node
that identified itself as most optimal in (p,e,c,m) metrics,
announces itself as Cell head Zh. The next optimal node in sequence claims itself as reserve Cell head Zh'.
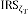
3.1 Network and Node activities under projected protocol
The network is to be crack into Cells.
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach 4

ISSN 2229-5518
IRS ζT = IRScr
Endif
Detecting packet drop at Mac layer level
IRSce IRSζT +δ'ζet
if (IRSce < IRSr) do
MacAlert: link-failure else
MacAlert: congestion
Endif
Fig2: ICEA for determining congestion caused packet dropping
Figure 1[8]: General overview of the Cell partitions in network.
3.4 Information sharing at intra Cell level [ between
Node and Cell head]
Each node n that is a subset to Cell Z verifies the Ingress load and shares degree of ingress load diln with Cell head. Once ndilk received from each node k of the Cell i, the Cell head zh calculates the degree of ingress load at Cell level zdili.


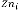
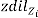
3.5 Intra level Congestion Evaluation Algorithm
(ICEA)
3.6 Intra level Egress Regularization Algorithm
(IERA)
This event occurs if Mac-layer alert indicates the conges- tion circumstance. Once the routing protocol [13] gets an alert from the Mac layer a propos the blocking at a node i, it alerts the fellow citizen node which is the source node s for conflict node i. Hence s evaluates it‘s dils by comparing with zdil of Zc(Cell of the node s). If dils is more in magni- tude than 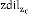 the variation between dils and
the variation between dils and 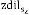 should
should
be either greater or equal to the egress threshold Ɛ then
node s regularizes the egress load by manipulate its buffer

time BTs such that 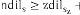 .
.
Here ε can be calculated with following equation

zn j
Intra level Congestion Evaluation Algorithm abbreviated as ICEA is presented in this section. ICEA is an optimal
zdil j
k 1
zn j
dilk
algorithm that helps in locating the packet dropping under
congestion. This evaluation occurs under Mac layer and
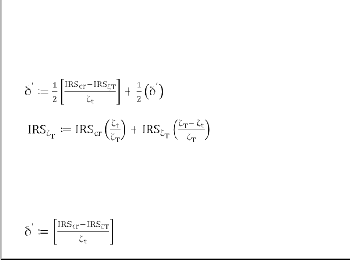
then alerts network layer.
At an event of ingress receiving by node i :
Updating Ingress receiving strength:
if (ζt < ζT) do
In case that the node s not able to normalize its egress so that disagreement node i terminates blocking then it alerts
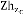
the 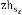 (Cell-head of theZc,SεZc). subsequent that event
(Cell-head of theZc,SεZc). subsequent that event
alerts all the nodes in the network building the all
nodes in the upstream of source node to way out load us- ing the above stated slant. Then all nodes update their ndil and send to Cell-head 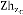 , then Cell-head
, then Cell-head 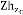 calculate Zdil and confirms integrity of the Zdil by evaluation with
calculate Zdil and confirms integrity of the Zdil by evaluation with
dil.
zdil
c
dil

concludes that congestion at conten-
tion node maintained by egress regularization at current
zdilz
Cell level. If c
dil

then CEA will be started at
endif
if (ζt ˂ ζT) do
Zp, which is adjacent upstream Cell to Zc in transmissible . In this process Cell head of the Zc firstly alerts the Cell head of the counterpart Zp then 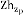 alerts all nodes that belongs to Zp, of the route path. The above procedure of egress regularization at Cell level can be referred as IERA (Intra level Egress Regularization Algorithm). Hence the nodes belong to Zp regularize their egress load by utilize
alerts all nodes that belongs to Zp, of the route path. The above procedure of egress regularization at Cell level can be referred as IERA (Intra level Egress Regularization Algorithm). Hence the nodes belong to Zp regularize their egress load by utilize
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach 5
ISSN 2229-5518
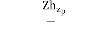
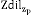
IERA and alert Cell-head about their efficient degree of ingress load ndil. Then measures and verifies the
zdilZ
result of p
dil
.True indicates the elimination
or minimization of congestion at the Cell due to the egress
zdilZ
If c
dil ( zdilZ
and c
dil )
begin
regularization at Cell Zp, if false then Cell head of the Zp
performs the action of alerting all other Cell heads using a

broadcasting[12] instrument about the congestion at adja- cent Cell in downstream of the heridetary. Hence all Cells in the upstream side of the Zp apply IERA and the Cells in downstream side of the Zp fill in theirZdil. Then all Cells broadcast Zdil to resource Cell. Hence the source Cell reva- luates the dil .Based on the dil , source node regularize its egress load.
Notations used in Algorithm:
i: Node that effected by congestion s: source node of the i.
Zc: current zone where i,s ϵ Zc
Zp: Immediate zone to Zc in upstream side of the hie-
rarchy.
{ nu1, nu2,…, nuk }zc: All upstream nodes to s
{ nd1, nd2,…, ndk }zc: All downstream nodes to s.
Alert: blocking at contention node handle at current Cell
Z c level. Return. Endif
Alerts
Alerts all nodes that belong to Cell Zp
For each node n ϵ Zp begin
If and begin
BTn= BTn +bt
Note: Value of barrier threshold bt should be decided
such that diln
Endif
Find diln and send diln to
End-of-for each measures
{ Zs,Zu1,Zu2,.....,Zuk }: Set of upstream zones to Zp in routing path, here Zs is a zone that contains source node of the
if and
(zdil
p
dil)
begin
routing path
{Zd1, Zd2,.., Zdm,..., Zt } : Set of downstream zones to Zp in routing path, here Zt is a zone that contains
target node of the routing path
Ɛ : Cell level egress threshold
: Network level Egress threshold
Algorithm:
Mac layer alerts about the blocking at node of Cell Zc to routing protocol, hence the following steps perform in
sequence
=
complete following at node S
Alert: Egress regularization at Zp leads to overcome con- gestion situation at contention Cell.
Return; Endif
Alerts all Cell heads in network regarding congestion
contention Cell.
{Z , Z , Z ,..., Z }
For each Cell z in S u1 u 2 uk begin
Zhz Alerts all nodes that belongs to Cell z
For each node n ε z begin
If ndiln> zdilz and (ndiln - zdilz ) ϵ z begin
BTn= BTn +bt
Note: Value of barrier threshold bt should be understood
If ndils > and ndils ‒ begin
BTs = BTs + bt
such that diln
Endif
zdilz z
Note: Value of buffer threshold bt should be certain such
that dils Return. Endif
s sends alert to about contention node i.
alerts all nodes that belongs to zone
1) {nu1, nu2,..., nuk} updates their ndil by apply IERA re- cursively and alerts
Find diln and send diln to Zhz
End-of-foreach
Zhz measures Zdilz and broadcast towards source Cell. End-of-foreach
{Z , Z ,..., Z ,..., Z }
For each Cell z in d 1 d 2 dm T begin
For each node n belongs to Cell z begin determine ndiln and sends to Zhz
End-of-foreach
Zhz measures Zdilz as
znz
{nd1, nd2,..., ndk} measures their ndil and alerts
zdilz
ndilk k 1

Measures zdil as fallows
znz
Zhz Sends Zdilz to source Cell via propagation [12] End-of-foreach
ZS Measures dil as
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach 6

ISSN 2229-5518
|Z|
zdili
cos tch

E
cte
e 1
dil
i 1
|Z|
Here 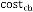 is the price of a blockage controlling activity
is the price of a blockage controlling activity
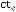
ch,E is total amount of events included. is the threshold
Hence source node S of Cell ZS, which is source node of
the routing path regularize it‘s egress load to direction-
finding path. Hence source node S of t‘s egress laod to
direction finding path.
Fig 3: Intra level Egress Regularization Algorithm
4 SIMULATIONS AND RESULTS DISCUSSION
In this section we discuss the outcome acquired from simu- lation conducted using ‗Madhoc simulator‘ [16] in this sec- tion. We evaluated concert using madhoc with the follow- ing considerations:
cost of an event e. The example events are:
1.‖ alert to source node from Mac layer‖
2. ―Alert from node to Cell head‖, ―propagation by Cell head to other Cell heads‖
3. ―Ingress judgment and egress regularization‖.
4. Alert about
5. bring up to date
TABLE 2
PARAMETERS USED IN MADHOC [16] FOR PERFORMANCE ANALSIS
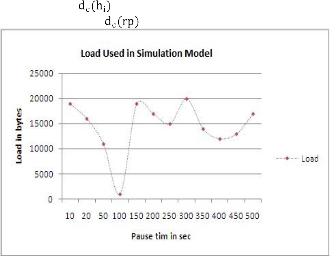
Fig 4: Load in bytes drive by source node of the routing path [in regu- lar interval of 10 sec]
5 CONCLUSION
The simulations are conducted on three routes differing by the no of hops and length.
a. Short length path: A route with 15 hops
b. middling length : A route with 40 hops
c. Max Length: A route with 81 hops
The same load is given to all the paths with a regular inter-
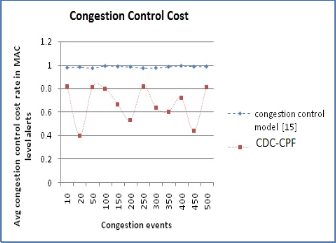
val of 10 sec. Load given in kilo bytes are shown in fig 4. The fig 5 concludes the improvement of CDC-CPF over congestion control protocol[15] in blockage control cost. A. The congestion detection cost evaluation between CDC- CPF and congestion control protocol[15] is explore in fig 6 that elevates the energy good organization achieved under CDC-CPF.
The process of capacity of congestion control and conges-
tion detection cost is as follows:
Based on the resource ease of use, bandwidth and energy,
for individual operation a threshold value between 0 and 1
assigned. In the mechanism of congestion detection and control the total cost is calculated by summing the cost threshold of every involved event. In fig 5 the judgment between congestion costs observed for CDC-CPF and jamming and contention control model [15] are shown.
This manuscript discussed about proposed ―Energy Effi- cient Cross layered blocking Detection and Control Routing Protocol‖ in short referred as CDC- CPF(Congestion Detection and have power over with Con- trol seaplane Functionality). CDC-CPF derived a cross layered congestion detection mechanism with energy effec- tiveness as primary criteria that included as congestion detection mechanism to our earlier work ―Two step cross layer congestion routing‖[18] .
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about QOS Optimization for Hierarchical Zones Structure Based Multi Cast Routing: A Two Level Congestion Control Approach 7
ISSN 2229-5518
Fig 5: Congestion Control cost comparison chart
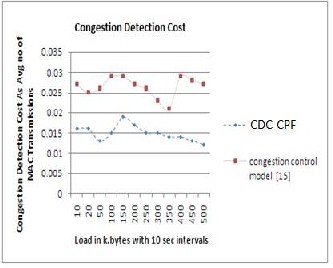
Fig 6: A line chart comparison of Congestion detection cost
REFERENCES
[1] Michael Gerharz, Christian de Waal, and Matthias Frank, ―A Prac- tical View on Quality-of-Service Support in Wireless Ad Hoc Ne t- works‖, BMBF
[2] Xiaoqin Chen, Haley M. Jones, A .D .S. Jayalath, ―Cogestion-Aware
Routing Protocol for Mobile Ad Hoc Networks‖, IEEE, 2007
[3] Hongqiang Zhai, Xiang Chen, and Yuguang Fang, ―Improving Transport Layer Performance in Multihop Ad Hoc Networks by E x- ploiting MAC Layer Information‖, IEEE, 2007
[4] Yung Yi, and Sanjay Shakkottai, ―Hop-by-Hop Congestion Control
Over a Wireless Multi-Hop Network‖, IEEE, 2007
[5] Tom Goff, Nael B. Abu-Ghazaleh, Dhananjay S. Phatak and Ridvan Kahvecioglu, ―Preemptive Routing in Ad Hoc Networks‖, ACM, 2001 [6] Xuyang Wang and Dmitri Perkins, ―Cross-layer Hop-byhop Con- gestion Control in Mobile Ad Hoc Networks‖, IEEE, 2008.
[7] Dzmitry Kliazovich, Fabrizio Granelli, ―Cross-layer Congestion
Control in Ad hoc Wireless Networks,‖ Elsevier, 2005
[8] Duc A. Tran and Harish Raghavendra, ―Congestion Adaptive
Routing in Mobile Ad Hoc Networks‖, 2006
[9] Nishant Gupta, Samir R. Das. Energy-Aware On-Demand Routing for Mobile Ad Hoc Networks, OPNET Technologies, Inc. 7255 Woo d- mont Avenue Bethesda, MD 20814 U.S.A., Computer Science Depart- ment SUNY at Stony Brook Stony Brook, NY 11794-4400 U.S.A.
[10] Laura, Energy Consumption Model for performance analysis of routing protocols in MANET,Journal of mobile networks and applica- tion 2000.
[11] LIXin MIAO Jian –song, A new traffic allocation algorithm in AD
hoc networks, ―The Journal of ChinaUniversity of Post and Teleco m- munication‖, Volume 13. Issue3. September 2006.
[12] Chun-Yuan Chiu; Wu, E.H.-K.; Gen-Huey Chen; "A Reliable and
Efficient MAC Layer Broadcast Protocol for Mobile Ad Hoc Ne t- works," Vehicular Technology, IEEE Transactions on , vol.56, no.4, pp.2296-2305, July 2007
[13] Giovanidis, A. Stanczak, S., Fraunhofer Inst. for Telecommun.,
Heinrich Hertz Inst., Berlin, Germany This paper appears in: 7th I n- ternational Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks, 2009. WiOPT 2009
[14] O

 gue, R.; Inst. of Fundamental Elec- tron., Univ. Paris-Sud 11, Orsay, France This paper appears in: 2010
gue, R.; Inst. of Fundamental Elec- tron., Univ. Paris-Sud 11, Orsay, France This paper appears in: 2010
IEEE 29th International Performance Computing and Communic a-
tions Conference (IPCCC)
[15] Yingqun Yu; Giannakis, G.B.; , "Cross-layer congestion and con-
tention control for wireless ad hoc networks," Wireless Communic a-
tions, IEEE Transactions on , vol.7, no.1, pp.37-42, Jan. 2008 [16] http://www-lih.univ-lehavre.fr/~hogie/madhoc/
[17] Prof.K.Srinivas and Prof.A.A.Chari. Article: Cross Layer Conge s- tion Control in MANETs and Current State of Art. International Jou r- nal of Computer Applications 29(6):28-35, September 2011. Published by Foundation of Computer Science, New York, USA
[18] Prof. K. Srinivas, Dr. A. A. Chari;"ICEA&IERA: Two-Step Cross
Layer Congestion Control Routing Protocol (pp. 36-44)", Vol. 9 No. 12
December 2011 International Journal of Computer Science and Info r-
mation Security
IJSER © 2012
http://www.ijser.org