Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 2, Fe bruary -2012 1
ISSN 2229-5518
Priority Based Routing in Mobile Ad-hoc
Jiwan Pokharel, Santosh Bhandari, Saroj Sharma,Prof. S. Venkateswarlu
Abstract— A mobile Ad hoc netw ork is a collection of w ireless mobile nodes f orming a netw ork w ithout using any existing infrastructure. All mobile nodes function as mobile routers that discover and maintain routes to other mobile nodes of the netw ork and can be connected dynamically in an arbi- trary manner [3]. Instead of just communicating based on the availability of pow er, w e w ould imple ment the priority calculation algorith m in the eventual
steps so as to protect the netw ork breach as w ell as obtain the communication system of desired f eature. Once a netw ork has b een constructed, w e w ould not again send data packets through the same sequence of nodes in successive iterations. This w ould, to some extent eliminate predictability of the path of communication. Hence, w e w ould consider the f actors like the pow er of node, time ta ken f or communication, interf e rence rate f or communi- cating node as w ell as attack possibility on it.
Inde x Terms— Ad-hoc, Attack Possibility, Interf erence rate,Node pow er, Predictability, Success rate, Computer Science, Mobile computing
—————————— ——————————
1 INTRODUCTION
A Mobile Ad-hoc networ k (MANET) is an infrastr uctur e less networ k wher e the nodes involved in it per tain dynamic pos i- tions at var ious time spans.[1] With the advancements in the mobile communication, the r egular demands of the customer have r ose. Not only netw or k lifetime, but the secur ity of com- municating system fr om attacks, minimal inter fer ence fr om neighbor ing wir eless components as w ell as the time con- sumed in the communication betw een the intermediary nodes and eventually the time for the communication betw een sour ce and destination nodes have now become the essential constr aints put forwar d by the customers. Thus, it is suitable to addr ess these r equir ements, which is tried by the pr oposal of this paper . Mobile natur e of the participating nodes led to the employment of Ad-hoc on-demand Vector Routing (AODV).[4] Using this mechanism, the data packet is sent only to those nodes which r espond to the listening packet sent by the source node.
Communication system in ad-hoc has advanced with year s. It is better to manage its communication thr ough the pr ioritized r equir ements [2],[8]. This would eventually manage the transmission accor ding to its prior ity list. For example: if an or ganization gives highest pr ior ity to the netw or k lifetim e, it
———— ——— ——— ——— ———
Jiwa n Pokha rel is currently pursuing Bachelor degree program in Comput- er Science & Engineering in K.L.C.E., India, E -ma il: jiwanpokha-
rel@gma il.com
Sa ntosh Bha nda ri is currently pursuing Bachelor degree program in I n-
forma tionScience & Technology in K.L.C.E., India, E -ma il: sa nflow-
er.bhn@gma il.com
Sa roj Sha rma is currently pursuing Bachelor degree program in Computer
Science & Engineering in K.L.C.E., India, E-ma il: ja ngosa roj@gma il.com
Prof. S. Venka teswa rlu is the HOD, Depa rtment of Computer Science &
Engineering, K.L. University, Ema il: somu23@kluniversity.in
would pr ovide its specification accor dingly such that the con stant r elated to networ k lifetime would pertain highest value
amongst the available sets of the constants. In the past, either
pow er of the participating mobile nodes or the cost involved was taken as maj or constraint in establishing the netw or k. W e, through this paper , shall provide additional impetus to br ing out even mor e advancements upon those technol ogies. The pow er-r outing and cost-r outing algor ithms [7],[10]mer ely con- sider the pow er available in the node or the node's lifetime and the costs involved in the netw or king r espectively. But, the intent of the pr oposal pr esented by this paper is to instituti o- nalize these factor s as well as the tw o others i.e. Inter fer ence factor and Attack possibility on the commu
nicating system so as to meet the specific needs of the spec i- fied implementable scenar io.
A basic concer n is ab out the pr edictability of the path in the
communication [11]. It is possible for an intr uder to analyze the traffic flow and encr oach into the communicating system. Thus, it is pr oposed that the nodes w ould not follow the same path for data flow once it ha s been traver sed in the pr evious iteration of tr ansmission. This would certainly br ing out the pr operty of unpr edictability in the flow of data packets. Also, if no other paths than the pr ior iter ation's path is possible, the sy stem w ould finally follow the same.
Tw o main phases ar e involved in MANETs viz. Route Discov-
ery and Route Maintenance. Route discovery r efers to ident i- fying the appropr iate path for data transmission betw een the tw o nodes.[4] For this , the algor ithm pr esented in the paper
employs ab ove mentioned constraints so that the r equir ements
IJSER © 2012
http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 2, Fe bruary -2012 2
ISSN 2229-5518
of the customer s/users ar e satisfied. In the r oute maintenance phase, the sour ce continually monitors the position of the nodes to make sur e that the data is being carr ied thr ough the path to destination without loss [4].
.
2 P ROCEDURE FOR PAP ER SUBM ISSION
2.1 Con straintless Power and Cost aware Routing
Algorithm
The optimum power and cost optimization algor ithm pr o- posed by [1] is taken as a base for our pr oposed algor ithm. The algor ithm ab olished the usage of the constraints like thr eshold and cutoff values and obtained the power and cost optimal communication scenario in ad-hoc networ k.
Algorithm power-cost-optimal
{
reply->value:=0; //For delivery failure.
S:=source(A);
/*Now, eliminate source as neighbor to any other node*/
send(listening -packet);
reply:=node-algorithm();
if(multiple relies)
{
reply:=reply(of node which has minimal routing distance i.e.|AB|);
if(minimal distance same for multiple nodes)
reply:=reply(of node having highest battery power);
}
if(reply->value)
send(reply->address);
else Delivery failure or destination reached;
}
The node algor ithm is used in each of the nodes, so as to ob- tain the compar ison of the pow er or battery lifetime of each node with the amount of ener gy r equir ed in sending the de- fined packet towar ds the neighboring node. Also, this algo- r ithm deter mines the least cost and mor e pow er efficient path for the transmission of the packet when tw o or mor e paths ar e available.
Algorithm node-algorithm(B)
{
//Initially all nodes have reply->value==0 if(Destination reached)
{
return(reply );
stop the process;
}
size:=listening -packet->size;
while(power(B)>power-calc(B)
{
reply->value:=1;
power-cost-optimal(B);
}
return(reply);
}
Feeney et al’s for mula for the measur ement for ener gy con- sumption is utilized in the pow er-calc algorithm so as to de- termine the amount of ener gy r equir ed to r eceive and transmit the cer tain sized packet.[5],[9]
Algorithm power-calc(B)
{
return(m*size + b);
}
2.2 The Density Ba sed Flooding Algorithm
This algorithm is used to identify the density of the nodes in a cluster and eventually determine the inter fer ence caused by them[6].
1. The node n1 which star ts the broadcast r esolves it neigh- bors and updates it Neighbor count .n1 and mar ks it type as.
ß nodes n1 <=
a nodes n1 >
and then mar k the message w ith its type and then br oadcast it
to all its neighbors w hich ar e listening at a specific port (by
assuming p1 = 1.)The node will add that packet ID I0 in its
‘Message Seen List’ L1 to avoid forwar ding it again.
2. On r eceiving a packet, a neighbor ing node will add that
packet ID I0 in its ‘Message Seen List‛ L2 and then update its
Neighbor count n2 and mar ks its type using the condition (1)
if I0 L2 then
{
if ti != ß and tpi = then
if < p2 then
Forward the Packet.
}
Else
Forward the Packet with pr obability 1.
}
Else
It is a pr eviously seen message. So dr op it
}
wher e ,
ti type of the curr ent node tpi type of the pr evious node
pr obability (randomly chosen between 0 and 1)
p2 = 1 /n 1 *
p2 is the pr obability in which it should r e-br oadcast the pack-
et. All the r emaining nodes of the netw or k will forward the
packet based on the condition. This will stop until all the nodes of the networ k r eceive at least one copy of the packet with same ID I0.
3 PROPOSED ALGOR ITHM
W e propose ‚Priority Based Algorithm” to determine the ap- pr opr iate path for data tr ansmission as follows:
i.) The r eply w ould contain:
a. Pow er of node b. Time of r eceipt
IJSER © 2012
http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 2, Fe bruary -2012 3
ISSN 2229-5518
c. Inter fer ence r ate due to neighbor nodes d. Amount of attacks
ii.) Inter fer ence rate is calculated by evaluating the density of
the neighbor ing nodes and their signal str ength. This value is eventually normalized in the range of [0,1].
iii.) Eventually employ the for mula when tw o or mor e neigh-
bors ar e capable of establishing a communicating system.
iv.) Add up to get maximum of the paths for each path, and employ formula as:
Pr obability (P) s(p t i a)
wher e,
s=success rate i.e. 0 or 1 p=pow er of node
t=time taken for nodal communication i=inter fer ence for node by neighbor s a=attack possibility on node
α, β, γ, Ώ ar e user expected constr aints which should fall in
the range [0,1].
4 M ATHEM AT IC AL SYNOPSIS
Above algor ithm is employed to obtain the mathematical ca l- culations as given below. For the values of the var ious con- stants employed in the formula we shall deploy the follow ing tabulated values. The values ar e generated as random num- bers i.e. 0.693, 0.066, 0.984, 0.479 and eventually used accor d- ing to the ascending order for the pr ior ities of the constants. We should take the pr ior ity order and value by using the table
1.
We have identified four possible scenar ios in the communica-
tion viz.
i. Networ k lifetime sensitive communication ii. Time sensitive communication
iii. Inter fer ence sensitive communication
iv. Attack sensitive communication
i.Network lifetime sens itive co mmunication:
In the gener al communication scenar ios, it is highly essential
to maintain longer networ k lifetime. Thus at such cases the dur ation or lifetime of networ k becomes the most important criterion.
ii. Time sensitive communication:
In the emer gency scenarios like natur al calamities, accidents
and many mor e, the time for communication plays vital r ole.
At such instances the communication needs to be faster r ather than having longer netw or k lifetime.
iii. Inte rference sensitive communication:
Military and secur ity r elated communications ar e sensitive
enough to not be hamper ed by the neighbor ing signals. Thus
it gives higher prior ity to the fr ee transmission of the comm u- nicating signal.
iv. Attack sensitive communication:
Highly secur ed communication which would decr ease the
chances of the possible attacks and thr eats is desirable in the security r elated or ganizations like military, finance, etc.
Table 1. Sample user defined priorities and corresponding values of the constants.
For network lifetime sensitive communica- tion |
Constant | Prior ity | Value |
α | 1 | 0.984 |
β | 2 | 0.693 |
γ | 4 | 0.066 |
Ω | 3 | 0.479 |
For time sens itive communication |
Constant | Prior ity | Value |
α | 4 | 0.066 |
β | 1 | 0.984 |
γ | 3 | 0.479 |
Ω | 2 | 0.693 |
For interfe rence sensitive communication |
Constant | Prior ity | Value |
α | 3 | 0.479 |
β | 4 | 0.066 |
γ | 1 | 0.984 |
Ω | 2 | 0.693 |
For attack sensitive communication |
Constant | Prior ity | Value |
α | 2 | 0.693 |
β | 3 | 0.479 |
γ | 4 | 0.066 |
Ω | 1 | 0.984 |
4.1 Values Taken For the Respective Node s
Eventually, w e have taken a communication scenar io having five nodes, wher e node 1 is the sour ce node and node 2 is the dest ination. The values for the power of node, (p), the r ate of inter fer ence, (i) and the possibility of attack, (a) for each of the nodes after their participation in the communication system ar e depicted below :
Table 2. Obtained values for power of node, inte rference rate and attack possibility (normalized in [0,1]).
| Node |
| 1 | 2 | 3 | 4 | 5 |
p | 0.00 | 0.90 | 0.70 | 0.60 | 0.70 |
i | 0.00 | 0.60 | 0.35 | 0.82 | 0.20 |
a | 0.00 | 0.40 | 0.72 | 0.19 | 0.80 |
The time r equir ed for the communication between the nodes is shown thr ough a 5x5 squar e matrix:
IJSER © 2012
http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 2, Fe bruary -2012 4
ISSN 2229-5518
Table 3.Time required for communication between two nodes.
1-3-5: 0.40601
1-4-3-5: 0.17838
1-4-5: 0.12783
Finally, this pr oves the path 1-2-4-3-5 to have the lar gest sum
for the pr obability values. Thus, it w ould be the optimal path
as per our algor ithm.
Using power calculation algorithm, the path followed by
packet can be depicted as:
2 4

4.2 Calculation for Network Sen sitive Communication 1 5
An assumption that all the neighboring nodes shall send the
success value as 1 to the eventual sour ce node of the iteration 3
is made to proceed in the calculation.
Thus, w e calculate the pr obability matr ix as follows:
As node 1 is the sour ce node, thus all the paths possible fr om
it ar e evaluated for their corr esponding pr obabilities: p(1,2)=0.8856-0.2079-0.0396-0.1916=0.6381 p(1,3)=0.6888-0.17325-0.0231-0.34488=0.51555 p(1,4)=0.5904-0.2772-0.05412-0.09101=0.16807
Her e, p(1,5) is not consider ed as w e don’t intend to dir ectly
establish the communication betw een the sour ce and the des-
tination.
Above p(1,2) has highest pr obability value th us next sour ce
shall be node 2.
Fig 1. Path followed as per Power Calculation Algorithm
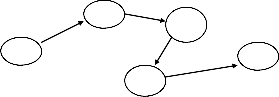
After using the pr ior ity based algor ithm, the path w ill be tra- versed as:
2 4
p(2,1)=0 ,p(3,2)=0, p(4,2)=0, p(5,2)=0 1 5
And, 3
p(2,3)=0.02976, p(2,4)=0.23044, p(2,5)=-0.15805
Her e p(2,4) has the highest value for pr obability thus node 2-4
is tr aversed. Eventually, p(3,4)=0 and p(5,4)=0.
p(4,3)=0.11985, p(4,5)=-0.04024
Thus path 4-3 is selected. And, p(5,3)=0, p(3,5)=-0.10954
The tabulated form of these values is:
Table 4. Calculated probability values
N o d e | 1 | 2 | 3 | 4 | 5 |
1 | 0.00 | 0.638 | 0.51 5 | 0.16 8 | 0.00 |
2 | 0.00 | 0.00 | 0.02 9 | 0.23 0 | -0.158 |
3 | 0.00 | 0.00 | 0.00 | 0.00 | -0.109 |
4 | 0.00 | 0.00 | 0.16 9 | 0.00 | -0.040 |
5 | 0.00 | 0.00 | 0.00 | 0.00 | 0.00 |
Thus, fr om the table w e can obtain the possible paths with the sum total of the pr obability values as:
1-2-3-5: 0.55832
1-2-4-3-5: 0.87885
1-2-4-5: 0.8283
1-2-5: 0.48005
Fig 2. Path followed as per Priority Based algorithm
5 CONCLU SION
This paper pr esents the user defined factor s like power of the node, time r equir ed for communication, rate of inter fer ence for each node and attack possibility on the corr esponding node as the pivotal keys to constr uct the comm unication sys- tem in the mobile ad-hoc envir onment. It focuses on identify- ing the need of the var ious scenarios and implementing the communication system accor dingly. In the end, w e intend to pr opose a solution for need-based scene which would be both optimal and easily acceptable in the implementation scenar io.
6 FUTURE WORKS
The paper can be extended to satisfy other user r equir ed con- straints if any. This shall make the implementation of ad-hoc , application specific.
ACKNO WLEDGMENT
W e w ould like to extend our sincer e thanks to Asst. Pr of. T.Vijaya Ssar adhi, Dept of Computer Science and Engineer ing, K.L. University, for the untir ing help and encouragement. It is our extr eme pleasur e to acknowledge our thanks to the a u-
IJSER © 2012
http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 2, Fe bruary -2012 5
ISSN 2229-5518
thor s of pr evious j our nals and papers which aided us to put a new perspective in the field of mobile networ king.
REFERENC ES
[1] Jiwan Pokhar el, Prathipati Sr ihyma, T.Vij aya Saradhi,
‚Constraintless Appr oach of Pow er and Cost Awar e Routing
in Mobile Ad hoc netw or ks‛, Inter national Journal of Com-
puter Applications, Vol.31,No.10, October 2011
*2+ Puneet Kumar , A.K.Vatsa,‛Secur e and Pr iority Based
Routing Mechanism in MANET thr ough Mobile Agent ‚,
Journal of Computing, vol.3, Issue 3, Mar ch 2011
[3] Damianos Gavalos, Charalampos Knostantopoulos, Basilis
Mamalis, Grammati Patzion, ‛Mob ilty Pr ediction in Mobile
Ad hoc Networ ks‛, Encyclopedia of next Gener ation Net- wor ks and Ubiquitous Computing.
*4+ S.Gunasekaran and Dr. K. Dur aiswamy,‛Multicast Mult i-
path Pow er Efficient Routing in Mobile Ad hoc Networ ks‛, International Jour nal of Computer Science and Networ k Sec u- r ity, Vol.10, No.4, Apr il 2010
*5+ L.M. Feeney, M. Nilsson, ‚Investigating the Ener gy Con- sumption of a Wir eless Networ k Inter face in an Ad hoc Net- wor king Env ir onment ‚, Pr oceeding of IEEE Infocom, April
2001
*6+ N. Karthikeyan, V.Palanisamy, K.Dur aiswamy, ‛Optimum
Density Based for pr obabilistic flooding pr otocol in mobile Ad
hoc networ k‛, Eur opean Journal of Scientific Resear ch
,Vol.39,No.4, 2010
*7+ Ivan Stojmenovic and Susanta Datta, ‛Power and Cost
Aw ar e Localized Routing with Guaranteed Delivery in Unit Graph Based Ad hoc Networ ks‛, W ir eless Communications and mobile computing, 2003
*8+ Saswati Sar kar Maria and Adamou, ‚A Framew or k for Op- timal Battery Management for W ir eless Nodes‛, IEEE Jour nal on Selected Ar eas in communications, Vol.21, No.2, Febr uary,
2003
*9+ L.M. Feeney,‛Ener gy Efficient Communication in Ad Hoc
Wir eless Networ ks‛, Computer and Netw or k Architectur e Laboratory, Sw edish Institute of Computer Science,2003 [10]Ivan Stojmenovic and u Lin,‛Pow er Awar e Localized Routing in W ir eless Netw or ks‛, IEEE transactions on parallel and Distributed Systems, Vol.12, No.10, October , 2001
*11+Biju Isaac, Khair uddin Ab Hamid, C.E. Tan, ‛Hybr id Mo- bility Pr ediction of 802.11 Infrastructur e Nodes by Location
Tracking and Data Mining‛, Journal of IT in Asia, Vol.3, 2010
IJSER © 2012
http :// www.ijser.org

