The research paper published by IJSER journal is about Neural Network Intrusion Detection Architecture for Distributed System 1
ISSN 2229-5518
Neural Network Intrusion Detection Architecture for Distributed System
ShahidNaseem
Reg # 2113246
School of Computer Sciences, NCBA&E, Lahore Pakistan shahid.naseem@gmail.com
Abstract----Attac ks on network infras truc ture pres ently are main threats against network and inf ormation s ec urity. W ith the rapid expans ion of c omputer networks , s ecurity has bec ome a crucial issue f or distributed s ys tems . U nauthorized activities in networks , intrus ion detec tion (ID) as a c omponent of def ens e-in-depth is very nec ess ary bec aus e traditional firewall tec hniques c annot provide c omplete protection against intrus ion. Introduction detection is the problem of identif ying unauthorized us e, misus e, and abus e of c omputer s ystems by both s ys tem ins iders and ext ernal. Intrusion Detec tion Sys tems c ombine dis tributed monitoring and data reduction through individual host and LAN monitors with c entralized data anal ysis to monitor a network of c omputers. IDS ’s in dis tributed s ystems are bas ed on the belief that an intruder ’s behavior will be notic eably diff erent from that of a legitimate us er. A main problem c onsidered in this paper is the network -us er identific ation problem, whic h is c onc erned with trac king a us er m oving across the network, poss ibly with a new us er -id on eac h c omputer. The increas ed c onnec tivity of c omputer s ys tems gives greater acc ess to outs iders and mak es it eas ier f or intruders to avoid detection. This pap er propos es a new way of applying neural networks to det ect intrusions i.e. “N eural N etw ork Intrus ion D etec tion Arc hitecture that will us e f or intrus ion detection. Neural network intrus ion det ec tion arc hitec ture c an be us ed to identif y eac h us er muc h like det ec tives to plac e peopl e at crime sc enes .
Index Items----- Neural, Intrus ion Detection, Distributed System , def ens e –in-depth, crac ker, legitimate.
————————————————————
ntrusion detection schemes can be classified into two categories: misuse and anomaly intrusion detection. Misuse refers to known attacks that exploit the known vulnerabilities of the system. Anomaly means unusual activity in general that could indicate an intrusion. If the observed activity of a user deviates from the expected behavior, an anomaly is said to occur.Misuse detection can be very powerful on those attacks that have been programmed in to the detection system [1]. However, it is not possible to anticipate all the different attacks that could occur, and even the attempt is laborious. Some kind of anomaly detection is ultimately necessary. One problem with anomaly detection is that it is likely to raise many false alarms. Unusual but legitimate use may sometimes be considered anomalous. The challenge is to develop a model of legitimate behavior that would accept novel legitimate use. It is difficult to build such a model for the same reason that it is hard to build a comprehensive misuse detection
system: it is not possible to anticipate all possible variations
of such behavior.The task can be made tractable in three ways:
i. Instead of general legitimate use, the behavior of individual users in a particular system can be modeled. The task of characterizing regular patterns in the behavior of an individual user is an easier task than trying to do it for all users simultaneously.
ii. The patterns of behavior can be learned for examples of legitimate use, instead of having to describe them by hand-coding possible behaviors.
iii. Detecting an intrusion real-time, as the user is typing
commands, is very difficult because the order of commands can vary a lot. In many cases it is enough to recognize that the distribution of commands over the entire login session, or even the entire day, differs from the usual.
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Neural Network Intrusion Detection Architecture for Distributed System 2
ISSN 2229-5518
Table 1: Intrusion Detection Model
A computer system is accessed by a user through an interface that translates its typing into commands. The user is free to submit what he wants (command line), or isguided by a constraining environment (menus, transaction monitor). These actions generate a udit trails that we obtain at the previous levels.
The hacker, attacking from inside as an authorized user or from outside as an intruder, uses vulnerabilities or flaws on the system. The neural network cannot take advantages of all the information in the audit data.One of the more interesting challenges f or intrusion detection in a networked environment is to track users and objects (e.g., files) as they move across the network. For example, an intruder may use several different accounts on different machines during the course of an attack.Since all attacks that utilize the network for system access will pass through the LAN segment, the LAN monitor will be able to monitor all of this traffic. This architecture will motivate our work by d escribing the types of behavior to be detected by formulating the network-user identification, an identifier for a network - wide user and bydescribing its use in the distributed systems.It is therefore, interesting to build a tool that monitors the activities of users without specifically looking for known vulnerabilities. The data come from the audit mechanisms activated on the systems, either for security purposes or for others such as accounting.
NNID (Neural Network Intrusion Detection)
architecture is based on these three ideas. NNIDA is a
neural network trained to identify users based on what commands they use during a day. The system administrator runs NNID at the end of each day to see if the users’ sessions match their normal pattern. If not, an investigation can be launched. The NNID model is implemented in a distributed systems environment and consists of keeping logs of the commands executed, forming command histograms for each user, and learning the users’ profiles from these histograms. NNID provides an elegant solution to off -line monitoring utilizing these user profiles. It is predicted that if there are 10 users, NNIDA will 96% accurate in detecting anomalous behavior (i.e. random usage patterns), with a false alarm rate of 7%. These results show that a learning offline monitoring system such as NNIDA can achieve better perf ormance than systems that attempt to detect anomalies on-line in the command sequences, and with computationally much less effort. The rest of the paper presents the implementation and an evaluation on a distributed computer systems.
Many misuse and anomaly intrusion detection systems (IDSs) are independent of the platform, system vul - nerability, and type of intrusion. It maintains a set of historical profiles for users, matches an audit record (user actions) with the appropriate profile, updates the profile whenever necessary, and reports any anomalies detected. Another component, a rule set, is used for detecting misuse.Often statistical methods are used to measure how anomalous the behavior is, how different e.g. the commands used are from normal behavior [2]. Such approaches require that the distribution of subjects’ behavior is known. The behavior can be represented as a rule-based model in terms of predictive pattern generation or using state transition analysis.IDSs also differ in whether they are on-line or off-line. Off-line IDSs are run periodi cally and they detect intrusions after-the-fact based on system logs. On-line systems are designed to detect intrusions while they are happening, thereby allowing f or quicker inter - vention. On-line IDSs are computationally very expensive because they require continuous monitoring. Decisions need to be made quickly with less data and therefore they are not as reliable.
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Neural Network Intrusion Detection Architecture for Distributed System 3
ISSN 2229-5518
Several IDSs that employ neural networks for on -line intrusion detection have been proposed. These systems
learn to predict the next command based on a sequence of previous commands by a specific user. The network is recurrent, that is, part of the output is fed back as the input f or the next step; thus, the network is constantly observing the new trend and “forgets” old behavior over time. The size of the window is an important parameter: Ifit is too small, there will be many false positives; if it is too big, the network may not generalize well to novel sequences. The most recent of such systems can predict the next command correctly around 80% of the time, and accept a command as predictable (among the three most likely next commands) 90% of the time.
One problem with the online a pproach is that most of the effort goes into predicting the order of commands. In many cases, the order does not matter much, but the distribution of commands that are used is revealing. A possibly effective approach could theref ore be to collect statistic s about the users’ command usage over a period of time, such as a day, and try to recognize the distribution of commands as legitimate or anomalous off-line. This is the idea behind the NNID Architecture [3] [4].
The NNID anomaly intrusion detection architecture is based on identifying a legitimate user based on the distribution of commands she or he executes [5]. This is justifiable because different users tend to exhibit different behavior, depending on their needs of the system. Some use t he system to send and receive e mail only, and do not require services such as programming and compilation. Some engage in all kinds of activities including editing, programming, email, web browsing, and so on. However, even two users that do the same thing may not use the same application program. This approach works even if some users have aliases set up as short-hands f or long commands they use frequently, because the audit log records the actual commands executed by the system. An event reported by a host monitor is called a host audit record. The record syntax isMonitor -ID, Host-ID, Audit-UID, Real-UID, Effective- UID, Time, Domain, Action, Transaction, Object, Return Value, error Code.Of all the possible events, only a subset is forwarded to the expert system. For the creation and application of the NID, it is the events
which relate to the creation of user sessions or to a change in an account that are impor tant. The Neural
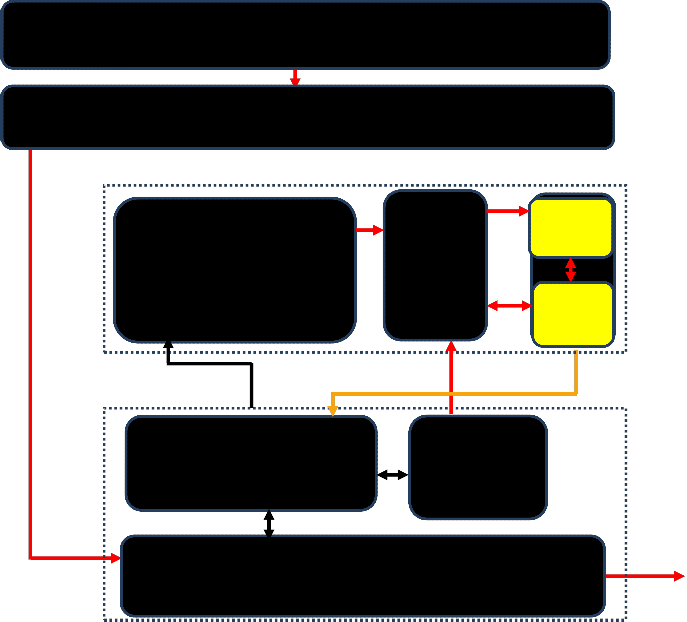
Network Intrusion Detection Architecture consists of the following: -
5.1 Data Acquisition
This module gathers the various audit trails (user ’s actions) on the system and transfers them to the station supporting the intrusion detection system [6].
5.2 Data Classification
This module arranges the data into a common f ormat that can be interpreted toa data analysis unit. It also checks the correctness of the records.
5.3 Data Analysis Unit
This is the analysis unit of the intrusion detection system. Its main function is to receive the formatted data from data classification unit and alarming the network security administrator if there is any intrusion detect in the data on the basis of some security policiesdefined by the neural network.
5.4 Data Formation Unit
This module analyses the intrusion based data coming from data analysis unit. The purpose of this unit is to encoding the intrusion based data and to format the data bit by bit and then decoding the data again and forward to analysis and control unit. [7].
5.5 Analysis and Control
It receives the output of the data from unit and translates it into a format suitable for intrusion detection. It also monitors the internal pa rameters of the network for additional information. It analysis the data by comparing the output data from data f ormation unit with the original data in the external memory. Then for the next bit, it will check the data from data formation unit and compare it with both internal and external memories and will generate the results.
5.6 Learning Unit
It is responsible for tuning and verifying the learning process to avoid biasing the model with intrusion behavior[8].
5.7 Internal & External Memory
Internal memory module is responsible for holding the results from analysis and control unit as well as forward this result to data analysis unit for alarming the security admi nistrator about the task completion. The external memory is responsible for holding the
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Neural Network Intrusion Detection Architecture for Distributed System 4
ISSN 2229-5518
initial data after applying the security policies. After gaining knowledge, the data analysis unit will gain the expertise to detect and remove the intrusions at external memory. In this way, the system performance will increase.
6. Conclusion
Most of the organizations use traditional firewall techniques in their networks for intrusion detection but it cannot provide complete protection against intrusion. Introduction detection is the process of identifying unauthorized use, misuse, and abuse of computer systems by both system insiders and external. Intrusion Detection Systems combine distributed monitoring and data reduction through individual host and LAN monitors with centralized data analysis to monitor a network of computers. IDS’s in distributed systems are based on the belief that an intruder ’s behavior will be noticeably different from that of a legitimate user. The current IDS’s do not consider the impact of the LAN structure when attempting to monitor user behavior for attacks against the system. Intrusion detection systems designed for a network environment wil l become important as the number and size of LAN’s increase [9]. Experimental evaluation on real -world data shows that NNIDA can learn to identify users simply by what commands they use and how often, and such an identification can be used to detect intrusions in a network computer system. The order of commands does not need to be taken into account. NNIDA is easy to train and inexpensive to run because it operates off - line on daily logs. As long as real -time detection is not required, NNIDA constitutes a promising, practical approach to anomaly intrusion detection. Neural network intrusion detection architecture will be helpful in solving the network-user identification problem.
References
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Neural Network Intrusion Detection Architecture for Distributed System 5
ISSN 2229-5518
Analysis and
Control
Learning
Unit
Internal
Memory
Knowledge Security Policy
External Memory

Intrusion Detection Architecture
IJSER © 2012 http://www.ijser.org