International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1280
ISSN 2229-5518
Irys
A Jewelry Tracking And Management
Application
Anagha Ainapure, Urvi Gandhi, Yashodhara Pandit, Megha Bisani1
Abstract— From the last few years Radio Frequency Identification (RFID) technology has gained increasing focus from the developers as well as actual users. Its main advantage lies in the usage of RFID tags over the now in use barcodes. The prominent advantages are:tags are available in sizes ranging from postage stamps to burly sizes, RFID tags need not be visible to the reader, mere presence in the read zone is sufficient for a successful scan ,tags have no moving parts and can be in protective material for an indestructible case with a multi-year life span, tags can be placed in extreme environments and perform to specifications thereby allowing organizations to handle a variety of industrial, material handling and asset management applications, RFID tags are available in various packaging and are available as a reusable tag too. The prime objective of “IRYS- Jewelry Tracking and Management Application” is to create a full-fledged android application which could locate a jewelry item based on the RFID code read as the input. It focuses on identifying an RFID tag attached to the jewelry item and shows the complete details. It will generate complete reports regarding sales analysis, staff management, inventory, customization of the product, etc. It will also provide marketing tools which will foster ROI of the jeweler. The app will be useful in B2B and B2C transactions. It is developed using the Android 4.0 version, API 15 (Ice-cream sandwich).
Index Terms— Android, Java, Jewelry, RFID, Scanners ,Tablet, Tags
—————————— ——————————
1 INTRODUCTION
Jewelry business has become a large scale industry operating on a multinational level. These day’s jewelers do not require just security of the items at display, but trendiest and more attractive displays to maximize sales.
Along with this, jewelry businesses demand the use of latest technology to its full potential in order to minimize human efforts and ease each and every transaction, be it B2B or B2C.One of the major tasks of jewelers is to take stock audits on a regular basis. This is a completely manual process, which requires physical handling of each jewelry item separately, and is therefore, very time consuming and prone to errors. A quick fix to this trouble is the use of barcodes, however it is a line of sight technology, susceptible to wear and tear, also it is read only, scanning one item at a time, cannot be programmed and can be duplicated, and yet the tiresome issue of stock auditing is not handled.
————————————————
1Department of Information Technology , Sinhgad College of Engineering, Pune , India
Also, inventory tracking may lead to misplacement, loss or even theft. In a premium business such as this, even a small error or loss can be significantly expensive. Huge amounts can be lost due to inefficient and slow inventory tracking; RFID speeds up this process and makes it more efficient and secure.
Therefore, while RFID is widely being used as an effective tool in retail industry, one application where it has immediate and direct benefits is Jewelry tracking. This RFID based jewelry tracking system enables tracking inventory via scanning and therefore instant stock update while increasing the staff productivity. Moreover, by automating these processes, the Jeweler can focus on his core business.
Also the various other modules such as list preparation and smart display assist the customer in making proper choices and speedup calculations. The E-catalogue feature of this application is designed to utilize the customer’s idle time and also helps to flash items which currently are not physically available at the counter which helps in cross- selling.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1281
ISSN 2229-5518
2 HARDWARE AND SOFTWARE COMPONENTS
2.1 HARDWARE COMPONENTS
2.1.1 RFID TAGS USED
The RFID tags are of two major types : Active tags and
Passive tags.
Active tags are self – powered while the passive tags are not. Passive tags are used by this application. A passive tag is an RFID tag that does not contain a battery; the power is supplied by the reader. When radio waves from the reader are encountered by a passive RFID tag, the coiled antenna within the tag forms a magnetic field. The tag draws power from it, energizing the circuits in the tag. The tag then sends the information encoded in the tag's memory.
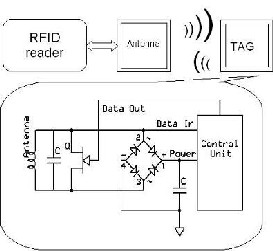
Fig 1. Circuits inside a passive RFID tag
2.1.2 RFID READERS OR SCANNERS
Ultra-portable devices which communicate via Bluetooth and need a host (PC, Mobile phone or PDA) to communicate with can be used to bring about the reading of the RFID tags .Once the devices are paired, the scanner automatically detects tagged jewelry items and transfers the data to the host. The reader pairs with the tablet on entering the MAC address of the reader into the tablet. On entering we test the connection and on successful connection we can save the MAC address for future use.
This device also helps with item search. Also, Wi-Fi enabled, mobile computer with an integrated RFID scanner, which automatically detects tagged jewelry items directly
from the display can be used, thus eliminating the need for a host, this scanner simply needs to be moved over trays of jewelry and count will be instantly displayed on its screen.
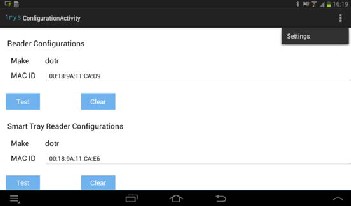
Fig 2. Reader Configuration setting
2.1.3 TAG PRINTER
This is an intelligent printer. It prints the unique hexadecimal code for every item on the tag. The Zebra Programming Language (ZPL) is one of the several languages used for writing the code used for this tag printing. Also the printer is used to print barcodes, which are used as a backup in case RFID chip fails. The printer has a ribbon which gets heated when the printer is powered on and then prints the information on the tag. A sample ZPL snippet can be written as follows:
string ItemCode=FR00000001;
^XA
^LH0,0
^RS^RFw,a^FD" +ItemCode+ "^FS
^FO140,20^FB500,1,,L,^A0N,18,16^FD" +ItemCode+ "^FS
^FO100,40^BY2,10,50^FT150,50^AEN,15,15^BCY,,Y,N^FD"
+ +ItemCode+ "^FS
^PQ1,0,1,Y
^XZ
2.2 SOFTWARE COMPONENTS
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1282
ISSN 2229-5518
2.2.1 JAVA ENVIRONMENT
This application was developed using the Java Development Toolkit (jdk 1.0.7) and the Java Runtime Environment.
2.2.2 ECLIPSE
Eclipse which is an Integrated Development Environment was enhanced with the Android Plug-in and used for coding.
2.2.3 ANDROID DEVICE
Android devices such a tablet with minimum version
4.0(Ice cream sandwich) are required for installing the APK
file of the application.
3 SYSTEM ARCHITECTURE
3.1 MIDDLEWARE USED FOR INTERFACING READER AND THE TABLET
Every reader is required to synchronize with the tablet for displaying the information which it reads from the tag. And for reader there is a different communication protocol which has to be followed. This obstacle is overcome by this middleware which sits between the reader and the tablet. The working can be showed as follows:
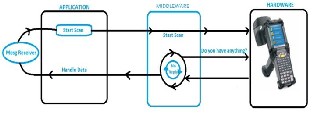
Fig 3: W orking of middleware
On starting the scan, the application and the middleware launches a MAIN THREAD called “start scan”. This communicates with the hardware. Along with it the middleware also launches a sub-thread which continuously queries the hardware device for information availability. When hardware responds, the sub-thread captures this information and transfers it to the application using the HANDLE DATA thread. But this sub-thread cannot do any changes in the application. Hence a SERVICE called “Mesg Receiver” is used to display the received information on the application. This middleware which is interfaced between the hardware and the application plays two major roles. It is a jar file working in coordination with the scanning.
There are various protocols which need for the communication between the hardware (reader) and application (android app) to take place. This middleware facilitates its easy functioning by separating the hardware protocols from the application protocols, i.e. if a new hardware is used by the jewelry retailer such as handheld Bluetooth reader instead of tunnel reader then it is not required to make any changes. This middleware takes care of it and the application side can operate hassle free. Secondly, the middleware is used for parsing of data. The hardware sends the data in Byte code, which it first converts into HEX and then to ASCII format.
3.2 OVERALL SYSTEM
The application will be integrated with the jewelry owner’s ERP server. The following diagram depicts the deployment of the system.
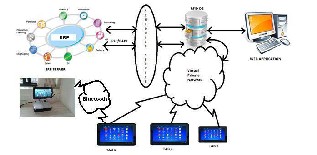
Fig 4. IRYS Network Diagram
The ERP is the main server which contains details about all the others systems such as accounts, sales, staff etc. This ERP is connected to the scheduler service via RFC and BAPI protocols. The scheduler service communicates with the ERP and RFID database using remote calls. The scheduler service also periodically updates the local databases from the main/head office, i.e. the databases of the various branches of the jewelry retailer’s shops. The RFID database consists information about the jewelry items in the stock. It is connected to the Web application which is the desktop version of the android app and has the same functionalities. The RFID database connects to the tablets on which the android application is deployed through the VPN (virtual private network). The VPN allows every tablet to connect with the LAN of the RFID database. The VPN is also used for imparting security by granting permission only to authorized personnel.
4 SYSTEM IMPLEMENTATION AND MODULES DESIGNED
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1283
ISSN 2229-5518
As we explored the android development environment, we came across several public abstract classes with public constructors and methods which simplify several important tasks. For example, we came across ‘SQLiteOpenHelper’, a class that can be used to manage the creation of a database as well as to manage database versions. It provides certain public methods such as ‘onCreate’ which is called when the database is created for the first time,
‘getWritableDatabase’, which creates or opens a database used for reading as well as writing. We have also
extensively used the public class ‘Environment’, especially the method ‘getExternalStorageDirectory’ in order to access the primary external storage directory or the SD card. Such methods reduce the efforts needed in coding simple tasks. We learned that the best way to keep background activities on, without updating the user-interface is to use threads instead of services. In order to display a scrollable list of the details of individual items, we have made use of List View. This view requires the use of an ‘Adapter’ in order to bind each data item to a view. This adapter can be customized by using the ‘BaseAdapter’ class as the superclass. The customized adapter can be used to create a defined layout for each row of the list. One of the most important concepts we learned during the course of this project is the use of the public abstract class ‘AsyncTask’. This class allows certain operations to be conducted in background and then publish the result of the operation on the user-interface thread with the help of 4 steps, onPreExecute - used to setup the task, doInBackground - used to perform the time-consuming operation in background, onProgressUpdate - used to display the progress on the UI and onPostExecute - invoked after the background operation is complete and has produced a result. In this project, we have used
‘AsyncTask’ for the parsing and insertion of Excel Sheet
data into SQLite Database in the android device. As we proceeded, we realized that android development is indeed quite beginner-friendly. There are a lot of different easier ways to implement one’s idea, provided that one is clear on object oriented programming concepts. When we tried to run the application on a device using USB, did not get installed on the device as we had unnecessary jar files in the ‘libs’ folder of the project, and the moment we optimized the folder, the IDE started running smoothly and the application was installed. The ‘Quick Fix’ prompts in Eclipse make it extremely simple to identify the nature of the error and help a beginner to understand what can be done to get rid of the error. This feature has indeed helped our team to strengthen our understanding of object oriented programming in Java. The aforementioned experiences are just a few of the ones we came across, in the initial stages of development and might differ for other beginners.
The system can be implemented in 3 easy steps, as we say it, Tag Tally Talk. Prior to its usage the jewelry items need to be tagged with the tag encoded with proper information. Once the tagging is done we can tally the count on a regular basis. The application also allows the owner to interact with his customers and staff. This system developed using the Java and RFID technologies is the best remedy for the jewelers’ most faced problem – stock take.
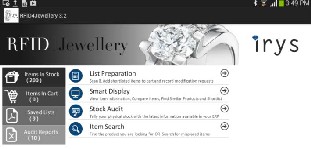
Fig5. Application Home Page
4.1 STOCK AUDIT [INVENTORY MANAGEMENT]
This module helps to track multiple physical pieces accurately and efficiently, so you achieve tighter monitoring of these high value items. Also stock verification becomes a hassle free and full proof process, saving hours of labor time.
It is designed with four columns viz. Expected Items, Scanned Items, Conflict Items, New Items orderly. The Expected Items is populated at the starting of the day. At the end of the day the items are scanned which appear in the Scanned Items list. The missing items count is displayed on the screen instantly. If any New Items are detected they are shown in the New Items column. Conflict Items lists all the items which are not meant to be present on the scanned tray. For example, if the tray in scan has all the rings and if an earring is detected then it is shown in this column.
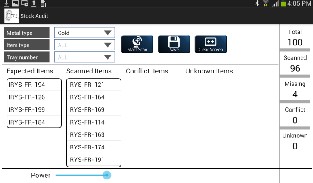
Fig 6. Stock Auditing
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1284
ISSN 2229-5518
4.2 LIST PREPARATION
The list preparation module helps the customer in deciding
his wish list. The items which he scans get automatically added in a list. The customer can then view the complete list along with individual item details. He can also add any comments to a specified jewelry item. This feature is mainly useful for B2B transactions where the customer has modifications in the original item. He can add it in the comments space and send it to the manufacturer. This helps to reduce errors and the end product is just as desired. The customizations can be e-mailed to the desired person instantaneously without exiting the application. Also the facility of saving the list on the device has been provided. It gets saved in pdf format on the SD card of the device.
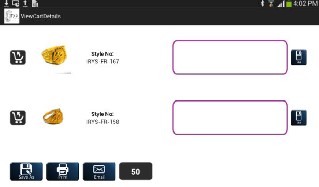
Fig 7. List Preparation
Fig 8. Smart Display
4.4 E-CATALOGUE
The module is designed to utilize the customer’s idle time. It is a slideshow of different items present in the store as also the ones which are not available at the moment but are there in the warehouse. It is used as a marketing strategy.
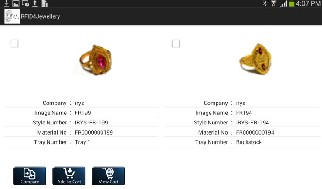
4.3 SMART DISPLAY
This is a different module designed to ease the customer’s efforts. This module divides the tablet screen into 4 sections. Each section consists of a single item’s information. This enables the customer to easily compare
5 RESULTS
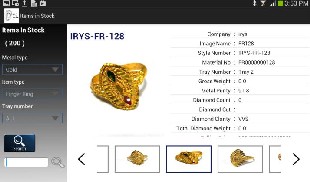
Fig 9. E-Catalogue
the items on various parameters and select the best one. If a customer finds an item interesting he can add it to his cart by clicking the “add to cart” option provided below.
After studying the system and putting it to practical use the following prominent results were recorded
• No item in the store remained unaccounted.
• The store ERP always remained up to date with the
correct data. Consistency in data across all stores could be maintained easily.
• Almost 80% reduction in time was observed in doing stock reconciliation.
• The staff could focus more on sales as information
about the product was available very easily thus fostering the ROI of the shop.
• Also the sales increased as more clarity about customer preferences could be achieved.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1285
ISSN 2229-5518
6 FUTURE SCOPE
• Virtual Try-On feature.
• Similar application for Windows phone/ I-phone.
• Integration with the social media.
7 CONCLUSION
This application is undertaken to design an automated system in order to maximize the jeweler shop owner’s profit by incorporating RFID technology in their business transactions. The various benefits encompass automation of inventory check process at store, reduction in the person- effort involved in Inventory audit which enables faster tally of the inventory at set intervals, electronic recording of the goods movement from Inventory room to the store display, reduction in shrinkage and enhanced visibility into supply chain from manufacturing unit to stores and for exhibitions or external displays.
ACKNOWLEDGEMENT
We are thankful to Miss Neha Vaidya , NeoTechID Solutions, Pune for providing me facilities and kind support throughout the research work. Also we are thankful to Prof. M.V. Nimbalkar for guiding us throughout. We are also thankful to the Almighty.
REFERENCES
[1] Journal article – "RFID JEWELRY MANAGEMENT SYSTEM," Krison Supboon and Daranee Hormdee,Embedded System Research Group, Department of Computer Engineering, Khon Kaen Univesity, Khon Kaen, Thailand.
[2]Journal article – “Overview on Android – The New Mobile Operating System” , SGI Reflections- International Journal of Science, Technology and Management. ISSN No. 0976-2140. Volume 2, Issue 1, April, 2011
[3]Book- Meier, R. (20 JAN 2012). Professional Android 4 Application
Development. Unites States of America: John Wiley & Sons, Inc.
[4]Website: “Development”,”Tools” www.wrox.com ; www.wiley.com
; developers.android.com
IJSER © 2014 http://www.ijser.org