International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1333
ISSN 2229-5518
Efficient Service time Prediction and Bandwidth Reservation Technique for Vertical Handoff in 4G Networks
1Nirmal Raj T,2 R.M.Suresh
Abstract- The main challenge in 4G networks is the vertical handoff between pairs of different types of networks in the presence of 2G,
3G, W LAN, W MAN, satellite etc. along with the fulfillment of Quality of Service (QoS) requirements. The lack of QoS can cause breaks in network during handoff or loss of network at remote condition. Hence in order to overcome these issues, in this paper, we propose an Efficient Service time Prediction and Bandwidth Reservation Technique for Vertical Handoff in 4G Networks. Initially, when the Mobile Terminal (MT) is on a highly movable condition, an efficient service time prediction is done. It collects the distance, data rate, velocity and time threshold. According to the algorithm, an efficient service time provides seamless movement. The second procedure is for providing an efficient bandwidth management through a described algorithm. The solution is able to provide a better method to guarantee QoS in the network by providing efficient bandwidth utilization method and to provide a mapping method that helps in improving the transmission quality.
Key words- vertical handoff, efficient bandwidth management, time prediction,
1. INTRODUCTION
1.14G networks
An emerging wireless networking standard designed to provide the last mile of high speed Internet access to the end user is WiMAX (802.16e) whose design enables high-speed mobile and fixed Internet access to the end user; as a fourth generation (4G) technology, WiMAX is an all-IP solution striving to provide services for data, video, and voice [1].
Fourth Generation (4G) wireless systems provide significantly higher data rates, offer a variety of services such as data, voice, high speed internet and applications, which is not possible due to speed limitations, and allow global roaming among a diverse range of mobile access networks. In a typical 4G networking scenario, handsets or mobile terminals with multiple interfaces can choose among the most appropriate access link between IEEE 802.11 Wireless Local Area Network (WLAN) , IEEE 802.16 Worldwide Interoperability for Microwave Access (WiMAX), satellite systems and Bluetooth, in addition to the traditional cellular telephony networks which are almost universally accessible today [2].
1.2 Handoff in 4G networks
Handover is the process of maintaining a user’s active session when a mobile terminal changes its connection point to the access network [2]. Handoff occurs when a Mobile Node (MN) moves from one wireless base station to another. It can be broadly classified into horizontal and vertical cases. Horizontal handoff occurs when MN moves between similar wireless networks, while vertical handoff occurs when the movement is between heterogeneous wireless networks. Vertical Handoff (VHO) is considered to be an important capability of the next wireless communication era [1].
Horizontal handoff happens between two BSs of the same system. It can be further classified into
1) Link-layer handoff: Horizontal handoff between two BSs, under the same Foreign Agent (FA), e.g., the handoff of an MT from BS10 to BS11
2) Intra-system handoff: Horizontal handoff between two BSs that belong to two different FAs and both FAs belongs to the same system and hence to the same Gateway Foreign Agent (GFA), e.g., handoff of MT from BS11 to BS12
Vertical handoff (Inter-System Handoff): Handoff between two BSs, belong to two different systems and two different GFAS, e.g., the handoff of the MT from BS12 [4, 5].
The ability of MTs to seamlessly transfer to the ‘‘best” access link among all available candidates with no perceivable interruption to an ongoing conversation (which could be a voice or video session) i.e., between heterogeneous networks are referred to as seamless vertical handovers. The emerging IEEE 802.21 standard creates a framework to support protocols for enabling seamless vertical handovers [2]. But providing seamless mobility and service continuity (i.e., minimal service disruption during roaming) support based on intelligent and efficient techniques is a critical issue since the seamless handoff schemes should have minimum handoff latency, lower packet loss, limited handoff failure or blocking and lower signaling overhead [6].
1.3 Vertical handoff and its issues
Vertical handoff decision algorithms help mobile terminals to choose the best network to connect to among all the available candidates and need to be designed to provide the required Quality of Service (QoS) to a wide range of applications while allowing seamless roaming among a multitude of access network technologies. In VHD algorithms, criteria such as cost of services, power consumption and the velocity of the mobile terminal may need to be taken into consideration to maximize user satisfaction [2].
Received Signal Strength (RSS) is the most widely used criterion because it is easy to measure and is directly related to the service quality. It has to deal with issues like Signal strength, Network connection time, Available bandwidth,
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1334
ISSN 2229-5518
Power consumption, Monetary cost, Security and User preferences. VHD algorithms can be quantitatively compared under various usage scenarios by measuring the mean and maximum handover delays, the number of handovers, the number of failed handovers due to incorrect decisions, and the overall throughput of a session maintained over a typical mobility pattern [2].
In vertical handoff performance, it is needed to develop algorithms for connection management and optimal resource allocation for seamless mobility [3]. It is crucial to provide seamless mobility and service continuity (i.e., minimal service disruption during roaming) support based on intelligent and efficient techniques. This means that seamless handoff schemes should have following features: minimum handoff latency, lower packet loss, limited handoff failure or blocking and lower signaling overhead [6]. The seamless and efficient handoff between different access technologies (vertical handoff) is a challenging problem. The heterogeneous co- existence of access technologies with largely different characteristics creates a decision problem of determining the “best” available network at the “best” time to reduce the unnecessary handoffs [8]. And, the most important and challenging issue is seamless handoff management in NGWS, which is used to ensure the QoS [5]. Without QoS consistency, the multimedia session will have the different QoS levels in these network domains and hence seamless continuity will not be doable [10]. Another challenging issue is for seamless roaming is to select an appropriate interface to ensure that a MN remains connected to the network. Furthermore, mobility management as well as the integration and interworking of the existing wireless systems are a complex task due to their specific characteristics [6]. False handoff initiation problem becomes increasingly severe on decreasing the size of the cell. The data rate capacity increases when the cell size of wireless system decreases [4]. Next-Generation Wireless Networks (NGWN) are expected to exhibit heterogeneity in terms of wireless access technologies, personalized and user-oriented services, application requirements, high usability and increased capacity. With NGWN, users will have greater demands for seamless roaming across different wireless networks, support of various services (e.g., multimedia applications) and QoS guarantees. The handoff latency is the time interval during which an MN cannot send or receive any data traffic during handoffs that is composed of L2 (link switching) and L3 (IP layer) handoff latencies. The overall handoff latency may be sufficiently long that results in packet loss, which is inappropriate for real-time applications such as Voice over IP (VoIP). Activating air interface all the time consumes battery power and bandwidth even if the device unit is not sending or receiving any packets. The handoff decision refers to the process of selecting the right moment when to perform the handoff. It is thus critical to avoid keeping idle air interfaces perpetually on [6].
To provide a good solution on the given problem of inefficient handoff latency, failure, and load balancing at time of vertical handoff; this paper is giving a solution in the paper work. The proposed method is divided into phases where the phase one is able to solve the latency and failure. The phase of
the proposed method is able to solve the problem of load balancing.
To make a structured paper, the current paper gives an introduction in the first section. To find a suitable solution, from the exiting work, some literature has done in the second section. The third section gives the proposed method with the problem definition. Finally, a suitable conclusion is given in section four.
2. LITERATURE REVIEW
2.1 Osaka Hassane Abdoulaziz et al., [7] has proposed a new vertical handoff decision algorithm called as Handover Necessity Estimation (HNE) to minimize the number of handover failure and unnecessary handover in heterogeneous wireless networks. They have proposed a multi-criteria vertical handoff decision algorithm based on two parts: traveling time estimation and time threshold calculation. The proposed methods are compared against two other methods such as the fixed RSS threshold based method and the hysteresis based method. Simulation results show that, this method reduces the number of handover failures and unnecessary handovers up to 80% and 70%, respectively. The drawback of the proposed method is that they have not considered the throughput metrics for the mobility management technique.
2.2 Yu-Chang Chen et al., [8] have proposed Vertical Handoff Translation Center (VHTC) architecture to improve the transmission QoS guarantees. Thus, the quality of transmission cannot be reduced enormously even by the effect of vertical handoff between heterogeneous wireless networks. This paper includes new approaches and architecture among Packet Translation, QoS Mapping, Bandwidth Borrowing Management and Vertical Handoff Protocol with a view to achieve the goal, that is, an advanced seamless heterogeneous wireless networks. Finally, simulation results about throughput, delay, jitter and packet loss rate are given to show the performance of vertical handoff implemented by VHTC. The drawback of the proposed method is that they have not considered the overhead metrics to provide a better handoff mechanism.
2.3 Abdellatif Ezzouhairi et al., [9] have proposed a new Hierarchical Transport layer Mobility protocol (HTM) that deals with local and global mobility and improves throughputs during the handoff period. HTM exploits the dynamic address reconfiguration feature of SCTP and introduces an Anchor Mobility Unit (AMU) in order to complete more efficient handoff procedures. Simulation and numerical results reveal that HTM guarantees lower handoff latency and packet loss, good throughput and limited signaling load compared to mSCTP (mobile SCTP) based mobility.
2.4 Rashid Abdelhaleem Saeed et al., [10] have presented an
industrial design for a new vertical handover algorithm for the
WiFi/WiMAX vertical handover heterogeneous network. The
proposed vertical handover is performed on the logical
adaptation layer above the MAC layer. The results of the new
algorithm show less protocol converter time overhead which
can guarantee the QoS. Finally, NS2 results for the throughput
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1335
ISSN 2229-5518
and delay are given to show the performance of the vertical handoff that is implemented. The results are compared with the other conventional methods. The drawback of the proposed protocol is that the method cannot perform well with the increase in number of hops.
2.4 Hong-yan QIAN et al., [11] have proposed Improved Mobile IP-Roaming Supported protocol (IMIP-RS). In IMIP- RS, the distance between mobile nodes and the domain agent can be multi-hops while the value in MIP is only 1-hop. It combines the handoff and buffer technologies in layer-2 with extended mobile IP technology in layer-3. It allows a roaming net to keep normal communication during fast moving. A demo system is developed and the protocol is verified. Test results indicate that it’s capable of achieving high data throughput, low response time and low packet loss rate. It can work with high QoS during rapid movement. The drawback of the proposed method is that they have not considered an efficient method to handle signal overhead.
2.5 Pratap S. Prasad et al., [12] have proposed a generic framework to approach the problem of mobility prediction using Hidden Markov Models (HMM). This method can be used to model hidden parameters in the models. The user movement information is extracted from a real dataset, a HMM is trained using this data and predictions are made using the HMM. This model can successfully predict long sequences of a mobile user’s path from observed sequences and also uses successive sequences of observed data to train its learning parameters to enhance prediction accuracy. Furthermore, they have shown that this model is very generic and can be suited to make predictions using the same information from the perspective of the access point or the mobile node. Future work includes addressing the issues in prediction based on time such as spatio-temporal user behavior and utilizing this information to make predictions.
3. PROBLEM DEFINITION AND PROPOSED
METHODOLOGY-
3.1 Problem definition
In our previous paper, we have proposed a QoS aware vertical handover decision for 4G networks. Initially, when MT on movement finds a new network, it collects the QoS information of the respective network that includes signal strength, network coverage area, and data rate, and available bandwidth, velocity of MT and network latency. Then MT compares the estimated measurements with its old network and network, which provides the better QoS, which is selected as the current network. The old network then performs the data transmission to the new network. In the system design, we have considered the UMTS and WiMAX networks in which the vertical handoff is performed.
Drawbacks
The proposed method does not handle handoff latency and failure.
They have not considered any method for load balancing.
Now as an extension work in paper [15], this paper develop an algorithm for connection management for seamless
mobility that handles the handoff latency, failure and provides better resource allocation for mobile user in order to avoid any kind of overhead in the network.
Before describing the phases of proposed method, an architectural diagram of 4G networks with the architecture of the proposed method is given. Then descriptions of the time threshold and Efficient Bandwidth Borrowings management are given. The proposed method done in this paper is divided into two phases where the phase one is able to solve the latency and failure. The second phase of the proposed method is able to solve the problem of load balancing.
3.2 Proposed method
3.2.1 Architecture of 4G network
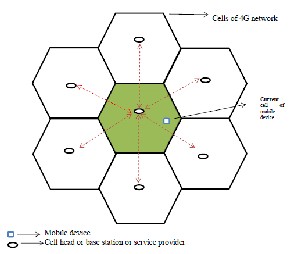
A 4G mobile network consists of several hexagonal structured cells with a service provider called as a base station. There are number of services and users present in the network. These devices are mobile in nature. These devices may be mobile, laptop, tablets, or any other networking devices. The mobile devices are highly movable along the cells in 4G network. The mobile device got services from a base station. The base station or the service providers of the 4G network are providing a number of tasks to the mobile device. The tasks may be video streaming and video calling. Each cell has six neighbor cells around it. The mobile device can enter only into these cells due to physical limitation. A structure of 4G network is given below.
Figure 1 shows the architecture diagram of 4G network
Architecture diagram of proposed method in a 4G network, number of service users as well as a service provider are present. Each service user is getting the service from only one user at a regular interval of time. Here, in this case, the service provider is stationary and service user is movable. The service provider process the data and the service user sent the data. The service user has high mobility in the network area. Here, the proposed methodologies are applied at service provider as it is processing the data.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1336
ISSN 2229-5518
Distance- To calculate the distance, this method is using the following concept. For this reason, this method takes two thresholds. The first threshold is Dmax, is the maximum distance from the service provider from the mobile node. The signal strength is Smin . These two values are determined at time of network establishment. The current signal strength is Scur . Then the formula for the current distance is
Dcur
= Dmax
* S min
S cur
(1)
Velocity- velocity is a relational parameter between the distance and time. So the formula for the velocity is
D1 − D 2
Figure 2 Architecture diagram of proposed methodology
3.1. Time Threshold Calculation for Minimizing
Handover Failures
V =
where V =velocity
t1 − t 2
(2)
D1 =distance at time t1
D2 =distance at time t 2
Data rate- The data rate is given is through the below formula.
where DR= data rate

DR = DPsen
Arec
(3)
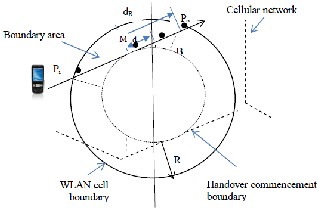
Figure 3: scheme diagram of W LAN to cellular network handover necessity estimation mechanism
Figure 3 shows the trajectory of a mobile terminal traveling over an area over which cellular network service is available and is also partially covered with a WLAN cell. The mobile terminal enters and exits the WLAN cell at points P i and Po , respectively, following a straight line. M is the middle point of the section of the trajectory inside the WLAN cell. The donut shaped area is called “boundary area”. R and r represents the radii of the outer and inner circles enclosing the boundary area, respectively. dR and dr represent the half length of the trajectory segments inside the outer and inner circles respectively. B is the intersection point of the trajectory and the inner circle.
Timing threshold
The main aim of the time threshold calculation is used to maintain the number of handover failures under a desirable threshold. For example, if the system designer has the need of limiting the probability of handover failures under 1%, then the time threshold is adjusted to make the ratio of the number of failed handovers to the total number of handovers below
1%. The time threshold is calculated using mathematical modeling and probability calculation and the parameters used for the calculation is explained below.
DPsen= total data packet sent at a time duration
Arec = total acknowledgement received at the same
time duration.
A time threshold parameter T1 is introduced to make the handover decisions: whenever the estimated traveling time tWLAN is greater than T1 , the MT will initiate the handover procedure. A handover failure occurs when the traveling time inside the WLAN cell is shorter than the handover latency from the cellular network to the WLAN, Ti. Thus, using Equation (4) the probability of a handover failure for the method using the threshold T 1 is given by 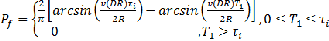 (4)
(4)
By using (4), an equation which can be used by the MT to calculate the value of T1 for a particular value of Pf when 0< Pf
<1:
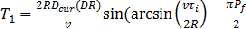 (5)
(5)
3.2.1 Traveling Time Prediction for Minimizing
Unnecessary Handovers
The method relies on the estimation of WLAN traveling time (i.e. time that the mobile terminal is expected to spend within the WLAN cell) and the calculation of a time threshold (t WLAN ). A handover to a WLAN is triggered if the WLAN coverage is available and the estimated traveling time inside the WLAN cell is larger than the time threshold. The estimated traveling time (tWLAN ) is
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1337
ISSN 2229-5518
2 2 + 2( − )
tWLAN =
R −l os v t s t pi
2
(6)
v (t s
− t in)
where R is the radius of the WLAN cell, los is the distance
between the access point and the mobile terminal takes an RSS
sample, v is the velocity of the mobile terminal, ts and t pi are
the times at which the RSS sample is taken and the mobile
terminal enters the WLAN cell coverage, respectively. los is
estimated by using the RSS information and log-distance path
loss model.
The time threshold (TWLAN ) is calculated based on various
network parameters as
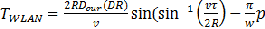 (7)
(7)
where is the handover delay from the cellular network to
the WLAN, and P is the tolerable handover failure,
unnecessary handover or connection breakdown probability.
A handover to the cellular network is initiated if the WLAN
RSS is continuously fading and the mobile terminal reaches a
handover commencement boundary area which size is
dynamic to the mobile terminal’s speed.
Similar to the arguments used in section 3.1, another
parameter T2 (T1< T2) is introduced to minimize the
probability of unnecessary handovers. By using (6) the
probability of an unnecessary handover is calculated as
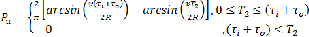 (6) Thus
(6) Thus
 (7) Equation (6) is derived from (7) for a particular value of Pu when 0 < Pu < 1. Parameters T 1 and T2 depend on the values of constants P f and Pu , which are selected by system designers.
(7) Equation (6) is derived from (7) for a particular value of Pu when 0 < Pu < 1. Parameters T 1 and T2 depend on the values of constants P f and Pu , which are selected by system designers.
They also depend on measurement of v, R, and . The
parameter T2 can be further adjusted dynamically to
encourage or discourage handovers to WLAN by considering
other performance criteria such as network load.
Parameters T1 and T 2 depend on values of constants Pf and
Pu which are selected by the system designers. They also depend on the measurement of v, D, DR, R, i and o . The
parameter T2 can be further adjusted dynamically to encourage or discourage handovers to WLAN by considering other performance criteria such as network load.
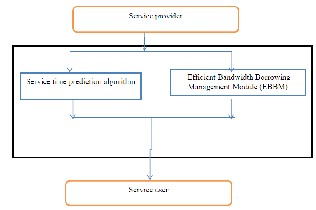
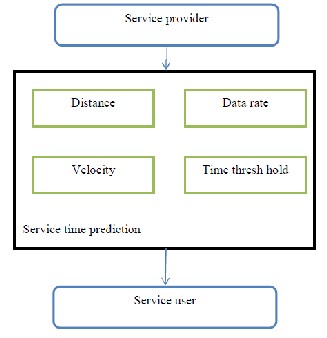
The diagram given below is the architecture diagram of the service time prediction algorithm. This phase works according to the data sharing between service provider and service user. There are few parameters on which the service time estimation depends. The parameters are distance between service provider and service user, data rate through which the service user is getting the service from the service provider, a threshold value of time that is that is set by the user, and velocity of the mobile node. These parameters are calculated at service provider using the sensors present at both service provider and service user.
Figure-4 Architecture diagram of Service time prediction algorithm
Here, it implements the service time prediction algorithm along with the bandwidth reservation in order to provide an efficient connection management algorithm for seamless mobility. The paper proposes the service time prediction method in order to remove the unnecessary handovers by considering the time the mobile terminal is expected to spend within a cell and get uninterrupted traffic services. It is based on the velocity, distance between the mobile and base station, time threshold [7], data rate and bandwidth availability of the cell.
Algorithm for phase-1
Begin
Step-1- Get the values of data rate, threshold of time, distance
and velocity as the methods described in equations (1), (2), (3)
and (7).
Step-2- Get the service time prediction method as given in
equation (3).
Step-3- Vertical handoff is done after getting time prediction
value.
Step-4- Apply the step 2 and 3 to the mobile node at a regular
interval of time that is in a highly movable state.
End
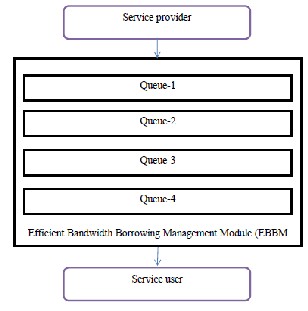
3.2.2 EBBM (Efficient Bandwidth Borrowing management Module)
EBBM module provides a set of priority queue in the paper. Different priority queues are distributed in a distinct bandwidth ratio. In addition, Minimal Bandwidth Guarantee Best Effort (MBGE) Queue proposed to avoid starvation occurs in the lower priority connection. The bandwidth disposition will be controlled by EBBM based on the classes of priorities with a view to obtain the greatest bandwidth
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1338
ISSN 2229-5518
utilization. EBBM method is also used to satisfy the QoS
requirements.
In EBBM, the bandwidth borrowing method within distinct
priority queues is presented specifically to promote the total
bandwidth utilization. Above all, the transmission quality of
the higher priority packets is concerned as well as the
prevention of starvation of the lower priority packets. When
the higher priority queues face congested; they are unable to
borrow bandwidth from the lower priority queues. If the
highest priority queues borrowed the bandwidth from the
lower priority queues, the lower priority packets would
neither enter their queues for transmission if needed nor take
their borrowed bandwidth back due to the guarantee for the
immediateness of the higher priority packet transmission. It
would lead to starvation occurred in the lower priority
queues.
EBBM makes it possible for the lower priority queues to
borrow bandwidth from the higher priority queues. The
higher priority queues are capable of taking back their
bandwidth from lower priority queues as long as their instant
bandwidth is needed. On the contrary, it is ruled that higher
priority queues are forbidden to grab the bandwidth from
lower priority queues.
The formula given below is to set up the management rules
of EBBM. Hypothetically, k and M means Queue
classifications and the capacity, respectively.
The entering data of each kind of queue is represented in
equation (4);
N
of efficient bandwidth estimation are described in the paper
[8].
Figure-5 shows the architecture diagram of Efficient Bandwidth Borrowing
Management Module
Also, this paper implements the Efficient Bandwidth Borrowing Management (EBBM) module [8] in order to guarantee the QoS in the network. The EBBM helps in efficient
ck (used )
= ∑ p (q )
i =0
(4)
utilization of bandwidth in the network by providing four
priority queues and distributing it in a different bandwidth
ratio. The Minimal Bandwidth Guarantee Best Effort (MBGE)
where, Pi means packet size,
q k means a kind of packet,
The unused capacity of each Queue is represented in equation (5);
queue is proposed here to avoid any scarcity of bandwidth in case of lower priority connection and hence helps in providing efficient utilization of bandwidth.
ck (unused )
=
ck ( M )
−
ck (used )
(5)
Algorithm for phase-2
Begin-
where, in each kind of Queue, Qck(used) denotes the used space,
Qck(M) means the capacity of Queue Q, Qck(unused) denotes the unused space.
When lower priority packets in the queues are full, the system is to detect other higher priority queues for borrowing their spare space, that is, Qck(unused)q . Furthermore, the borrowing condition must follow Formula (6).
N
Step-1- When the mobile device is getting services from the service provider, the services are divided into a set of jobs.
Step-2- The jobs are scheduled in some priority queues through Minimal Bandwidth Guarantee Best Effort (MBGE). Step-3- When lower priority packets in the queues are full, the system detects the other higher priority queues for borrowing their spare space.
Step-4- Later, the bandwidth is retrieved by the higher priority
∑ p
i =0
(q ) ≤ Q
, j<k
j
(6)
queue for providing efficient bandwidth management.
di k ck (unused )
Also, 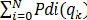 stands for the lower priorities, unable to enter their original queues. If there is spare bandwidth in the higher priorities, they can borrow them.
stands for the lower priorities, unable to enter their original queues. If there is spare bandwidth in the higher priorities, they can borrow them.
The below diagram describes the architecture of efficient bandwidth estimation. Bandwidth is related to the channel that relates service provider to the service user. So this phase of the proposed method is working at service provider level. The service provider schedules the jobs giving weightages on priorities and providing them efficient bandwidth. The details
End
Overall algorithm
Begin
Step-1- A mobile node is getting service from a service provider and services are divided into a number of jobs. As the mobile device is highly movable and jobs required more bandwidth utilization the process are given in the below steps Process 1-
Step-2- The mobile device and the service provider are having sensing data about distance and time.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1339
ISSN 2229-5518
Step-3- Process the data as given in phase two. Step-4- The information is processed to the step-8. Process-2-
Steps-5- Register the jobs provided by the service provider to
service the user at a service provider.
Step-6- Get the bandwidth utilization as mentioned in the
phase-2.
Step-7- Add it to the step 8.
Step-8- In this step, the result of step-4 and step-7 are
combined and applied. End
4. SIMULATION RESULTS
4.1 Simulation Model and Parameters
Figure 5: Simulation Topology
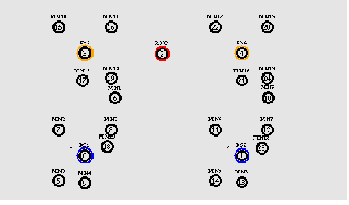
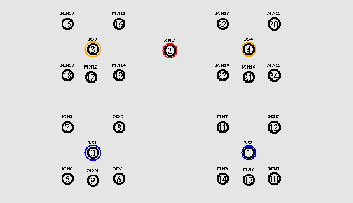
Figure 6: Handoff Scenario
To simulate the proposed Efficient Service time Prediction and Bandwidth Reservation (ESPBR) scheme, NS-2 [13] is used. In the simulation, clients (SS) and the base station (BS) are deployed in a 1000 meter x 1000 meter region for 50 seconds simulation time. It consists of 4 base stations among which, BS1 is based on WLAN and BS2 is based on 802.16
WiMAX and remaining BS3 and BS4 are based on UMTS. Each network contains 5 mobile nodes (refer figure 2). All nodes have the same transmission range of 250 meters.
At 5 seconds, MN1 from BS1 begins to handoff to BS3 of UMTS network. At the same time, MN6 from BS2 of UMTS network begins to handoff to BS4 of WiMAX network.
This is illustrated in Figure 3.
The simulation settings for UMTS and WiMAX are
presented in table 1 and table 2. The simulation settings used
for 802.11 and general parameters are summarized in table 3.
Table 1: Simulation settings for UMTS Table 2: Simulation settings for WiMAX Table3: General Simulation Settings
B. Performance Metrics
We compare our proposed Efficient Service time Prediction and Bandwidth Reservation with EBBM Technique. We mainly evaluate the performance according to the following metrics:
Throughput: It is the amount of traffic (real time or non- real time) that is received in the destination, represented in Megabits / second.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1340
ISSN 2229-5518
Delay: It is the average end-to-end delay occurred at the
destination for all flows.
Drop: It is the number of packets dropped during the data
transmission.
Delivery Ratio: It is the ratio between number of packets
received and the number of packets sent during the
transmission.
A. Based on Rate
In our first experiment, we vary the rate as 250,500,750 and
1000Kb.
18.5
18
17.5
17
16.5
16
Rate Vs Throughput
250 500 750 1000
Rate (Kb)
ESPBR EBBM
400
300
200
100
0
0.5
0.4
0.3
0.2
0.1
0
Rate Vs Delay
250 500 750 1000
Rate (Kb)
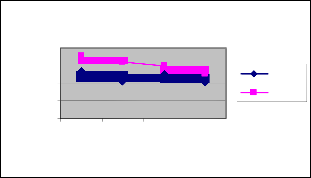
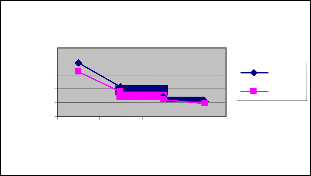
Figure 7: Rate Vs Delay
Rate Vs De lvie ryRatio
250 500 750 1000
Rate (Kb)
ESPBR EBBM
ESPBR EBBM
Figure 10: Rate Vs Throughput
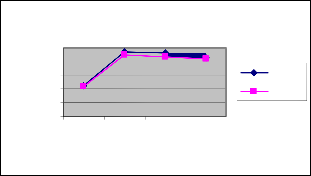
Figure 7 shows the delay of ESPBR and EBBM techniques for different rate scenario. We can conclude that the delay of our proposed ESPBR approach has 24% of less than the EBBM approach.
Figure 8 shows the delivery ratio of ESPBR and EBBM techniques for different rate scenario. We can conclude that the delivery ratio of our proposed ESPBR approach has 16% of higher than the EBBM approach.
Figure 9 shows the drop of ESPBR and EBBM techniques for different rate scenario. We can conclude that the drop of our proposed ESPBR approach has 29% of less than the EBBM approach.
Figure 10 shows the throughput of ESPBR and EBBM techniques for different rate scenario. We can conclude that the throughput of our proposed ESPBR approach has 0.5% of higher than the EBBM approach.
B. Based on Time
In the second experiment, the metrics are evaluated based on the time.
Tim e Vs Delay
80000
60000
40000
20000
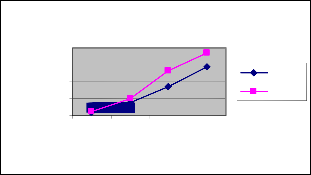
Figure 8: Rate Vs Delivery Ratio
Rate Vs Drop
ESPBR EBBM
400
300
200
100
0
Tim e(Sec)
ESPBR EBBM
0
250 500 750 1000
Rate (Kb)
Figure 11: Time Vs Delay
Figure 9: Rate Vs Drop
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 1341
ISSN 2229-5518
Tim e Vs Throughput
20
15
10
5
0
Tim e(Sec)
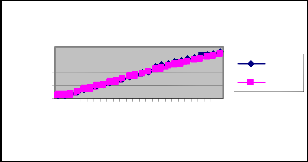
Figure 12: Time Vs Throughput
ESPBR EBBM
REFERENCES
[1] A. Dvir, R. Giladi, I. Kitroser and M. Segal, “Efficient Decision Handoff Mechanism for Heterogeneous networks”, International Journal of Wireless and Mobile Networks (IJWMN) ,Vol.2, No.1, February 2010
[2] Xiaohuan Yan, Y. Ahmet Sekerciog˘lu and Sathya Narayanan, “A survey of vertical handover decision algorithms in Fourth Generation heterogeneous wireless networks”, ©2010 Elsevier B.V.
[3] SuKyoung Lee, Kotikalapudi Sriram, Kyungsoo Kim, Yoon Hyuk Kim, and Nada Golmie, “Vertical Handoff Decision Algorithms for Providing Optimized Performance in Heterogeneous Wireless Networks”, IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, JANUARY 2009 (To appear)
[4] Debabrata Sarddar, Tapas Jana, Souvik Kumar Saha, Joydeep Banerjee
,Utpal Biswas, M.K. Naskar, “Minimization of Handoff Failure
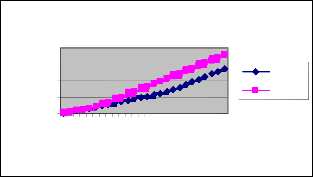
Figure 11 shows the delay of ESPBR and EBBM techniques
for different time scenario. We can conclude that the delay of
our proposed ESPBR approach has 12% of less than the EBBM
approach.
Figure 12 shows the throughput of ESPBR and EBBM
techniques for different time scenario. We can conclude that
the throughput of our proposed ESPBR approach has 2% of
higher than the EBBM approach.
5. CONCLUSION
In this paper, we have proposed an Efficient Service time Prediction and Bandwidth Reservation Technique for Vertical Handoff in 4G Networks. The mobile node is free among the network areas of different service provider. To provide latency and less failure, the service provider implements two phases of parallel procedure. These procedures are independent of another. The first method provides the seamless handoff and the second method provides an efficient bandwidth estimation technique. The above paper provides a literature work followed by an introduction to a proposed technology.
The proposed method provides a better method to guarantee QoS in the network by providing efficient bandwidth utilization method. It provides a mapping method that helps in improving the transmission quality. It also provides a method to handle handoff failure in the network to provide continuity in the communication between the mobile users.
After giving a suitable solution on latency, failure and load balancing, the future work is focusing on giving a movable node level solution for 4G networks.
Probability for Next-Generation Wireless Systems”, International
Journal of Next-Generation Networks (IJNGN) Vol.2, No.2, June 2010 [5] Debabrata Sarddar, Kaushik Mandal, Tapas Jana, Utpal Biswas and M.K. Naskar, “A Handoff Technique to Reduce False-Handoff Probability in Next Generation Wireless Networks”, (IJCSE) International Journal on Computer Science and Engineering, Vol. 02,
No. 03, 2010, 630-634
[6] Christian Makaya and Samuel Pierre, “Adaptive handoff scheme for heterogeneous IP wireless networks”, © 2008 Elsevier
[7] Abdoulaziz, Issaka Hassane, Li Renfa, and Zeng Fanzi. "Handover Necessity Estimation for 4G Heterogeneous Networks." International Journal of Information (2012).
[8] Chen, Yu-Chang, Ja-Hsing Hsia, and Yi-Ju Liao. "Advanced seamless vertical handoff architecture for WiMAX and WiFi heterogeneous networks with QoS guarantees." Computer Communications 32.2 (2009): 281-293.
[9] Ezzouhairi, Abdellatif, Alejandro Quintero, and Samuel Pierre. "Adaptive end-to-end mobility scheme for seamless horizontal and vertical handoffs." Ubiquitous Computing and Communication Journal (2010): 1-14.
[10] Saeed, Rashid A., Hafizal Mohamad, and Mazlan Abbas. "WiFi/WiMAX Seamless Convergence with Adaptive Vertical Handover for Continuity of Internet Access." Communications in Information Science and Management Engineering (2011).
[11] Qian, Hong-yan, Bing Chen, and Xiao-lin Qin. "A Novel Mobility Management Protocol Supporting Network Seamless Roaming." Journal of Networks 5.3 (2010): 367-374.
[12] Prasad, Pratap S., and Prathima Agrawal. "Movement prediction in wireless networks using mobility traces." Consumer Communications and Networking Conference (CCNC), 2010 7th IEEE. IEEE, 2010.
[13] Network Simulator: http:///www.isi.edu/nsnam/ns
IJSER © 2014 http://www.ijser.org












