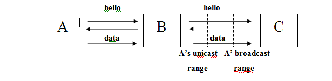International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1334
ISSN 2229-5518
Detecting Good Neighbours in Wireless Network
Prof. S.M.Shinde (HOD Computer, JSCOE), S.G.Kamthe (PG student JSCOE)
Abstract— In adhoc networks, routes could also be disconnected due to dynamic movement of nodes. So, route choice and topology combination is incredibly tough and difficult issue. Such networks are prone to each internal and external attacks[11] as there are unhealthy neighbor nodes. This drawback affects performance of routing protocol in adhoc networks. All information related with sensible neighbor area is kept in routing table to improve performance of routing protocol. Main objective is to design Mobile Ad-Hoc network with equipping every device to maintain the data needed to properly route Traffic continuously, To increase the performance of network by distinguishing good and bad nodes by adding further parameters i.e. signal strength, flow capability and relative position of a node in to the account, To minimize delay and create it energy efficientis expected outcome.
Index Terms— MANET, AODV, PDR, AEODV, SNR, DSDV, DSR.
1 INTRODUCTION
—————————— ——————————
A mobile Ad-hoc network (MANET) is a multihop wireless network supported by IEEE 802.11 has some mobile devices that we tend to referred to as network nodes. Nodes attached with one another via wireless association to each exchange
interest data in order to maintain the network property. These
devices subject to movement at random. Therefore, this sort of
network referred to as infrastructure less network and nodes need to maintain its topology. These nodes generate traffic to be forwarded to another node.
1.1 Types of MANET
Vehicular adhoc network (VANET) is basically used for communication among the vehicles and between vehicles and roadside equipment.
Internet Based Mobile Ad-hoc Networks (iMANET) are
ad-hoc networks that link mobile nodes with fixed nodes i.e.
Internet-gateway nodes. In such type of networks adhoc rout-
ing algorithms don’t apply directly.
Wireless ad hoc networks usually consist of mobile battery operated computing devices that communicate over the wireless medium. One of important parameter which has a main rule in this type of network is energy efficiency which needs to seriously manage. While the processing capacity and the memory space of computing devices increase at a very fast speed, the battery technique lags far behind. Therefore, it is critical to derive energy conservation schemes to increase the device and network operation time. Energy is indeed scarce resource in ad hoc wireless networks. Each nodeo perform function of a router along with being a source or destination. Thus the failure of some nodes operation can greatly impede performance of the network and even affect the basic availability of the network, like routing, availability. Thus it is of paramount importance to use energy efficiently when establishing communication patterns.Minimum energy routing protocols are therefor popularly used to maintain network stability.
1.2 Minimum Energy Routing Protocols
a) Minimum Total Transmission Power (MTTP) protocols: These protocols set the link cost to the transmission power and use a shortest path algorithm to search for the minimum ener- gy path. PAMAS [3] used the Dijkstra shortest path algorithm to search for the path. PARO [6] performed power aware rout- ing optimization across the MAC and Network layers. In this scheme, one or more intermediate nodes elect toforward pack- ets on behalf of the source-destination pairs to reduce the transmission power.
b) Minimum Total TransCeiving Power (MTTCP) protocols:
As the nodes consume energy not only when forward- ing packets but also when receiving packets, the protocol in [5] assigned the transmission power as well as receiving power to be the link cost metric, and used the Bellman-Ford shortest path algorithm to find the minimum energy path.
c) Minimum Total Reliable Transmission Power (MTRTP):
The authors in [6] claimed that a link cost should be a function of both the energy required for a single transmission attempt across the link and the link error rate, which determines the number of retransmission attempts needed for a successful transmission, and accordingly, proposed new minimum total reliable transmission power protocol. This protocol mainly aims to minimize the energy consumption in transmitting data packets from a source to a destination reliably
Protocols used for wired networks cannot be used in wireless networks because of dynamic movement of nodes in
network .Protocols for wireless network is different from wired network.
Section II discussed review of different adhoc protocol and section III discussed programmer design and suggest the procedure for detecting the Good neighbour and simulation
result by comparing performance of existing protocol with suggested protocol section IV after analysis of protocol pro- vide outcome of the new protocol.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1335
ISSN 2229-5518
2 RELATED WORK
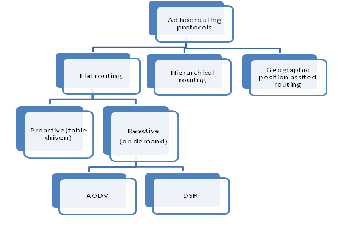
The characteristics of Manet [10] have led to the development of MANET specific routing protocol A routing protocol is the mechanism by which user traffic is directed and transported through the network from a source node to a destination node. In general, these protocols may be categorized as table driven , on-demand, and hybrid.
Fig-1 classification of protocols
2.1 Classification
a) Proactive Routing Protocols:
Routes to all or any destinations square measure maintained by causing periodical management messages. There is really redundant information measure wastage for causing the man- agement packets that is DSDV.
b) Reactive Routing Protocols:
Route is discovered if desired (on demand). Hence, it reduces
the routing overhead. It does not have to seek for and main-
tain the routes on that there is no route request. This approach is best appropriate once the network is static and traffic is lightweight .For example DSR and AODV.
c) Hybrid Routing :
The accidental network will use the hybrid routing protocols that have the advantage of each proactive and reactive routing protocols to balance the delay and management overhead. The common disadvantage of hybrid routing protocols is that it ends up in a lot of memory and power consumption.
2.2 AODV
Our paper focuses on improving the performance of AODV protocol. AODV is reactive protocol. Working of this protocol is described below.
————————————————
• Prof. S.M.Shinde is currently working as HOD , Computer Engg. Dept. JSCOE , Hadapsar,Pune ,India, E-mail: sharmi_anant@yahoo.co.uk
• S.G.Kamthe is currently pursuing masters degree program in Computer
Engineering in JSCOE,India, Ph-9766793133. E-mail: shitalkamthe10@ gmail.com
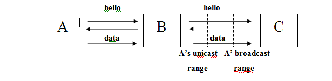
AODV protocol permits mobile nodes to quickly get routes for brand new destinations, and it doesn’t need nodes to take care of routes to destinations that don’t seem to be participated in active communication. Also, AODV routing permits mobile nodes to retort link breakages and changes in constellation in an exceedingly timely manner.the most objectives of the pro- tocol is quickly and dynamically adapt to changes of condi- tions on the network links, for instance, thanks to quality of nodes the AODV protocol works as a pure on-demand route acquisition system. Management messages utilized in AODV [7] are Route Request Message (RREQ) , Route Reply Message (RREP) , Route Error Message (RERR), Route Reply Acknowl- edgment (RREP-ACK) Message , Greeting Message.
Fig-2 Route discovery
A) Route discovery:
When a supply node needs to send a message to some
destination node, and does not have a legitimate route to the
destination, it initiates a path discovery method to find the opposite node. Source broadcasts a route request (RREQ) management packet to its neighbours, that then forward the request to their neighbour and so on either the destination or associate degree intermediate node with a brand new route to the destination is found. The AODV protocol uses destination sequence numbers to make surethat everyone routes contain the foremost recent route data. Every node maintains its own sequence range. Throughout the forwarding method the RREQ intermediate nodes record the address of the neighbour from that the primary copy of the printed packet is received in their route tables, thereby establishing a reverse path. When RREQ reaches the destination or associate degree intermediate node with a recent enough route, the intermediate node or destination node responds by unicasting a route reply (RREP) management packet back to the neighbour from that initial received the RREQ [8].
B) Route Maintenance:
A route discovered between a source node and a destination
node is maintained as long as needed by the source node. The
destination node or some intermediate node moves, the node upstream of (RERR) message to the affected active upstream neighbour/nodes. Consequently, these nodes propagate the RERR to their predecessor nodes. This process continues until the source node is reached. When RERR is received by the source node, it can either stop sending the data or reinitiate the route discovery mechanism by resending a new RREQ message if the route is still required[9,10].
C) Route expiry :
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1336
ISSN 2229-5518
If a route is not used for a certain time, a timer will expire and the route will be removed from the list of active routes (active routes are routes currently in use) in the routing table. Instead of deleting the node from routing table routing table it is kept there for some time period. If the same route is needed in that period, the existing parameters will be used for a faster route establishment. When this additional time expires, the route is deleted from the routing table.
D) Local connectivity:
A node may offer connectivity information by broadcasting Hello messages periodically.When this Hello message is re- ceived, a route to the neighbour should be added to the rout- ing table if it does not already exist. If the route exists, its life- time is increased. When the node moves structure of the ad- hoc network changes the route expires.
Neighbours are classified as ’bad’ if the quality of the inter- connecting channel is poor. AODV control messages along with Hello message are accepted only from neighbours which are ’good’. In order to differentiate between good and bad neighbours, the SNR is measured each time a packet that con- tains an AODV control message is received. Local and global connectivity of a network auto increases when good neigh- bour are present throughout the network. [4].
AODV maintains small amount of routing information and it
assumes that nodes will cooperate it is more vulnerable to
n/w attacks. In order to improve performance of AODV flow capacity, signal strength. Arrival time is used to maintain transmission range .Depending on transmission range nodes address is stored in table. As in existing system the data is send through the good neighbour, if there is good neighbour all are in some distance means, it will make some delay.
As stated in [1] performance of network increases rapidly by
considering good nodes into the account. Categorizations of
good and bad nodes depend upon signal strength, flow capac-
ity of nodes.
Paper [2] propose a novel protocol termed error-aware can- didate set routing protocol (ECSRP). ECSRP chooses a route with the nodes having enough residual battery power and avoids overusing certain routes. For multiple routes tradeoff between energy-efficiency and load balancing is used to select the optimal route. Consideration of channel condition helps to reduce the number of retransmissions and saves energy.
S. Doshi, S. Bhandare, and T.X.Brown [3] suggested minimum
energy consumption for the node in ad-hoc network by select-
ing route with minimum energy requirement. An improve-
ment of the neighbor detection algorithm based on the differ-
entiation of good and bad neighbors using signal to noise ratio
(SNR) value is proposed in [4].
An approach for MANET routing based on stability and hop-
count[5], where the stability metric considered is the residual
lifetime of a link.A decision method for the number of neces-
sary nodes in mobile ad hoc networks for covering and collect- ing data from an arranged area is proposed in[6].
MRPC in [7] identifies the capacity of a node by its residual battery energy and expected energy spent in reliably forward- ing a packet over a specific link. Such a formulation better cap-
tures scenarios where link transmission costs also depend on
physical distances between nodes and the link error rates.Ad- hoc On Demand Distance Vector Routing (AODV) [8] presents a novel algorithm for the operation of ad-hoc networks. Each Mobile host operates as a specialized router, and routes are obtained as needed (that is on-demand) with little or with no reliance on periodic advertisements. The Routing Protocol of AODV Based on Link Failure Prediction.
Qing Li, Cong Liu, Hang Hong [9] introduces the mechanism
of link failure prediction into the AODV routing protocol in the process of data transmission and increases packet delivery rate.
3 PROPOSED WORK (AEODV)
By selecting good neighbours in wireless network using route Information and considering signal strength flow capacity as well as considering energy efficient node and if good nodes are at same distance then select one which minimizes delay is main objective of the paper.
Whenever any node runs out of energy, communication links between nodes will break. This is considered as the end of the network lifetime. Since the lifetime of each node depends on energy consumption, it is important to preserve energy of these nodes in such a way that to incrase network lifetime.
To find the delay between the nodes every node update the received time of packet .Delay is calcul ated by receiving time of packet in current node minus sending time of packet by previous node and also update calculated delay in routing list.To avoid that delay, by using energy system model, one can send the data with more energy means to avoid delay by considering the highest remaining battery power, minimum number of hops and minimum amount of traffic loads[16]. Categorization of nodes is predicted on performance metrics such as transmission range and power of node, signal strength [14], capacity of node for high packet forwarding along with relative position of node [15]. Routing table maintains address of node for maintaining record of the entire nodes. Which are used for data transmission and forwarding. To find the strength of signal & number of bytes in forwording below giv- en mathematical model is used.
Transmitter Signal strength
=  S H { (SH - Streshold * T )/e } ---------------Iffarther ( T > e )
S H { (SH - Streshold * T )/e } ---------------Iffarther ( T > e )
= 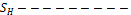 Closer ( T < e)
Closer ( T < e)
= 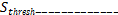 Otherwise -------------- ( 1)
Otherwise -------------- ( 1)
bvte rate
= 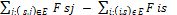
Flow of protocol is calculate transmission pow- er,transmission range & receiving power[13].Verify signal strength, flow capacity & transmission range if it matces te criteria then consider it as good neighbor make connection and broadcast message as depicted in fig-3.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1337
ISSN 2229-5518
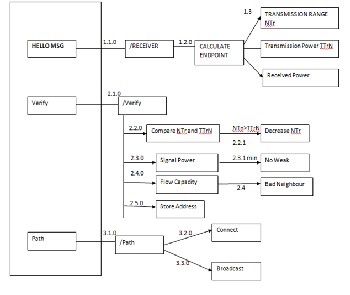
Fig-3 Data flow
4 RESULT
Proposed approach for good neighbor node detection in mobile adhoc networks is identified and comparing result with routing protocol AODV using ns2 [12] . Initially it has been assumed that all nodes have their own transmission range with nodes of dy- namic movement.
Mobility scenario is generated by using random way point model with50 nodes in an area of 500m by 500m.The simulation param- eters are mentioned below:
Table-1 Simulation parameters
(ii) Average throughput is calculated by bytes received by destination per second.
(iii)Delay by considering time to receive data. (iv) Energy efficiency of node.
Fig. [4-6] provide simulation scenario of a node.
Fig-4 Node with packet drop
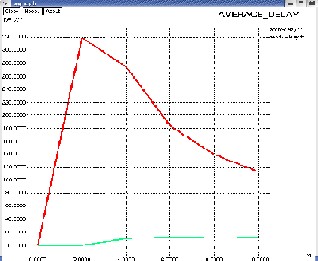
Fig-5 Delay Comparison Graph
Results are examined by delay & energy as well as PDR
& through put.The performance of suggested approach is evaluated by using following metrics:
(i) The packet delivery ratio (PDR) between the number of packets produced by CBR sources and number of packets re- ceived by CBR sink at final destination.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1338
ISSN 2229-5518
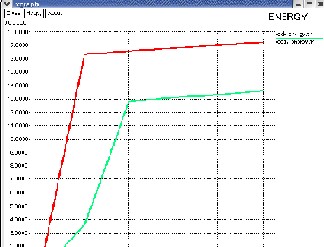
Fig-6 Energy Comparison Graph
4 CONCLUSION
Internet & wireless technologies have support one of the cele- brated techniques called Adhoc Network. Adhoc Networks are assortment of mobile nodes connected by wireless links and additionally receiving attention within the scientific community. In adhoc networks, routes are also disconnected due to dynamic movement of nodes. So, route selection and topology combination is very troublesome and challenging issue. Such networks are additional liable to each internal and external attacks due to presence of dangerous neighbour nodes. Observed problem affects the performance of routing protocol.
All information connected with smart neighbour are kept in routing table that improves performance of routing protocol in terms of excellent communication and stable route. It improves data throughput, improve overall performance of the network with in fixed and dynamic transmission range.
REFERENCES
[1] Umang Singh and Prof. B. V. R. Reddy and Prof M.N. Hoda. ” GndaDetect- ing Good Neighbour Nodes In Adhoc Routing Protocol ” 2011 IEEE.
[2] L.Tan, P.Yang, and S. Chand 2007 IEEE. ” Energy Efficient Routing Protocol
In Manets” 2007 IEEE.
[3] S. Doshi, S. Bhandare, and T.X.Brown. “An On-Demand Minimum Energy
Routing Protocol For A Wireless AdHoc Network” Volume 6 Issue 3 July
2002 , pp. 50-66.
[4] Srdjan Krco and Marina Dupcinov, “ Improved Neighbor Detection Algoithm for AODV Routing Protocol”, IEEE communications letters, vol. 7, no. 12, December 2003.
[5 ] Sridhar K N and Mun Choon Chan “Stability and Hop-Count based Approach for Route Computation in MANET” , 0-7803-9428-3/05/$20.00 ©2005 IEEE Youngrag Kim, Shuhrat Dehkanov, Heejoo Park, Jaeil Kim
[6] Chonggun Kim “The Number of Necessary Nodes for Ad Hoc Network Areas”
2007 IEEE Asia-Pacific Services Computing Conference
[7] A. Misra and S.Banerjee”Mrpc: Maximizing Network Lifetime For Reliable
Routing In wireless Environments” IEEE 2002
[8] C. E. Perkins and E. M. Royer, “Ad hoc on demand distance vector (AODV)
routing,” Internet-Draft, draft-ietf-manet-aodv-02.txt, Nov.1998
[9] Qing Li, Cong Liu, Hang Hong Jiang, “The Routing Protocol of AODV Based on Link Failure Prediction”, ICSP2008 Proceedings, 978-1-4244-2179-
4/08/$25.00 ©2008 IEEE
[10] C. Siva Ram Murthy and B.S.Manoj, “Ad hoc Wireless Networks”,Pearson
2005. ISBN 81-297-0945- 7
[11] H. Yang, X. Meng, and S. Lu, “Self-Organized Network-Layer Security in Mo bile Adhoc Networks.International Conference on Mobile Computing and Networking”, Atlanta, GA, USA, 2002, 11-20.
[12] www.isi.edu/nsnam
[13] P.Santi, “Topological Control in Wireless Adhoc and Sensor Networks”, John
Wiley & Sons Ltd.,2005
[14] P. Gupta and P. R. Kumar, “The Capacity of Wireless Networks”, IEEE Trans actions on Information Theory, 46(2): 388-404,2000
[15] P. Gupta, P. R. Kumar, “Critical Power for Asymptotic Connectivity in Wireless Network” In W. M. McEneany, G. Yin, and Q, Zhang, editors, Stochastic Analysis Control, Optimization and Applications,pages 547-566, Birkhauser, Boston,
MA, 1998.
[16] Imad S. AlShawi, Lianshan Yan, Wei Pan, Bin Luo” Lifetime Enhancement in Wireless Sensor Networks Using Fuzzy Approach and A-Star Algorithm” IEEE SENSORS JOURNAL, VOL. 12, NO. 10, OCTOBER 2012
IJSER © 2014 http://www.ijser.org