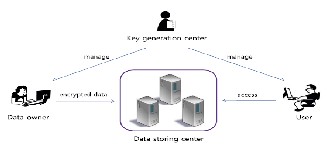
Junbeom Hur proposed a CP-ABE scheme[1] for a secure data
Fig.1 Architecture of data sharing center
International Journal of Scientific & Engineering Research, Volume 6, Issue 4, April-2015 121
ISSN 2229-5518
Ciphertext Policy - Attribute Based Encryption (CP-ABE) System Solution for Securely Sharing Images Owned by One Stakeholder with
Unknown Stakeholder
Miss. Pooja Tandale, Mr. Sidheshwar Khuba
Abstract— One of the most challenging issues in sharing systems is the enforcement of access policies and the policies updates support. Ciphertext policy attribute-based encryption (CP-ABE) is a promising cryptographic solution to this issue. Cipher text – Attribute Based Encryption scheme enables an encryptor to define the attribute set over a universe of attributes that a decryptor needs to possess in order to decrypt the ciphertext. Thus, each viewer with a different set of attributes is allowed to decrypt different pieces of data per the security policy. It is designed to use CP-ABE scheme to improve security and efficiency in attribute based image sharing. The designed image sharing system includes Key Generation Center, Image Owner, Image Viewer, Image Server system entities that helps to share image securely using CP-ABE scheme. Here, specifically focus is on sharing image in ‘.jpg/.jpeg’ format.
Index Terms— Image security, Image sharing system, Attribute base encryption, Access Control, Network security, CP-ABE, Image
Encryption.
—————————— ——————————
etwork and computing technology enables many people to easily share their data with others are using online external storages. People can share their lives with friends by uploading their private photos or messages into the online social networks; or upload highly sensitive personal health records (PHRs) into online data servers such as Mi- crosoft Health Vault, Google Health for ease of sharing with their primary doctors or for cost saving. As people enjoy the advantages of these new technologies and services, their con- cerns about data security and access control also arise. Im- proper use of the data by the storage server or unauthorized access by outside users could be potential threats to their data. People would like to make their sensitive or private data only accessible to the authorized people with credentials they speci-
fied.
Attribute based encryption (ABE) comes in two types
called key-policy ABE (KP-ABE) and ciphertext-policy ABE. In
KP-ABE, attributes are used to describe the encrypted data
and policies are built into users’ keys; while in CP-ABE, the
attributes are used to describe users’ credentials, and an en-
cryptor determines a policy on who can decrypt the data. Be-
tween the two approaches, CP-ABE is more appropriate to the
data sharing system because it puts the access policy decisions
in the hands of the data owners [2], [3].
Most of the existing ABE schemes are constructed on the
architecture where a single trusted authority, or KGC has the
power to generate the whole private keys of users with its
————————————————
• Miss. Pooja Tandale , currently pursuing masters degree in computer science and engineering at NKOCET in Solapur University,India.
E-mail: tandalepooja11@gmail.com
• Mr.Sidheshwar Khuba, Professor in department of computer science and engineering at NKOCET in Solapur University, India.
E-mail: sa.khuba@gmail.com
master secret information [4], [5], [9]. Thus, the key escrow problem is inherent such that the KGC can decrypt every ci- phertext addressed to users in the system by generating their secret keys at any time. Chase and Chow [6] presented a dis- tributed KP-ABE scheme that solves the key escrow problem in a multiauthority system. Chow [7] proposed an anonymous private key generation protocol in identity-based literature such that the KGC can issue a private key to an authenticated user without knowing the list of users’ identities Bethencourt et al. [4] and Boldyreva et al. [8] proposed first key revocation mechanisms in CP-ABE and KP-ABE settings, respectively. These schemes enable an attribute key revocation by encrypt- ing the message to the attribute set with its validation time.
It would be interesting to consider attribute-based en- cryption systems by applying advanced cryptosystem for data sharing. Designed system should encrypt images.

Junbeom Hur proposed a CP-ABE scheme[1] for a secure data
Fig.1 Architecture of data sharing center
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 4, April-2015 122
ISSN 2229-5518
sharing system. The key issuing protocol generates and issues user secret keys by performing a secure two-party computa- tion (2PC) protocol between the KGC and the data storing cen- ter with their own secrets. The 2PC protocol deters them from obtaining any master secret information of each other such that none of them could generate the whole set of user keys alone. The privacy and data confidentiality can be crypto- graphically enforced against any KGC or data storing center.
Thus, existing system is efficient to securely manage the data distributed in the data sharing system..
Designed Ciphertext Policy - Attribute Based Encryption (CP- ABE) system securely share image owned by one stakeholder with unknown stakeholder. The KGC is responsible for the attribute key management as in the previous CP-ABE schemes without leaking any confidential information to the other par- ties. Therefore, designed system is the most suitable for the image sharing scenarios where users encrypt the image and upload it to the image server. The designed system share
‘.jpg/.jpeg’ image securely in distributed system using CP- ABE scheme.
The designed system architecture is depicted in Fig 2, which includes the following system entities:
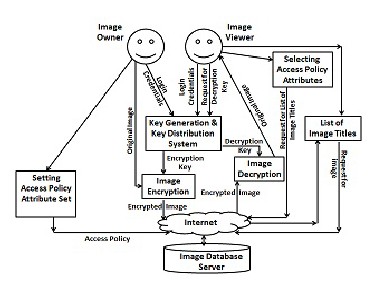
Fig. 2 System Architecture
The designed system securely share image owned by one stakeholder with unknown stakeholder using ciphertext poli- cy attribute based encryption technique.So the designed sys- tem helps to improve image security and specific access con- trol for improper use of the data by the storage server or unau- thorized access by outside users.
I place on record and warmly acknowledge the continuous encouragement, in valuable supervision, timely suggestions and inspired guidance offered by Prof. Sidheshwar A. Khuba, Professor, Department of Computer Science and Engineering, Nagesh Karajagi Orchid College of Engineering &Technology, Solapur.
[1] J.-M. Zhu and J.-F. Ma, “Improving Security and Efficiency in Attribute Based
Data Sharing,” IEEE Transactions on knowledge and data engineering , vol.
25, no. 10, october 2013
[2] L. Ibraimi, M. Petkovic, S. Nikova, P. Hartel, and W. Jonker, “Mediated Ci- phertext-Policy Attribute-Based Encryption and Its Application,” Proc. Int’l Workshop Information Security Applications (WISA ’09), pp. 309-323, 2009.
[3] S. Yu, C. Wang, K. Ren, and W. Lou, “Attribute Based Data Sharing with Attribute Revocation,” Proc. ACM Symp. Information, Computer and Comm. Security (ASIACCS ’10), 2010.
[4] J. Bethencourt, A. Sahai, and B. Waters, “Ciphertext-Policy Attribute-Based
Encryption,” Proc. IEEE Symp. Security and Privacy, pp. 321-334, 2007.
[5] X. Liang, Z. Cao, H. Lin, and D. Xing, “Provably Secure and Efficient Bound- ed Ciphertext Policy Attribute Based Encryption,” Proc. Int’l Symp. Infor- mation, Computer, and Comm. Security (ASIACCS), pp. 343-352, 2009.
[6] M. Chase and S.S.M. Chow, “Improving Privacy and Security in Multi- Authority Attribute-Based Encryption,” Proc. ACM Conf. Computer and Comm. Security, pp. 121-130, 2009.
[7] S.S.M. Chow, “Removing Escrow from Identity-Based Encryption,” Proc. Int’l
Conf. Practice and Theory in Public Key Cryptography (PKC ’09), pp. 256-276,
2009.
[8] A. Boldyreva, V. Goyal, and V. Kumar, “Identity-Based Encryption with
Efficient Revocation,” Proc. ACM Conf. Computer and Comm. Security, pp.
417-426, 2008.
[9] V. Goyal, A. Jain, O. Pandey, and A. Sahai, “Bounded Ciphertext Policy At- tribute-Based Encryption,” Proc. Int’l Colloquium Automata, Languages and Programming (ICALP), pp. 579-591, 2008.
IJSER © 2015 http://www.ijser.org