International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1458
ISSN 2229-5518
A Systematic Literature Survey on Network Attacks, Classification and Madels For Anomaly– Based Network Intrusion Detection Systems
Rachna Nagdev, Anurag Jain
Abstract - The importance of network security has rown tremendously and a number of devices have been introduced to improve the security of a network. Network intrusion detection systems (NIDS) are among the most widely deployed such system. Popular NIDS use a collection of signatures of known security threats and viruses, which are used to scan each packet's payload. Most IDSs lack the capability to detect novel or previously unknown attacks. A special type of IDSs, called Anomaly Detection Systems, develop models based on normal system or network behavior, with the goal of de- tecting both known and unknown attacks. Anomaly detection systems face many problems including high rate of false alarm, ability to work in online mode, and scalability. This paper presents a selective survey of incremental approaches for detecting anomaly in normal system and network traffic.
Index Terms— Computer Networks, Network Security, Anomaly Detection, Intrusion Detection.
—————————— ——————————
HIS field of intrusion detection has received increasing attention in recent years. One reason for this is the explo- sive growth of the Internet and the large number of net-
worked systems that exist in all types of organizations. The increase in the number of networked machines has lead to an increase in unauthorized activity, not only from external at- tackers, but also from internal attackers, such as disgruntled employee and people abusing their privileges for personal gain.
Security is a big issue for all networks in today’s enterprise environment. Hackers and intruders have made many suc- cessful attempts to bring down high-profile company net- works and web services. Many methods have been developed to secure the network infrastructure and communication over the Internet, among them the use of firewalls, encryption, and virtual private networks. Intrusion detection is a relatively new addition to such techniques. Intrusion detection methods started appearing in the last few years. Using intrusion detec- tion methods, you can collect and
use information from known types of attacks and find out if someone is trying to attack your network or particular hosts. The information collected this way can be used to harden your network security, as well as for legal purposes. Both commer- cial and open source products are now available for this pur- pose. Many vulnerability assessment tools are also available in the market that can be used to assess different types of securet ty holes present in your network.
————————————————
• Rachana Nagdev, Computer Science dept ,Radharaman Institute of Tech- nology,RGPV University ,India . E-mail: (rachna.nagdev@gmail.com)
• Anurag Jain, HOD Computer Science dept. , Radharaman Institute of
Technology ,India. E-mail: (anurag.akjain@gmail.com)
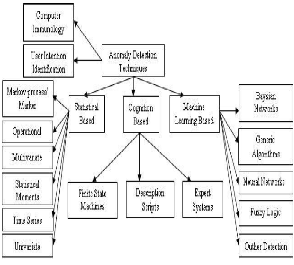
All the classification of intrusion detection sytem is described below as shown in fig(1).
Operational Model/ Threshold Metric
The count of events that occur over a period of time deter- mines the alarm to be raised if fewer then “m” or more than “n”events occur. This can be visualized in Win2k lock, where a user after “n” unsuccessful login attempts here lower limit is “0” and upper limit is “n”. Executable files size downloaded is restricted in some organizations about 4MB.The difficulty in this sub-model is determining m and n[2].
Markov Process or Marker Model:
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1459
ISSN 2229-5518
The Intrusion detection in this model is done by investigating the system at fixed intervals and keeping track of its state a probability for each state at a given time interval Is. The change of the state of the system occurs when an event hap- pens and the behavior is detected as anomaly if the probability of occurrence of that state is low. The transitions between cer- tain commands determine the anomaly detection where com- mand sequences were important.
Statistical Moments or Mean and Standard
Deviation Model:
In statistical mean, standard deviation, or any other correla- tions are known as a moment. If the event that falls outside the set interval above or below the moment is said to be anoma- lous. The system is subjected to change by considering the aging data and making changes to the statistical rule data base. There are two major advantages over an operational model. First, prior knowledge is not required determining the normal activity in order to set limits; Second, determining the confidence intervals depends on observed user data, as it var- ies from user to user. Threshold model[2] lacks this flexibility. The major variation on the mean and standard deviation mod- el is to give higher weights for the recent activities.
Multivariate Model:
The major difference between the mean and standard devia- tion model is based on correlations among two or more met- rics. If experimental data reveals better judicious power can be achieved from combinations of related measures rather than treating them individually.
Time Series Model:
Interval timers together with an event counter or resource measure are major components in this model. Order and inter- arrival times of the observations as well as their values are stored. If the probability of occurrence of a new observation is too low then it is considered as anomaly. The disadvantage of this model is that it is more computationally expensive.
Finite State Machine
A finite state machine (FSM) or finite automation is a model of behavior captured in states, transitions and actions. A state contains information about the past, i.e. any changes in the input are noted and based on it transition happens. An action is a description of an activity that is to be performed at a given moment. There are several action types: entry action, exit ac- tion, and transition action
Description Scripts
Numerous proposals for scripting languages, which can de- scribe signatures of attacks on computers and networks, are given by the Intrusion Detection community. All of these scripting languages are capable of identifying the sequences of specific events that are indicative of attacks.
Adept Systems
Human expertise in problem solving is used in adept systems. It solves uncertainties where generally one or more human experts are consulted. These systems are efficient in certain problem domain, and also considered as a class of artificial intelligence (AI) problems. Adept Systems are trained based on extensive knowledge of patterns associated with known attacks provided by human experts.
Cognition Based Detection Techniques:
Cognition-Based (also called knowledge-based or expert sys- tems) Detection Techniques work on the audit data classifica- tion technique, influenced by set of predefined rules, classes and attributes identified from training data,set of classification rules, parameters and procedures inferred.
Boosted Decision Tree
Boosted Tree (BT), that uses ADA Boost algorithm to generate many Decision Trees classifiers trained by different sample sets drawn from the original training set, is implemented in many IDS successfully [2,8]. All hypotheses, produced from each of these classifiers, are combined to calculate total learn- ing error, thereby arriving at a final composite hypothesis.
Support Vector Machine
Support vector machines (SVM), reliable on a range of classifi- cation tasks, are less prone to over-fitting problem, and are effective with unseen data. The basic learning process of the SVM includes two phases: 1) Mapping the training data from the original input space into a higher dimensional feature space, using kernels to transform a linearly non separable problem into a linearly separable one, 2) Finalizing a hyper plane within the feature space, with a maximum margin using Sequential Minimal Optimization (SMO) or Osuna’s method.
Artificial Neural Network
Artificial Neural network (ANN) architectures [1](popular one being , Multilayer Perceptron (MLP), a layered feed-forward topology in which each unit performs a biased weighted sum of their inputs and pass this activation level through a transfer function to produce their output), are able to identify not read- ily observable patterns, however MLP is ineffective with new data. For general signal processing and pattern recognition problems, another branch of ANN that makes use of radial basis function, called The Modified Probabilistic Neural Net- work [3](related to General Regression Neural Network (GRNN) classifier and generalization of Probabilistic Neural Network (PNN)), was introduced by Zaknich. It assigns the
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1460
ISSN 2229-5518
clusters of input vectors rather than each individual training case to radial units.
Machine learning techniques[5] to detect outliers in datasets from a variety of fields were developed by Gardener (use a One-Class Support Vector Machine (OCSVM) to detect anom- alies in EEG data from epilepsy patients ) and Barbara (pro- posed an algorithm to detect outliers in noisy datasets where no information is available regarding ground truth, based on a Transductive Confidence Machine (TCM) [7].Unlike induction that uses all data points to induce a model, transduction, an alternative, uses small subset of them to estimate unknown attributes of test points. To perform online anomaly detection on time series data in, Ma and Perkins presented an algorithm using support vector regression. Ihler et al. present an adap- tive anomaly detection algorithm that is based on a Markov- modulated Poisson process model, and use Markov Chain Monte Carlo methods in a Bayesian approach to learn the model parameters [10].
Common Attacks and Vulnerabilities and Role of NIDS
Current NIDSs requires substantial amount of human inter- vention and administrators for an effective operation. There- fore it becomes important for the network administrators to understand the architecture of NIDS, and the well known at- tacks and the mechanisms used to detect them and contain the damages. In this section, we discuss some well known attacks, exploits, and vulnerabilities in the end host operating systems, and protocols.
Confidentiality: In such kinds of attacks, the attacker gains access to confidential and otherwise inaccessible data.
Integrity: In such kinds of attacks, the attacker can modify the system state and alter the data without proper authorization from the owner.
Availability: In such kinds of attacks, the system is either shut down by the attacker or made unavailable to general users. Denial of Service attacks fall into this category.
Control: In such attacks the attacker gains full control of the system and can alter the access privileges of the system there- by potentially triggering all of the above three attacks.
Attacks detected by a NIDS
A number of attacks can be detected by current generation of
NIDS. Some of these are listed and described below.
Scanning Attack
In such attacks, an attacker sends various kinds of packets to
probe a system or network for vulnerability that can be ex- ploited. When probe packets are sent the target system re- sponds; the responses are analyzed to determine the character- istics of the target system and if there are vulnerabilities. Thus scanning attack [1] essentially identifies a potential victim. Network scanners, port scanners, vulnerability scanners, etc are used which yields these information. Once the victim is identified, the attacker can penetrate them in a specific way. Scanning is typically considered a legal activity and there are a number of examples and applications that employ scanning. The most well known scanning applications are Web search engines. On the other hand independent individual ay scan a network or the entire Internet looking for certain information, such as a music or video file. Some well-known malicious scanning include Vertical and Horizontal port scanning, ICMP (ping) scanning, very slow scan, scanning from multiple ports and scanning of multiple IP addresses and ports. NIDS signa- tures can be devised to identify such malicious scanning activ- ity from a legitimate scanning activity with fairly high degree of accuracy.
Denial of Service (DoS) Attacks
A Denial of Service attack attempts to slow down or complete- ly shut down a target so as to disrupt the service and deny the legitimate and authorized users an access. Such attacks are very common in the Internet where a collection of hosts are often used to bombard web servers with dummy requests. Such attacks can cause significant economic damage to ecom- merce businesses by denying the customers an access to the business. There are a number of different kinds of DoS attacks [7], some of which are mentioned below.
Flaw Exploitation DoS Attacks
In such attacks, an attacker exploits a flaw in the server soft- ware to either slow it down or exhaust it of certain resources. Ping of death attack is one such well known attack. A ping of death (POD) [1] is a type of attack on a computer that involves sending a malformed or otherwise malicious ping to a com- puter. A ping is normally 64 bytes in size (or 84 bytes when IP header is considered); many computer systems cannot handle a ping larger than the maximum IP packet size, which is
65,535 bytes. Sending a ping of this size can crash the target computer. Some limitations of the protocol implementation also lead to vulnerability which can be exploited to implement DoS attacks[6] such as DNS amplification attack which uses ICMP echo messages to bombard a target. For these attacks, a signature can be devised easily, such as to determine a ping of death attack a NIDS needs to check the ping flag and packet size.
Flooding DoS Attacks
In a flooding attack, an attacker simply sends more requests to a target that it can handle. Such attacks can either exhaust the processing capability of the target or exhaust the network bandwidth of the target, either way leading to a denial of ser- vice to other users. DoS attacks are extremely difficult to com-
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1461
ISSN 2229-5518
bat, as these do not exploit any vulnerability in the system, and even an otherwise secure system can be targeted. A more dangerous version of DoS attack [5] is called Distributed De- nial of Service attack (DDoS), which uses a large pool of hosts to target a given victim host. A hacker (called botmaster) can initiate a DDoS attack by exploiting vulnerability in some computer system, thereby taking control of it and making this the DDoS master. Afterwards the intruder uses this master to communicate with the other systems (called bots) that can be compromised. Once a significant number of hosts are com- promised, with a single command, the intruder can instruct them to launch a variety of flood attacks against a specified target.
Penetration Attacks
In penetration attack [1], an attacker gains an unauthorized control of a system, and can modify/alter system state, read files, etc. Generally such attacks exploit certain flaws in the software, which enables the attacker to install viruses, and malware in the system. The most common types of penetra- tion attacks are:
User to root: A local user gets the full access to every compo- nent of the system.
Remote to user: A user across the network gains a user ac- count and the associated controls.
Remote to root: A user across the network gains the complete control of the system.
Remote disk read: An attacker on the network gains access to the inaccessible files stored locally on the host.
Remote disk write: An attacker on the network not only gains access to the inaccessible files stored locally on the host, but can also alter them.
SSH Attack
SSH attacks are a main area of concern for network managers, due to the danger associated with a successful compromise. The fact that the number of people using and relying on the Internet is increasing rapidly makes breaking into and com- promising systems an ever more lucrative activity for hackers. One popular class of attack targets is that of Secure Shell (SSH) daemons. By means of SSH[1], a hacker can gain access to and potentially full control over remote hosts. Once compromised, a hacker can sabotage not only the host itself, but also use it for attacking other systems. The detection of intrusions, espe- cially in the case of SSH, is therefore crucial for preventing damage to hosts and networks.
Intrusion Detection System (IDS) is software that automates the intrusion detection process and detects possible intrusions.
Intrusion Detection Systems serve three essential security functions: they monitor, detect, and respond to unauthorized activity by company insiders and outsider intrusion. An IDS is composed of several components:
Sensors[11] which generate security events; Console to moni- tor events and alerts and control the sensors Central Engine that records events logged by the sensors in a database and uses a system of rules to generate alerts from security events received.
In many simple IDS implementations [12] these three compo- nents are combined in a single device or appliance. More spe- cifically, IDS tools aim to detect computer attacks and or com- puter misuse, and to alert the proper individuals upon detec- tion.
IDSs use policies to define certain events that, if detected will issue an alert. In other words, if a particular event is consid- ered to constitute a security incident, an alert will be issued if that event is detected. Certain IDSs have the capability of sending out alerts, so that the administrator of the IDS will receive a notification of a possible security incident in the form of a page, email, or SNMP trap [9]. Many IDSs not only recog- nize a particular incident and issue an appropriate alert, they also respond automatically to the event. Such a response might include logging off a user, disabling a user account, and launching of scripts. IDSs are an integral and necessary ele- ment of a complete information security infrastructure per- forming as “the logical complement to network firewalls”
.Simply put, IDS tools allow for complete supervision of net- works, regardless of the action being taken, such that infor- mation will always exist to determine the nature of the securi- ty incident and its source. Ideally the team’s network is sepa- rated from the outside world by a well designed firewall. The outside world includes the team’s host organization. Firewalls protect a network and attempt to prevent intrusions, while IDS tools detect whether or not the network is under attack or has, in fact, been breached. IDS tools thus form an integral part of a thorough and complete security system. They don’t fully guarantee security, but when used with security policy, vulnerability assessments, data encryption, user authentica- tion, access control, and firewalls, they can greatly enhance network safety. IDS can also be used t o monitor network traf- fic[9], thereby detecting if a system is being targeted by a net- work attack [10]such as a DoS attack. IDSs remain the only proactive means of detecting and responding to threats that stem from both inside and outside a corporate network.
Intrusion detection tools use several techniques to help them determine what qualifies as an intrusion versus normal traf- fic[9]. Whether a system uses anomaly detection, misuse de- tection, target monitoring, or stealth probes, they generally fall into one of two categories:
• Host-based IDSs (HIDS) – examine data held on individual computers that serve as hosts. The network architecture of host-based [5] is agent-based, which means that a software agent resides on each of the hosts that will be governed by the
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1462
ISSN 2229-5518
system.
• Network-based IDSs (NIDS) – examine data exchanged between computers[5]. More efficient host-based intrusion detection systems are capable of monitoring and collecting system audit trails in real time as well as on a scheduled basis, thus distributing both CPU utilization and network overhead and providing for a flexible means of security administration.
IDSs can also be categorized according to the detection ap- proaches they use[8]. Basically, there are two detection meth- ods: misuse detection and anomaly detection. The major def- erence between the two methods is that misuse detection iden- tifies intrusions based on features of known attacks while anomaly detection analyzes the properties of normal behavior. IDSs that employ both detection methods are called hybrid detection-based IDSs. Examples of hybrid detection-based IDSs are Hybrid NIDS using Random Forests and NIDES[4]. The following subsections explain the two detection ap- proaches.
4.1 Misuse Detection
Misuse detection catches intrusion in terms of the characteris- tics of known attacks. Any action that conforms to the pattern of a known attack or vulnerability is considered as intrusive. The main issues in misuse detection system are how to write a signature that encompasses all possible variations of the perti- nent attack. And how to write signatures that do not also match non-intrusive activity. Block diagram fig.(a) of misuse based detection system is as following. Misuse detection iden- tifies intrusions by matching monitored events to patterns or signatures of attacks. The attack signatures are the characteris- tics associated with successful known attacks The major ad- vantage of misuse detection is that the method possesses high accuracy in detecting known attacks. However, its detection ability is limited by the signature database. Unless new attacks are transformed into signatures and added to the database, misuse-based IDS cannot detect any attack of this type. Defer- ent techniques such as expert systems, signature analysis, and state transition analysis are utilized in misuse detection.
4.2 Anomaly Detection System
It is based on the normal behavior of a subject (e.g. a user or a system). Any action that significantly deviates from the nor- mal behavior is considered as intrusive. That means if we could establish a normal activity profile for a system, then we can flag all system states varying from established profile. There is a important difference between anomaly based and misuse based technique that the anomaly based try to detect the compliment of bad behavior and misuse based detection system try to recognize the known bad behavior. In this case we have two possibilities: (1)False positive: Anomalous activi- ties that are not intrusive but are flagged as intrusive. (2) False Negative: Anomalous activities that are intrusive but are
flagged as non intrusive. The block diagram fig.(b) of anomaly detection system is as following: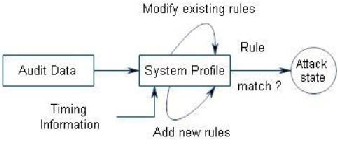
Fig.(a) Misuse Detection System
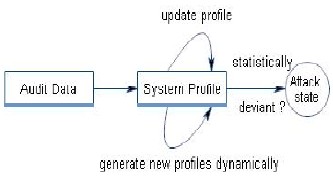
Fig.(b) Anomaly Detection System
Anomaly detection assumes that intrusions are anomalies that necessarily differ from normal behavior. Basically, anomaly detection establishes a profile for normal operation and marks the activities that deviate significantly from the profile as at- tacks. The main advantage of anomaly detection is that it can detect unknown attacks[13, 14] However, this advantage is paid for in terms of a high false positive rate because, in prac- tice, anomalies are not necessarily intrusive. Moreover, anom- aly detection cannot detect the attacks that do not obviously deviate from normal activities. As the number of new attacks increases rapidly, it is hard for a misuse detection approach to maintain a high detection rate. In addition, modeling attacks is a highly qualified and time- consuming job that leads to a heavy workload of maintaining the signature database . On the other hand, anomaly detection methods that discover the intrusions through heuristic learning are relatively easy to maintain.
When there is an intruder who has no idea of the legitimate user’s activity patterns, the probability that the intruder’s ac- tivity is detected as anomalous should be high. Four possibili- ties in such a situation, each with a non-zero probability.
• Intrusive but not anomalous: An IDS may fail to detect this type of activity since the activity is not anomalous.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 5, May-2014 1463
ISSN 2229-5518
But, if the IDS detects such an activity, it may report it as a false negative because it falsely reports the absence of an intrusion when there is one.
• Not intrusive but anomalous: If the activity is not intru- sive, but it is anomalous, an IDS may report it as intrusive. These are called false positives because an intrusion detec- tion system falsely reports intrusions.
• Not intrusive and not anomalous: These are true nega- tives; the activity is not intrusive and should not be re- ported as intrusive.
• Intrusive and anomalous: These are true positives; the ac- tivity is intrusive and much be reported as such.
In this paper, we review IDS tools are becoming increasingly necessary. They round out the security arsenal, working in conjunction with other information security tools, such as firewalls, and allow for the complete supervision of all net- work activity. It is very likely that IDS capabilities will become core capabilities of network infrastructure (such as routers, bridges and switches) and operating systems. In future we would like to find out how data mining can help improve in- trusion detection and most of all anomaly detection. For that purpose we have to understand how an IDS work to identify an intrusion. By identifying bounds for valid network activity, data mining will aid an analyst to distinguish attack activity from common everyday traffic on the network. This will re- quire, I believe, combination of multiple complicated methods to cover all of the difficulties will make it even more time con- suming.
1. Alex Lam, "New IPS to Boost Security, Reliability and Performance of the Campus Network," Newsletter of Computing Services Center, 2005.
2. B.Pfahringer, "Winning the KDD99 Classification
Cup: Bagged Boosting," in SIGKDD Explorations,
2000.
3. D. Barbar´a, C. Domeniconi and J. Rogers, “Detecting
outliers using transduction and statistical testing”
ACM
4. D. Dasgupta, ”An artificial immune system as a mul-
tiagent decision support system” IEEE International
Conference on Systems, Man and Cybernetics, Oct.
1998, pp. 3816-3820
5. FBI agents bust 'Botmaster', Reuters News Service,
November 4, 2005.
6. Internet Denial of Service: Attack and Defense Mech-
anisms, by Jelena Mirkovic, Sven Dietrich, David Dit-
trich and Peter Reiher, Prentice Hall PTR, ISBN
0131475738, 2005.
7. J. Ma and S. Perkins, “Online novelty detection on temporal sequences” ACM SIGKDD International Conference on Knowledge Discovery and Data Min- ing (KDD), Washington, DC, Aug. 2003.
8. Levin, "KDD-99 Classifier Learning Contest: LLSoft‟s
Results Overview" SIGKDD Explorations, 2000.
9. LI Yongzhong,YANG Ge,XU Jing Zhao Bo “A new in-
trusion detection method based on Fuzzy HMM
“IEEE Volume 2, Issue 8, November 2008.
10. A. Ihler, J. Hutchins, and P. Smyth, “Adaptive event
detection with time-varying Poisson processes” ACM SIGKDD Int. Conf. on Knowledge Discovery and Da- ta Mining (KDD), Philadelphia, PA, Aug. 2006.
11. SK Sharma, P Pandey, SK Tiwar “An improved net- work intrusion detection technique based on k-means clustering via Naïve bayes classification” IEEE Vol-
ume 2, Issue 2, February 2012, Issn 2151-961.
12. Tarem Ahmed, Boris Oreshkin and Mark Coates, De-
partment of Electrical and Computer Engineering
McGill University Montreal, QC, Canada “Machine
Learning Approaches to Network Anomaly Detec-
tion” in Workshop on Tackling Computer Systems
Problems with Machine Learning Techniques, 2007.
13. Vaughn, Randal and Evron, Gadi (2006), "DNS Am-
plification Attacks," March 17, 2007.
14. Zhenglie Li”Anomaly Intrusion Detection Method
Based on K-Means Clustering Algorithm with Particle
Swarm Optimization “Springer Volume 4, Issue 2,
April 2011.
IJSER © 2014 http://www.ijser.org