International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 191
ISSN 2229-5518
A Novel Multi Stream Superposition Multi Rate
Coded Modulation (MS-SMRCM)
Ahmed E. Zein Eldin, Esam A.A. Hagras, Hala Mansour Abdel-Kader
Abstract—This paper is concerned with the design of a wireless data transmission which provides Un-equal Error Protection (UEP). A Multi Stream Superposition Multi Rate Coded Modulation (MS-SMRCM) system has been introduced. In the proposed MS-SMRCM, each user data bit stream can be divided into two bit streams. The first bit stream represents the region of high priority, while the second represents the region of low priority. These two bit streams are encoded, spread and interleaved separately. The resultant chip interleaved sequences are modulated and superimposed together to achieve UEP at the receiver side. A simple Chip-By-Chip (CBC) iterative Multi User Detection (MUD) strategy is used. In AW GN channel, the proposed MS-SMRCM in case of eight users input, the performance of
single user is better than eight users by 2.2 dB at BER = 10−4. The performance is investigated over AW GN and Rayleigf fading channels in
the presence of High Power Amplifier (HPA).
Index Terms— CBC Iterative MUD, HPA, MS-SMRCM, UEP, AW GN, Rayleigh Fading Channel.
—————————— ——————————
NY communication channel is characterized by a so- called channel capacity. Operating near capacity implies power efficiency and simultaneously bandwidth efficien-
cy. Obviously, there is a trade-off between power and band- width efficiency. Therefore, achieving power and bandwidth efficiency simultaneously is a challenging task [1], as well as, in future Broadband Wireless Access systems; the main chal- lenge is to transmit an error sensitive application data with a higher bit rate efficiently over error prone wireless channels.
Error performance of communication channels is usually
poor without error control due to channel imperfections and the inherent additive noise. Using error control coding will cause bandwidth expansion, which is not desirable, where; the limitation and higher cost of spectrum occupation are among the most important challenges in wireless communication sys- tems. In order to overcome this drawback, such coding and modulation should be integrated to match the channel situa- tion, Coded Modulation (CM) schemes are used to achieve both power and bandwidth efficient communication by map- ping information sequences onto an expanded set of channel signals with the help of error correcting codes [1-3].
In such Equal Error Protection (EEP) systems, a fixed code is constructed for the worst case of average channel/source con- ditions, this result in the waste of resource for the protection of the least sensitive bits, since they are assigned the same pro- tection level as the most sensitive bits.
A classic technique that used for maximizing error control performance while limiting the required redundancy is to ap- ply Unequal Error Protection (UEP) [4]. Codes that are de-
————————————————
signed to provide different levels of data protection are known as UEP codes, the term UEP implies that the resources availa- ble to provide protection to the various bit streams are not equally distributed, but instead, each bit stream may be pro- tected so that it withstands a different level of channel noise.
Simply, different levels of protection are provided for differ-
ent parts of the data according to their degrees of importance,
UEP receiver matches the protection level according to the
system requirement, and thus can save the system resources.
For example, in packet communications, the header must be
protected more than the payload, because in the worst case, if the destination address is lost, the entire packet will be lost. A multilevel encoder in [5] is considered an UEP system, the information sequence is divided into parallel sequences in decreasing order of importance, and the encoding process consists of the different rate encoders to create the desired UEP characteristics. Specific examples include practically all digital speech and image transmission systems.
Superposition Coded Modulation (SCM) implies transmis- sion of different symbol streams on the same modulation in-
terval, it is a powerful modulation technique that is being con- sidered in many emerging broadband communication sys- tems. SCM has been studied as an alternative scheme for high throughput transmission [6-7]; it has several advantages over conventional CM schemes. One interesting feature of SCM is that, the transmitted signal exhibits an approximately Gaussi- an distribution since it is a linear superposition of several in- dependent code words (each referred to as a layer). Superposi- tion coding is conceptually simpler and has lower encoding complexity. Another feature of superposition coding is that it can be treated as a perfectly cooperating multiple access sys- tem by viewing one layer as one user. Hence, the low cost CBC iterative decoding techniques developed in [8] can be em- ployed.
The most common types of power amplifiers used in com- munication systems are Travelling Wave Tubes Amplifiers
(TWTA) and Solid State Power Amplifiers (SSPA). Obviously
HPAs are a part of almost all communication links and due to
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 192
ISSN 2229-5518
the non-linear nature of the electronic components that they are made of, their conversion characteristics are non-linear.
In general, two major classes defining the time behavior of
BPSK signaling is considered over a time invariant single
path channel. A multi user 𝑢, {𝑢 = 1,2, … . , 𝑈}, each user data input, 𝑑𝑢 ∈ {+1, −1}, is un-equally partioned based on data
𝑢 𝑢 𝑢
HPA; HPA models with memory and memory-less HPA
models. The word memory-less implies not only an instanta-
neous relationship between input and output, but also implies
that the device does not exhibit frequency selective behavior over the bandwidth of operation. In addition to amplify the signal, the non-linear amplifier generates non-linear distortion
priority into 𝑘 sub-sequences {𝑑𝑘 = 𝑑1 , … , 𝑑𝑘 , 𝑘 = 1,2, … . , 𝐾},
the 𝑘𝑡ℎ sub-sequence is encoded using different rate convolu-
tional encoders (used as component codes) at the 𝑘𝑡ℎ level [13].
Convolutional encoders transform a whole sequence of in-
formation bits into a sequence of encoded bits by convolving
the information bits with a set of generator coefficients, result-
𝑢 𝑢 𝑢
in both amplitude and phase which causes the loss of system
reliability resulting in a higher BER [9,10].
In this paper, a multi user (multi stream) MS-SMRCM sys- tem is introduced, the coding scheme is designed in such a
ing in coded sub-sequences [15], {𝐶1 , … , 𝐶𝑘 }, 𝐶𝑘 , are spread using a length 𝑆 spreading sequences 𝑆𝑘 ∈ {+1, −1}, the same
composite spreading sequence is applied to all layers. The en-
coded chip sequence obtaining after spreading is written as,
𝑢,𝑘
way that, for each user, the most important information bits
result in a better error rate than other information bits using
{𝑆𝑗
, 𝑗 = 1,2, … . , 𝐽}, where, 𝐽 = 𝑁 × 𝑆 is the chip length.
In contrast to Code Division Multiple Access (CDMA),
different rate convolutional encoders. All of the layers employ
a common spreading sequence, the interleaving index se- quences is considered as a code to distinguish layers. Binary Phase Shift Keying (BPSK) signaling is considered over a time- invariant single path channel with equal power allocation in the presence of non-linear HPA Rapp model [10], considering both AWGN and Rayleigh fading channels. CBC iterative MUD strategy is applied.
This paper is organized as follows, a transmitter structure
specific spreading codes are used for layers separation. Inter- leaving is essential for system performance, as it reduces the mutual dependence among superimposed chips. A specific distinct chip layered random interleavers are employed as
layer specific interleavers for layer separation, �𝜋𝑗 , 𝑘 =
1,2, … . , 𝐾 �, to produce interleaved chip layered data sequenc-
es, {𝐼𝑢,𝑘 , 𝑘 = 1,2, … , 𝐾}, the interleaved chips layered data se-
quences are mapped onto the modulated symbols,
𝑢,1, … , 𝑥𝑢,𝑘 �, which are elements of a BPSK constellation.
for the proposed MS-SMRCM in the presence of non-linear
HPA is presented in section 2, section 3, introduces a CBC it-
�𝑥𝑗
𝑗
Afterward, the modulated symbols are weighted, this
erative MUD, the proposed MS-SMRCM system performance evaluation is investigated in section 4, the conclusions are pre- sented in Section 5.
weighting corresponds to power and phase allocation and is
crucial for the performance of SM, to simplify discussion, the
weighting factor {𝛽𝑢,𝑘 } is assumed to be real constant
weighting factor, i.e., the magnitudes of chips are all identical
and set to 1, the weighted symbols are superimposed together
to produce the SMRCM signal sequence 𝑥� 𝑢 .
𝑢 = ∑𝑈,𝐾
𝛽𝑢,𝑘
𝑢,𝑘 (1)
SCM has been investigated by many authors [1-3], [11,12].
SCM consists of transmitting both bit streams in all available
𝑥�𝑗
𝑥�𝑗
𝑢=1,𝑘=1 𝑥𝑗
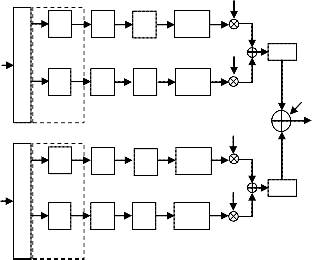
modulation intervals using superposition of channel codes in the modulation space. The transmitter of the proposed system is depicted in Fig. 1.
𝜷𝒖,𝟏
𝑢, is fed to the HPA, non-linearly amplified, as given in
[9], Rapp model is used for modeling memory-less SSPA be-
havior models for the proposed SMRCM system, the output of
HPA, 𝑥𝑗 , is given by:
𝑥� 𝑢 (𝑡) = 𝐴(𝑡) 𝑐𝑐𝑐 (𝜔 𝑡 + 𝜑(𝑡)) (2)
𝒅𝒖 𝒖
𝟏 C1 𝟏
𝒖,𝟏
𝒖,𝟏
𝒖,𝟏 𝒋
𝒋
𝒖,𝟏
𝒋
𝜷𝒖,𝒌
𝑥𝑢 (𝑡) = 𝐹[𝐴(𝑡)] 𝑐𝑐𝑐 [𝜔 𝑡 + 𝜑(𝑡) 𝛹(𝐴(𝑡))] (3)
Where, 𝐹[𝐴(𝑡)],𝛹[𝐴(𝑡)] are the gain distortion function
that represents the Amplitude to Amplitude transfer charac-
𝒖 𝒅𝒖 .
𝑪𝒖 𝑺𝒖,𝒌
𝒖,𝒌
𝒙𝒖,𝒌
�𝒙𝒖
teristics (𝐴𝐴/𝐴𝐴), and the phase distortion function that rep-
𝒌 𝒌
𝒋 𝒖,𝒌 𝑰𝒋
𝒋
𝒋
𝒋
𝒋
resents Amplitude to Phase transfer characteristics (𝐴𝐴/𝑃𝐴),
given by:
𝒓𝒋
𝑢 𝑢
𝑥� 𝑢
𝑼 𝑼𝒖
𝑼,𝟏
𝑼,𝟏
𝑼,𝟏 𝒙𝑼,𝒌
⎧ 𝐴𝐴⁄𝐴𝐴 : 𝐹�𝑥�𝑗 � = 𝑥𝑗 =
𝑢 2𝑝
![]()
1⁄2𝑝
𝑪𝟏
𝑺𝒋
𝑼,𝟏 𝑰𝒋
𝒋
𝒙𝒋
𝒋
𝒙�𝑼 ⎨
��1 + 𝑥�𝑗 ⁄𝑣𝑠𝑎𝑡 � �
(4)
𝐴𝐴⁄𝑃𝐴 ∶ 𝛹(𝐴(𝑡)) = 0
𝑼 .
𝑢 𝑢
𝒅𝒌
𝑪𝑼 𝑺𝑼,𝒌
𝑰𝑼,𝒌
𝒙𝑼,𝒌
𝑥�𝑗 , 𝑥𝑗
are the input and output signals voltage, 𝑣𝑠𝑎𝑡 is the am-
𝒌
𝒋 𝑼,𝒌 𝒋
𝒋
plifier input saturation voltage, 𝑒, is called "knee factor", that con-
trols the smoothness of the transition from the linear region to the
saturation region (Limiting Region) of characteristic curve. As the
value of 𝑒, increases, the SSPA model approaches the limiter
Fig. 1. Transmitter structures of the proposed MS-MRCM
model [9, 10].
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 193
ISSN 2229-5518
Generally, the spread information signal looks like random interference to all the other users, increasing the number of
𝑈,𝐾
𝑉𝑉𝑟�𝑟𝑗 � = � |𝛽
𝑢=1,𝑘=1
𝑢,𝑘
| 𝑉𝑉𝑟�𝑥𝑢,𝑘 � + 𝜎2 (7𝑏)
u,k in “(6),” can be ap-
users increases the amount of interference, resulting in a de-
graded system performance, which can be partially sup-
Using the central limit theorem, ξj
proximated by a Gaussian random variable with:
𝑢,𝑘 � = 𝐸�𝑟𝑗 � − 𝛽𝑢,𝑘 𝐸�𝑥𝑢,𝑘 � (8𝑉)
pressed at the receiver while decoding each user signal [14].
𝐸�𝜉𝑗
𝑢,𝑘
𝑗
𝑢,𝑘
The decoding/detection principle discussed below is de-
𝑉𝑉𝑟�𝜉𝑗
� = 𝑉𝑉𝑟�𝑟𝑗 � − |𝛽𝑢,𝑘 |2𝑉𝑉𝑟�𝑥𝑗
� (8𝑏)
rived based on the similarity between the superposition cod-
ing scheme and the Interleave Division Multiple Access
scheme (IDMA) [15]. An iterative CBC-MUD algorithm is ex-
The ESE outputs are the Logarithm Likelihood Ratio
(LLRs) about {𝑥𝑗 } computed based on “(7-8),” as:
𝑃𝑟�𝑥𝑗 � = +1|𝑟𝑗
ploited to suppress the channel fading and multiple access
𝐿�𝑥𝑢,𝑘![]()
� = 𝑙𝑐𝑙 �
𝑢,𝑘 � = −1|𝑟 �
interference.
The receiver is assumed to have perfect knowledge of the
𝑃𝑟�𝑥𝑗
𝑗
(𝑟𝑗 − 𝐸(𝜉𝑢,𝑘![]()
𝑗
channel state information. The received signal is processed
iteratively, since there are large numbers of interference terms,![]()
⎛𝑒𝑥𝑒 �−
= 𝑙𝑐𝑙 ⎜
2𝑉𝑉𝑟(𝜉𝑘 ) �⎞
(𝑟 − 𝐸�𝜉𝑢,𝑘 � + 𝛽𝑢,𝑘 )2 ⎟
the Gaussian approximation is still valid even after last itera- tion.![]()
𝑒𝑥𝑒 �− 𝑗
⎝![]()
𝑢,𝑘
𝑗
2𝑉𝑉𝑟(𝜉𝑢,𝑘 )
𝑗 ⎠
The received signal at time instant 𝑗 can be written as:
𝑈
2𝛽𝑢,𝑘 �𝑟𝑗 − 𝐸(𝜉𝑗 )�
= 𝑢,𝑘
(9)
𝑢 𝑉𝑉𝑟�𝜉𝑗 �
𝑟𝑗 = � 𝑥𝑗
𝑢=1
+ 𝑛𝑗 , 𝑗 = 1,2, … , 𝐽 (5)
For the layer 𝑘, the corresponding ESE outputs 𝐿�𝑥𝑢,𝑘 , 𝑗 =
𝑢,𝑘
Where, 𝑥𝑗 denoted the transmitted data symbols for the
user at time instant 𝑗, and 𝑛𝑗 zero mean AWGN with
1,2, … . . . , 𝐽�, are de-interleaved to form 𝐿�𝐶𝑗
and delivered to the DSE for layer 𝑘.
, 𝑗 = 1,2, … . . , 𝐽�,
𝑢
ance 𝜎2 = 𝑁0 /2.
For simplicity, we focus on the chip related to 𝑑1 , the first
𝑢,𝑘
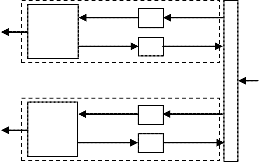
The CBC iterative receiver, in Fig. 2, consists of an Elemen-
bit of layer k. It is assumed that, 𝐿�𝐶𝑗
� are uncorrelated due
tary Signal Estimator (ESE) and a bank of single user A Poste-
to interleaving [15]. Let the interleaving for layer k be ex-
riori Probability (APP) detectors for the De-Spreading opera-
pressed as 𝜋𝑗
𝑗 𝑗ˋ
tion (DES) working in turbo type manner [16].
𝑢,𝑘 = 𝑗ˋ , i.e., 𝐶 𝑢,𝑘 = 𝑥𝑢,𝑘 . Then based on “(9),” the
APP detector outputs log-APP ratios, LLR for 𝑑𝑢 can be com-
{𝑳(𝑪𝒖,𝒌)}
𝟏
𝒖,𝟏
{𝑳(𝒙𝒖,𝒌)}
puted using 𝐿�𝐶𝑢,𝑘
� as:![]()
𝑢
𝒖�
{𝑬
(𝑪𝒖,𝒌)}
𝒖,𝒌)}
𝑢 𝑃𝑟(𝑑𝑘 ) = +1|𝑟
𝒆𝒙𝒕 𝒋
{𝑬𝒆𝒙𝒕 (𝒙𝒋
𝒖,𝟏
![]()
𝐿(𝑑𝑘 ) = 𝑙𝑐𝑙 �𝑃𝑟(𝑑𝑢 ) = −1|𝑟�
𝑢,𝑘
𝑢,𝑘
. . ∏𝑗=1 𝑃𝑟�𝐶𝑗
= 𝑆𝑗
|𝑟𝑗ˋ �
𝒓𝒋
= 𝑙𝑐𝑙 � 𝑆
𝑢,𝑘
𝑢,𝑘 �
. {𝑳(𝑪𝑼,𝒌)}
𝑼,𝒌)}
![]()
∏𝑗=1 𝑃𝑟�𝐶𝑗
𝑆 𝑢,𝑘
= −𝑆𝑗
𝑢,𝑘
|𝑟𝑗ˋ �
𝒋 𝟏
𝑼,𝟏
{𝑳(𝒙𝒋
= � 𝑙𝑐𝑙
𝑃𝑟�𝐶𝑗
𝑢,𝑘
= 𝑆𝑗
|𝑟𝑗ˋ �
𝑢,𝑘
(10)
𝑼� .
{𝑬
𝒆𝒙𝒕
(𝑪𝑼,𝒌)}
𝑼,𝒌
−𝟏 𝒆𝒙𝒕 𝒋
𝑼,𝟏
𝑗=1
𝑆
𝑃𝑟�𝐶𝑗
= −𝑆𝑗
|𝑟𝑗ˋ �
Fig. 2. Receiver structures of the iterative decoding/detection for the pro-
= � 𝑆𝑢,𝑘
𝑗
𝐿�𝐶 𝑢,𝑘
� (11)
posed MS-SMRCM
The received signal at time instant 𝑗 can be re-written as:
𝐾 ,𝑈
Convolutional decoders can easily process soft-decision
input (i.e., information on the reliability of the demodulator output) and compute soft-decision output (i.e., information on the reliability of the estimated information bits). A soft value implies a real number such as a probability is used, instead of
𝑟𝑗 = 𝐹 �� 𝛽𝑢,𝑘 𝑥𝑘 ,𝑢
𝑘 =1
𝑢=1
� + 𝜉𝑘,𝑢
(6)
a binary value which is defined by a hard value [14].
The use of soft-in/soft-out decoding stages [17]:
Where, 𝜉𝑗
= 𝑟𝑗 − 𝛽𝑢,𝑘 𝑥𝑗
, represents a distortion term
1. The use of soft a-prior information.
with respect to xu,k
𝑢,𝑘
, xu,k
is treated as a random variable with
𝑢,𝑘
2. Interleaving between chips to remove correlation be-
tween them.
mean 𝐸�𝑥𝑗
� and variance 𝑉𝑉𝑟(𝑥𝑗
𝑢,𝑘
). The initial values for
𝑢,𝑘
3. Iterations to improve previous data estimates.
𝑢,𝑘 �� form the output of the DES
both mean 𝐸�𝑥𝑗
� and variance 𝑉𝑉𝑟�𝑥𝑗
� are "0" and "1" re-
The Extrinsic LLRs �𝐸𝑥𝑡�𝐶𝑗
spectively. Then form “(6),” we can write:
𝑈,𝐾
and are fed back to the ESE after interleaving. In the next itera-
𝑢,𝑘
𝐸�𝑟𝑗 � = � 𝛽𝑢,𝑘 𝐸�𝑥𝑢,𝑘
� (7𝑉)
tion, {𝐸𝑥𝑡�𝑥𝑗
𝑢,𝑘
�} are used to update
𝑢,𝑘
𝑢=1,𝑘=1
�𝐸�𝑥𝑗
�� and �𝑉𝑉𝑟�𝑥𝑗
�� as [12].
IJSER © 2013
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 194
ISSN 2229-5518
𝑢,𝑘
𝑒𝑥𝑒�𝐸𝑥𝑡(𝑥𝑢,𝑘
)) − 1)�
each one is 192 bit length and no convolutional encoders are
𝐸�𝑥𝑗![]()
� = � �
𝑒𝑥𝑒�𝐸𝑥𝑡(𝑥𝑢,𝑘 )) + 1)�
𝑢,𝑘
used, it can be written in the form MS-USM (192 − 192). The
second case is MS-UEP-SCM, where each user data length is![]()
𝐸𝑥𝑡(𝑥𝑗 )
𝑢,𝑘
= 𝑡𝑉𝑛ℎ �
2 � (12)
𝑢,𝑘 2
un-equally partioned into two layers, the high priority data
stream is 128 bit length, convolutionally coded with rate,
(𝑅 = 1⁄2), while the low priority data stream is 256 bit length
𝑉𝑉𝑟�𝑥𝑗
� = 1 − 𝐸�𝑥𝑗 �
(13)
This iterative process is repeated a preset number of times.
The iterative process continues in this manner until further
iterations yield little or no significant improvement. In the
final iteration the DES produces hard decisions on information
bits to re-construct the each user data transmitted.
In this section, the simulated results demonstrate the per- formance of the proposed MS-SMRCM system. Each user data
length is assumed to be (𝑁 = 384) bit length partioned into two bit streams or two layers (𝐿 = 2), based on data priority,
the encoding process is applied. The same spreading code is
used for all layers, it contains (𝑆 = 16 𝑐𝑟 32) balanced se-
quences. The number of iterations in the CBC iterative receiver
was set to (𝐼𝑡𝑒𝑟 = 3).
For the HPA linearity, an ideal amplifier would be a totally
linear response device, but real amplifiers are only linear re-
sponse within certain practical limits, so, the HPA non-
linearity behavior can be investigated at different smoothness factors. Fig. 3 shows the relationship between input voltage and output voltage linear response and non-linear response at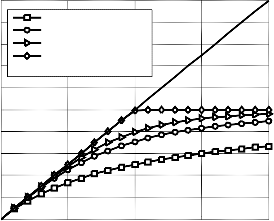
different HPA smoothness factors (𝑒 = 1,2,3,100).
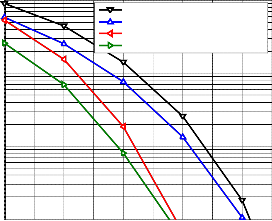
and has no coding, it can be written in the form MS-UEP-
SCM(128, 1⁄2 − 256).
The third case is MS-EEP-SCM, where each user data
length is equally partioned into two bit streams, each one has
the same priority, using equal error rates convolutional en-
coders, it can be written in the form, MS-EEP-SCM(192,1/2 −
192,1/2). Finally, the fourth case, Multi Rate input and Multi
Rate Coding, where each user data input is un-equally par-
tioned into two layers, high priority data stream is 128 bit length, convolutionally encoded with rate, (𝑅 = 1⁄3), while the low priority is 256 bit length, encoded with rate, (𝑅 =
2⁄3), the resultant symbols can be written in the form MS-
SMRCM(128, 1⁄3 − 256, 2⁄3), the difference between MS-
USM and MS-UEP-SCM is 0.2 dB, while the difference be-
tween MS-SMRCM and MS-EEP-SCM is 0.2 dB.
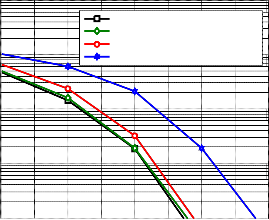
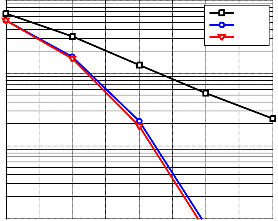
Fig. 6. shows the effect of iteration number in detection
process, for iteration=1, at Eb⁄N0 = 8 dB, BER performance of four users is degraded to 2.4 × 10−3 , while, for iteration=2,3 the performance is improved to be 5.8dB and 5.9dB respective-
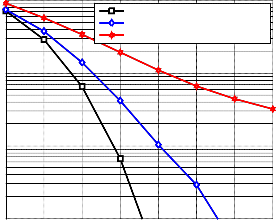
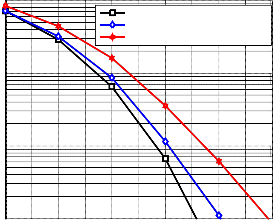
ly. Fig. 7 shows the Rayleigh fading channel effect on MS-
SMRCM performance at velocity 90 𝑘𝑘/ℎ𝑟, the difference be-
tween a single user and two users performance is 0.9 dB and
while the difference between a single user and four users is 2.8
dB at Eb⁄N0 = 14 dB. The simulation results for AWGN chan-
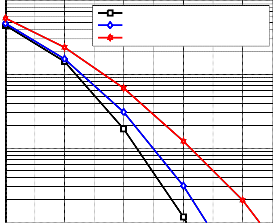
nel in the presence of non linear HPA are shown in Fig. 8,
Nonlinear Rapp p = 1
Nonlinear Rapp p = 2
Nonlinear Rapp p = 3
Nonlinear Rapp p = 100
where the difference between a single user and two users per- formance is 0.7 dB, while the difference between a single user
and four users is 2.6 dB at Eb⁄N0 = 14 dB. In Fig. 9, the effect
of HPA non-linearity behavior over the Rayleigh fading chan-
nel is clear, the single user performance is better than two us-
ers by 4 dB, while at Eb⁄N0 = 14 dB, the BER performance of four users is degraded to 3.2 × 10−4 .
0
10
-1
10
SMRCM [ U1 (128,1/3 - 256,2/3) ]
MS-SMRCM [ U2 (128,1/3 - 256,2/3) ] MS-SMRCM [ U4 (128,1/3 - 256,2/3) ] MS-SMRCM [ U8 (128,1/3 - 256,2/3)]
Fig. 3. Relationship between Input voltage and output voltage linear re-
sponse and non-linear response at (𝑒 = 1,2,3,100).
Fig. 4 shows the MS-SMRCM performance for 1,2,4,8 users
using spreading length 16, where the single user performance
is better than two, four and eight users by 0.1 dB, 0.2 dB and
2.3 dB respectively at BER= 10−4 due to the effect of multi user
input with different code rates.
Fig. 5 shows the four users performance evaluation in four
cases over AWGN channel, the first case is MS-USM, where,
each user data length is equally partioned into two bit streams,
IJSER © 2013
-2
10
-3
10
-4
10
0 1 2 3 4 5 6 7 8
Eb/No(dB)
Fig. 4. BER performance of MS-SMRCM using two different rates
(𝑈 = 1,2,4, 𝑁 = 384, 𝐿 = 2, 𝑆 = 16, 𝐼𝑡𝑒𝑟 = 3)
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 195
ISSN 2229-5518
-1 -1
10 10
MS-USM [ U4 (192 - 192 ) ]
MS-UEP-SCM [ U4 (128,1/2 - 256 ) ] MS-SMRCM [ U4 (128,1/3 - 256,2/3 ) ]
MS-EEP-SCM [ U4 (192,1/2 - 192,1/2 ) ]
SMRCM [ U1 (128,1/3 - 256,2/3) ]
MS-SMRCM [ U2 (128,1/3 - 256,2/3) ] MS-SMRCM [ U4 (128,1/3 - 256,2/3) ]
-2
10 10
-3
10 10
-4
10
0 1 2 3 4 5 6 7 8 9
Eb/No(dB)
-4
10
0 1 2 3 4 5 6 7 8 9
Eb/No(dB)
Fig. 5. BER performance of MS-SMRCM using two different rates
(𝑈 = 4, 𝑁 = 384, 𝐿 = 2, 𝑆 = 32, 𝐼𝑡𝑒𝑟 = 3)
Fig. 8. BER performance of MS-SMRCM using two different rates and
HPA Rapp model (𝑈 = 1,2,4, 𝑁 = 384, 𝐿 = 2, 𝑆 = 32, 𝑒 = 3, 𝐼𝑡𝑒𝑟 = 3)
-1 -1
10 10
Iter =1
Iter =2
Iter =3
SMRCM [ U1 (128,1/3 - 256,2/3) ]
MS-SMRCM [ U2 (128,1/3 - 256,2/3) ] MS-SMRCM [ U4 (128,1/3 - 256,2/3) ]
-2 -2
10 10
-3 -3
10 10
-4
10
0 1 2 3 4 5 6 7 8
Eb/No(dB)
-4
10
0 2 4 6 8 10 12 14
Eb/No(dB)
Fig. 6. BER performance of MS-SMRCM using two different rates
(𝑈 = 4, 𝑁 = 384, 𝐿 = 2, 𝑆 = 32, 𝐼𝑡𝑒𝑟 = 1,2,3)
-1
10
SMRCM [ U1 (128,/3 - 256,2/3) ]
MS-SMRCM [ U2 (128,1/3 - 256,2/3) ] MS-SMRCM [ U4 (128,1/3 - 256,2/3) ]
-2
10
-3
10
-4
10
0 1 2 3 4 5 6 7 8 9 10
Eb/No(dB)
Fig. 7. BER performance of MS-SMRCM using two different rates
(𝑈 = 1,2,4, 𝑁 = 384, 𝐿 = 2, 𝑆 = 32, 𝑆𝑒𝑒𝑒𝑑 = 90 𝑘𝑘/ℎ𝑟, 𝐼𝑡𝑒𝑟 = 3)
Fig. 9. BER performance of MS-SMRCM using two different rates and
HPA Rapp model
(𝑈 = 1,2,4, 𝑁 = 384, 𝐿 = 2, 𝑆 = 32, 𝑒 = 3, 𝑆𝑒𝑒𝑒𝑑 = 90 𝑘𝑘/ℎ𝑟, 𝐼𝑡𝑒𝑟 = 3)
In this paper, a novel MS-SMRCM communication system has been investigated. In the proposed MS-SMRCM, the user data stream is un-equally partioned based on data priority. Simulation results for the proposed MS-SMRCM are com- pared with the three systems USM, UEP-SCM and EEP-SCM over AWGN channel. Also, the performances of all users have been studied in the presence of HPA Rapp model and Ray- leigh fading channels.
Four users comparison in AWGN channel, the perfor- mance of the proposed MS-SMRCM is better than MS-USM by
about 2.4 dB. Also, the proposed MS-SMRCM is better than
MS-UEP-SCM by 0.2 dB. The performance of the proposed
MS-SMRCM is degraded by about 0.2 dB compared with MS-
EEP-SCM, All comparisons have been studied at BER = 10−4.
In HPA, the difference between single user and two and four
users is 0.8 dB and 2.6 dB at BER = 10−4 respectively. The
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 196
ISSN 2229-5518
Rayleigh fading channel effect at velocity 90 𝑘𝑘/ℎ𝑟 in the
presence of HPA, the difference between single user and two
users is 4 dB while, the four users performance is 3.2 × 10−4
at 𝐸𝑏 ⁄𝑁0 = 14 dB.
[1] Hoeher and Peter Adam “Superposition Coded Modulation Myths and
Facts,” Communications Magazine, IEEE, Vol. 49, pp. 110-116, Dec. 2011.
[2] Karabulut and Güneş Z. “Rate Design Rule for Superposition Coded Modula- tions,” Canadian Conference on Electrical and Computer Engineering, Vol. 1, pp. 365-368, May 2004.
[3] Wang and Xin “Design of Superposition Coded Modulation for Unequal Error Protection,” IEEE International Conference on Communications, Vol. 2, pp. 412-416, Jun 2001.
[4] Atungsiri, S. A. , Tateesh, S. T. , Kondoz and Ahmet M. “Multirate Coding for
Mobile Communication Link Adaptation,” IEE Proceedings Communica- tions, Vol. 144(3), pp. 211-216, 1997.
[5] Imai H, Hirakawa S. “A New Multilevel Coding Method using Error Correct-
ing Codes,” IEEE Transactions on Information Theory, Vol. 23(3), pp. 371-377,
1977.
[6] Yang G, Shen D, Victor OK “UEP for Video Transmission in Space-Time
Coded OFDM System,” IEEE INFOCOM, Vol. 2, pp.1200-1210, 2004.
[7] Tong, Jun , Ping, Li , Ma and Xiao, “Superposition Coding with Peak-Power
Limitation,” IEEE International Conference on Communications, 2006. ICC
'06. Vol. 4, pp. 1718-1723, June 2006.
[8] Tianbin Wo, Meelis Noemm, Dapeng Haoand Peter Adam Hoeher “Iterative Processing for Superposition Mapping,” Journal of Electrical and Computer Engineering, Vol. (2010), 13 pages, 2010.
[9] Pavol Pavelka, Jozef Krajňák, Pavol Galajda and Dušan Kocur “Analysis of
Non Linear Distortions in MC-CDMA Systems,” Acta ElectrotechnicaetIn-
formatica Vol. 7(4), 2007.
[10] Amanjot Singh and Hardeep Kaur, “Non linearity analysis of high power
amplifier in OFDM system,” nternational Journal of Computer Applications, Vol. 37(2), Jan. 2012.
[11] G. Karabulut and A. Yongacoglu, “Superposition Block Coded Modulation,” Canadian Conference on Electrical and Computer Engineering,Vol. 3, pp.1629-1632, May 2003.
[12] X. Ma and L. Ping, “Coded Modulation using Superimposed Binary Codes,” IEEE Tran. Inform. Theory, Vol. 50 (12), pp. 3331-3343, Dec. 2004.
[13] Ahmed E. Zein Eldin , Esam A.A. Hagras , Hala Mansour Abdel-Kader, ‘’ A Novel Superposition Multi Rate Coded Modulation (SMRCM),’’ International Journal of Computer Networks and Wireless Communications (IJCNWC), Vol. (3), no. 2, pp. 190-196, April 2013.
[14] Rolf Johannesson, Kamil Sh. Zigangirov ‘’ Fundamental of Convolutional
Codes,’’ Wiley, John & Sons, Incorporated, March, 1999.
[15] Li Ping, “Interleave Division Multiple Access and Chip By Chip Iterative
Multi User Detection,” IEEE Communication Magazine, Vol. 43(6), pp. S19- S23, June 2005.
[16] L. H. Liu, J. Tong, and Li Ping, “Analysis and Optimization of CDMA Sys- tems with Chip-Level Interleavers,” IEEE J. Select. Areas Comm. Vol. 24(1), pp. 14.
[17] Mark C. Reed, ‘’Iterative Receiver Techniques for Coded Multiple Access Communi- cation Systems,’’, PhD dissertation, Dept. of Division of Information Technology, En- gineering and the Environment, School of Physics and Electronic Systems Engineer-
ing., University of South Australia 1999, available at,
http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1 .35.2415 (2013)
IJSER © 2013 http://www.ijser.org