Euclidian distance between two feature vectors is computed as
𝐸(𝑝, 𝑞) = � 1 ∑𝑀
(𝑝 − 𝑞 )2
(5)
The 2-D wavelet decomposition of 𝐽 levels on each non- overlapping block represents the block in terms of 3𝐽 + 1
wavelet sub-band images.
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 908
ISSN 2229-5518
2-class, N-class Approach for Complete
Multimodal Biometric Identification
Abhijit Shete, Kavita Tewari
Abstract— Multibiometric systems are expected to be more reliable than unimodal biometric systems for personal identification due to the presence of multiple, fairly independent pieces of evidence e.g. Unique Identification Project “Aadhaar” of Government of India. In this paper, we present a two step multibiometric identification system. In the first step the person is classified as an imposter or genuine, and in second step exact reorganization of a person is done. Here we have proposed PCA and Wavelet based technique to perform fusion at score level by considering two biometric modalities face and fingerprint, which handles 2-class problem and k-NN classifier to identify an individual that handles N-class problem. The results indicate that the proposed technique can lead to substantial improvement in multimodal matching performance. In this paper, score level fusion is done using two different strategies based on performance parameters, EER (Equal Error Rate) and DI (Decidability Index).
Index Terms— Wavelet, PCA, Multimodal Fusion, Decidibility Index, EER, ROC, GAR, k-NN.
—————————— ——————————
number of biometric characteristics are being used in various applications. Each biometric has its pros and cons and, therefore, the choice of a biometric trait for a
particular application depends on a variety of issues besides its matching performance. A reliable identity management system is a critical component in several applications that render services to only legitimately enrolled users. A biometric system is essentially a pattern recognition system that acquires biometric data from an individual, extracts a salient feature set from the data, compares this feature set against the feature set(s) stored in the database, and executes an action based on the result of the comparison. Identification occurs when a biometric system attempts to determine the identity of an individual.
The most popular approaches to face recognition are based on either (i) the location and shape of facial attributes, such as the eyes, eyebrows, nose, lips, and chin and their spatial relationships, or (ii) the overall (global) analysis of the face image that represents a face as a weighted combination of a number of canonical faces [1].
The most popular ones are based on the minutiae pattern of the fingerprint and are collectively called minutiae-based approaches. The main disadvantage of image-based approaches consists in their limited ability to track with variations in position, scale and orientation angle. Usually the variation in position between the two fingerprints is cancelled by choosing a reference point in each fingerprint. [2]
————————————————
• K. Tewari is currently working as Associate Professor and Head of
Electronics Department at VES Institute Of Technology, Mumbai, India.
E-mail: ktewari_vesit@yahoo.co.in
In this paper we conclude that, if two biometrics are comparable, then performance of the automated Biometric Identification Subsystem involving two step classification improves by score level fusion techniques [3].
The paper is organized as follows. This introduction serves as the first section. The following section introduces biometric traits used and their feature extraction method. Section 3 summarizes two step classification in detail. Section 4 explains similarity measure used and score level normalization. Fusion techniques used are formulated in section 5. Weights necessary to handle 2-class problem, are calculated in section 6. Also experimental results including k-NN classification experiments are shown in the same section, and finally a brief conclusions section will summarized the paper.
Face recognition is a non-intrusive method, and facial attributes are probably the most common biometric features used by humans to recognize one another. The appearance-based approach, such as PCA based approach generally operates directly on an image-based representation (i.e., array of pixel intensities). It extracts features in a subspace derived from given images. Using PCA, a face subspace is constructed to represent “optimally” only the face object.
Fingerprint reorganization using minutiae-based approaches are different from one other, most of these methods require extensive preprocessing operations (e.g. orientation flow estimation, ridge segmentation, ridge thinning, minutiae detection) in order to reliably extract the minutia features [4]. They either match directly the fingerprint images [5], or match features extracted from the image by means of certain filtering or transform
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 909
ISSN 2229-5518
operations [6], hence their name image-based methods. In this paper we use an image-based method of fingerprint recognition. The fingerprint patterns are matched based on wavelet domain features which are directly extracted from the gray-scale fingerprint image without preprocessing.
In this paper we use PCA for feature extraction and as a dimensionality reduction technique, which transforms the
feature vector 𝜑𝑖 to a vector 𝐹𝑖 which has a dimensionality𝑑, where 𝑑 < 𝑀 × 𝑁 i.e. pixel resolution of an image of person 𝐴.
Let 𝐴𝑖 , 𝑖 = 1,2, … … 𝑝 be an image from database containing 𝑝
images. For each image we form a pixel vector
𝜑𝑖 𝜖 ℜ𝑘 , (𝑘 = 𝑀 × 𝑁) and compute feature vector 𝐹𝑖 where
𝐹𝑖 𝜖 ℜ𝑑 , 𝑑 ≪ 𝑘. In order to apply PCA we first form a data
matrix 𝐷 which contains p rows, at each row 𝜑𝑖 ′𝑠 are stored,
thus 𝐷 has dimensionality of 𝑝 × 𝑘. Next covariance matrix
of 𝐷 ∶ 𝐶𝐷 is computed. For this covariance matrix we get 𝑘
eigenvalue and eigenvector pairs, where each eigenvector 𝑒𝑖
is of dimensionality 𝑘.
The transformation matrix 𝜓 is formed by simply putting
eigenvector with biggest 𝑑 eigenvalues as column of 𝜓. The
feature vector 𝐹𝑖 is then obtained as follows
𝑇
A wavelet decomposition of each fingerprint image was performed using db10 wavelet in order to extract a feature vector of length 48.
Our method of two step classification is applied as follows,
1] Extract the feature vector (template) from acquired biometric sample e.g. face and finger of a person using method given in section 2.
2] Determine minimum distance for each sample, by measuring similarity of extracted template to all the templates in the respective database.
3] Determine fused score by using score normalization and
one of the fusion strategy.
4] Declare a person as genuine or imposter by selecting
threshold where False Match Rate (FMR) is 0.01%.
5] If genuine proceed for Step-2
(N=40=number of individuals per trait)
5] From second procedure in Step-1 identify class of a
person i.e. identity of a person.
6] If person identified by both traits is same, identification
𝐹𝑖 = 𝜓𝑇 𝜑𝑖
Where 𝜓𝑇and 𝜑𝑇
(1)
are the transposes of 𝜓 and 𝜑 respectively.
is over, else start from the beginning.
Feature vector length used for face trait is 20.
Feature extraction is done by cropping [90 × 90] square
region centered around the reference point and located
inside the fingerprint pattern. Reference point is detected by
the method proposed by Li Wang [7]. Central subimage is
divided into 4 non-overlapping blocks of size [45 × 45].
![]()
Euclidian distance between two feature vectors is computed as
𝐸(𝑝, 𝑞) = � 1 ∑𝑀
(𝑝 − 𝑞 )2
(5)
The 2-D wavelet decomposition of 𝐽 levels on each non- overlapping block represents the block in terms of 3𝐽 + 1
wavelet sub-band images.![]()
𝑀 𝑖 =1 𝑖 𝑖
Where M = Dimension of feature vector. E = 0 Indicates
match condition.
1 2 3
�𝐴 , �𝐷 , 𝐷 , 𝐷 �
𝑗=1,…..,𝐽
� (2)
Where 𝐴𝐽 is a lowpass approximation of the original block,
and 𝐷𝑟
are the highpass details at different scales 2𝑗
and
The intersection operator introduced by Swain and
orientations 𝑟. Wavelet coefficients of large amplitude in
Ballard in [8] is used as a measure of similarity between
1 2 3
𝐷𝑗 , 𝐷𝑗 and 𝐷𝑗
correspond, respectively, to vertical high
two feature vectors. If 𝑄 and T are the two feature vectors,
frequencies (horizontal edges), horizontal high frequencies
(vertical edges), and high frequencies in both directions.
then measure of similarity between them can be given as
∑3𝐽 𝑚𝑖𝑛(𝑄𝑖 ,𝑇𝑖 )
The normalised 𝑙2-norm of each wavelet sub-band is
𝐶(𝑄, 𝑇) =
![]()
𝑖=1
𝑚𝑖𝑛�∑3𝐽 𝑄𝑖 ,∑3𝐽 𝑇𝑖 �
(6)
computed in order to create a feature vector of length 3𝐽 per
𝑖=1
𝑖=1
block as given by Eq.(3)
� �𝑒𝑗 , 𝑒𝑗 , 𝑒𝑗 �
� (3)
𝐶 = 1 indicates match and 𝐶 = 0 indicates non-match
condition as shown in Figure 1(a) in this paper, we have
examined performance of two fusion techniques, Feature
1
Where
𝑟
2 3
𝑗=1,…..,𝐽
𝑟 𝐽 3 𝑙
Level Fusion and Match Score Level fusion with three different fusion strategies.
𝑒𝑗
= �𝐷𝑗 � �∑𝑖=1 ∑𝑙=1�𝐷𝑖 �
(4)
2 2
for all 𝑗 = 1 … … … 𝐽 and 𝑟 = 1, 2, 3
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 910
ISSN 2229-5518
The individual feature values of vectors exhibit significant differences in their range as well as form. Augmenting such diverse feature values will not be appropriate for fusion. Since all three similarity measures exhibits different range we have used “min-max” normalization technique to bring all scores in common range. Let x and x' denote a feature value before and after normalization, respectively. The min-max technique computes x' as [9]![]()
𝑥′ = 𝑥−𝑚𝑖𝑛(𝐹𝑥)
𝑚𝑎𝑥(𝐹𝑥 )−𝑚𝑖𝑛(𝐹𝑥)
We performed the experiments on Intel Core2 Duo machine using Matlab (R2010b). The performance of proposed approach is measured in terms of Receiver
Operating Characteristic (ROC) curve, which plots Genuine Accept Rate (GAR) against the False Match Rate (FMR) at different thresholds. The FMR, False Non-Match Rate (FNMR) and GAR are given by Eqs. (10)-(12), respectively.
𝐼𝑚𝑝𝑜𝑠𝑡𝑒𝑟 𝑐𝑙𝑎𝑖𝑚𝑠 𝑎𝑐𝑐𝑒𝑝𝑡𝑒𝑑
where Fx is the function which generates x, and min(Fx)![]()
𝐹𝑀𝐹 =![]()
× 100 (12)
𝑇𝑜𝑡𝑎𝑙 𝑖𝑚𝑝𝑜𝑠𝑡𝑒𝑟 𝑐𝑙𝑎𝑖𝑚𝑠
and max(Fx) represent the minimum and maximum of all
possible x values that will be observed, respectively.
𝐹𝑁𝑀𝐹 = 𝑇𝑟𝑢𝑒 𝑐𝑙𝑎𝑖𝑚𝑠 𝑟𝑒𝑗𝑒𝑐𝑡𝑒𝑑 × 100 (13)
𝑇𝑜𝑡𝑎𝑙 𝑡𝑟𝑢𝑒 𝑐𝑙𝑎𝑖𝑚𝑠
𝐺𝐴𝐹 = (1 − 𝐹𝑁𝑀𝐹) × 100 (14)
Let n = number of individuals and
m = number of images per individual, then number of
genuine scores can be obtained as nm(m − 1)⁄2
and
(Assignment of Weights based on EER)
This fusion strategy assigns the weight to each characteristic e.g face and finger, based on their equal error rate (EER). Weights for more accurate characteristic are higher than those of less accurate characteristic. Thus the weights are inversely proportional to the corresponding
errors. Let ek be the EER to characteristic k, then weight wk
associated to characteristic k can be computed by,
imposter scores can be obtained as n(n − 1)m2 using the same database. For the database used n = 40 and m = 8,
therefore we get 1120 genuine matching’s and 99840
imposter matching’s. In this paper we have used 1120 genuine and 6240 imposter pairs for each database. FMR
and FNMR are obtained for all thresholds (t) by Eq.(13)
Eq.(14), these equations are suitable for Color Indexing
distance measure. For Euclidian and Hamming distance
−1
w = �∑t � ∗
(8)
limits need to be changed.![]()
k=1 ek ek
𝐹𝑀𝐹 (𝑡) = 1 ∑1
𝐼𝐼𝑝𝐼𝑠𝑡𝑒𝑟(𝑠)
(15)![]()
𝑘 𝑇𝑘
𝑠=𝑡
1 𝑡
(Assignment of Weights based on Decidability Index)
𝐹𝑁𝑀𝐹𝑘 (𝑡) =
Where Tk
𝐺 ∑𝑠=0 𝐺𝑒𝐺𝐺𝑖𝐺𝑒(𝑠)
𝑇𝑘
k
(16)
In strategy B, weights are assigned to individual
characteristic based on their imposter and genuine scores
distributions. The means of these distribution are defined
I and T G are the total number of imposter and
genuine matches respectively. Equal Error Rate (EERk ) is
define as the rate at which FMRk(t) = FNMRk (t). In practice
the score distributions are not continuous and a crossover
I G I
by µk and µk respectively, and standard deviations by σk
and σG respectively. A parameter Decidability Index d is
used as measure of separation of these two distributions for![]()
characteristic k as
𝐺 𝐼 �
point might not exist. In this case, we report the interval as
per FVC2000: Fingerprint Verification Competition.
𝑑𝑘 =
√2 �𝜇𝑘 −𝜇𝑘
(9)
The FVC2000-Db1_a fingerprint database [10] contains a
𝐺 2
𝐼 2
![]()
��𝜎𝑘 � +�𝜎𝑘 �
If dk is small, overlap region of two distributions is less.
Therefore, weights are assigned to each characteristic
proportional to this parameter as,
total 800 fingerprint images of size 300x300 and 500 dpi
resolution from 100 individuals with 8 images per
individual, which were captured with low-cost optical sensor “Secure Desktop Scanner” by KeyTronic.
The ORL standard face database [11] consists of 400 face
𝑤𝑘 = ( ∑𝑡
𝑑𝑘 )−1 ∗ 𝑑𝑘
(10)
images attained from 40 individuals. Each individual have
For both fusion strategies B and C 0 ≤ wk ≤ 1, (∀k);
10 images of different expression or gesture. The resolution
t
k=1
wk = 1 and the fused score for user i is computed as,
of the image is 112×92 and the gray scale is 256.
𝐹𝑚 = ∑𝑡
𝑤𝑘 ∗ 𝑆𝑘𝑝 ; (∀𝑝)
(11)
In this paper, we have selected 40 individuals and 8 images per individual from each database resulting 320
In our case t = 3, k = 1, 2, 3 indicates face, finger, iris respectively. Skp indicates match score of pth pair of kth
characteristic.
images per trait.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 911
ISSN 2229-5518
The experimental results obtained are shown in
Table 1. The values of EER, 𝑑𝑘 and GAR are significantly
improved in both fusion strategies A and B, than individual
biometric Face and Finger. Among the fusion strategies the
EER and 𝑑𝑘 of strategy B are better than other strategy,
where as GAR of strategy A is higher than strategy B.
TABLE 1
PERFORMANCE ANALYSIS BEFORE AND AFTER FUSION
![]()
![]()
Performanc e Parameter | Face alone | Finger alone | Fusion -A 𝑾𝟓 = 𝟎. 𝟒𝟒𝟒𝟒 𝑾𝟓 = 𝟎. 𝟒𝟓𝟓𝟒 | Fusion -B 𝑾𝟓 = 𝟎. 𝟒𝟓𝟒𝟒 𝑾𝟓 = 𝟎. 𝟒𝟒𝟓𝟓 |
EER | 0.1107 | 0.1164 | 0.0604 | 0.0603 |
𝒅𝒌 | 21.09 | 15.19 | 34.88 | 34.94 |
GAR @ 0.01% FMR | 64.02 | 60.00 | 85.54 | 84.29 |
![]()
The example of performance graphs of fusion strategy B are shown in Figure 1. Similar graphs can also be obtained for other strategies.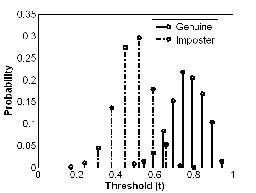
![]()
Figure 1(a) Genuine and Imposter Distribution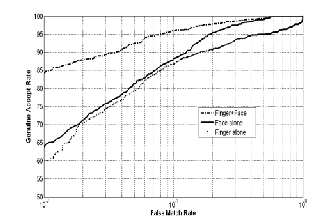
Figure 1(c) ROC curves.
The recognition performances achieved by using wavelet features for fingerprint and PCA features for face trait respectively have been evaluated using a k-NN classifier, with no rejection option a shown in TABLE 2. A number of k images from each individual (for a total of
40k images per trait) have been used as the training set, whereas the remaining 8 - k images from each individual (for a total of 40 x (8-k) images) have been used for testing.
TABLE 2
![]()
![]()
K-NN CLASSIFIER RESULTS
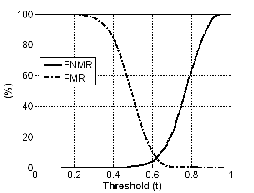
Figure 1(b) FNMR and FMR curves
This paper deals with score level biometric fusion
techniques. Among the fusion strategies the EER and dk of
strategy B are better than strategy A, where as GAR of
strategy A is higher than strategy B. The high recognition rates achieved by our method as well as its low computational complexity reveal that the method can be used to efficiently solve a security problem involving a
small number of fingerprint images. 2-class and N-class problems are effectively solved by using score level fusion and k-NN classifier.
[1] Lin Hong and Anil Jain, Fellow, IEEE, “Integrating Faces and
Fingerprints for Personal Identification”, IEEE TRANSACTIONS
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 912
ISSN 2229-5518
ON PATTERN ANALYSIS AND MACHINE INTELLIGENCE, VOL. 20, NO. 12, DEC. 1998.
[2] Marius Tico etal. “FINGERPRINT RECOGNITION USING WAVELET FEATURES” IEEE 0-7803-6685-9/01/$10.0002001
[3] Y.N. Singh, P. Gupta, “Quantitative Evaluation of Normalization Techniques of Matching Scores in Multimodal Biometric Systems”, S.-W.Lee and S.Z. Li (Eds.) : ICB2007, LNCS 4642, PP.
574-583, 2007 © Springer-Verlag Berlin Heidelberg 2007.
[4] JAIN. A.K., HONG, L., PANKANTI, S., and BOLLE, R: “An identity authentication system using fingerprints”, Proc. IEEE,
1997, 85, (9). pp. 1364-1388
[5] WILLSON. C L., WATSON, C.T., and PAEK, E.G.: “‘Effect of resolution and image quality on combined optical and neural network fingerprint matching”, Patt. Recognit., 2000, 33, (Z), pp.
317-331
[6] LIE, C.J., and WANG, S.D. “Fingerprint feature extraction using
Gabor filters”, Eleclron. Lett., 1999, 35, (4). pp. 288-290
[7] Li Wang and Nandita Bhattacharjee, “Fingerprint reference point detection based on local ridge orientation patterns of
fingerprints,” international Joint Conference on Neural
Networks, pp. 1-8, 2012.
[8] SWAIN, M.L, and BALLARD, D.H.: ‘Color indexing’, Int, J.
Comput.Vis., 1991, 7, (I), pp. 11-32
[9] Handbook of Multi Biometrics, , Arun A. Ross ,Karthik
Nandakumar .Anil K. Jain. Springer
[10] Finger print database - FVC2000 - Db1_a http://bias.csr.unibo.it/fvc2000
[11] Face Database - ORL (AT&T) http://www.cl.cam.ac.uk/research/dtg/attarchive/facedatabas e.html
[12] Arun Ross and Rohin Govindarajan, “Feature Level Fusion Using Hand and Face Biometrics”, Appeared in Proc. Of SPIE Conference on Biometric Technology for Human Identification II, Vol.
5779, pp. 196-204 (Orlando, USA), March 2005.
[13] M. Tico, P. Kuosmanen and J. Saarinen,”Wavelet domain features for fingerprint recognition”, ELECTRONICS LETTERS
4th January2001 Vol. 37 No. 1
[14] Handbook of Fingerprint Recognition. Maltoni, D., Maio, D., Jain, A. K., and Prabhakar, S. Springer, 2009.
[15] Multirate systems and Filter banks, P. P. Vaidyanathan, Englewood Cliffs; Prentice Hall. 1993.
IJSER © 2013 http://www.ijser.org