International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518
Wireless Broadband Network Technology Infrastructure and
Related Intellectual Property Application & Security
Nandini mishra, M.Tech (CSE), Department of Comp. Sc. & Engg. Bhagwant University, nandini.mishra73@gmail.com
Neelam maurya,M.tech (CSE), Department of Comp. Sc. & Engg. Bhagwant University, neelam.iandu@gmail.com
Nikita gaur,M.tech (CSE), Department of Comp. Sc. & Engg. MMMEC Gorakhpur, gaur.nikki@gmail.com
Abstract -
Since the beginning of this millennium, there has been an unprecedented growth in broadband wireless networks. This can be at tributed to high demand for wireless multimedia services such as data, voice, video, and the development of new wireless standards. The growth of wireless broadband networks is expected to gradually outpace landline communications because advancements in these technologies have continued to enable higher broadband speeds. This paper explores broadband fixed wireless and broadband mobile technologies. The characteristics of these technologies are examined. This paper also explores the relat ive strengths and weaknesses of each of the technologies as well as their relationship to each other. In this paper, we would be discussing about major issues pertaining to security feature in broadband technology. To know different securities aspect which may hinder advancement of b roadband technology? In this research paper taking up Wimax broadband technology working concepts and it’s different security features, which needs to be taken up at a clear scale.
Keywords : Wireless Broadband network technologies, Application, 4G Broadband, Security, limitation, Wireless Broadband work
1. INTRODUCTION
Generally, broadband wireless networks can be categorized into two types: fixed and mobile wireless. The broadband fixed wireless network technologies of interest here are Wireless Fidelity (Wi-Fi), which is an IEEE 802.11 standard and Worldwide Interoperability for Microwave Access (WiMax), which is also an IEEE 802.16 standard. The two broadband mobile wireless network technologies are the third Generation (3G) and Fourth Generation (4G) networks. The 3G standards are defined by ITU-T, IMT2000 and the standards for the 4G are currently being defined.
Security problems are increasing rapidly as hacker attacks on home PCs and major company websites such as government organizations. One of the most compelling uses of broadband connections is to allow enterprises to Connect branch offices and telecommuters into the corporate network with high speed remote access. To come across the suggested subsequent security solutions:
Firewall: To access control policy connecting two networks firewall implemented. Firewalls might be dependent on the software like checkpoint, CA or hardware appliance similar to Net Screen, watch guard and Nokia etc. Personal firewalls solutions still give the impression of being for Home users resembling Network ICE etc.
Anti-Virus: Anti-Virus looks for patterns in the files or memory of your computer to specify possible occurrence of a recognized virus.
Encryption: To think about encrypting traffic at your PC communications are mostly responsive. The beginning of denial of service attacks from these computers VPN, SSL provide secure for ecommerce transactions the Firewall with VPN protection secures sensitive data to the remote site and prevent both U-turn attacks and products similar to Net Screen PGP and Cisco etc. The type of tracking appears the danger of cookies.
Modem Security: In some cases modem configuration & authentication information would be stored on modem, in others, stored on your computer.
Shared Cable Modem Connection: Cable networks are shared among numerous subscribers in a given neighborhood. As a result, neighbors could monitor your transmission by using sniffer. Please ensure service provider upgraded networks and equipments to DOCSIS (Data over Cable Service Interface Specification).
Content Inspection: Since interactive technologies like
Java, JavaScript, ActiveX are a big part of broadband content sites & emails, as well as potentially an emerging vehicle for hack attacks. It is recommended that disable mobile codes such as Java, JavaScript & ActiveX. Disable scripting features in e-mail programs. You may want to explore active content security products such as Trend Micro, CA, and Finjan etc.
System Security: It is recommended that you log off & power down your PC when you are not using your connection.
2. WHAT IS A WIRELESS BROADBAND NETWORK?
Wireless broadband terminology should not be confused with the generic term ―broadband networking‖ or BISDN (Broadband Integrated Services Digital Network), which refers to various network technologies (fiber or optical)
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518

implemented by ISPs and NSPs to achieve transmission
speeds higher than 155 Mbps for the Internet backbone. In a lay-person’s terms, BISDN is the wire and cable that run through walls, under floors, from pole to telephone pole, and beneath feet on a city street. BISDN is a concept and a set of services and developing standards for integrating digital transmission services in a broadband network of fiber optic and radio media. BISDN encompasses frame relay service for high-speed data that can be sent in large bursts, the Fiber Distributed-Data Interface (FDDI), and the Synchronous Optical Network (SONET). BISDN supports transmission from 2 Mbps to much higher transfer rates. Wireless broadband, on the other hand, refers to the wireless network technology that addresses the ―last mile‖ problem whereby we can connect isolated customer premises to an ISP or carrier’s backbone network without leasing traditional T-1 and higher speed copper or fiber channels from your local telecommunication service provider. Wireless broadband refers to fixed wireless connectivity that can be utilized by enterprises, businesses, households and telecommuters who travel from one fixed location to another fixed location. In its current implementation, it does not address the needs of
―mobile users‖ on the road. Technologically, wireless broadband is an extension of the point-to-point, wireless- LAN bridging concept to deliver high-speed and high capacity pipe that can be used for voice, multi-media and Internet accessservices. While in simple implementations, primary use of wireless broadband is for connecting LANs
to the Internet, in more sophisticated implementations, you
may connect multiple services (data, voice, video) over the same pipe. The latter requires multiplexing equipment at customer premises or in a central hub. From an implementation perspective Wireless Broadband circumvents physical telecommunications networks; it is as feasible in rural as it is in urban areas. For topographies that haven’t yet technically evolved to cable and copper wire infrastructures, vendor solutions circumventing costly installation, maintenance and upgrades, means skipping 120 years of telecommunications evolution. In other areas, deregulation is making the licensing process for Wireless Service Providers (WSPs) hassle free.
Wireless broadband is faster to market, and subscribers are added incrementally, bypassing those installations that are required before wired subscribers can connect.
2.1.Type of broadband wireless networks
Fig. (1)Type of broadband wireless networks
2.1.1. Fixed broadband wireless networks
Fixed broadband wireless technologies can be defined
as high-speed wireless networks that connect to stationary locations and are intended to serve nomadic users . Wireless Fidelity (Wi-Fi) and Worldwide Interoperability for Microwave Access (WiMax) technologies are the fixed wireless technologies that are examined in this paper. These two technologies are respectively governed by IEEE 802.11 and 802.16 specifications.
Wi-Fi
Wi-Fi is the first high-speed fixed wireless technology to penetrate the fixed wireless broadband market. The first WLAN (802.11) which was introduced in 1997 was capable of supporting 2 Mbps and 802.11b was approved by IEEE in
1999. There are currently many wireless products based on
Wi-Fi technologies which include the approved IEEE
802.11a, b and g specifications, and a yet to be defined
802.11n specification. The impact 802.11n might have when it finally goes to the market may difficult to quantify at this time, but it is expected to deliver up to 600 Mbps. In a report in 2006, In-Stat stated that during 2008, more than 50% of the chipset shipped out will be based on 802.11n. Wi-Fi as a high-speed wireless technology has enjoyed broad deployment, most notably in hotspots around the world including homes and offices, and increasingly in cafes, hotels, and airports.
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518
WiMAX
Worldwide Interoperability for Microwave Access (WiMax) is an emerging fixed broadband wireless technology that will deliver last mile broadband connectivity in a larger geographic area than Wi-Fi. It is expected to provide coverage anywhere from one to six miles wide. Such WiMax coverage range is expected to provide fixed and nomadic wireless broadband connectivity without necessarily having a line-of-site (LOS) with a base station. WiMax will also enable greater mobility, higher speed data applications, range and throughput than its counterpart, Wi- Fi.
There are several advantages that can be derived from the deployment of WiMax. Firstly, it supports higher throughput rates, higher data speed rates, and wider operating range. These make the technology very useful for deployment in bad terrain areas or in environments with limited wired infrastructure. Moreover, WiMax supports and interfaces easily to other wired and wireless technologies such as Ethernet, ATM, VLANs, and Wi-Fi. The main drawback to the deployment of WiMax is proprietary equipment. WiMax equipment must be able to utilize power efficiently in order to deliver optimum functionality. For WiMax, the output power usage is based on a ranging process that determines the correct timing offset and power settings. Therefore, the transmissions for each subscriber station are supposed to be such that they arrive at the base station at the proper time and at the same power level. When WiMax is deployed outdoors, in non-line of sight environments it may encounter delay, which can cause potential intersymbol interference.
2.1.2. The broadband mobile wireless networks
The evolution of mobile service started with the first generation (1G) networks, which was implemented based on Frequency Division Multiple Access (FDMA) and these networks were basically for voice communication. The 1G network was replaced by second-generation (2G) networks, which are mainly used for voice applications.
These 2G systems provided circuit-switched data
communication services at a low speed. The competitive rush to design and implement digital systems led to a variety of different and incompatible standards . The 2.5G is an enhancement of the 2G technologies to provide increased data capacity on the 2G networks. This led to the introduction of technologies such as General Packet Radio Service (GPRS) and Enhanced Data Rates for Global Evolution (EDGE).
.
Third-generation networks
Third-generation (3G) networks started with the vision to develop a single global standard for high-speed data and high-quality voice services. The goal was to have all users worldwide to use a single standard that would allow for true global roaming.
Fourth generation networks
The 4G is a new generation of wireless intended to complement and replace the 3G systems, in the near future. Accessing information anywhere, anytime, with a seamless connection to a wide range of information and services, and receiving a large volume of information, data, pictures, video, and so on, are the key features of the 4G infrastructures. The future 4G infrastructures will consist of a set of various networks using IP (Internet protocol) as a common protocol so that users are in control because they will be able to choose every application and environment. Based on the developing trends of mobile communications, the 4G will have broader bandwidth, higher data rate, and smoother and quicker handoff and will focus on ensuring seamless service across a multitude of wireless systems and networks. The key concept is integrating the 4G capabilities with all of the existing mobile technologies through advanced technologies. Application adaptability and high dynamism are some of the main features of 4G services of interest to users. These features mean services can be delivered and available to the personal preference of different users and support the users’ traffic, air interfaces, radio environment, and quality of service. Connection with the network applications can be accomplished in various forms and at various levels correctly and efficiently. The dominant methods of access to this pool of information will be the mobile telephone, PDA, and laptop to seamlessly access the voice communication, high-speed information services, and entertainment broadcast services.
2.2. 4 G Mobile Broadband Technologies
4G mobile broadband technologies will allow wireless carriers to take advantage of greater download and upload speeds to increase the amount and types of content made available through mobile devices.
2.2.1 Defining 4G Mobile Broadband Technology
4G networks are comprehensive IP solutions that deliver voice, data, and multimedia content to mobile users anytime and almost anywhere. 4G technology standards offer greatly improved data rates over previous generations of wireless technology. Faster wireless broadband connections enable wireless carriers to support higher-level data services, including business applications, streamed audio and video, video messaging, video telephony, mobile TV, and gaming. Users need the ability to communicate, conduct business, and move around the globe as easily and seamlessly as they did with the ―around the corner‖ set.
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518
2.2.2 Trends Driving the Transition to 4G Technology
Unified Technology
Today’s global economy needs a ―borderless‖ or unified wireless platform. The world is shrinking and mobile users conduct business all across the world, much like they used to do with people around the corner.
Increasing Expectations
Today, customers require the same broadband experience they get at the office or at home, regardless of their locations. They want easy access and use, high speed and low latency, better security and privacy, and seamless, global mobility.
Rich Media
Music and video downloads, high-quality video conferencing, high-definition movie downloads, video on demand, and other trends are driving the need for 4G networks and their increased data capacity.
Personal Expression
Mobile users today want to do more than simply consume information. They want to create things and share them. They also want to do it anytime, anywhere through blogs, social networks, and similar applications they use with fixed-line Internet connections.
3. WIRELESS BROADBAND NETWORK
INTELLECTUAL PROPERTY
3.1 Business Scenarios - Where Wireless Broadband Is
Useful
Implementation depends on the type of business, its business needs and usage. These needs are different for households, small, medium and large businesses. Typical wireless broadband applications are:
Internet access: where it is difficult/expensive to lay pipe in cities/rural areas
Inter-LAN connectivity in a campus environment
Inter-building connectivity in a down town core where cable digging is a problem and expensive
Multimedia or video connection for TV services
Distance-learning based on permanent connections to remote areas where instructor material is based on using multi-media material
Government facilities in distant areas
Telemedicine and medical facilities: in patient/outpatient,
emergency rooms surgery
―As needed‖ connectivity in contrast to permanent
connectivity
Connecting historic or older buildings where laying cable could be difficult or expensive
Outdoor, field operations: disaster recovery, battlefields
Home banking
Interactive Gaming sites
3.2. The economic benefits of new spectrum for wireless broadband
Fig.2. 4G Mobile Broadband Technologies
2.3.Broadband Solutions
Adaptive Broadband :
Cisco.
EndGate :
Ericsson:
Fuzion
Lucent Technologies
Motorola’s Aspira Architecture for Broadband
New bridge of Ottawa, Canada, now owned by
Alcatel of Europe
Nokia’s Broadband Offering
Nortel
Nucentrix
Spike Technologies
WaveRider
3.2.1. The surge in wireless data traffic has caused a
“Spectrum crunch.”
With the proliferation of smartphones, tablets, and other mobile devices with internet access, wireless data traffic has grown tremendously, increasing by more than 100% between 2009 and 2010. Industry forecasters expect that a rapid pace of growth in data traffic will continue for at least the next few years. For example, one industry forecaster projects that mobile data traffic will increase by a factor of
20 between 2010 and 2015. It is unlikely that wireless carriers will be able to accommodate this surging demand without additional spectrum. Other approaches to expanding the capacity of wireless networks, including improvements in spectral efficiency, increases in network density through cell site construction, and offloading traffic to wireline networks via Wi-Fi or other antenna systems, will likely be insufficient to allow capacity to keep up with demand. In short, the projected growth in data traffic can be achieved only by making more spectrum available for wireless use. In response to this ―spectrum crunch,‖ the Obama Administration has proposed making an additional 500 MHz of spectrum available for wireless broadband.
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518
Wireless data traffic has increased dramatically in recent years
The rapid growth in wireless data traffic shows no sign of slowing
The surging demand for wireless services cannot be met without additional spectrum.
3.2.2.Wireless broadband can serve as a platform for innovation.
Wireless broadband has the potential to transform many different areas of the American economy by providing a platform for new innovation. Areas where the innovations will likely have significant impact include consumer products and services, such as media-rich mobile apps and high definition streaming video; products to enhance business productivity, such as mobile video conferencing solutions and access to web-based business applications; health care, where the quality of care will be enhanced and costs reduced through products like patient-physician video conferencing and remote transmission of diagnostic information and images; and education, where digital classroom materials and educational applications are already enhancing learning.
Consumer applications
Business Productivity
Health Care
Education
3.2.3Wireless broadband will have significant benefits for public safety.
Wireless broadband has a vital role to play in improving the ability of emergency personnel to communicate efficiently and to obtain necessary information quickly, including real- time videos, images, and other data. The creation of a state- of-the-art nationwide wireless broadband network for public safety communications will ensure that the public safety benefits of wireless broadband are available throughout the nation, and will also enable interoperability at the national level, making first responders more effective when they are called on to cross jurisdictional lines. With sufficient dedicated spectrum for public safety use, public safety personnel will have access to critical information even in emergency situations when commercial wireless networks are congested.
3.2.4.Wireless broadband is likely to have a substantial impact on jobs, growth, and investment.
Like other information and communication technologies that have transformed the economy in the past, the spread of wireless broadband is likely to increase the rate of growth in per capita income; spur economic activity through new business investment; and support many new highquality jobs. Because these effects are difficult to quantify precisely, CEA does not endorse any specific numeric prediction. Nonetheless, the evidence is clear that the wireless industry is an important source of investment and
employment, and that supporting the growth of this industry
through new spectrum allocation is likely to generate substantial economic benefits.
Evidence on the economic impact of information and communication technology: A large body of literature has linked macroeconomic performance with the growth in information and communication technology
Evidence on the economic impact of broadband: A number of economic studies have examined the impact of broadband on measures of economic
Projections on the economic impact of wireless broadband: Although it is too soon for the
empirical data to yield reliable estimates of the economic impact of wireless broadband, a few studies have estimated economic effects with the
available evidence.
Other countries recognize the importance of wireless broadband.
Japan and South Korea have been world leaders in rolling out high-speed broadband services, and enjoy high levels of wireless broadband adoption. Europe, too, is moving forward with efforts to
improve wireless broadband.
Voluntary incentive auctions and new unlicensed spectrum will promote economic benefits:For commercially held spectrum, voluntary incentive auctions will ensure that spectrum is repurposed from the lowest value uses to the highest; and that the economic benefits are widely shared among stakeholders, including broadcasters, wireless carriers, consumers, and taxpayers.
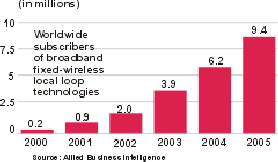
Fig (3). Wireless Broadband Market
4. DISTANCE LIMITATIONS ON WIRELESS Broadband
Distances vary with frequency band, technology and vendor implementation. One factor that users must keep in mind that performance or throughput may become lower with distance because of signal strength after certain distance may not be sustainable at higher speeds. Therefore, some vendors offer lower speeds at greater distances. Speeds in wireless broadband (mid-2000 circa) can go from sub one megabit (< 1 Mbps) to 45 Mbps range.
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518
The following table gives some idea of frequency, speed and
distance relationship:
Type of Broadband Technology | Frequency | Distance | Range of DataSpeed** |
MMDS | 2.1 to 2.7 GHz | 30 to 35 miles | 10 Mbps |
International WLL | 3.2-3.7 GHz | 25 miles | 10-11 Mbps |
ISM | 902-928 MHz | 5 to 25 miles | 5-7 Mbps |
LMDS | 24 to 38 GHz | 3 to 5 miles | Up to 45 Mbps |
Table (1) Relationship Between Frequency, Distance and
Speed.
5. WIRELESS BROADBAND WORK
Essentially you need a piece of equipment in each building where you want to connect two LAN segments. For those situations, where a clear line of sight is not available, one or multiple hubs may be deployed – acting as repeaters and logical diverters of radio signals. The Customer Premise Equipment (CPE) in most implementations consists of two fundamental components: a Network Interface Unit (NIU) - an indoor unit providing circuit emulation and Ethernet data services – essentially a Transceiver and an antenna unit mounted on the top or side of the building. In some cases, the transceiver and antenna are integrated into one unit – e.g. in Nortel’s Reunion Broadband Wireless Access products. NIU is connected to the data network (typically a LAN) in the two buildings.
5.1. Point to Point Broadband Network
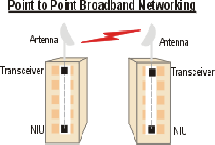
Fig 4(a) Point to point Broadband Network
Where multiple services (voice and data are employed), there is another piece of equipment that is called Base station equipment – that provides multiplexing and channel separation.
In those cases where a clear line of site is not available between to points or where multiple locations need to be served, there is a Hub in the center as shown in the following schematic.
5.2. Multipoint Broadband Network
Differences in data transfer between components reveal some of the benefits of a wireless system as opposed to other technical alternatives like cable and Digital Subscriber Line (DSL), or traditional ISDN.
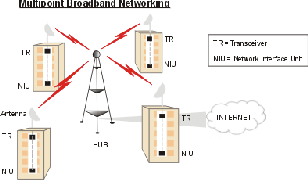
Fig 4(b) Multipoint Broadband Networking
6. HIGH SPEED NETWORKS
6.1. Goals set in speed measures
The most commonly used term to describe future planning for the next transition in networked connectivity is simply
―next generation,‖ used in reference to networks or access.
Most of the definitions and considerations focus on measurable capacity, and largely continue to use speed as its measure. The Ofcom document in the United Kingdom,
―Delivering Super-Fast Broadband in the UK‖2 is a well- thought-out document that offers a crisp example of this approach. The goal, while occasionally described in that document by the generic term ―next generation access,‖ is usually referred to as the title indicates: ―super-fast broadband.‖ The goal is defined in terms of download and uploads speeds. The speeds set out as future goals in the UK document as ―very fast‖ are what would be considered as second-tier speeds by the standards of what is available today in the best performing countries: 40 to 50 Mbps download, and 20 Mbps upload. Complementing this target, the government document ―Digital Britain‖ emphasizes a commitment to universal availability of 2Mbps downstream service by 2012. This too is a modest goal by the standards of the highest performing countries, but is broadly consistent with the near-term goals of other European countries' universal access plans.
6.2. Dual targets
Many of the European plans adopt a dual-track approach. They seek truly universal access to first generation broadband technologies, and independently also seek to catalyze high levels of availability and adoption of next generation capacities. The Finnish Government's National Plan of Action for improving the infrastructure of the information society sets a goal that by 2010 every permanent residence, permanent business, and government body will have access to a network with an average
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518
download rate of 1Mbps.3 The Finnish plan has a more
ambitious medium-term goal, calling for a fiberoptic or cable network permitting a 100Mbps connection to be available for access within 2 kilometers of 99% of permanent residences, businesses, and public administration bodies by 2015. The ―bite‖ of this plan is that it authorizes regional governing bodies that conclude that market demand will not meet that target to design public plans that will. The German Federal Government's Broadband Strategy4 adopts a similar two-step strategic goal, with universal availability of at least 1Mbps throughout Germany targeted by the end of 2010, and a less ambitious availability of 50Mbps to 75% of households by 2014. That target is out of step with offerings already available in the highly competitive French market, but is intended to represent a commitment to truly universal access to what would count as prior-generation broadband. Since that time, a new minister has been appointed and the targets are reorienting towards a fiber and applications-based definition of targets, as well as to supporting fixed-mobile convergence.6 Recognizing this dual-target approach of universal access to first generation broadband and high degrees of penetration for nextgeneration connectivity, the European Commission's recent guidelines on state aid specifically separate out first generation broadband networks and next generation networks for separate analysis.
6.3. A focus on fiber
Another way of defining ―next generation‖ in terms of high and potentially growing capacity is to focus on the trajectory of deployment of fiber-to-the-home (FTTH) in particular.
The recent European Regulator's Group report entitled
―Report on Next Generation Access: Economic Analysis and Regulatory Principles‖ captures the degree to which this focus on ―next generation‖ heavily emphasizes fiber as a widely shared goal in Europe.8 This approach is at odds with the equally widely-stated commitment to technological neutrality in government planning. The ERG report attempts to reconcile this tension by emphasizing that cable broadband also largely depends on fiber backhaul; that current investments in higher-speed cable infrastructure include pulling fiber deeper into the neighborhood; and that a core goal of all current models is therefore to bring cable as close to the home as possible.
.
6.4. Capacity to support future applications
A variant of the effort to define high capacity as the measure of the next generation transition uses anticipated applications, rather than speed measures, or as a complement to speed measures, to define the goal. This variant is most explicitly represented in South Korea's IT839
program. South Korea uses the term ―ubiquity‖ to describe
its goals, but defines it very differently than that term is used in Japan, as we will see. South Korea's plan calls for a network aimed to support a list of eight services, three infrastructures, and nine growth engines, hence 839. Ubiquity gets translated most directly into WiBro service— wireless broadband, anytime, anywhere, on the move; digital multimedia broadcasting, in vehicle infotainment, RFID etc. The three infrastructures are called Broadband Convergence Network, aiming to provide services of 50-
100Mbps to 20 million people, Ubiquitous Sense Network,
to manage information through RFID so that things can be connected to people, and provision of Ipv6-based services.
7. WIRELESS BROADBAND NETWORK APPLICATION
7.1. Bandwidth requirements for broadband application
Application | Upstream Speed | Downstream Speed |
Medium-Resolution Videoconferencing (640x480P) | 384-1200 Kbps | 384-1200 Kbps |
Streaming Video (720P) | 1.2 - Mbps | |
Standard-Definition Digital Television (720x480 Interlaced) | 4 Mbps | |
Basic HD Videoconferencing (1280x720 resolution) | 1.2 - 4 Mbps | 1.2 - 4 Mbps |
Telepresence: High- Resolution HD Videoconferencing (1920x1080 resolution) | 5 Mbps | 5 Mbps |
Video Home Security Service | | 10 Mbps |
High-Definition (HD) Digital Television (1440x1080 Interlaced) | | 15 Mbps |
Telepresence: Very High- Resolution HD Videoconferencing (5760x1080) | 15 Mbps | 15 Mbps |
Table (2): Bandwidth requirements for broadband applications
7.2. Speech Recognition Enabled Wireless Applications
Speech is the most intuitive user interface for conversation and communication. Therefore, speech recognition technology has been touted as a promising technology that will solve following problems in mobile and wireless applications:
User input interface
Conversion of text to voice and vice-versa
While using voice-based input to business applications still in early stages of development except for simple set of commands, voice has crept into a number of IT applications.
7.3. Take advantage of Ceragons’s wireless backhaul
platform featuring
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 3, Issue 11, November-2012
ISSN 2229-5518
Industry leading system gain
Advance Network capabilities
Highest Spectral Efficiency
Support for All-IP
Seamless integration with any HSPA,WiMAX and
LTE Network
8. WIRELESS & MOBILE COMPUTING SECURITY
8.1. Security in Broad Sense
Securing information from unauthorized access is a major problem for any network - wireline or wireless Security, in a broad sense, focuses on network security, system security, information security, and physical security. It is made up of a suite of multiple technologies that solve numerous authentication, information integrity, and identification problems. It includes the following technologies – firewalls, authentication servers, biometrics, cryptography, intrusion detection, virus protection, and VPNs
8.2. The task of securing wireless networks can be divided into five challenges:
Network access control
Network resource protection
End-point, including wireless client, protection
Secure end-to-end data traffic transmission
Secure network configuration, operation and management
8.3. Understanding the Components
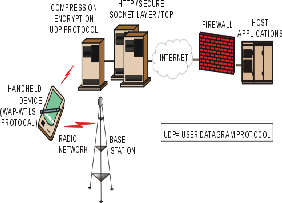
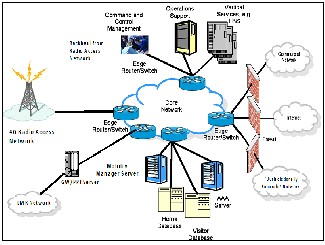
Fig (5) A Schematic of Security Architecture for Mobile
WAP-based Devices
9. CONCLUSION
This paper examined the fixed and mobile broadband
wireless networks and provides a comparative view of both technologies. There has been an unprecedented rapid growth in the demand for mobility globally, seamless communication, data services, and ubiquitous computing. Fixed broadband wireless networks are helping users meet
the growing need for broadband wireless access at hotspots
and beyond, while broadband mobile technologies are expected to enable broadband wireless network access for highly mobile users. When discussing the security of wireless technologies, there are several possiblePerspectives. Different authentication, access control and encryption technologies all fall under the umbrella of security. Although relevant and important building blocks for overall security, these are not the focus of this paper. Instead, it will explore the problems at the implementation level of the current wireless access technologies and their Real world implications.
Many operators today are being forced to seriously consider the integration of Wi-Fi just to address capacity issues. A number of others, however, are moving beyond this basic entry point, incorporating Wi-Fi into their overall network strategy, with a focus on using the best available Wi-Fi technology in order to enable significant new business opportunities. Given the significant competitive advantage a coherent and well-executed Wi-Fi strategy can create — in a world of exponentially rising bandwidth demand — the technology merits serious consideration
10.REFERANCE
1.Government Resolution: National Plan of Action for improving the infrastructure of the information society. Government of Finland, 4
December 2008.
2.Federal Ministry of Economics and Technology, February 2009.
3.Eric Besson, Digital France 2012. October 2008.
4..http://www.arcep.fr/fileadmin/reprise/communiques/communiques/2
6. Advanced Encryption Standard Fact Sheet. (2001, January 19).
Retrieved August 28, 2010, from http://www.kern.com/files/SecurityFinal_F.pdf
7. Aikaterini, A-V. (2006). Security of IEEE 802.16.
Royal Institute of Technology.
8.. Bai,L.(2007).Analysis of the Market for WiMax Services.
9. Barbeau, M. (2005). WiMax/802.16 Threat Analysis. Q2SWinet’05.
10. Barongo,M.W. (2008). Dimensioning MobileWIMAX
in the Access & Core Network: A Case Study. HELSINKI UNIV.
11. Bruno Puzzolante, G.R. (2006). Nationwide Implementation of a
WiMAX Mobile Access Network
12. Chungo-Kuo Chang, C.-T.H. (2007). Secure Mobility for IEEE 802.16e Broadband Wireless Networks.
13. Edurado B.Fernandez, M.V. (2007). Patterns for Wimax security.
14. G.Cayla, S.C. (November, 2005,). WIMAX an Efficient.WiMax
Forum.
15. G.Nair, J.C. (2004). IEEE 802.16 Medium access Control & Service
Provisioning Intel Technology Journal.
16. Hasan J. (2006). Security Issues of IEEE 802.16. School of
Computer and Information.
17. IEEE. (2004). IEEE Std 802.16-2004, IEEE standard for WiMax
802.16-2004.
18. Muleta, J. (2005). Broadband Technologies for rural Development. NCC Rural Access.
19. Prakash, N. (2006). Wireless Broadband Access Using WiMax
Standard.
20. Sikkens B. (2008). Security Issues and proposed solutions concerning authentication and authorization for WiMax. 8th twente student Conference on IT.
21.Monica Paolini is the founder and president of Senza Fili Consulting and can be contacted at
monica.paolini@senzafiliconsulting.com.
IJSER © 2012 http://www.ijser.org





