International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1347
ISSN 2229-5518
WMI Based Real Time Agentless Enterprise
Monitoring
Balaji Patil, Ankur Jain, Vinay Kumar Pathak
Abstract— Looking towards the complex, heterogeneous and dynamic nature of the networks, failures are unavoidable. Monitoring can be used for detection and reporting of failures. This underlines the need to develop a unified strategy for implementation and management of network resources in an enterprise.
This paper describes novel agentless system for real-time monitoring of windows based clients remotely by subscribing to those remote events. Monitoring is done using W indows Management Instrumentation (W MI) services. Results of service events are stored in Server. This system is called as Unified network resourse management system. We have demonstrated the system's capabilities and the results that are obtained from the clients using W MI services. These results include system hardware configuration, software configuration in terms of OS details, applications installed etc. This information is very useful to the administrator for maintenance of failures in the networks. Any change at the client system details, will be notified automatically by the clients to the server, so that server will have real- time updated information. This updated information will be very helpful incase of crashing of the remote client. Using this collected data, crashed clients can be restored in very short period of time. Real time monitoring of the clients is necessary for the maintaining the health of an enterprise network.
Index Terms— Agentless, Event, Enterprise monitoring, Passive Monitoring, Remote monitoring
—————————— ——————————
N todays era of Information Technology (IT), technology is developing rapidly and introduction of new applications will further promote the IT development. Looking towards the complex, heterogeneous and dynamic nature of the thou- sand nodes of enterprise networks failures are unavoidable. So monitoring is used for detection and reporting of failures. In such a complex environment network administrators have to struggle a lot in order to solve the network problems rapidly
and effectively ensuring their availability.
With the expansion of network scale, administrators can not
complete these tasks manually. It becomes difficult to main-
tain the enterprise resourceses, monitor their availability and security of data. Administrators have to take the help of au- tomated tools. In the management of enterprise network find- ing reasonable and feasible solution to improve the efficiency
of system is a challenge.
So we propose a better and effective unified network man-
agement approach. In this approach we collect more and more
remote data from clients in real-time. After collection and
analysis of this data the network resources are managed.
Unified network resource management strategy is just seen as
managing the changing resources in the networks or clients
for example, the hardware configuration, options and strate-
gies of the operating system etc. This dynamism underlines
the need to develop a unified strategy for implementation and
————————————————
• Ankur Jain has completed his BE Computer Engineering from Maharashtra
Institute of technology, Pune, India. E-mail: ankurjain2190@gmail.com
management of network resources in an enterprise.
Most of the remote network management systems are devel- oped by the Windows-based component development i.e. COM as across Windows Management Instrumentation Commands (WMIC) provides very powerful functions for light weight implementation of remote network management. With this motivation we have developed a uniform standard remote resource management and monitoring enterprise sys- tem using WMIC services, consisting managing computer sys- tem resources, user resources and necessary alarming mecha- nisms.
So a better automated solution is developed using WMIC for remote management of components services that monitors resources without causing any distarbance in usual organiza- tion work.
This paper is organized in 5 sections. In section 1 we have tried to expain the need and motivation for development of unified resourse management system. Section 2 explains the technologies/techniques used for development of the system. Section 3 explains the proposed enterprise resource manage- ment system. In section 4 we have discussed the results and in section 5 we have written the conclusion.
In this section we are revising the technologies, techniques and existing tools available. In the past remote resourse man- agement systems has been developed using various technolo- gies like SNMP, COM, RMON etc.
The SNMP service is most widely used service for monitoring of networks. SNMP had a disadvantage of requirement of re-
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1348
ISSN 2229-5518
mote agent. Another thing that needs to be mentioning is that
being only a protocol, SNMP cannot offer the full management support that the typical enterprise system needs. While WMI provides the remote agentless monitoring of network. So we have used the WMI technology for development of automated unified resourse management system.
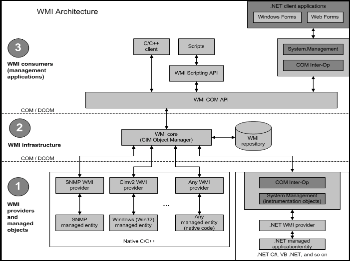
Windows Management Instrumentation (WMI) [4] is the Mi- crosoft implementation of Web-Based Enterprise Management (WBEM), which is an industry initiative to develop a standard technology for accessing management information in an en- terprise environment. WMI uses the Common Information Model (CIM), a industry standard to represent systems, appli- cations, networks, devices, and other managed components. The ability to obtain management data from remote client- computers is what makes WMI useful. Remote WMI connec- tions are made through DCOM. The WMI Architecture is as shown in the fig.1.
Fig. 1 WMI Architecture [4]
For monitoring of the networks various types of monitors are available. We have used the Active monitoring for real-time notification of the events or changes in the enterprise net- works. Monitors are of following types-
The passive monitoring [5] approach uses devices to watch the traffic as it passes through it. These devices can be special purpose devices such as a sniffer or they can be built into oth- er devices such as routers, switches or even end nodes. Exam- ples of such built in techniques include Remote monitoring, SNMP and WMI devices. The passive monitoring devices are polled periodically and information is collected to assess net- work performance and its status.
The passive approach measures the real time traffic on the enterprise network without increasing overhead on the net- work.
There are various automated network monitoring tools are available in the market, few of them are mentioned below with their features.
PRTG Network Monitor [9] monitors system availability us- ing a variety of methods from simple ping through SNMP and WMI protocols to specific tasks such as HTTP, DNS and Re- mote Desktop availability using sensors. Using specific sen- sors for specific machines, an administrator can monitor ser- vice availability and reliability. Also, PRTG comes with some bandwidth monitoring sensors, which can trap the DOS at- tacks and performance of networks related issues. PRTG is easy to install & operate and it supports all Windows versions, XP/2003 or later. It has inbuilt number of graphical utilities for visual presentation of the collected monitoring infor- mation. A host of supported network services and protocols: SMTP, PING, HTTP, POP / POP3, FTP, PPP, etc.
Whatsup gold [10] is a network management suite. It can monitor devices using SNMP. Whatsup gold also features WMI support for Windows monitoring and agentless SSH monitoring for Linux/Unix systems monitoring everything on your network. A wide range of plugins are available for Whatsup gold. There are five main aspects to this software: Discovery, Mapping, Monitoring, Alerting, and Reporting. It provides Performance monitors (CPU utilization, Disk and space utilization, Interface utilization, Memory, Ping Latency etc). It supports application monitoring but requires polling at regular intervals and hence it consumes network bandwidth.
Operations Manager [11], a component of Microsoft System
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1349
ISSN 2229-5518
Center 2012, is software that helps you monitor services, de- vices, and operations for many computers from a single con- sole. Operations Manager will tell you which monitored ob- jects are not healthy, send alerts when problems are identified, and provide information to help you identify the cause of a problem and possible solutions. Administrator can configure what will be monitored by selecting computers and devices to be monitored and importing management packs that provide monitoring for specific features and applications. Major dis- advantage of this tool is it has bugs in monitoring applica- tions.
All these above mentioned tools have some advantages and shortcomings, so this study underlines need of developing a unified automated monitoring tool which will monitor the enterprise network. Table 1 shows the impact of monitoring method, which provides the reason for development of an agentless WMI based automated monitoring tool [11].
TABLE 1
Methods of Monitoring
Method of Moni- toring | Impact of overheads |
With Agent | Processor: 1% average increase in processor utilization Disk: 9% average increase in pages/second Space: 351 MB data Network: 02 MB/min additional traffic Memory: Requires 19-32 MB memory |
Agentles s | Processor: less than 1% average increase in processor utilization Disk: less than 1% average increase in pag- es/second Space: less than 10 MB Network: less than 1 MB/min additional traffic Memory: Required only 1MB memory |
Considering the need of enterprise network management an automated tool is developed with required features. Real time agent less discovery of clients is basically monitoring the in- frastructure, changes taking place in client’s environment, etc. These changes are then notified to the server (administrator). This helps administrator to take necessary decisions accord- ingly and it ensures availability and reliability of enterprise network.
For developing the unified monitoring tool one has to decide
the critical areas and devices, parameters to be monitored as per the need of enterprise.
For this to happen the administrator must first subscribe those
events for which it requires notification from the clients. These
events are subscribed using temporary event subscription. After the connection is established between the clients and server, once the server subscribes events to the clients, it re- ceives notifications from the client in real time.
In this section we have described principles [4] considered in the development of the system - i) Support for remote client monitoring and control of resources by reading the remote client data in real time ii) Support for heterogeneous operating systems iii) Single central server for storage and retrival of comprehensive client data iv) To provide a graphical user in- terface for collecting and presenting the data collected from the clients v) Easy to use, easy to expand, low-cost, high- performance enterprise resourse management system.
The remote CPU is able to be operated in the same way as lo- cal computer. Remotely performance monitoring and client availability is done. The performance measurement parame- ters are CPU utilization, memory utilization, free disk space, new software installation, network adapters and OS patches, etc. These results which are monitored will be outputted to web-based graphical user interface using dynamic HTML technology.
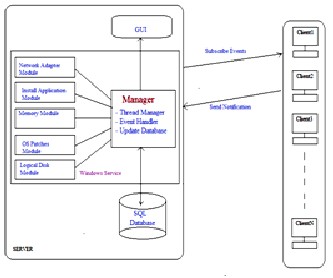
Fig. 2 System Architecture
The system architecture has following components-
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1350
ISSN 2229-5518
The services are first initialize using COM components. In order to receive asynchronous event notifications, WMI calls the ProvideEvents() method to notify the provider to start providing event notifications. One of the arguments of this method is a pointer to the IWbemObjectSink interface that is used by the provider to forward its events to a consumer.
Then WMI registers its event handling code (represented by
the IWbemObjectSink pointer) with a provider, so that the pro- vider calls the IWbemObjectSink::Indicate method each time an event is triggered which enumerates class properties. At the same time, database is updated and notification is popped up in the GUI. The system is implemented using in Microsoft Visual C++ and HTML.
The collected data can be used for various purposes such as managing network, handling security, identifying potential issues with client systems, illegal activities and installation of any unauthorized applications.
Following is the algorithm for connecting to the remote client for subscribing to events and receiving events notifications within seconds of occurrence.![]()
![]()
![]()
The events for which notifications are required are mentioned in the Table 2. For event notifications, event subscription que- ry is generated and sent to the target client. As and when events occur, they are notified to the server.
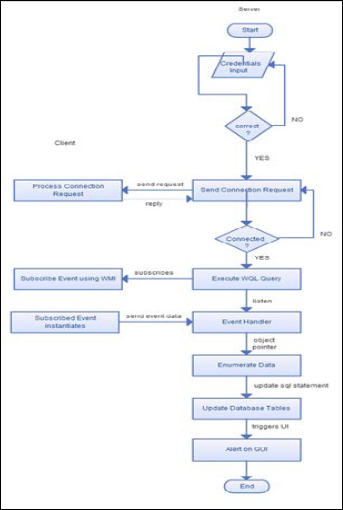
The flowchart for monitoring the network is shown in fig. 3.
Fig. 3 Flowchart for Monitoring
TABLE 2
Event Notifications for Devices
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1351
ISSN 2229-5518
In this section we have discussed the results of our system, which shows the notifications received form the clients for changes happened. Fig. 4 shows events data received from client and is stored in database. Data includes information about Adapter Type, Caption, Description, name of the Net- work Adapter changes from Client. Similarly fig. 5 shows events received form clients it includes Caption, File System, Volume Name and what is the change in Logical Disk from Client.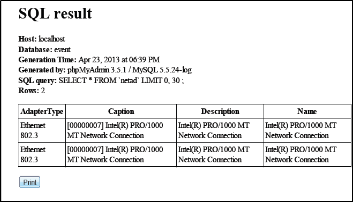
Fig. 4 Network Adapter Update in Database at Server
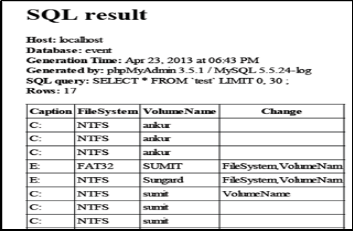
Fig. 5 Logical Disk Update in Database at Server
We have developed a monitoring service that will change the current monitoring techniques used in the enterprise monitor- ing. This system is helpful in pulling event notifications from remote clients in real time. It also monitors the infrastructure of the enterprise and generates necessary notifications period- ically based on request. The developed system will be very useful to the administrator without any significant overheads on network traffic because of its angentless nature. This sys- tem can be used for-
i) Detection of failures in the functioning of com- plex enterprise networks.
ii) The collected information can be used for health
monitoring of enterprise networks.
iii) The information can be used to create virtual en- vironment and backup of the workspace in case of disaster recovery.
iv) This service helps in managing enterprise re- sources and making informed decisions by the administrator as well as manager.
As a part of the future work the system can be extended for non Windows OS. The modified and extended version of this system can be used for the replication and creating a virtual machines.
I would like to thank Dr.Maitreya Natu from TRDDC, Pune for guiding me. I thank Dr. L. K. Kshirsagar, Principal, MIT Pune for helping me to publish this paper.
[1] Patricio Domingues, Paulo Marques, Luis Silva ESTG, “Resource Usage of Win- dows Computer Laboratories” – Leiria, Portugal Univ. Coimbra, Portugal Univ. Coimbra – Portugal
[2] Matt Schnaidt ,Debra Hensgen, John Falby, Taylor Kidd, David St. John, “Pas- sive, Domain-Independent, End-to-End Message Passing Performance Moni- toring to Support Adaptive Applications in MSHN” Computer Science De- partment Naval Postgraduate School Monterey, CA 93943-5118
[3] Ammu Qudsiya, “Modeling Performance Monitoring Of It Infrastructure Com- ponents Using Timed Petri Nets”. A* – Research Scholar, Department of Mathematics, Mother Theresa Women’s University, Kodaikanal, India. In- dian Journal of Computer Science and Engineering (IJCSE)
[4] Hui Peng and Yao Wang, ”WMIC Realize Enterprise Remote Information Management “, Second Pacific-Asia Conference on Circuits, Communications and System (PACCS) -2010
[5] Genevieve Bartlett, John Heidemann, Christos Papadopoulos, “Understanding Passive and Active Service Discovery” http://www.sigcomm.org/events/sigcomm-conference
[6] Antonis Papadogiannakis, Demetres Antoniades, Michalis Polychronakis, and Evangelos P. Markatos, “Improving the Performance of Passive Network” www.ist-lobster.org/publications/papers
[7] Martin Friedrich, ” Making WMI Queries in C++ “, www.codeproject.com
[8] http://msdn.microsoft.com.len-us/default.aspx
[9] http://www.paessler.com/prtg [10] http://www.ipswitch.com/ [11] http://technet.microsoft.com/
IJSER © 2015 http://www.ijser.org