International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 971
ISSN 2229-5518
Throughput Evaluation In Heterogeneous
Networks
Mr. Prajwalsingh C. Parihar Mr. Parul Sahare Mr. Kapil Lalwani. Asst. Professor. Asst. Professor. Asst. Professor.
Dept. of ECE Engg. Dept. of Electronics Engg. Dept. of Electronics Engg. DBACER, Nagpur RKNCE, Nagpur DBACER, Nagpur
e-mail : prajwal.parihar@gmail.com
Abstract-Today’s wireless users expect great things from tomorrow’s wireless networks. These expectations have been fueled by hype about what the next generations of wireless networks will offer. The rapid increase of wireless subscribers increases the quality of services anytime, anywhere, and by any-media becoming indispensable. Integration of various networks such as CDMA2000 and wireless LAN into IP-based networks is required in these
kinds of services, which further requires a seamless vertical handoff to 4th generation wireless networks
The proposed handoff algorithm between W LAN and CDMA2000 cellular network is implemented. The results of the simulation shows the behavior of the handoff and the time spent in WLAN or CDMA. The number of weak signal beacons determines whether a handoff is required or not. In this Algorithm, traffic is classified into real-time and non real-time services.
Index Terms— 1. Introduction, 2.NS-2 overview, 3. 3. Example: An Overlay Networks, 4. Handoff, 5. Horizontal Handoff, 6. Vertical
Handoff, 7. Overview, IEEE 802, and 802.11 Working Group, 8. Architecture of WWAN
(CDMA 2000), 9. Architecture of WLAN, 10. Workflow, 11. Basic Wireless Scenario, 12. Options, 13. Set up Simulator, 14. Configure
Nodes, 15. Create Nodes, 16. Source and Destination, 17. Run It, 18. Trace File, 19. Results, 20 Refrances
—————————— ——————————
1. Introduction
In the past decade, the telecommunications industry has witnessed an ever accelerated growth of the usage of the mobile Communications. As a result, the mobile communications technology has evolved from the so-called second-generation (2G) technologies, GSM in Europe, IS-
95(CDMA) and IS-136 (TDMA) in USA, to the third generation (3G) technologies. Along with the standards development for providing voice service to mobile users, a group of standards to deliver data to the mobile users have evolved from both SDOs (Standards development organizations) and industry. Systems and applications, such as Short Message Service (SMS) for sending and receiving short text messages for mobile phone users, have been built and continue to be developed.
2G systems such as GSM, IS-95, and CDMA One
were designed to carry speech and low bit rate data. 3G systems were designed to provide higher data rate services. During the evolution from 2G to 3G, a range of wireless systems, including GPRS, Bluetooth, WLAN and Hiper LAN have been developed. All these systems were designed independently, targeting different service types, data rates, and users. As these systems all have their own merits and shortcomings, there is no single system that is good enough to replace all the other technologies. In cellular networks such as GSM, a call is seamlessly handed over from one cell to another using hard handover without the loss of voice data. This is managed by networks based
handover control mechanisms that detect when a user is in a handover zone between cells and redirect the voice data at the appropriate moment to the mobile node via the cell that the MN has just entered. In 4G networks a handover between different networks is required. A handover between different networks is referred to as a vertical handover. Although commercial mobile telephone networks existed as early as the 1940’s, many consider the analog networks of the late 1970’s to be the first generation (1G) wireless networks.
4G Networks are all IP based heterogeneous
networks that allow users to use any system at anytime and anywhere. Users carrying any integrated terminal can use a wide range of applications provided by multiple wireless networks. 4G systems provide not only telecommunications services, but also a data-rate service when good system reliability is provided. 4G networks face number of challenges in providing service anywhere and anytime.
An event when a mobile station moves from one wireless cell to another is called Handoff.
In this project we are going to discuss Handoff
Criteria, Handoff Strategies, Handoff Methods, Handoff
Scenarios and different types of handoffs. We will also discuss WLAN-CDMA Cellular interconnection architecture based on IP [24]. And finally we will implement algorithm for Vertical handoff procedure between WLAN and CDMA cellular network. The algorithm will deal with two different types of handoffs, Mobile download handoff procedure in which mobile host moves from WLAN into CDMA network
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 972
ISSN 2229-5518
and Mobile Upward handoff procedure in which mobile host moves from CDMA into WLAN
2. NS-2 overview
• Collection of various protocols at multiple layers
– TCP(reno, tahoe, vegas, sack)
– MAC(802.11, 802.3, TDMA)
– Ad-hoc Routing (DSDV, DSR, AODV, TORA)
– Sensor Network (diffusion, gaf)
– Multicast protocols, Satellite protocols,
and many others
• Codes are contributed from multiple research
communities
– Good: Large set of simulation modules
– Bad: Level of support and documentation varies
• The source code and documentation is currently maintained by VINT project at ISI
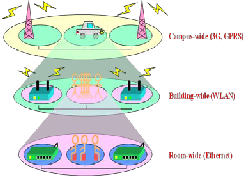
3. Example: An Overlay Networks
activities would be considered as a Horizontal handoff, since connection is disrupted solely by device mobility.
6. Vertical Handoff
A Vertical handoff is a handoff between two network access points, which are using Different connection technologies. For example, when mobile device moves out an 802.11b network into a GPRS network, the handoff would be considered a vertical handoff.
7. Overview, IEEE 802, and 802.11 Working
Group
• IEEE Project 802 charter:
– Local & Metropolitan Area Networks
– 1Mb/s to 100Mb/s and higher
– 2 lower layers of 7 Layer OSI Reference
Model
• IEEE 802.11 Working Group scope:
– Wireless connectivity for fixed, portable
and moving stations within a limited area
– Appear to higher layers (LLC) the same as
existing 802 standards
• Transparent support of mobility
(mobility across router ports is being address by a higher layer committee)
8. Architecture of WWAN (CDMA 2000)
4. Handoff
The transfer of a cellular phone transmission from one radio frequency within a cell to another radio frequency in an adjacent cell. Handoffs occur when a cellular phone user passes out of the range that the cell can handle and into another cells range, and the signal is passed from one base station to the next. The handoff is transparent to the user and typically will not result in a loss of service unless the user moves out of range of a cells base station. The transition and the process required to make the transition are both referred to as the handoff.
5. Horizontal Handoff
A Horizontal handoff is a handoff between two network access points that use the same network technology and interface. For example, when a mobile device moves in and Out of various 802.11b network domains, the handoff
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 973
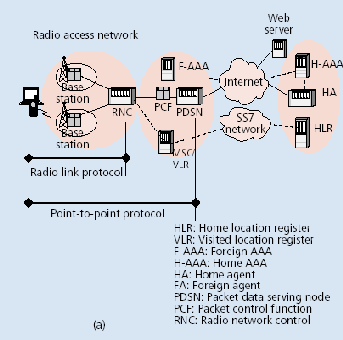
ISSN 2229-5518
11. Basic Wireless Scenario
• Chain of 5 nodes, spaced 200m apart
• Use DSDV routing
• FTP transfer from one end to the other
Want to measure the throughput

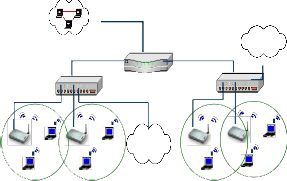
9. Architecture of WLAN
Internet
LAN
12. Options
• # ===============
# Define options
# ===============
set val(chan) Channel/WirelessChannel ;#
channel type
set val(prop) Propagation/TwoRayGround ;#
Hub/Switch
10. Workflow
Router
LAN
Hub/Switch
radio-propagation model
set val(ant) Antenna/OmniAntenna ;# Antenna type
set val(ll) LL ;# Link layer type set val(ifq) Queue/DropTail/PriQueue ;# Interface queue type
set val(ifqlen) 50 ;# max packet in
ifq
set val(netif) Phy/WirelessPhy ;# network interface type
set val(mac) Mac/802_11 ;# MAC
type
1) (Optional) Create custom ns2 object.
2) Create TCL scenario file.
3) Run the scenario to produce a trace file.
4) Process the trace file to get results.
set val(rp) DSDV ;# ad-hoc routing protocol
set val(nn) 5 ;# number of
mobilenodes
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 974
ISSN 2229-5518
13. Set up Simulator
• # Create simulator
set ns_ [new Simulator]
# Set up trace file
$ns_ use-newtrace
set tracefd [open simple.tr w]
$ns_ trace-all $tracefd
# Create the "general operations director"
# Used internally by MAC layer: must create!
create-god $val(nn)
# Create and configure topography (used for mobile scenarios)
set topo [new Topography]
# 1000x1000m terrain
$topo load_flatgrid 1000 1000
14. Configure Nodes
• $ns_ node-config -adhocRouting $val(rp) \
-llType $val(ll) \
-macType $val(mac) \
-ifqType $val(ifq) \
-ifqLen $val(ifqlen) \
-antType $val(ant) \
-propType $val(prop) \
-phyType $val(netif) \
-channel [new $val(chan)] \
-topoInstance $topo \
-agentTrace ON \
-routerTrace ON \
-macTrace OFF \
-movementTrace OFF
15. Create Nodes
• for {set i 0} {$i < $val(nn) } {incr i} {
set node_($i) [$ns_ node]
$node_($i) random-motion 0 ;#
disable random motion
$node_($i) set X_ 0.0
$node_($i) set Y_ 0.0
$node_($i) set Z_ 0.0
}
$node_(0) set X_ 0.0
$node_(1) set X_ 200.0
$node_(2) set X_ 400.0
$node_(3) set X_ 600.0
$node_(4) set X_ 800.0
16. Source and Destination
• # 1500 - 20 byte IP header - 40 byte TCP header =
1440 bytes
Agent/TCP set packetSize_ 1440 ;# This size
EXCLUDES the TCP header
set agent [new Agent/TCP]
set app [new Application/FTP]
set sink [new Agent/TCPSink]
$app attach-agent $agent
$ns_ attach-agent $node_(0) $agent
$ns_ attach-agent $node_(4) $sink
$ns_ connect $agent $sink
17. Run It
• # 120 seconds of running the simulation time
$ns_ at 0.0 "$app start"
$ns_ at 120.0 "$ns_ halt"
$ns_ run
$ns_ flush-trace close $tracefd
18. Trace File
s -t 0.000000000 -Hs 0 -Hd -2 -Ni 0 -Nx 0.00 -Ny
0.00 -Nz 0.00 -Ne -1.000000 -Nl AGT …
r -t 0.000000000 -Hs 0 -Hd -2 -Ni 0 -Nx 0.00 -Ny
0.00 -Nz 0.00 -Ne -1.000000 -Nl RTR …
Each line represents a message being transferred
• Common fields:
– Event type (s = send, r = received, d =
drop)
– Time stamp
– Source and destination
– XYZ co-ordinates of the node
– Network layer (AGT = agent, RTR =
router, …)
– … many many others
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 3, March-2014 975
ISSN 2229-5518
19. Results
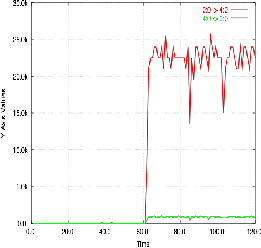
20. References
1) http://electronics.howstuffworks.com/cell- phone.htm
2) Hierarchical Mobile IPv6 mobility management (HMIPv6). Available at: http://www.ietf.org/internet-drafts/draft-ietf- mobileip-hmipv6-07.txt
3) Meng Shiun Pan, “4G Networks”
IJSER © 2014 http://www.ijser.org




