International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 11
ISSN 2229-5518
Software Security Issues: Requirement
Perspectives
Nikhat Parveen, Md. Rizwan Beg, M. H. Khan
Abstract— W ith the fast growing of software development life cycle, software engineering under a huge pressure to deliver the business requirements without paying too much attention to the security issues that the software might encountered. Many applications are outsourced too where the application development lacks strong integration of software security. For this reason security issues becomes a problem for the growth of a business and availability of requirement by its customers. Therefore, security should be tightly bound during the software development life cycle, right from the beginning. This paper discusses 21 issues related to security with respective to requirement that can eliminate vulnerabilities at the early development of life cycle. By keeping these issues at back of mind, working people in the area of software security can able to build more secure software and also the goals of security can easily be identified..
Index Terms— Software security, software development life cycle, security requirement issues, confidentiality, integrity and availability.
1 INTRODUCTION
—————————— ——————————
HE most important question arises related to security that “What makes secure software different?” Many research- ers realize that security is an innate property of the soft-
ware that has to be built in. Most of application lacks security today. The traditional practices are even no more effective for developing secure applications. The IT services companies are also improving their SDLC with the security at the very early stages. The current scenario is that the application demand tight software security embedded inside to prevent hackers getting in, due to this reason addressing security earlier in the lifecycle will help to mitigate the risks of application security attacks.
Maintaining a high level of security is not so simple, to en- dorse it the security issues has to be taken under higher priori- ty. Unlike functional requirement, non-functional requirement of application, security and its performance are always given lower priority. If the importance of these non functional fac- tors fails it will directly loss the customer value and their faith. If the researchers and developers tries to identify and analyze the reason behind the cause of security breach, they generally put blame entirely on virus attack, denial of service, spam mail etc. If we analyze from the depth of our knowledge we will found that the facts of the most important factors in software security breach, is, bad software which is actually behind eve- ry security problem and malicious attack. By identifying and targeting each individual security threats and providing solu- tion for those attacks and if we also put focus on the security aspect of software, we surely can build a more robust and reli- able system in totality.
Since the researchers and developers have done significant work in the field of integrating security throughout the soft- ware development life cycle, ‘right from the beginning’, still a major portion of work needs to be carried out in order to made software more secure and reliable. In this paper we intend to propose twenty one security issues which if practically ap- plied from the very beginning of software development life cycle i.e., from requirement analysis phase, it will definitely contribute in secure and reliable development of software. The
paper is organized as follows: in section II ‘Software Security’
is defined, and, ‘Security Issues’ is listed, section III describes
‘From Security Issues to Security Requirements and section IV
focus on’ Impact of Security Issues in Design, Implementation
and Deployment of software, with conclusion.
2 SOFTWARE SECURITY
Software security is an approach which protects from risk and maintains security failures in order to increase system reliabil- ity [1]. The main objective of software security is to have knowledge about the attacker and to foresee attacker’s motive and perception. Developing secured software is not an ad- vantage but it has become a necessity for software organiza- tion. Traditionally, software development is thought of as building software that works under normal conditions. But when the security aspect is clubbed with building software, the designer and developer focal point becomes attacker's per- spective and ‘how they can become a threat to the software’. Software security can be thought of as building software which performs under intentional and unintentional malicious attack [2]. The software security should exhibit ability to de- fend itself and the system from the attacker’s exploitation and misuse of software security loop holes. Software with build-in security should reflect features like predictable execution, trustworthiness, conformance, attack resistant, attack tolerant and attack resilient.
Security should begin at the requirement level and it must cover all the characteristics that secure the process [3]. Security is the degree of resistance to, or protection from attack. In or- der to elicit security requirements one’s should have the knowledge regarding security issues. The most common is- sues are CIA (Confidentiality, Integrity and Availability) [4,5].
• C : Confidentiality is prevention of unauthorized disclosure of information.
• I : Integrity is prevention of unauthorized modification of
information.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 12
ISSN 2229-5518
• A : Availability is prevention of unauthorized withholding
of information.
Confidentiality ensures that only authorized user can access
regardless of where the information is kept and how it is ac-
cessed. This can be maintained by mechanism like access con-
trol, password, biometrics, encryption, privacy and ethics
whereas integrity is to safeguard the accuracy and complete- ness of information and processing methods from being changed intentionally, unintentionally, or accidentally. Integri- ty needs to be maintained for ensuring privacy, security and
reliability of data and information. The mechanism to main- tain integrity is configuration management and auditing. Simi- larly availability is to ensure access of information and related assets for authorized users whenever needed. Availability can also be maintained by mechanisms like data backup plan, dis- aster management or business continuity.
Still the researchers and developers found that there are vari- ous issues regarding security. The best way to spread software security knowledge is to trained software development staff on serious security issues. Researchers have done tremendous job in this direction but there are various issues that can be addresses. On the basis of literature review, the issues are proposed and listed below.
1. Access Control: selective restriction of access to a place or other resource
2. Accountability: responsibility to someone or for some activity.
3. Accuracy: the quality of being near to the true value
4. Assessment /Evaluation: The classification of some- one or something with respect to its worth.
5. Auditability: The ability to achieve accurate results.
6. Authorization: Permission to access a resource.
7. Availability: The quality of being at hand whenneed-
ed.
8. Awareness: A state of elementary or undifferentiated
consciousness.
9. Confidentiality: Discretion in keeping secret infor- mation.
10. Consistency: A harmonious uniformity or agreement among things or parts.
11. Error Classification: A wrong action attributable to bad judgment or ignorance or inattention. The act of distributing errors into classes or categories of the same type.
12. Excellence: The possessing good qualities in high de- gree.
13. Flexibility: The quality of being adaptable or variable.
14. Fortification: A defensive wall or other reinforcement
built to strengthen a place against attack.
15. Identification /Authentication: The act of identify fact
or reliable information.
16. Integrity: An undivided or unbroken completeness or
totality with nothing wanting.
17. Interoperability: The ability to exchange and use in- formation.
18. Non-Repudiation: Non refusal to acknowledge.
19. Prevention: The act of preventing.
20. Privacy: The state of being concealed or hidden.
21. Unambiguity: Clarity achieved by the avoidance of ambiguity.
By analyzing the above listed security issues, at the early stage of software development, it is found that this securi- ty issues will elicit the requirement of the software in bet- ter way and helps to improve the production of software security.
3 FROM SOFTWARE SECURITY ISSUES TO SECURITY
REQUIREMENTS
Security, like beauty, is in the eye of the beholder. The specific security requirement particularly is different for business pur- pose, selfie, user preferences and/or defense perspective. The TCSEC [6] Glossary defines security requirement as “the set of laws, rules, and practices that regulate how an organization manages, protects, and distributes sensitive information".
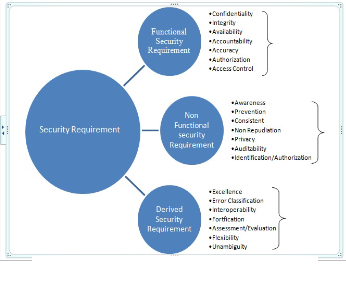
Security requirement can be classified into three groups: They are
Functional Security Requirement: It is a property of a system required to check condition or capability needed to control or limit the fulfillment of require- ments.
Non-functional Security Requirement: It is a property of a system required to ensure fulfillment of require- ments with respect to abuse or misuse conditions.
Derived Security Requirement: It is an implicit from
Functional/non-functional state of requirements.
A security requirement is a manifesto of a high- level organi- zational policy into the detailed requirement of specific sys- tem.
Fig 1 shows the relationship between classifications of Securi- ty Requirement and each group has its own security issues.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 13
ISSN 2229-5518
Fig 1 Software Security Requirement Issues
During development of software, developers must review the above listed issues in order to reduce vulnerabilities in the system. If the software engineers have these issues at the back of their minds during eliciting requirement for software de- velopment, it will certainly reduce the re-work for the devel- oper and improve the quality of the software product. The issues are described in detail from requirement perspectives.
1. Issue related to Access Control: It provides a form of au- thenticated user accesses only what they are authorized for [7]. This issue suggests that accesses to resources and ser- vices should be permission based. If the authenticated user is permitted/allowed to access resources and services then these permitted users should not be denied access to that services that they are legitimately expect to received. To produce secure software, it is mandatory to implement ac- cess control at requirement perspective.
2. Issue related to Accountability: Accountability is a func-
tional requirement that plays a vital role for maintaining number of logs for any task/ activities or action performed to accomplish a work in order to maintain security of pre- vention [8]. It involves tracking of activities of processes and maintains log details. Security can be maintained through audit transactions which help to determine the at- tacker or source of attack if occurred in software [9, 10].
3. Issue related to Accuracy: For any secured and reliable
software system, it is necessary to produce accurate re-
quirement for the system [3]. The issues relate that the
software development team should perform various activi-
ties such as scenarios, interviews, etc. in order to produce correct and accurate requirement for the software. Accura- cy can also be considered in terms quality factors such as speed, time.
4. Issue related to Assessment/Evaluation: Assessment is an
inherent classification that can be applied on process to get a quality software product. These issues suggest that each and every process should be classified in terms of require- ment which ensures that necessary security controls are in-
tegrated during requirement, design and implementation of a software product [23].if a assessment of a product is done properly it means consistency is maintained which means quality a subset of security. Assessment or evalua- tion if done considering the current security environment can help the software developer to analyze and measure the level of security implementation in their software product versus industry standards and best practices [12].
5. Issue related to Auditability: Auditing in security is a fea- ture to achieve accurate result. This issue suggests that Auditability must be implemented to judge the accounta- bility feature of software security and assist in redesign a full proof security policy and procedures for implementing a secure software system [3]. It helps the security auditor to thoroughly understand the flow of information and devel- op a plan for properly securing the system.
6. Issue related to Authorization: It is a process for assessing the security of a system by verifying the specified opera- tion performed by authenticated person. Authorization can
be implemented through access control where access is au- thorized. [11].
7. Issue related to Availability: It is a property for ready-to- service in corrective manner [13]. It needs to be a security goal as the loss of availability is referred to as “denial-of-
services”. This issue states that a balanced approach needs to be maintained between security and availability of re- quirement that should be highly secure and available all time. By maintaining availability the system is responsible for delivering; storing and processing information are ac- cessible when needed.
8. Issue related to Awareness: The issue of awareness in re- quirements of software security requires more adequate re- search treatment. Requirements as expressions of interests, goals and needs in software development are rarely physi- cally located [14]. This issue relate with constant acquisi- tion of new information and updation of existing knowledge related to security aspect for development of software. This can be resolved by providing security awareness program for training software development team on critical software security issues [5, 6].
9. Issue related to Confidentiality: Prevention or protection against access of information by unauthorized person can be defined confidentiality. This issue suggests that confi- dentiality should be maintained by ensuring that infor- mation is not accessed by any unauthorized person [10]. It can be resolved by providing assurance that the infor- mation is shared only among authorized users [13].
10. Issue related to Consistency: Consistency is key feature
when evaluating security effectiveness and performance
for eliciting requirement of software. It is advisable for re-
quirement engineer to maintain consistent requirement
protocol or standards for securing the software [15, 16].
11. Issue related to Error Classification: Due to bad error han-
dling and lack of proper knowledge regarding errors, secu-
rity could not be maintained. Software developers and
software security practitioners should be concerned about
the various errors which create problems leading to soft-
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 14
ISSN 2229-5518
ware vulnerability. This issue suggests that the error should be categorized and classified according to the secu- rity rules. If the error perceived, it should be removed at the early stage of software development.
12. Issue related to Excellence: The possessing of good quali-
ties in high degree by any software refers to excellence.
This issue suggests that the security is a subset of quality.
Hence in order to achieve security in totality, the quality of
the software should be of highest standards [17].
13. Issue related to Flexibility: Flexibility in software security
can be defined in terms of quality of being adaptable or
variable when external changes occur. This issue suggests
that the various requirements concerning security should
not be rigid and must be flexible as required.
14. Issue related to Fortification: Integrity is an important in- gredient of software and it should be maintained through- out the software engineering process [13]. The issue sug- gests that the various process used in security engineering process should be secured in individuality and totality. On- ly the concerned individual should have access to the tech- nicalities of software security and for the rest it should be kept as secret.
15. Issue related to Identification/Authentication: The act of identifying fact or reliable information is termed as authen- tication. This issue suggests that the process of identifica- tion and authentication must be implemented to find legit- imate user who log on to a system with respect to the au- thorized access rights [18]. Authentication can be judge by various techniques which include use of passwords, bio- metric techniques, smart cards, certificates, etc.
16. Issue related to Integrity: In terms of software security, integrity is concerned with securities that prevent unau- thorized modification of information. Integrity should be maintained by ensuring information that cannot be altered by unauthorized person [10, 13]. Integrity of information provides an assurance that the data is authentic and com- plete.
17. Issue related to Interoperability: The ability to exchange
and use information is the era of globalization. Most soft-
ware is platform independent which provides interopera-
bility. It means that software that able to exchange infor- mation directly infect the security of the software [19]. Hence this issue suggests that if one or more software are interacting together then all the software involved in the communication must be secured.
18. Issue related to Non-Repudiation: In general the non re- fusal of any transaction is termed as non-repudiation. Any parties involved in a transaction cannot repudiate the va- lidity of transaction [20]. The objective of non-repudiation is to validate the transaction that is committed between two parties. Non-repudiation can be obtained through digi- tal signatures.
19. Issue related to Prevention: “Prevention is better than
cure”, a well known quotation, the developer must keep
this in mind and build the software with security in such a
way that when threat attack on software internally or ex-
ternally can be safeguard and protect from infection. Secu-
rity in the software should be synchronized to prevent any kind of threat from internal or external source rather than cure it.
20. Issue related to Privacy: Privacy can be seen as an art of being concealed or isolated from the presence or view of others [8]. Security and privacy issues now become major concerns in the requirement of software systems. The issue suggests that privacy can ensures individual’s right to control what information is collected, how it is used, who has used it, who maintains it, and what purpose it is used for [21]. Privacy protection as a tool of security can be im- plemented by designing and enforcing sound privacy and data protection laws and technologies [22].
21. Issue related to Unambiguity: Unambiguity always been
issues for software security, this issue suggests that the im- plementation of software security will achieve clarity, by avoidance of ambiguity.
The above listed 21 issues related to requirement perspective suggest that if these issues will be improved properly at the
early stage of software development, it will certainly reduce the re-work of developer and also helps to meet the security goals of the software.
4 Impact of Security Issues in Design, Implementation and Deployment of software
Security should be consider from the requirement phase, all the personnel from requirement engineers to software devel- opers must be aware of most recent software security issues, especially functional requirement security issues and non- functional security issues. The awareness of security issues should be more technical and in-depth for SDLC team mem- bers.
In order to achieve the security goals for the software, the se- curity will be tightly bound from requirement phase to de- ployment phase of software development life cycle. If the se- curity issues are properly followed and removed by require- ment engineer, it will help the system software designer to design more secure software and the programmer will be able to produce secure code. Following the above mentioned secu- rity issues, the implementation engineer will able to configure and run software more securely. The deployment engineer will able to deploy more secured software in open environ- ment.
5 CONCLUSION
Security is not something that is addressed at the end of the product lifecycle nor is it a specific objective that occurs dur- ing project execution. Security must be everywhere. Tradition- ally, security issues are first considered during the Design phase of the software development life cycle once the software requirement specification has been frozen. The paper tried to produce issues related to securities and forced requirement engineer to address security at requirement phase so that the
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 15
ISSN 2229-5518
vulnerabilities can be mitigate at the early development of software. Each security issues must be resolved so that the security must be tightly bound from the beginning to the de- ployment of secure software.
REFERENCES
[1] Chandra, S, and R A Khan. "Software Security: A Quantitative Approach." CSI Communication: 19-23. August 2010.
[2] Julia H. Allen, Sean Barnum, Robert J. Ellison, Gary McGraw, Nancy R. Mead:
Software Security Engineering: A Guide for Project Managers, Addison Wes- ley Professional, 2008, pp 6-8.
[3] Parveen, Nikhat, Rizwan Beg, and M. H. Khan. "Integrating Security and Usability at Requirement Specification Process." International Journal of Computer Trends and Technology (IJCTT) 10: 236-240.
[4] G.McGraw, “Software Assurance for Security”,IEEE Computer 32(4), pp. 103-
105(April,1999).
[5] http://searchwarp.com/swa268042.html
[6] Sterne, Daniel F. "On the Buzzword “Security Policy”." IEEE. (1991)
[7] Keromytis, Angelos D, and Jonathan M. Smith. "Requirements for Scalable Access Control and Security Management Architectures." ACM Transactions on Internet Technologies, Vol. 7.No.4 (2007).
[8] Breaux, Travis D., Annie I. Anton, and Eugene H Spafford. "A distributed requirements management framework for legal compliance and accountabil- ity."ScienceDirect Computers &Society. I.I0 (2008):
[9] "SECURITY REQUIREMENTS." National Information Assurance Training and Education Center. IRI, Pocatello, Idaho. Web. 28 May 2014.
[10] "Security Requirements Engineering: A Framework for Representation and
Analysis." IEEE Computer Society. 34.1 (2008): 133-153. [11] "Authorization." From Wikipedia to encyclopedia. 2014.
[12] "Common Criteria for Information Technology Security Evalua- tion."http://www.commoncriteriaportal.org/. Common Criteria, Web. 28
May 2014.
[13] Avizienis, Algirdas, Jean-Claude Laprie,, et al. "Basic Concepts and Taxono- my of Dependable and Secure Computing." IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING,. 1.1 (2004)
[14] Damian,, Daniela, and Brian Corrie. "Awareness meets requirements man- agement: awareness needs in global software development."
[15] HEITMEYER, CONSTANCE L., RALPH D JEFFORDS, and BRUCE G LABAW. "Automated Consistency Checking of Requirements Specifica- tions." ACM Transactions on Software Engineering and Methodology,. 5.3 (1996): 231-261.
[16] Manzoor,, Umar, Kiran Ijaz, Wajiha Shamim,, and Arshad Ali Shahid. "Ensur- ing Data Security & Consistency in FTIMA - A Fault Tolerant Infrastructure for Mobile Agents." World Academy of Science, Engineering and Technology International Journal of Electrical, Electronic Science and Engineering. 1.3 (2007): 465-470.
[17] http://en.wikipedia.org/wiki/Excellence.
[18] "Web Authentication Security." SANS Institute InfoSec Reading Room. 06 june 2003. Reading.
[19] Headayetullah, Md, and G.K. Pradhan. "INTEROPERABILITY, TRUST BASED INFORMATION SHARING PROTOCOL AND SECURITY: DIGI- TAL GOVERNMENT KEY ISSUES." International Journal of Computer Sci- ence and Information Technology. 2.3 (2010):
[20] Tsai, Chii-Ren. "Non-Repudiation In Practice."
[21] Breaux, Travis D., and Annie I Anton. "Analyzing Regulatory Rules for Priva- cy and Security Requirements." IEEE TRANSACTIONS ON SOFTWARE
ENGINEERING,. 34.1 (2008): 5-20.
[22] Liu, Lin, Eric Yu , and John Mylopoulos. "Security and Privacy Requirements
Analysis within a Social Setting."
[23] "Information Technology Security Assessment." Assessment. 2013.
IJSER © 2014 http://www.ijser.org
