International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 2132
ISSN 2229-5518
Sharing of Patient confidential data using ECG
steganography
V.Sankari [1], K. Nandhini [2]
Abstract— In accordance with Health Insurance Portability and Accountability Act (HIPAA) the patient’s privacy and security is important in the protection of healthcare privacy. At the same time, the number of aging population are growing significantly. Point-Of-care (PoC) applications in hospitals are used widely around the world. The Security Regulations are implemented to provide data integrity, confidentiality, and availability. Therefore, patients ECG signal and other physiological readings such as temperature, blood pressure, glucose reading, position, etc., are collected at home by using Body Sensor Networks (BSNs) .It will be transmitted and diagnosed by remote patient monitoring systems (RPM). At the same cost ,patient confidentiality is protected against intruders while data traverse in open network and stored in hospital servers. In this project, to fulfill HIPAA act, a Discrete Wavelet Transform based steganography technique has been proposed. DWT technique allows ECG signal to put out of sight the patient confidential data and thus guarantees the patient’s privacy and confidentiality. In addition the following mechanism were incorporated in this project: (1) encryption and decryption for data confidentiality and integrity (2) a three-tier security for data (3) ECG based Steganography to exchange data. A degree of high privacy is guaranteed for patient and simultaneously the Stego ECG remains diagnosable. Our scheme also ensures security, scalability, and efficiency.
—————————— ——————————
IJSER
n accord with HIPAA regulations, the patients confidential
information sent through the public network should be
protected and secure. Patient privacy is important that a
patient can control who will use his/her confidential health
information, such as name, address, telephone number, and
Medicare number and who can access patient’s data and who
cannot. At the same time number of aging population is in-
creasing significantly, monitoring patients at their home can
reduce the increasing traffic at hospitals and medical centres.
The primary goal is to provide confidentiality, integrity, and
availability. Steganography is a branch of cryptography that
involves hiding information “in plain sight”. Hiding a mes- sage reduces the chance of a message being detected. The main aim is to hide patient's confidential data and other phys- iological information in ECG signal. ECG signal is used be-
cause the size of ECG is large compared to other medical im- ages. Therefore, patients ECG signal and other physiological readings such as temperature, blood pressure, glucose read- ing, position, etc., are collected at homes by using Body Sensor Networks (BSNs) will be transmitted and diagnosed by re- mote patient monitoring systems. At the same cost that the patient confidentiality is protected against intruders while data traverse in open network and stored in hospital servers.
This technique allow ECG to put out of sight the patient confidential data and thus guarantees the patient’s privacy and confidentiality. The aim is to show that both the Host ECG and stego ECG signals can be used for diagnoses and the difference would be undetectable.
The work of this project is motivated by investigations from the above and similar research findings. Our first objec- tive is to save patient confidential data from harm by using steganography method. From the proposed model, we then formulate new steganography technique using ECG and in- troduce their respective algorithms, which are fast and
scalable, but are also capable of providing high-quality and
consistent performance.
Information Security is to prevent the unauthorized access,
misuse of data, content modification, or denial of access,
facts(data), etc., The primary goal is to provide confidentiality, integrity and availability. The good security in reality is com- pile of these solutions. The solid physical security is essential to guard substantial assets like papers, records. Communica- tion security (COMS) is essential to guard information in transmit. Computer security (COMPS) is essential to control access over others computer systems, and Network security (NET) is vital to secure the local area network. Together, these concepts provide Information security (INFOS). You guard these things against threats, vulnearbility.
Among these, an important sub discipline of hiding infor- mation is steganography. Information hiding is recent tech- niques have become important in a number of applications. It is important that communication must be secured by encrypt- ing the secret messages. While cryptography protect the con- tent of the messages, steganography concealing the secret message. Usually means hiding information in other infor- mation.
The main target of steganography is to put out of sight the secret message in the other cover media so that nonentity can see that and both participants are converse in secret way.
By combining the techniques of steganography and the other techniques, information security has improved noticeably. Steganography is used as copyright, averting e-document forging, ensure data confidentiality. Such carriers are text, document, audio, image, video, 3D models recording, etc., Hiding a message reduces the chance of a message being de- tected. If the message is also encrypted then it provides anoth- er layer of protection.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 2133
ISSN 2229-5518
Steganography are of two types
1) Fragile: In this type of steganography, if the file is mod- ified then the embedded information is destroyed.
2) Robust: This steganography, embed information into a media which cannot be simply destroyed.
Goals of Steganography are capacity and security.
Several researchers have been proposed to secure patient confidential data. There are techniques that are based on en- cryption and cryptographic algorithms. These techniques are used to secure data during the communication and storage. As a result, the final data will be stored in encrypted format [2], [4], [16], [17]. The limitations of using encryption based tech- niques is its large computational overhead. Therefore, encryp- tion based methods are not suitable in resource-constrained mobile environment.
Rest of the paper is organized as follows. Section II briefly discusses the related works in this area. In section III , the basic methodology, system design, the embedding process and the extraction process is discussed. Section IV shows the result of the project. Finally, section V concludes the paper.
tion. In this project a signal called low frequency chirp is used to embed watermark in which patient's data taken as 15 digit code. The watermarking scheme used here is the blind recov- ery of the watermark is used at the receiver end and the em- bedded watermark can be removed. Original size of host sig- nal increased after watermarking. Not more secure compared to other techniques. Same as normal image steganography. The watermarking process has no encryption key method.
K.Zheng and Xu-Qian [6] shows that, reversible water- marking algorithm has developed for electrocardiogram (ECG) signal based on wavelet transforms. This method is based on applying wavelet transform on the original ECG sig- nal to detect QRS complex. Next, the non QRS coefficients are selected, are shifted one bit to the left and the watermark is embedded. In electrocardiogram signal, the energy is concen- trated in QRS complex waves. So the selection of wavelet coef- ficients for hiding should avoid making QRS complex waves distort obviously. The algorithm hides bits in the expansion of selected coefficients of high frequency sub- band of Haar wavelet transform based on lifting scheme. The performance has been evaluated in terms of ECG signal distortion and em- bedding capacity. This method has low capacity since it is shifting one bit. So, one bit can be stored for each ECG sample
value. Finally, this algorithm is for normal ECG signal. How- ever, for abnormal signal in which QRS complex cannot be
Many approaches have been established to secure patient con-
fidential data [2], [4], [5], [16], [17]. However, these approaches
are [15], [7], [6], [8] proposed to secure data based on ste-
ganography techniques to hide secret information inside med-
ical images.
Ibaida and Khalil [15] shows that, it embed confidential da- ta of patients into a position which is called special range numbers, of the ECG host signal which is in digital that will provide minimum distortion to ECG, and any secret infor- mation embedded is completely extractable. In this, that there are many possible SRN create it tremendously difficult for attackers to recognize the locations of private bits. This exper- iments display that percentage residual difference (PRD) of watermarked ECGs for normal and abnormal ECG segments. This method has high computational overhead. This algo- rithm is developed for normal ECG signal of the patient but not for abnormal ECG signals such as Ventricular tachycardia, fibrillation, etc., Moreover, the capacity of this algorithm is low. No encryption key is involved in its watermarking pro- cess.
S.Kaur, R. Signghal [7] work shows that, each ECG sample is quantized using 10 bits, and is divided into segments. Pa- tient ID is used in the modulation process of the signal. The resulting watermarked signal is 11 bits per sample. The final signal consists of 16 bits per sample, with 11 bits for water- marked ECG and 5 bits for the factor and patient Identifica-
detected.
H. Danyali and H. Golpira [8] proposes a technique based on histogram shifting in wavelet transform domain, in which blind reversible watermarking approach for medical images are proposed. In their work MRI medical image is used as host data. The watermark data is embeded into a subband regions which is in high frequency of the transformed image. Two thresholds were used based on the watermarking. One in the initial part and the other in the ending part of the histogram. The histogram located between the two thresholds remains unchanged. A two dimensional wavelet transform is applied to the image, to extract the watermarked data in the cover me- dia. Therefore the hidden watermarked data are extracted. This algorithm performs well for MRI images but not for ECG host signals. Moreover, the capacity of this algorithms is low.
The sender side of the proposed ECG steganography method consist of three stages. This proposed technique has authentication stage that prevent unauthorized users from extracting the hidden data and it is designed to secure the information of patients hiding with minimal distortion of the host ECG signal.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 2134
ISSN 2229-5518
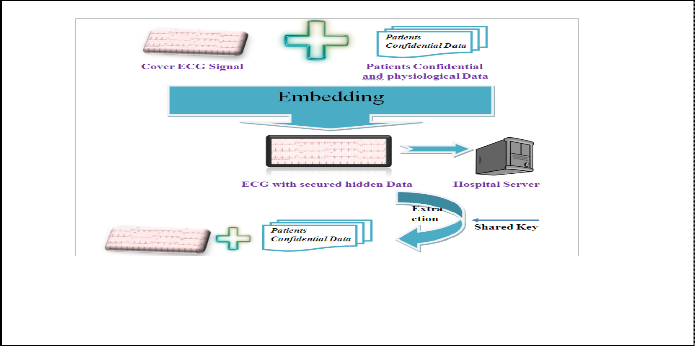
Fig. 1. Scenario of ECG Steganography that embed patient confidential data in ECG signal to get ECG with secured data and extraction process.

from modify or reading the content of data that is encrypt-
IJSER
Electrocardiogram Tracing of heart’s electrical activity, the rhythm of the heart in term of beats per minute (bpm).
10 electrodes in total are placed on the patient. 6 are chest
electrodes called V1-V6. 4 are limb electrodes as right arm, left arm, right leg, left. The format of ECG signal consist of Q wave, R wave, S wave, the QRS complex, P and T waves. The signal normally begins with P wave that following the QRS wave or QRS complex. Then it was followed by the corresponding T and U waves. A U-wave may be present and lies after the T-wave. The QRS complex is the most im- portant component in the ECG signal because of its high amplitude and speared nature, it process more electrical activity, it indicates depolarization of the ventricles which have superior muscles. The subsequent processing of the ECG signal such as calculation of the RR interval, P and T waves for ventricular fibrillation and tachycardia, etc are estimated by detection of QRS complex. The two types of ECG signal used and generated in this project are as fol- lows 1) Normal Signal and 2) Tachycardia(abnormal). A heart rate above 150 bpm called Tachycardia.
For Security purpose, the patient’s data are first encrypted using Public key cryptosystem. The patient confidential information is encrypted in such a way that prevent unau- thorized persons who does not have the shared key from accessing confidential data. Encryption is the initial security solution for communicating in open network Therefore, encryption itself does not provide security. Encryption does not save data from hacking but it prevents the intruder
ed. It may protect valuable data that is in stored encrypting
files.
In this stage to ensure high data security, the embedding operation is performed which hides data in the wavelet coefficients and propose high data security. In this stage a discrete wavelet transform operation is performed. Then the stego ECG signal with patients confidential information is further encrypted for strong and high security purpose.
To extract the secret data from the stego ECG signal, the following information is required at the receiver side. The shared key value for decrypting data. Shared key for de- crypting digital stego ECG.
This is necessary that the encryption algorithm should run in the reverse order. It requires the cipher text of pa- tient data and the secret shared key and produces the orig- inal data.
In this stage the receiver should undergo the reverse
operaion to retrieve patients confidential information and
the original ECG signal. They should have the shared key
for decrypting the digital stego ECG signal and shared key for decrypting information. The security of this system is based mainly on the idea of having secure shared key be- tween the sender and the receiver entities. Any changes in any key value in the encryption and decryption process will not allow to extract the data. Using the shared key, the extraction operation starts extracting the secret bits in the correct order according to the sequence rows. The extracted secret bits are decrypted using the same shared key.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 2135
ISSN 2229-5518
![]()
ALGORITHM
1: SC ecg : the host ecg signal (cover)
2: SS : calculate the size of ecg signal
3: SD : read the secret data
4: b bits : the secret bits
5: bs : size of secret bits
6: k : encryption key (asymmetric)
7: ks : size of the key
8: ESD : encrypted secret data of pateint
9: ESD S D + k
10: convert the encrypted data into binary so as to obtain indi- vidual bits of the data.
11: B(ESD) : binary digits of ESD
12: ASC : analog ecg signal
13: DSC : digital ecg signal
14: DSC SC + A/D
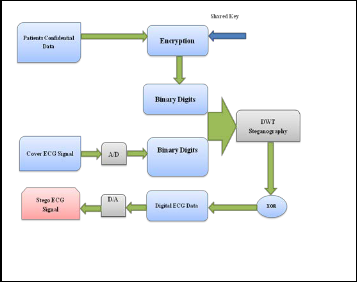
Fig. 2. Block Diagram of proposed steganography which includes encryp- tion, dwt, decryption.
This scheme has implemented and conducted some tests. In the implementation, the patients confidential information such
IJSEas name, date ofRbirth, age, address, Medicare number, phone
15: convert the DSC into binary notation so as to obtain indi-
vidual bits of the signal.
16: Prepare the secret data to embed
17: Decompose the SC using DWT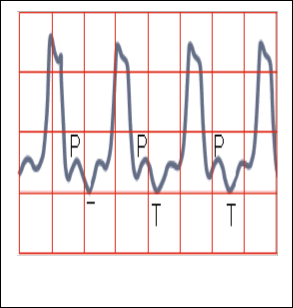
18: secg embed (bits (b) in LCF of SC )
19: Repeat step 18 until all the data bits are embedded
20: to increase security encrypt the secg using xor
21: end
22: ASC SC + D/A
23: ECG apply inverse dwt and decryption (recomposition)![]()
24: Finally the secret data can be obtained by converting the extracted binary to data bit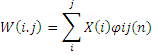
number, and other physiological readings such as patient loca- tion, temperature, glucose, haemoglobin, blood pressure are not sent to the receiver as a separate message, but, instead, transmitted along with the ECG signal as cover or host medi- um to hide the above specified datas. Specifically, this scheme hides patient personal data and physiological data in the ECG signal.
Fig. 3. Sample ECG Signal
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 2136
ISSN 2229-5518
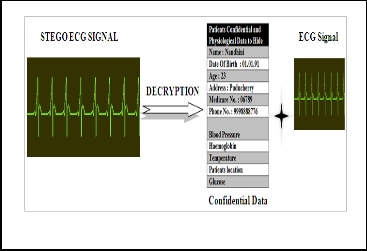
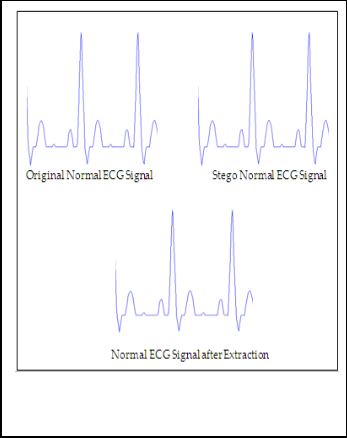
Fig. 4. Embedding patient confidential information in the ECG signal

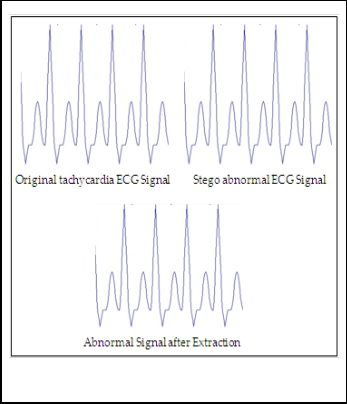
Fig.7. Normal ECG Signal before applying the steganography opera- tion and after the steganogarphy operation as well as after extracting the secret data.
Fig. 5. Decoding process extracting patient data from the ECG signal
Fig. 6. Generated original normal ECG signal using MATBAB
Fig.8. Abnormal ECG Signal before the steganography operation and after steganogarphy operation as well as after extraction.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 2137
ISSN 2229-5518
In this project, a novel steganography algorithm is proposed to hide patient confidential and physiological data in the ECG signal using Discrete Wavelet Transform. The HIPAA regula- tion comply in this paper i.e., information sent through the public network will be protected and secured. ECG signal hides the corresponding patient confidential data and thus guarantees the patient’s privacy and confidentiality. The proposed algorithm provide significantly improved security, efficiency and performance. Three tier of security is provided. Any doctor can see the Stego ECG signal and only authorized doctors can extract the secret information and have access to the confidential patient information as well as other readings stored in the host ECG signal. The distortion will be less. The difference will be undetectable in Stego ECG signal, and both the Stego ECG and Host ECG can be used for diagnoses.
[1] Ayman Ibaida, Ibrahim Khalil “Wavelet Based ECG Steganography for Protecting Patient Confidential Information in Point-of-Care Sys-
tems” IEEE Transactions On Biomedical Engineering.
[8] H. Golpira and H. Danyali, “Reversible blind watermarking for med- ical images based on wavelet histogram shifting,” in IEEE Interna- tional Symposium on Signal Processing and Information Technology (ISSPIT), 2009. IEEE, 2010, pp. 31–36.
[9] Eric Maiwald “Fundamentals of Network Security” Himal Impres-
sion Press, 2008.
[10] Arvind Kumar, Km. Pooja “Steganography- A Data Hiding Tech- nique” International Journal of Computer Applications (0975 – 8887) Volume 9– No.7, November 2010.
[11] Fabien A. P. Petitcolas, Ross J. Anderson and Markus G. Kuhn, “In-
formation Hiding A Survey”, Proceedings of the IEEE, special issue on protection of multimedia content, 87(7):1062{1078, July 1999.
[12] Shashikala Channalli et al, “Steganography An Art of Hiding Data”,
International Journal on Computer Science and Engineering Vol.1(3),
2009, 137-141 137.
[13] Provos, N. & Honeyman, P., “Hide and Seek: An introduction to steganography”, IEEE Security and Privacy Journal, 2003
[14] Pradeep Kumar Jaisal, Dr. Sushil Kumar, Dr. S.P Shukla, “A Survey of Electrocardiogram Data Capturing System using Digital Image Processing: A Review”, IJCST Vol. 3, Iss ue 1, Jan. - March 2012 ISSN
: 0976-8491 (Online) | ISSN : 2229-4333 (Print)
[15] Ibaida, A. ; Sch. of Comput. Sci. & IT, RMIT Univ., Melbourne, VIC,
Australia ; Khalil, I. Al-Shammary, D. , “Embedding patients confidential data in ECG signal for healthcare information systems”,
Engineering in Medicine and Biology Society (EMBC),
2010 Annual International Conference of the IEEE.
IJSER
[2] W. Lee and C. Lee, “A cryptographic key management solution for
hipaa privacy/security regulations,” IEEE Transactions on Infor- mation Technology in Biomedicine,, vol. 12, no. 1, pp. 34–41, 2008.
[3] K. Malasri and L. Wang, “Addressing security in medical sensor
networks,” in Proceedings of the 1st ACM SIGMOBILE international workshop on Systems and networking support for healthcare and as- sisted living environments. ACM, 2007, p. 12.
[4] H. Wang, D. Peng, W. Wang, H. Sharif, H. Chen, and A.
Khoynezhad, “Resource-aware secure ecg healthcare monitoring through body sensor networks,” Wireless Communications, IEEE, vol. 17, no. 1, pp. 12–19, 2010.
[5] M. Li, S. Yu, Y. Zheng, K. Ren, and W. Lou, “Scalable and secure sharing of personal health records in cloud computing using at- tributebased encryption,” Parallel and Distributed Systems, IEEE Transactions on, vol. 24, no. 1, pp. 131–143, 2013.
[6] K. Zheng and X. Qian, “Reversible Data Hiding for Electrocardio- gram Signal Based on Wavelet Transforms,” in International Confer- ence on Computational Intelligence and Security, 2008. CIS’08, vol. 1,
2008.
[7] S. Kaur, R. Singhal, O. Farooq, and B. Ahuja, “Digital Watermarking of ECG Data for Secure Wireless Commuication,” in 2010 Interna-
tional Conference on Recent Trends in Information, Telecommunica- tion and Computing. IEEE, 2010, pp. 140–144.
[16] I. Maglogiannis, L. Kazatzopoulos, K. Delakouridis, and S.
Hadjiefthymiades, “Enabling location privacy and medical data en- cryption in patient telemonitoring systems,” IEEE Transactions on In- formation Technology in Biomedicine,, vol. 13, no. 6, pp. 946–954,
2009.
[17] F. Hu, M. Jiang, M. Wagner, and D. Dong, “Privacy-preserving tele- cardiology sensor networks: toward a low-cost portable wireless hardware/ software codesign,” IEEE Transactions on Information Technology in Biomedicine,, vol. 11, no. 6, pp. 619–627, 2007.
[18] Lisa M. Marvel, Member, IEEE, Charles G. Boncelet, “Spread Spec-
trum Image Steganography” Jr., Member, IEEE, and Charles T. Ret- ter, Member, IEEE.
[19] Ying Wang, Member, IEEE, and Pierre Moulin, Fellow, IEEE “Per- fectly Secure Steganography: Capacity, Error Exponents, and Code Constructions”, Transaction on Information theory, Vol. 54, No. 6, June 2008.
[20] Weiming Zhang, Shuozhong Wang, and Xinpeng Zhang, “Improving
Embedding Efficiency of Covering Codes for Applications in Ste- ganography”, Vol. 11, No. 8, August 2007
————————————————
• Ms. K. Nandhini received the B.Tech. degree in Information Technology
from Dr. Pauls Engineering College, Anna University, India, in 2012 and currently pursuing masters degree program in Computer Science and
Engineerng in Pondicherry University, India, PH-9943796831. E-mail: nandhini21b.e@gmail.com
IJSER © 2013 http://www.ijser.org