International Journal of Scientific and Engineering Research Volume 4, Issue 1, January 20123 1
ISSN 2229-5518
Session Initiation Protocol
Akbar Ali, Nehal Ahmad, Mohd Sharique Akhtar, Aditya Srivastava
Abstract The Session Initiation Protocol (SIP), developed by SIP working group specified by the Internet Engineering Task Force (IETF), peer-to-peer communication protocol to establish, manipulate, and tear down communication sessions at application layer. SIP covers all over the world’s organization because of its recent applications, thus allowing the implementation of a number of features using SIP, such as video conferencing, peer-to- peer application, instant messaging and voicemail, online gaming. SIP makes it possible to easily connect the various components of an overall communications system, rapidly deploy applications, reduce costs, and improves customer service and employee productivity by simplifying your organization’s communications architecture. The protocol is extensible that means developers can easily write custom applications for SIP to accommodate video and voice streaming, instant messaging and other emerging communications media and features. Using SIP, simple-to-develop and quick to deploy custom applications can be easily integrated into communications sessions. The SIP is a signaling protocol for initiating, managing and terminating sessions across packet networks. SIP sessions involve one or more participants and can use unicast or multicast communication. The SIP is text-encoded and highly extensible. SIP may be extended to accommodate features and services such as call control services, mobility, interoperability with existing telephony systems, and more. SIP is implemented in different wired and wireless networks, which has security issues.
—————————— ——————————
SIP has recently become the main signaling protocol for Internet applications, thus allowing the implementation of a number of features using SIP, such as video conferencing, online gaming, peer-to-peer application, instant messaging, presence services and voicemail. SIP also supports mobile applications, which are more flexible applications than others. SIP is implemented in different networks (wired and wireless), that is a part of security issues while implementing SIP. The Session Initiation Protocol is a part of VoIP that is responsible for the initiation setup for the connection. The purpose of this PM is to investigate how the Session Initiation Protocol works in the call set up phase and which kind of features that this protocol supports. Session Initiation Protocol could also be used in media connections. The idea behind this protocol was to make it look similar as when you using a regular phone, i.e. enter the number you would like to call, hear the phone ringing or a busy signal. The main difference according to a regular phone’s protocol is that when using the Internet as device for transporting the call, no actually circuit in the network is established. Determine the location of the target end point-SIP supports address resolution, name mapping, and call redirection. Determine the media capabilities of the target end point Via Session Description Protocol (SDP); SIP determines the “lowest level” of common services between the end points. Conferences are established using only the media capabilities that can be supported by all end points. Determine the availability of the target end point — if a call cannot be completed because the target end point is unavailable, SIP determines whether the called party is already on the phone or did not answer in the allotted number of rings. It then returns a message indicating why the target end point was unavailable. Establish a session between the originating and target end point If the call can be completed, SIP establishes a session between the end points.
SIP also supports mid-call changes, such as the addition of another end point to the conference or the changing of a media characteristic or codec. Handle the
transfer and termination of calls, SIP supports the transfer of calls from one end point to another. During a call transfer, SIP simply establishes a session between the transferee and a new end point (specified by the transferring party) and terminates the session between the transferee and the transferring party. At the end of a call, SIP terminates the sessions between all parties.
A SIP system has two basic components user agents and network servers.
User agents are the end point systems that participate directly in the communication network. A user agent contains two protocol, user agent client and user agent server. The user agent client is used to initiate a call, while the user agent server is used to response a request. The presence of both in a user agent enables point to point operations.
Network Server handles signaling associated with multiple calls providing name resolution and user location. The Network Server is of the following types that are Registrar Server, Redirect Server, Proxy Server and Presence Server.
Registrar Server Receives registration messages from endpoints regarding current user location and maps the SIP addresses with the physical location(s) in the domain where the endpoint is located. These mapping data are stored in a database, which can reside on the same machine or on a remote server. Using the REGISTER message to set the key also allows for more advanced key management, such as unregistering and setting validity time, as can be
IJSER © 2013
International Journal of Scientific and Engineering Research Volume 4, Issue 1, January 20123 2
ISSN 2229-5518

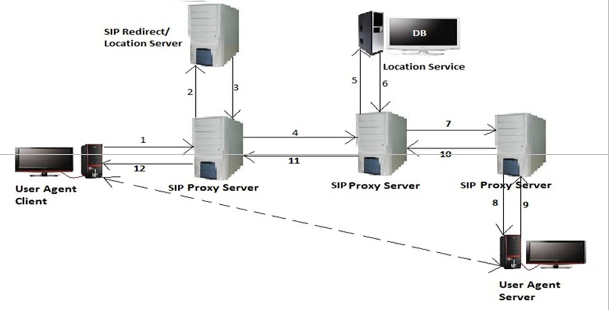
Fig:1. SIP Architechture
done with the location registration itself. This makes key management relatively easy, as a compromised private key easily can be invalidated by simply unregistering the association with the SIP registrar.
Redirect Server helps endpoints to find the desired address by redirecting them to try another server. Suppose a user is not in their home domains, Sessions need to be redirected to him. The redirect server maps a SIP request destined for user to the URI of device closest to user.
Proxy Server forwards the SIP messages to multiple proxy servers, creating a search tree, in order for the SIP messages to reach their destination. There are two different operating modes for these servers, stateless and stateful. In the stateless mode server forgets all the information once the request is sent while in the stateful server save previous routing information and is able to use it for improving the message transfer.
Presence Server accept, store and distribute presence information that allows users to see availability of people they want to contact. It has two distinct set of clients, Presentities and Watcher.
It provides presence information about themselves to the server to be stored and distributed, known as producers of information.
It receives presence information from server, known by consumers of information
1. UAC sends INVITE request to SIP Proxy Server
2. If SIP Proxy Server can’t find the UAS location,
forking process proceeds to the Redirect Server.
3. Redirect server returns the address of the next proxy
server.
4. Based on the receive address from the redirect server, the proxy server forks the request to the next SIP proxy server.
5. The proxy server consults the location server for the address of the next hop.
6. The location server returns the address of the next hop.
7. The proxy server forks the request to the next hop.
8. This time, the proxy knows the location of the called
party and forks the invitation request to User B.
9. Step 9-12.the acknowledgment message from User B
will be returned to User A using the same path as the
request message.
10. Step13 Once the call setup procedure is completed;
the session will be directly established between
UAC and UAS. For IP network, the voice/audio
stream can be carried over IP using RTP.
SIP works on request-response processes for initiate, maintain and tear down the communication among peer of devices. SIP is a lightweight protocol because it requires very few messages, called methods, for managing a session. A SIP message is either a request from a client to a server, or a
IJSER © 2013
International Journal of Scientific and Engineering Research Volume 4, Issue 1, January 20123 3
ISSN 2229-5518
response from a server to a client. A SIP request message begins with a request line, followed by header fields, and an optional message body. Similarly, a SIP response message begins with a status line, followed by header fields, and an optional message body. The request line and header field define the nature of the call in terms of services, addresses, and protocol features. The message body is independent of the SIP protocol and can have an arbitrary content.
3.1 Request messages
Request messages are messages send from client to server for inviting a call. Request processes have following methods.
INVITE: Invites for a call, changes call parameters (re- INVITE).
ACK: Confirmation of final response for INVITE. BYE: Terminates a call.
CANCEL: Terminate searches and “ringing”. OPTIONS: Queries the capabilities of the other side. REGISTER: Registers with the Location Service user’s location.
INFO: Sends mid-session information that does not modify the session state.
3.2 Response messages
Response messages are messages send from server back to the client. Response messages contain numeric response codes. The SIP response codes extend HTTP response codes. There are two types of responses.
4 MESSAGE TYPE
These responses are used by the server to indicate progress, but they do not terminate SIP transactions i.e. 1xx class.
Final responses terminate SIP transactions, and it has five categories i.e. 2xx, 3xx, 4xx, 5xx, 6xx classes.
SIP messages has following three parts-
Every SIP message begins with a Start Line. The Start Line conveys the message type (method type in requests, and response code in responses) and the protocol version. The Start Line may be either a Request-line (requests) or a response line (responses), The Request-line includes a Request URI, which indicates the user or service to which this request
is being addressed. The Status-line holds the numeric Status- code and its associated textual phrase.
SIP Header fields are used to convey message attributes and to modify message meaning. They are similar in syntax and semantics to HTTP header fields (in fact some headers are borrowed from HTTP) and thus always take the format. Headers can span multiple lines. Some SIP headers such as Via, Contact, Route and Request-Route can appear multiple times in a message or, alternatively, can take multiple comma separated values in a single header occurrence.
A message Body is used to describe the session to be initiated (for example, in a multimedia session this may include audio and video codec types, sampling rates), or alternatively it may be used to contain opaque textual or binary data of any type which relates in some way to the session. Message bodies can appear both in request and in response messages. SIP makes a clear distinction between signalling information, conveyed in the SIP Start Line and headers, and the session description information, which is outside the scope of SIP.
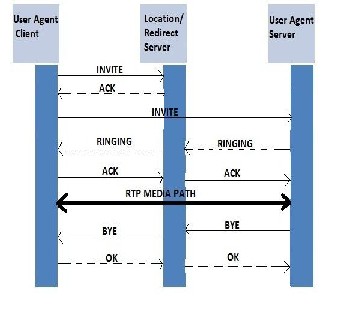
Fig.2: Call Setup Scenarios
The Figure 2 shows a basic SIP call setup scenario, using the messages INVITE , Re-INVITE, ACK, BYE, CANCEL, OPTIONS, REGISTER.
If a call is to be routed through a number of different Proxy servers Redirect server is used. When a caller UA sends an INVITE request to the redirect server, the redirect server
IJSER © 2013
International Journal of Scientific and Engineering Research Volume 4, Issue 1, January 20123 4
ISSN 2229-5518
contacts the location server to determine the path to the called party, and then the redirect server sends that information back to the caller. The caller then acknowledges receipt of the information. The caller then sends a request to the device indicated in the redirection information (which could be the callee or another server that will forward the request). Once the request reaches the callee, it sends back a response and the caller acknowledges the response. RTP is used for the communication between the caller and the callee.
SIP supports mobility and dynamically issued IP addresses, has an important feature. In order to have a functioning application, the user must be able to move between different networks. By using a location server that registers the current IP address of the user, the user may be in the same or different network. When the user connected to the service, the list at the location server is dynamically updated with the current IP address and once the user has disconnected from the service, the IP address is removed from the list. SIP also supports forking of process which means that the SIP server could send one incoming requests to more than one different UAS. This could be used to develop call forwarding to voice mail or functionality where you have two different numbers connected to the user name (e.g. both at home and in the office).The message body in a SIP message is using the MIME(Multipurpose Internet Mail Extension) mechanisms; hence a message may carry binary or text objects. By using this, a SIP message may contain information from a webpage, an email address or even an IRC (Internet Relay Chat) chat channel.
Authentication in SIP is the most important security issue, since no trusted third party makes sure that the information in the setup connection is reliable. Authentication in SIP should not only be used to identify the sender of the message but also to ensure that some critical information was not altered in transit. For authentication, the SIP protocol uses a digest authentication, which is based on the HTTP digest authentication. The response contains a checksum encrypted by MD5, containing the user name, password, a given nonce value, the HTTP method and the requested URL. This prevents the password from being sent in clear text. However, the security is not that strong in HTTP basic authentication and this is not a fully satisfied solution6.
For integrity and confidentiality SIP uses data encryption. There are two different ways of encryption that are supported, end to end (i.e. between two users) and hop to hop (i.e. between two successive SIP entities). End to end confidentiality requires that all information that is not to be read by passing routing servers is encrypted and this is
performed by S/MIME. Hop to hop is useful to protect the information that the intermediate SIP entity needs. This encryption is performed by external mechanisms, such as IPsec or TLS (Transport Layer Security).
When it comes to voice applications, it is very important that each package arrives. Since SIP can be used over UDP, which is a non-reliable transportation protocol, this has to be considered in SIP. This is handled in a way that both the client and the server transmit the requests until a response arrives. For the INVITE request, there could be a quite long delay before the callee picks up the phone; hence this is handled in a separate way to avoid unnecessary overhead. While UDP has lack of reliability it is still preferred in SIP since the handshaking process that takes place in TCP creates a lot of overhead.
SIP has been described as “a simple protocol but powerful implications”. It addresses many of the major issues of the development of Internet telephony, a technology that is predicted to change the way businesses and people talk to each other. Because of its extensive nature, many applications implemented with SIP. The main applications implemented with SIP are as follows:
A SIP session can contain any combination of media (voice, data, video, etc.). These sessions can be modified at any time by adding new parties or by changing the nature of the session. SIP allows browsers to become augmented with multimedia capability. Using SIP, simple, but very powerful, services like click-to-dial become possible. User profiles can be managed through a web interface and voice plug-ins are incorporated into browser technology.
The de-facto standard for describing content on the Internet, to convey information about the protocol used to describe the session and has an URL-style addressing system. It uses the Domain Name System (DNS) to deliver requests to the server that can appropriately handle them.
E-mail, voicemail, faxes, and phone messages are accessible from the same box. Alternatively, people use many different devices to communicate. Unified messaging helps people that use different communication devices, media, and technologies to communicate at any time and under their own control.
Directory services are to a network what white pages are to the telephone system. They store information about things in the real world, such as people, computers, printers, and so on, as objects with descriptive attributes. People can use the service to look up objects by name; or, like the yellow pages, they can be used to look up services. Network managers use
IJSER © 2013
International Journal of Scientific and Engineering Research Volume 4, Issue 1, January 20123 5
ISSN 2229-5518
directories to manage user accounts and network resources. From a manager's viewpoint, a directory service is like an inventory of all the devices on the network. Any device can be located by using a graphic interface or by searching for its name or some properties (e.g., “colour printer”). Once located, a manager can control the device (e.g., disable it or block certain users from accessing it). The directory is a central database where all objects and users are managed.
Software based IP_PBX that is compliant with the SIP standard can be utilized in a single office setting or multiple office locations, offering flexibility and options for future expansions.
A website contains click-to dial links that establish a session between the end user and the website organization. This kind of service could be a part of a value-added web-hosting service offered by a service provider or it could be developed by an enterprise’s IT department.
A web page may be popped when a particular number is called (with SIP, it is just as easy to direct an user to a web page as it is to a telephone). SIP supports IVR (Interactive Voice Response) features, navigating users through options and providing auto-responses to common requests. In addition, SIP’s forking facility is perfect for fulfilling the ACD (Automated Call Distribution) function.
Because a SIP session can consist of any form of communication, it is possible to promote an IM session to a telephone call or even a whiteboard or video session at the click of a button. It is also easy to invite other people to join your session, creating spontaneous conference calls. Using third party call control, a conference service could even check the presence status of people due to join a conference and when all the parties are available it could establish the session by connecting them all to a conference bridge. Presence goes hand-in-hand with the evolution of voice services. A network that has dynamically updated information about an user’s preferences and availability can perform more intelligent call routing than today’s PSTN or existing find-me/follow-me services.
Because SIP client software is lightweight, it can be embedded in mobile phones and PDAs so that these services can cross all platforms. Using SIP as the signalling protocol means that sessions can be established between different devices that then negotiate the appropriate media capability. These devices become means of accessing those services associated with a user instead of being closed, proprietary systems.
Dedicated portable telephone handsets support Voice over IP on 802.11 wireless LAN connections. They may use SIP and other proprietary protocols (i.e., Skinny) and may also support wireless telephony protocols (i.e., GSM)
SIP enables a convergence at the desktop. Voice services can be assimilated into other applications to change the way we use our computers. The information management capabilities of the Internet can be used to transform communication systems and improve productivity. Using SIP features such as user profiling, presence management and instant messaging, third party call control and integration with media, many services can be created by service providers or enterprise IT departments. All the advanced telephony services inherited from the Intelligent Network are supported by SIP. This includes services such as call forwarding, call hold, call waiting, etc.
SIP can be integrated into product such as:
1. IP phones.
2. Media Gateways.
3. Web-enabled telephony portals.
4. Internet call centres.
5. Soft switches.
6. Application servers.
SIP is one of the protocols that grows rapidly and covers all field of communication over the world. Today there exist both commercial and open source implementation of Session Initiation Protocol, hardware and software based. Voice over IP is becoming more and more popular and new features and application are being added all the time. The protocol is still under development and new features are being added. The focus from the beginning was to provide a new dynamic protocol that was powerful but still simple. SIP is based on MIME and less overhead with TCP. SIP supports mobility and dynamically issued IP addresses that makes it too much powerful. Now it is important to enhance the protocol with adequate security as well.
We would like to express our gratitude to Prof. Dr. Nagraj Guruprasad, Director of Buddha Institute of Technology, GIDA, Gorakhpur and Prof. Rajeev Ranjan Tripathi, Head of Department (CS/IT), Institute of Technology, GIDA, Gorakhpur,UP (INDIA) for their kind support.
[1] J. Rosenberg, H. Schulzrinne, G. Camarillo, A. Johnston, J. Peterson, R. Sparks, M. Handley, and E. Schooler, \SIP: Session Initiation Protocol," RFC 3261 (Proposed Standard), Jun. 2002, updated by RFCs 3265, 3853,
IJSER © 2013
International Journal of Scientific and Engineering Research Volume 4, Issue 1, January 20123 6
ISSN 2229-5518
4320, 4916. [Online]. Available:
http://www.ietf.org/rfc/rfc3261.txt
[2] P. Resnick, \Internet Message Format," RFC 2822
(Proposed Standard), United States, 2001. [Online]. Available:
http://www.ietf.org/rfc/rfc2822.txt
[3] N. Freed and N. Borenstein, \Multipurpose internet
mail extensions (mime) part one: Format of internet message
bodies," RFC 2045 (Proposed Standard), United States, 1996.
[Online]. Available: http://www.ietf.org/rfc/rfc2045.txt
[4] J. Rosenberg, \The Session Initiation Protocol (SIP)
UP-DATE Method," United States, 2002. [Online]. Available:
http://www.ietf.org/rfc/rfc3311.txt
[5] J. Elwell, \Connected Identity in the Session Initiation
Protocol (SIP)," United States, 2007. [Online]. Available:
http://www.ietf.org/rfc/rfc4916.txt
[6] D’Heureuse, N., J. Seedorf and S. Niccolini, 2009. A policy framework for personalized and role-based SPIT prevention. Proceedings of the 3rd International Conference on Principles, Systems and Applications of IP
Telecommunications, Jul. 07-08, ACM, Atlanta, GA, USA. DOI: 10.1145/1595637.1595653
[7] Cui, X., Y. Zhang, W.J. Lee and S.J. Koh, 2010. SIPbased IM and its security solutions. Proceedings of the 6th International Conference on Wireless Communications Networking and Mobile Computing, Sep. 23-25, IEEE Xplore Press, Chengdu, pp: 1-4. DOI: 10.1109/WICOM.2010.5601309
[8] Taber, S., C. Schanes, C. Hlauschek, F. Fankhauser and T. Grechenig, 2010. Automated security test approach for SIP-based VoIP softphones. Proceedings of the 2nd International Conference on Advances in System Testing and Validation Lifecycle, Aug. 22-27, IEEE Xplore Press, Nice, pp:
114-119. DOI: 10.1109/VALID.2010.20
[9] Security considerations for voice over IP systems , D.
Richard Kuhn, Thomas J.
[10] Walsh, Steffan Fries, National Institute of Standards and Technologies. NIST special publication 80058. January
2005, p. 3945.
[11] Session Initiation Protocol , KK Tan and HL Goh.
P.13101314 Volume 2, IEEE International conference on
Information Technology, 11:th14:th of December 2002
[12] Design and Implementation of a SIPbased VoIP
architecture , S. Zeadally and F. Siddiquini IEEE AINA 2004
SIP, Session Initiation Protocol used in VoIPKarin
Tybring,Petra Wahlund,Zhu Yunyun.
[13] Session Initiation Protocol Security: A Brief Review
Aws Naser Jaber, Chen-Wei Tan, Selvakumar Manickam and
Ali Abdulrazzaq Khudher National Advanced IPv6
Centre,University Sains Malaysia, 11800 USM, Penang,
Malaysia
[14] SIP Communication for Dummies by Lawrence
Miller, CISSP, and
Peter H. Gregory, CISA, CISSP Foreword by Alan
B. Johnston
[15] STREAM CONTROL TRANSMISSION PROTOCOL
SUPPORT IN SESSION INITIATION PROTOCOL PROXY
SERVER by Thomas Kwok Cheong Pang B.A.Sc. (Computer
Engineering), Simon Fraser University, 1995
IJSER © 2013