Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h, Vo lume 3, Issue 1, January -2012 1
ISS N 2229-5518
Secured Multi Path Routing with Trust Establishment Using Mobile Ad Hoc Networks T. Nirmal Raj, S. Saranya, S. Arul Murugan, G. Bhuvaneswari
Abs tract - We propose a novel method of message security using trust-based multi-path routing. Simulat ion results, coupled w ith theoretical justif ication, aff irm that the proposed solution is much more secured than the traditional mu lti-path routing algorithms. We propose a method to securely route messages in an ad-hoc netw ork using multi-path routing and trustw orthiness of the nodes. Hence, w e aim at addressing the issues underlying message conf identiality, message integrity and access control. We combine multi-path routing and trust w ith sof t encryption technology to propose a scheme w hich is much more secure than traditional mult i-path algorithms. By sof t encryption, w e mean having encryption methods, but are more eff icient in terms of perf ormance and require less resource.
Ke ywords : Trust, Misbehaving nodes, sof t encryption, Dynamic Source Routing, Multi-path routing.
—————————— ——————————
1. INTRODUCTION
A mobile ad hoc networ k (MANET) is a kind of wir eless ad hoc networ k, and is a self-configur ing netw or k of mobile r outers (and associated hosts) connected by wir eless links – the union of which form an arbitrary topology. The r outers ar e fr ee to move randomly and or ganize themselves arb itr arily; thus, the netw or k’s wir eless topology may change rapidly and unpr edictably. Mobile ad hoc networ ks (MANETs) ar e composed of a set of stations (nodes) communicating thr ough w ir eless channels, w ithout any fixed backbone support. With the advancement in radio technologies like Bluetooth, IEEE 802.11 or hiper lan, a new concept of netw or king has emer ged which makes wir eless networ ks incr easingly popular in the computer industry. This is particular ly true w ithin the past decade, which has seen wir eless networ king being adapted to enable mobility.
Later on number s of differ ent pr otocol have been pr oposed as a r outing solution for mobile ad hoc netw or ks. These differ ent r outing techniques classified as pr oactive, r eactive and hybr id r outing pr otocols. Reactive r outing pr otocols have been found to be user friendly and efficient when compar ed to other r outing pr otocols. The main boon of Reactive r outing protocols when compar ed w ith Pr oactive and Hybr id r outing pr otocols is the r elatively unconditional low storage r equir ements, higher mobility and the availability of r outes w hen needed. Ther e ar e a variety of r eactive r outing pr otocols such as AODV, DSR, LAR1, LMR, ABR, SSI, TORA, RDMAR, MSR, AOMDV, MRAODV, ARA. Most of the multipath r outing pr otocols like AOMDV, MP-OLSR and MP-DSR ar e the extension of unipath pr otocols like AODV, OLSR and DSR. In these pr otocols w e use the DSR in this paper . DSR is the next generation pur e r eactive r outing pr otocol for MANETs. It was proposed for the first time by Johnson and Maltz [5] in
or der to pr ovide r outing w ith minimum overhead while adapting to the networ k dynamics.
DSR is under going fast evolution thanks to the many optimizations integrated into it. DSR is based on a pur e r eactive appr oach and oper ates using tw o simple and complementary mechanisms: r oute discovery and r oute maintenance. In this paper We propose a novel method of message secur ity using tr ust -based multi-path r outing we pr opose a method to secur ely r oute messages in an ad-hoc networ k using multi-path r outing and tr ustworthiness of the nodes. W e aim at addr essing the issues underlying message confidentiality, message integrity and access contr ol.
2. RELATED WORKS
Secur ity in MANETs has been a topic of much discussion in the last few years. Ther e ar e a plenty of wor ks available in the liter atur e that discuss secur ity in MANETs. But efficiently pr oviding complete message secur ity in such networ ks still r emains an open issue.
Much r esearch wor k has been done to make the r oute discover ed by Dynamic Sour ce Routing (DSR) secur e. A Trust based multi path DSR pr otocol is pr oposed by Poonam et al. [11] in which uses multi-path forwarding approach. In this appr oach each node forwar ds the RREQ if it is r eceived fr om differ ent path. Thr ough this method detect and avoid misbehaving nodes which wer e pr eviously included due to vulner ability in DSR r oute discovery. In the traditional DSR pr otocol [5] when a node r eceives a RREQ packet, it checks if it has pr eviously pr ocessed it, if so it dr ops the packet. A misbehaving node takes advantage of this vulner ability and forwar ds the RREQ fast so that the RREQ fr om other nodes ar e dr opped and the path discover ed includes itself. In th eir pr otocol
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h, Vo lume 3, Issue 1, January -2012 2
ISS N 2229-5518
each node broadcast the packet embedding tr ust information about the node fr om which the packet is r eceive. At the source node a secur e and efficient r oute to the destination is calculated as w eighted average of the number of nodes in the r out e and their trust values.
All the existing models have one or mor e of the following limitations. Most of the methods use the traditional DSR r equest discovery model, in which a node dr ops a RREQ packet, if it has pr eviously processed it. A misb ehaving node takes advantage of this and forwar ds the RREQ packet fast so that the RREQ r eceived fr om other nodes, which arr ive later , ar e dr opped and the path discover ed includes itself. Most of the tr ust based r outing pr otocols have used forward tr ust model to find the path fr om source to destination. In this model trust is embedded only in the RREQ packet when it is forwar ded. So each node evaluates only its pr evious node and the source node evaluates all the nodes involved in path. But w e believe that the tr ust is asymmetr ic, so mutual tr ust infor mation should be used. In watch dog and pathrater appr oach the tr ust values ar e not updated based on node behavior , rather they ar e updated periodically. Such per iodic updates ar e not able to quantify the misbehaving nodes. Ther efor e the path discover ed includes misbehaving nodes. All of these possible vulnerabilities have been taken car e of in [11]. The authors have designed a secur e r outing pr otocol, called Tr ust based multi path DSR pr otocol, which depends on two-way effort of the node by embedding tr ust to find an end-toend secur e r oute fr ee of misbehaving nodes. This pr otocol has a drawback r outing overhead is very high compar ed to traditional DSR due to br oadcasting of RREQ packet. The other drawback is that all the one hop neighbor s of destination after r eceiving first RREQ pr opagate to destination and also among them. Then this r esults in discar ding the RREQ packet fr om most of the other paths to the destination node.
3. GLOMOSIM
Glomosim is a library-based sequential and parallel simulator for wir eless netw or ks. This has been developed using PARSEC, a C-based parallel simulation language. Glomosim can be modified to add new protocols and applications to the libr ary. Ther efor e Glomosim is a good choice for implementing the differ ent traffic sources.
4. TRUST BASED MULTI-PATH ROUTING WITH SOFT ENCRYPTION TECHNOLOGY
W e pr opose a method to secur ely r oute messages in an ad- hoc networ k using multi path r outing and trustworthiness of the nodes. Hence, w e aim at addr essing the issues under lying message confidentiality, message integr ity and access control. W e divide the message into differ ent parts and encrypt these parts using one another . W e then r oute these parts separately using differ ent paths between a pair of sour ce-destination nodes. An intermediate node can access differ ent parts on the basis of its tr ustworthiness. That is, a mor e trusted node is allow ed to featur e in mor e paths than a less trusted node and hence access to mor e message parts than a less trusted node. This featur e allows the r outing algor ithm to avoid nodes that ar e mor e likely to attempt ‘br eaking-in’ the encryption. In addition, suspected nodes which have high computation pow er and ar e hence likely to be mor e successful in cryptanalysis can be given less par ts to stymie their plans. Since establishment of tr ust also r equir es cryptographic key exchange, w e use a soft appr oach to tr ust. Trust levels of peer nodes of the networ k ar e found using effort r eturn based tr ust model. W e use a var iation of the model, which uses a combination of derived tr ust and r eputation to estimate tr ust values of a node.
W e combine multi-path r outing and tr ust with soft encryption technology to pr opose a scheme w hich is much mor e secur e than tr aditional multi-path algorithms. Networ ks using the DSR pr otocol have been connected to the inter net. DSR can inter oper ate with mobile IP, and nodes using mobile IP and DSR have seamlessly migr ated betw een W LANs, cellular data services, and DSR mobile ad hoc etw or ks. The DSR pr otocol include easily guaranteed loop-fr ee r outing, support for use in networ ks containing unidir ectional links, use of only ‚soft state‛ in r outing, and very rapid r ecovery when r outes in the netw or k change. This is the r eason for pr eparing to the DSR protocol.
4.1 SOFT ENCRYPTION TECHNIQUES AND ROUTING
A 4n-bits message is divided into four parts of n bits each. Let us denote these parts by a, b, c and d. W e define the bit operation XOR on bit vectors k and l as follows:
If k = {k1, k2, k3<, kn} And l = {l1, l2, l3, <, ln} Then
k XOR l = {k1 XOR l1 , k2 XOR l2 , k3 XOR l3 , <; kn XOR ln}
The afor ementioned par ts a, b, c, and d ar e then encrypted by means of the following equations:
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h, Vo lume 3, Issue 1, January -2012 3
ISS N 2229-5518
a’ = a XOR c b ’ = b XOR d c’ = c XOR b
d’ = d XOR a XOR b
The parts a’, b ’, c’ and d’ ar e now r outed instead of a, b , c and d. Paths betw een the sour ce and destination nodes ar e found using DSR. A node w aits for intermediate multiple paths to the destination. Routing paths ar e selected fr om
The set of paths using a novel trust defined strategy.
At the destination node, the message par ts can be decrypted using the following equations:
a=b ’ XOR d’
b=a’ XOR b ’ XOR c’ XOR d’
c=a’ XOR b ’ XOR d’
d=a’ XOR c’ XOR d’
4.2 TRUST ESTABLISHMENT
A node is assigned a discr eet trust level in the range of -1 to
4. A tr ust level of 4 defines a complete trust and a tr ust level of -1 defines a complete distr ust. These tr ust levels also define the maximum number of packets, which can be r outed via those nodes. A tr ust level of -1 signifies that any packet coming fr om that node should be dr opped. No packet is in turn r outed to these nodes, leading to an isolation of malicious nodes.
4.3 TRUST LEVELS ASSIGNMENT
The tr ust level assigned to a node is a combination of dir ect inter action with its neighbour s and the r ecommendations fr om its peers. A node assigns a dir ect tr ust level to its neighbour on the basis of the acknowledgements r eceived. If the neighbour sends a pr ompt acknowledgement of the packet r eceived, it is assum ed that the node is not involved in a r esour ce intensive br ute-for ce attack and hence is assigned a higher tr ust level. The dir ect tr ust is then combined with the tr ust r ecommendation fr om its peers and a final tr ust level is assigned to it. But these tr ust levels ar e assigned dynamically and ar e cached by a node for per formance enhancement. The tr ust r ecommendations ar e piggybacked on DSR r outing packets.
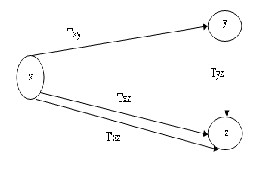
Figure 1: Trust levels assignment
Let us consider that Txy r epr esents the dir ect tr ust in node Y by node X, and let Tyz r epr esents the tr ust r ecommended by the node Y in node Z. If T’xz r epr esents the dir ect trust of node Z in node X, then the tr ust assigned by X in Z.
T’xz = 1- (1- Txz ).(1- Txyz )
Wher e Txyz = 1 -(1- Txy ) Tyz
The trust levels ar e normalized to integer values using standar d methods. Each node is given an integer tr ust value lying betw een -1 and 4. If a new node j oins the networ k, it sends a hello packet to its neighbours. The neighbour s would assign an initial trust value of 0 to the node. The tr ustw orthiness of the node can be incr eased if the node shows benevolent behaviour . Similarly, w hen a node leaves the networ k, it would no longer r espond to the messages. The neighbour may conclude that the netw ork has lost its connectivity or the node has exited the networ k.

5. RESULT
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h, Vo lume 3, Issue 1, January -2012 4

ISS N 2229-5518
7. REFERENCES
6. CONCLUSION
The simulation experiments conducted w er e evaluated in Global Mobile Information System Simulator (GloMoSim). GloMoSim is a scalable simulation envir onment for lar ge wir eless and wir e line communication systems using parallel discr eet-event simulation language called PARSEC. GloMoSim is an event based system coded in C. GloMoSim implements all the seven layer s of the ISO-OSI r efer ence model and is customizable and assessable at all the layers. It supports various pr e compiled models and protocols at various layer s including the DSR r outing algor ithm at the networ k layer , which was used as a basis for our system. On the Medium Access Contr ol(MAC)layer , pr otocols such as CSMA, FAMA,MACA and IEEE 802.11 ar e curr ently available. On the application lay er , models such as TCPLIB, CBR (Constant Bit Rate) and HTTP tr affic ar e supported. It is at the application layer that the soft encryption using various message parts is implemented.
W e discussed var ious methods that have been pr oposed and highlighted their r espective advantages and limitations in var ious scenarios. W e have pr ovided some ideas of possible solutions to these pr oblems and w e have discussed how our pr oposed system can incor por ate these solutions. Based on these settings, w e have intr oduced a tr ust based multi-path algor ithm for message secur ity in MANETs. W e have discussed the message encryption and the tr ust establishment methodologies that can be used in the system. Then, we have pr oposed a trust based strategy for r oute selection. The implementation of this trust-based approach using DSR was then discussed. Finally, the simulation r esults obtained fr om our algor ithm ar e compar ed against the r esults obtained using traditional algor ithms such as normal DSR and multi-path r outing using disj oint paths, used as benchmar ks. Our pr oposed solution pr oved to be much mor e secur ed than the r esults obtained fr om tradit ional multi-path r outing algor ithms.
[1] Br och, J., Maltz, D. A., Johnson, D. B., Hu, Y.C. and Jetcheva, J. G. 1998 A per formance compar ison of multihop wir eless ad hoc netw or k r outing pr otocols. In proceeding of International Confer ence Mobile Computing and Networ king (MobiCom), ACM Pr ess, 85–97.
[2] Buchegger , S. and Boudec, J. 200 7. Per formance Analysis of the CONFIDANT Pr otocol: Cooper ation Of Nodes— Fairness In Distr ibuted Ad hoc NeTw or ks. In Pr oceeding ACM W or kshop Mobile Ad Hoc Networ king and Computing (Switzer land, 2006). 226-236.
[3] Gar finkel, S.1995 PGP: Pr etty Good Pr ivacy. O‘Reilly
and Associates.
[4] Haniotakis, T., Tr agoudas, S. and Kalapodas, C. 2009. Secur ity enhancement thr ough multiple path transmission in ad hoc netw or ks. IEEE Communications Society, 4187-
4191.
[5] Johnson, D. B., Maltz, D. A., Hu, Y. C. and Jetcheva, J.G.
2008. The dynamic sour ce r outing pr otocol for mobile ad
hoc netw or ks (DSR). Inter net draft IETF RFC 3561, http://www.ietf.or g/r fc/r fc3561.txt.
[6] Marti, S., Giuli, T. J., Lai, K. and Baker , M. 2006 . Mitigating r outing misbehavior in mobile ad hoc netw or ks. In Proceeding of Sixth Annual International Confer ence Mobile Computing and Netw or king (MobiCom). ACM Pr ess, New Yor k, NY, 255-265.
[7] Nar ula, P., Dhurandher , S. K., Misra, S. and W oungang, I. 2007. Security in mobile ad-hoc netw or ks using soft encryption and tr ust-based multi-path routing. Elsevier Journal of Computer Communications, 760-769.
[8] Pir zada, A. A., Datta, A. and McDonald, C. 2004. Pr opagating trust in ad-hoc netw or ks for r eliable r outing. In Pr oceeding of IEEE Inter national Wor kshop W ir eless Ad Hoc Networ ks (Finland, 2004). 58 -62.
[9] Pir zada, A. A., Datta, A. and McDonald, C. 2005 . Trustbased r outing for ad-hoc wir eless netw or ks. In Pr oceeding of. IEEE International Confer ence Networ ks (Singapor e, 2004). 326-330.
[10] Pissinou, N., Ghosh, T. and Makki, K. 2005 . Collaborative tr ust-based secur e r outing in multihop ad hoc networ ks. Networ king (Athens, Gr eece 200 5). Lectur e Notes in Comput er Science, vol. 3042, 1446-1451.
[11] Poonam, Gar g, K., and Misra, M. 2010. Trust based multi path DSR pr otocol. In Pr oceedings of Fifth
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h, Vo lume 3, Issue 1, January -2012 5
ISS N 2229-5518
International Confer ence on Availability, Reliability and
Secur ity, (Poland, February, 2010). 204-209.
[12] QUALNET simulator , Available fr om:
<http://www.scalable-networ ks.com>.
[13] Wang, C., Yang, X. and Gao, Y. 2005. A Routing Pr otocol Based on Tr ust for MANETs. In Pr oceeding of Sixth Annual International Confer ence on Gr id and Cooperative Computing (Beij ing, China ). Lectur e notes in computer science, vol. 3795, 959-964.
[14] Yong, C., Chuanhe, H. and W enming, S. 2007. Trusted Dynamic Source Routing Pr otocol. IEEE International Confer ence on W ir eless Communications, Netw or king and Mobile Computing (Athens, Gr eece 2007), 1632-1636.
[15] Zhou, L. and Haas, Z. J. 2009 . Secur ing ad hoc networ ks IEEE Netw or k Magazine, vol. 13, no. 6, 1-12.
AUTHORS PROFILE

T.Nirmal Raj M.Sc,. Mphil w or king as an Senior Assistant Pr ofessor in the Department of Computer Science and Applications in Sr i Chandr asekhar endra Saraswathi Viswa Mahavidyalaya, Enathur , Kanchipuram, Tamil Nadu. He has published mor e than 5 Paper s in National, International
j ournals and confer ences. His r esearch inter est lies in the
ar ea of Networ k. mailt o: t nirmalr ajcse@gmail.com

S.Saranya Mphil, Resear ch Scholar in the Department of Computer Science & Applications in SCSVMV University, Enathur, Kanchipuram. She r eceived the degr ee in Master of Computer Science fr om Madras Univer sity in 2010. She has pr esented 2 papers in National confer ence & participated many National and Inter national Confer ences. Her inter ested ar ea in r esear ch is Networ k. mailt o: sarandhana889@gmail.com
S.Arul Murugan Mphil, wor king as a assistant pr ofessor in sr i sankar a arts & science college..He has pr esented 2 paper s in national confer ence in the ar ea of data mining and war ehousing & participated many National and Inter national Confer ences.. His ar ea of inter est is netw or king and data mining mailt o: ar ul_jasmines@yahoo.co.in

G.Bhuvaneswari Mphil, Research Scholar in the Department of Computer Science & Applications in SCSVMV University, Enathur , Kanchipuram. She r eceived the degr ee in Master of Computer Science
fr om Madras University in 2010. She has
pr esented 1 papers in National confer ence & participated many National and International Confer ences. Her inter ested ar ea in r esear ch is Netw or k. mailt o:
bhuvanagan@gmail.com

IJSER © 2012 http :// www.ijser.org






