1) H.323 [9],
2) Session Initiation Protocol (SIP) [3],
3) Media Gateway Control Protocol (MGCP) [2], and
4) Real-time Transport Protocol (RTP) [1].
International Journal of Scientific & Engineering Research Volume 4, Issue 1, January-2013 1
ISSN 2229-5518
STUDY OF VOIP SERVICES AND ITS
APPLICATIONS
Kailash Tambe, Rohan Bhor, Tejas Patwari, Batish Momin, Prashant Vhatkar
Abstract— Now a day’s ‘IP Telephony’ is becoming an increasingly popular subject. Internet Telephony (Voice over IP) essentially means a voice mes- sage transmitted using the Internet Protocol. IP Telephony generally refers to the use of the SIP signalling protocol used to setup, control and manage voice. The Session Initiation Protocol (SIP) is a signaling protocol for initiating, managing and terminating voice sessions across packet networks.IP Telephony based on SIP through mobiles phone enables the user to make voice call at very low call rates. One can use SIP phones to call your friends and family at any geographical location. But the restriction is both the party communicating must be SIP users. Because of the use of Internet facility helps in reducing the call rates. IP Telephony based on SIP through mobiles phone provides mobile environment for VoIP calls. VoIP would fail if re- mained wired. So through this system one can make VoIP call from their mobile phones which are having Internet access facility.IP Telephony based on SIP through mobiles phone had achieved the feature of portability which is absent the traditional telephone call system.
Index Terms— VOIP, RTP, SIP, PROXY SERVER
—————————— ——————————
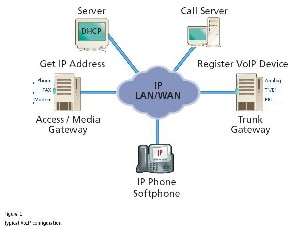
V VOIP stands for Voice over IP. VOIP is a tech-
nology which is used for transmission of voice packets on
packet switched IP networks. VOIP is also known as IP te- lephony or Internet telephony. The simple idea behind the concept of VOIP is to send the digitized samples of voice over data network and then replay these packets at receiver end to hear the original voice. We can send audio, video or timed text over VOIP. In general, it can be used for multimedia communication over IP network. Though it incurs cost for network connectivity, many applications like Skype [5], Ya- hoo Messenger [6], Google Chat [7], etc. allow “free" calls to their users. Here, free refers to a marginal cost of making the user call. Long distance phone calls such as Jumblo[8], are also cheaper than traditional phone calls. VOIP also reduces the infrastructure cost as a only a single network is required to carry the data as well as voice packets. Packets are only delivered when there is a media content to be delivered. The user can receive and make calls from anywhere. It is also pos- sible to combine VoIP services with other systems such as email, conferencing, and so on. Some modes of operations for VoIP are [4]:
1) PC-to-PC,
2) Phone-to-Phone,
3) PC-to-Phone,
4) Phone-to-PC, and
5) Network to Network.
————————————————
Rohan Bhor is currently pursuing Batchler degree program in computer engineer- ing in Pune University, India, PH-+91-892 892 9009.
E-mail:rohanbhor09@yahoo.co.in
Tejas Patwari is currently pursuing Batchler degree program in computer engi-
neering in Pune University, India.
Batish Momin is currently pursuing Batchler degree program in computer engi-
Some important technologies and protocols related to VoIP are:
1) H.323 [9],
2) Session Initiation Protocol (SIP) [3],
3) Media Gateway Control Protocol (MGCP) [2], and
4) Real-time Transport Protocol (RTP) [1].
neering in Pune University, India.
IJSER © 2013
Prashant Vhatkar is currently pursuing Batchler degree program in comhtptpu:/t/werww.ijser.org
engineering in Pune University, India.
International Journal of Scientific & Engineering Research Volume 4, Issue 1, January-2013 2
ISSN 2229-5518
Many well known threats to internet applications also apply to the VOIP. A VOIP application may face different attacks like spam over internet telephony (SPIT), spoofing and identi- ty theft.
In this type of attack an attacker masquerades as another VoIP caller. For example, an attacker can try to insert a fake caller ID into an ordinary VoIP call so that the receiver be- lieves the call to be coming from a known and trusted source (a bank, for example). A receiver may place trust on a user whose identity has been faked by the attacker. In such con- versation, the receiver may be tricked to disclose his personal information like account numbers, social security numbers etc. This is same as the traditional phishing attacks where a user follows links in an unsolicited email and is tricked to provide personal information. The bits and pieces of the in- formation provided by the may be used to complete the iden- tity records of victims for identity theft.
VOIP voice/data packets may sometimes be sent unencrypted over the internet. This raises questions regard- ing the confidentiality of VOIP service. So, it is possible for an attacker to collect the data traveling over VOIP system. He may also try to reconstruct the conversation.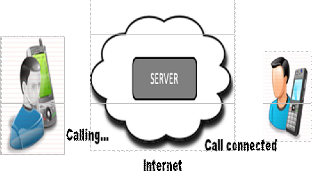
Fig- ure 3.1: SIP users and the Communicating server
The input to the system is valid SIP user number, which the user gets while registration such as 101, 102. Ac- cording to dialed number the call establishment is done with help of the server. The server here acts like a proxy which helps to connect call. The server here is responsible to initiate, manage and terminate the call. The callee can accept or reject the call. The subsystem i.e. the server will also generate different tones like busy tone, ringing tone etc. It also helps to add new user or delete users
The functionalities of subsystem are explained below
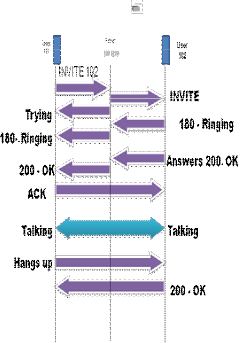
Figure 3.2 : Basic flow diagram showing communication be- tween two SIP users
The SIP server is used to resolve usernames to IP addresses, so that requests sent from one user agent to an- other can be directed properly. A user agent registers with the SIP server, providing it with their username and current IP address, thereby establishing their current location on the network. This also verifies that they are online, so that other user agents can see whether they’re available and invite them into a session. Because the user agent probably wouldn’t know the IP address of another user agent, a re- quest is made to the SIP server to invite another user into a session. The SIP server then identifies whether the person is currently online, and if so, compares the username to their IP address to determine their location. If the user isn’t part of that domain, and thereby uses a different SIP server, it will also pass on requests to other servers.
In performing these various tasks of serving client requests,
the SIP server will act in any of several different roles.
Registrar server
Proxy server
Redirect server
Registrar servers are used to register the location of a user agent who has logged onto the network. It obtains the IP address of the user and associates it with their
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1, January-2013 3
ISSN 2229-5518
username on the system. This creates a directory of all those who are currently logged onto the network, and where they are located. When someone wishes to establish a session with one of these users, the Registrar server’s information is referred to, thereby identifying the IP addresses of those involved in the session.
Proxy servers are computers that are used to for- ward requests on behalf of other computers. If a SIP server receives a request from a client, it can forward the request onto another SIP server on the network. While functioning as a proxy server, the SIP server can provide such functions as network access control, security, authentication, and au- thorization.
1. Reduce long distance calling cost: The main benefit that attracts multiple customers is the cost of phone calls over IP and to be more precise almost a complete ab- sence of fees for international and long distance calls that are charged so high by phone companies.
2. Portability: Wherever you have an access to mobile In- ternet connection you can sign up with your SIP ac- count and make and receive phone calls to your VoIP number.
3. Functionality: Since VoIP is digital one can offer more services together with voice such as call redirection, call waiting and call on hold, audio conference etc.
4. They simplify and enhance telecommunications for business users.
1. This SIP API is expensive to use.
2. SIP has disadvantages depend lot choices of client phone, hardware, network, and Internet telephony service provider.
3. Minimum Requirements: Dial-up service may be suffi- cient for your Internet needs, but it won’t be powerful enough to carry voice.
4. High-speed service, usually broadband is usually con- sidered a minimal necessity for successful SIP service.
5. No facility to make Emergency Calls.
Mobile phones: Because SIP client software is lightweight; it can be embedded in mobile phones so that these services can cross all platforms. Using SIP as the sig- nalling protocol means that sessions can be established be- tween different SIP user that then negotiate the appropriate media capability.
LAN VoIP Calls: The softphone developed help the LAN
user to communicate with each other for free. The maxi-
mum number of the SIP user supported is 20.
Business purpose and private network users: Help the SIP
user in a virtual private network to establish call within its network. It would also provide facility of conferencing for the employee who is not physically present at office.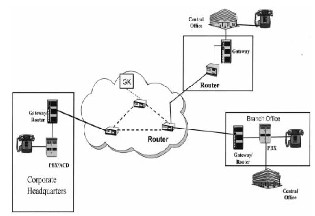
Business use of VOIP
We thank department of computer engineeri8ng
MITCOE for its kind support during the work.
[1] H. Schulzrinne, S. Casner, R. Frederick, and V. Jacobson. RTP: A Transport Protocol for Real-Time Applications. RFC 3550 (Standard), July 2003. Updated by RFCs 5506, 5761, 6051, 6222.
[2] F. Andreasen and B. Foster. Media Gateway Control Protocol (MGCP) Version 1.0. RFC 3435 (Informational), January 2003. Updated by RFC
3661.
[3] J. Rosenberg, H. Schulzrinne, G. Camarillo, A. Johnston, J. Peterson,
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1, January-2013 4
ISSN 2229-5518
R. Sparks, M. Handley, and E. Schooler. SIP: Session Initiation Protocol. RFC 3261 (Proposed Standard), June 2002. Updated by RFCs 3265, 3853,
4320, 4916, 5393, 5621, 5626, 5630, 5922, 5954, 6026, 6141.
[4] Gerald Q. Maguire Jr. Practical Voice Over IP (VoIP): SIP and related protocols. http://www.ict.kth.se/courses/IK2554/VoIP-20100826. pdf. Accessed February 27, 2011.
[5] Skype Internet Telephony. http://www.skype.com/. Accessed February
27, 2011.
[6] Yahoo! Messenger. http://messenger.yahoo.com/. Accessed February
27, 2011.
[7] Google Chat. http://www.google.com/talk/. Accessed February 27,
2011.
[8] Jumblo, VoIP service provider. http://www.jumblo.com/. Accessed
February 27, 2011.
[9] International Telecommunication Union. Packet-based Multimedia
Communications Systems. ITU-T Recommendation H.323, December
2009.
http://www.itu.int/rec/T-REC-H.323-200912-I Accessed February 27,
2011.
IJSER © 2013 http://www.ijser.org