By introducing soft computing tools we can add intelligence to

the recognition system, so that the system can tell the likelih- ood of the particular image to be on a particular database and other intelligent features can also be introduced.
International Journal of Scientific & Engineering Research,Volume 3, Issue 6, June-2012 1
ISSN 2229-5518
SCIFI-A Project Proposal
Soft Computing for Identificati Back-propagation Neural Network, Fingerprint, Fingerprint Matching, Fuzzy Logic, Minutia, Neural Network.on of
Fingerprint Image
Samayita Bhattacharya, Kalyani Mali
Abstract— To uniquely recognizing humans based upon one or more intrinsic physical or behavioral traits is called as Biometrics. Biometrics is one of the biggest tendencies in human identification. The fingerprint is the most widely used biometric. However consid ering the automatic fingerprint recognition a completely solved problem is a common mistake. The most popular and extensively used method is the minutiae-based method (minutia are specific points in a finger image. It is the unique, measurable physical characteristics scanned as input and stored for matching by biometric systems. For fingerprints, minutiae include the starting and end ing points of ridges, bifurcations and ridge junctions among other features). There are many different algorithms being used to get this accomplished. Here we have discussed soft computing tools namely fuzzy logic and neural network and how they can be used in fingerprint recognition.
Index Terms— Back-propagation Neural Network, Fingerprint, Fingerprint Matching, Fuzzy Logic, Minutia, Neural Network.
—————————— ——————————
DENTITY is to establish the identity of a person, or to ascer- tain the origin, nature, or definitive characteristics of a par- ticular person. To uniquely identify a person, the recent trend is to use biometric. Fingerprints are the graphical flow-like ridges present on human fingers. Finger ridge configurations do not change throughout the life of an individual except due to accidents such as bruises and cuts on the fingertips. This property makes fingerprints a very attractive biometric iden- tifier. Fingerprint-based personal identification has been used for a very long time. Owning to their distinctiveness and sta- bility, fingerprints are the most widely used biometric fea- tures. Nowadays, most automatic fingerprint identification systems (AFIS) are based on matching minutiae, which are
local ridge characteristics in the fingerprint pattern.
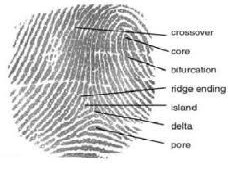
Figure 1: Finger Image
However, a potential ways to improve the algorithms espe- cially on pre-processing steps are still needed to be studied. There have been many algorithms developed for extraction and matching of minutia. Most algorithms found in the litera- ture are somewhat difficult to implement and use a rather heuristic approach.
By introducing soft computing tools we can add intelligence to
the recognition system, so that the system can tell the likelih- ood of the particular image to be on a particular database and other intelligent features can also be introduced.
IJSER © 2012
International Journal of Scientific & Engineering Research,Volume 3, Issue 6, June-2012 2
ISSN 2229-5518

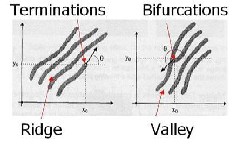
tigation. The model relies on representing only the two most prominent structures: ridge ending and ridge bifurcation, which are collectively called minutiae.
Figure 2: Different fingerprint patterns
Conventional computing or often called as hard computing, requires a precisely stated analytical model and often a lot of computation time. Many analytical models are valid for ideal cases, and real world problems exist in a non-ideal environ- ment.
Soft computing differs from conventional (hard) computing in that, unlike hard computing, it is tolerant of imprecision, un- certainty, partial truth, and approximation. In effect, the role model for soft computing is the human mind. The guiding principle of soft computing is: Exploit the tolerance for impre- cision, uncertainty, partial truth, and approximation to achieve tractability, robustness and low solution cost. Soft computing may be viewed as a foundation component for the emerging field of conceptual intelligence. Few soft computing tools are: Fuzzy Systems, Neural Networks, Evolutionary Computation, Machine Learning and Probabilistic Reasoning.
Biometrics consists of methods for uniquely recognizing hu- mans based upon one or more intrinsic physical or behav- ioural traits. Currently Biometrics is one of the biggest tenden- cies in human identification.
Fingerprints, due to its inimitability, distinctiveness and stabil-
ity are the most widely used biometrics in recent days. Fingerprints are the graphical flow-like ridges present on hu- man fingers. Finger ridge configurations do not change throughout the life of an individual except due to accidents such as bruises and cuts on the fingertips. This property makes fingerprints a very attractive biometric identifier. Fin- gerprint-based personal identification has been used for a very long time.
Most of the automatic fingerprint identification/verification
————————————————
![]() Samayita Bhattacharya is a PhD student in the Department of Computer Science and Engineering, University of Kalyani, India. E-mail: samayi- ta.bhattacharya@gmail.com
Samayita Bhattacharya is a PhD student in the Department of Computer Science and Engineering, University of Kalyani, India. E-mail: samayi- ta.bhattacharya@gmail.com![]() Kalyani Mali is an Associate Professor in the Department of Computer Science and Engineering, University of Kalyani, India. E-mail: kalyanima- li1992@gmail.com
Kalyani Mali is an Associate Professor in the Department of Computer Science and Engineering, University of Kalyani, India. E-mail: kalyanima- li1992@gmail.com
systems adopt the model used by the Federal Bureau of Inves-
Figure 3: Fingerprints and Minutia
Identification system recognizes an individual by searching the entire template database for a match. It conducts one-to- many comparisons to establish the identity of the individual. In an identification system, the system establishes a subject’s identity (or fails if the subject is not enrolled in the system da- tabase) without the subject having to claim an identity.
Large volumes of fingerprints are collected and stored every-
day in a wide range of applications including forensics, access
control, and driver license registration.
An automatic recognition of people based on fingerprints re-
quires that the input fingerprint be matched with a large number of fingerprints in a database.
Fingerprint matching techniques can be placed into two cate-
gories: minutiae-based and correlation based. Minutiae-based techniques first find minutiae points and then map their relative placement on the finger. (However, there are some difficulties when using this approach. It is dif- ficult to extract the minutiae points accurately when the fin- gerprint is of low quality.)
Automatic fingerprint identification system (AFIS) can be fur- ther made more accurate using soft computing tools. The most used fingerprint recognition system in current days depends on minutia extraction. Different soft computing tools can be used in different phases of fingerprint feature extraction, clas- sification and matching.
Noise is a big issue in fingerprint extraction and matching.
Wavelets can be used in removing noise from the fingerprint image. In the minutia extraction phase only extracting minutia does not help to get enough information about the minutia, so aligning minutia becomes a necessary step. Fuzzy techniques can be used in minutia alignment. For the hierarchical classifi- cation of fingerprints neural network can be used. We can set
IJSER © 2012
International Journal of Scientific & Engineering Research,Volume 3, Issue 6, June-2012 3
ISSN 2229-5518

four classes for hierarchical classification i.e. arch, left loop, right loop and whorl [8].
A B C D Figure 4: AFIS Pattern Types:(A) Arch; (B) Left Loop; (C) Right Loop; (D) Whorl
In our project proposal, we proposed to use back propagation neural network for fingerprint identification with fuzzy tech- niques incorporated after hierarchical classification and minu- tia detection.
The term neural network was traditionally used to refer to a network or circuit of biological neurons. The modern usage of the term often refers to artificial neural networks, which are composed of artificial neurons or nodes. Artificial neural net- works are composed of interconnecting artificial neurons (programming constructs that mimic the properties of biologi- cal neurons).
Artificial neural networks may either be used to gain an un-
derstanding of biological neural networks, or for solving ar- tificial intelligence problems without necessarily creating a model of a real biological system.
The real, biological nervous system is highly complex and in-
cludes some features that may seem superfluous based on an
understanding of artificial networks.
Real life applications and the tasks to which artificial neural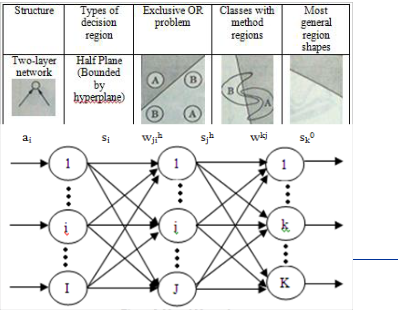
networks include classification, including pattern and se- quence recognition; novelty detection and sequential decision making. Figure 5 shows geometrical interpretation of pattern classification and decision regions for different perceptron networks.
Figure 5: Neural Networks
Figure 6: Simplified view of a 3 layer feed-forward
artificial neural network
Back-propagation is a common method of teaching artificial neural networks how to perform a given task.
It is a supervised learning method, and is a generalization of the delta rule.
It requires a teacher that knows, or can calculate, the desired
output for any input in the training set.
It is most useful for feed-forward networks (networks that
have no feedback, or simply, that have no connections that
loop).
The term is an abbreviation for "backward propagation of
errors".
Back-propagation requires that the activation function used by the artificial neurons (or "nodes") be differentiable.
![]() Given a set of input-output patterns (al, bl), l= 1, 2, … L,
Given a set of input-output patterns (al, bl), l= 1, 2, … L,
where the lth input vector al = (al1, al2, …., all)T and the lth output vec- tor bl = (bl1, bl1, … , bll)T.
![]() Assume only one hidden layer and initial settings of weights to be arbitrary.
Assume only one hidden layer and initial settings of weights to be arbitrary.
![]() Assume input layer with only linear units.
Assume input layer with only linear units.
![]() Then the output signal is equal to the input activation value for each
Then the output signal is equal to the input activation value for each
of these units. Let η be the learning rate parameter.
![]() Let a = a(m) = al and b = b(m) = bl.
Let a = a(m) = al and b = b(m) = bl.
![]()
![]() Activation of unit i in the input layer, xi = ai(m).
Activation of unit i in the input layer, xi = ai(m).
![]() Activation of unit j in the hidden layer, xjh = wjih xi
Activation of unit j in the hidden layer, xjh = wjih xi
![]()
Output signal from the jth unit in the hidden layer, sjh = fjh (xjh) Activation of unit k in the output layer, xko = wkj sjh
Output signal from the kth unit in the output layer, sko = fko (xko) Error term for the kth output unit, δko = (bk – sko) fko
Updates weights on output layer, wkj (m + 1) = wkj (m) + η δkosjh
Error term for the jth hidden unit, δjh = fjh ![]() δko wkj
δko wkj
![]()
Updates weights on the hidden layer, wjih (m + 1) = wjih (m) + η δjhaj
![]()
Calculate the error for the lth pattern, El = ½ (blk – sko)2
R © 2012
ww.ijser.org
International Journal of Scientific & Engineering Research,Volume 3, Issue 6, June-2012 4
ISSN 2229-5518
![]() Total error for all patterns, E = El
Total error for all patterns, E = El
Apply the given patterns one by one, may be several times, in some random order and update the weights until the total error reduces to an acceptable value.
Fuzzy logic is a form of many-valued logic derived from fuzzy set theory to deal with reasoning that is fluid or approximate rather than fixed and exact. In contrast with "crisp logic", where binary sets have two-valued logic, fuzzy logic variables may have a truth value that ranges in degree between 0 and 1. In simple words we can say fuzzy logic is a super set of con- ventional (boolean) logic that has been extended to handle the concept of partial truth--the truth values between completely true and completely false. Furthermore, when linguistic va- riables are used, these degrees may be managed by specific functions.
Because fingerprint patterns are fuzzy in nature integrating the fuzzy encoder with back-propagation neural network (BPNN) as a recognizer which has variable fault tolerances for fingerprint recognition can help recognition in huge.
In the field of artificial intelligence, neuro-fuzzy refers to com- binations of artificial neural networks and fuzzy logic. Human brain recognition system for biometric works neuro-fuzzily. Neuro-fuzzy hybridization results in a hybrid intelligent sys- tem that synergizes these two techniques by combining the human-like reasoning style of fuzzy systems with the learning and connectionist structure of neural networks. Neuro-fuzzy hybridization is widely termed as Fuzzy Neural Network (FNN) or Neuro-Fuzzy System (NFS) in the literature.
Both neural networks and fuzzy systems have some things in common. They can be used for solving a problem (e.g. pattern recognition) if there does not exist any mathematical model of the given problem. They solely do have certain disadvantages and advantages which almost completely disappear by com- bining both concepts.
Neural networks can only come into play if the problem is
expressed by a sufficient amount of observed examples. These
observations are used to train the black box. On the one hand no prior knowledge about the problem needs to be given. On the other hand, however, it is not straightforward to extract comprehensible rules from the neural network's structure.
On the contrary, a fuzzy system demands linguistic rules in-
stead of learning examples as prior knowledge. Furthermore the input and output variables have to be described linguisti- cally. If the knowledge is incomplete, wrong or contradictory, then the fuzzy system must be tuned. Since there is not any
formal approach for it, the tuning is performed in a heuristic way. This is usually very time consuming and error-prone.
Compared to a common neural network, connection weights and propagation and activation functions of fuzzy neural net- works differ a lot.
Although there are many different approaches to model a
fuzzy neural network most of them agree on certain characte-
ristics such as the following:
![]() A neuro-fuzzy system based on an underlying fuzzy sys-
A neuro-fuzzy system based on an underlying fuzzy sys-
tem is trained by means of a data-driven learning method derived from neural network theory. This heuristic only takes into account local information to cause local changes in the fundamental fuzzy system.
![]() It can be represented as a set of fuzzy rules at any time of
It can be represented as a set of fuzzy rules at any time of
the learning process, i.e., before, during and after. Thus the system might be initialized with or without prior knowledge in terms of fuzzy rules.
![]() The learning procedure is constrained to ensure the se-
The learning procedure is constrained to ensure the se-
mantic properties of the underlying fuzzy system.
![]() A neuro-fuzzy system approximates a n-dimensional un- known function which is partly represented by training examples. Fuzzy rules can thus be interpreted as vague prototypes of the training data.
A neuro-fuzzy system approximates a n-dimensional un- known function which is partly represented by training examples. Fuzzy rules can thus be interpreted as vague prototypes of the training data.
![]() A neuro-fuzzy system is represented as special three-layer
A neuro-fuzzy system is represented as special three-layer
feedforward neural network as it is shown in Figure 6.
o The first layer corresponds to the input variables.
o The second layer symbolizes the fuzzy rules.
o The third layer represents the output variables.
o The fuzzy sets are converted as (fuzzy) connection weights.
o Some approaches also use five layers where the fuzzy sets are encoded in the units of the second and fourth layer, respectively. However, these models can be transformed into a three-layer architecture.
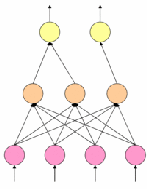
Figure 7: The architecture of a neuro-fuzzy system
IJSER © 2012
International Journal of Scientific & Engineering Research,Volume 3, Issue 6, June-2012 5
ISSN 2229-5518
There are many methods in the literature for fingerprint iden- tification using minutia as a feature.
But there is not much work done using soft computing tool
such as neural network.
We are proposing a new method of fingerprint identification
system where the minutia will be taken as feature to train the
neural network system.
As a three layer neural network may not be useful enough to
map a fingerprint image perfectly to a certain user, we are planning to implement a four (or even more) layer neural network.
And then finally add fuzzy logic to make the system more flexible.
![]()
Cut effective area of a fingerprint image
Block-wise divide the image
Extract minutia of each block
Calculate the number of minutia for each block and gra-
dient for each minutia
![]() Use this number and the respective gradient values as a
Use this number and the respective gradient values as a
feature to train the back propagation neural network
![]() Use 40% data (fingerprint image of a same person of same finger) to train the system
Use 40% data (fingerprint image of a same person of same finger) to train the system
Later on incorporate fuzzy logic with this system to decrease error rate.
We are planning to use fuzzy logic in input as well as output layer, and so making the system at least a 5 layer network (in- put fuzzy layer, input of actual neural network, hidden layer, output layer of neural network, output layer of fuzzy logic)
Figure 8: Simplified version of our proposed algorithm
Most of the fingerprint recognition systems rely on minutiae matching algorithms. Although minutiae based techniques are
widely used because of their temporal performances, they do not perform so well on low quality images and in the case of partial fingerprint they might not be used at all. Therefore, when comparing partial input fingerprints to pre-stored tem- plates, a different approach is needed. Soft computing can help to achieve better result for these types of case. Different soft computing tools can be applied in different phases of pre- processing also.
[1] X. Jiang andW. Yau, “Fingerprint minutiae matching based on the local and global structures,” in Proc. 15th Int. Conf. Pattern Recognition, vol.
2, Barcelona, Spain, Sep. 2000, pp. 1042–1045.
[2] D. K. Isenor and S. G. Zaky, “Fingerprint identification using graph
matching,” Pattern Recognit., vol. 19, no. 2, pp. 113–122, 1986.
[3] A. K. Jain, L. Hong, and R. Bolle, “On-line fingerprint verification,”
IEEE Trans. Pattern Anal. Mach. Intell., vol. 19, no. 4, pp. 302–314, Apr.
1997.
[4] A. K. Jain, L. Hong, S. Pankanti, and R. Bolle, “An identity authentica- tion system using fingerprints,” Proc. IEEE, vol. 85, no. 9, pp. 1365–1388, Sep. 1997.
[5] N. Ratha, S. Chen, and A.K. Jain, “Adaptive Flow Orientation Based
Feature Extraction in Fingerprint Images,” Pattern Recognition, vol. 28, no.
11, pp. 1,657-1,672, 1995.
[6] K. Karu and A.K. Jain, “Fingerprint Registration,” Research Report,
Michigan State Univ., Dept. of Computer Science, 1995.
[7] A. Almansa and L. Cohen, “Fingerprint image matching by minimiza- tion of a thin-plate energy using a two-step algorithm with auxiliary va- riables,” in Proc. IEEE 5thWorkshop Applications Computer Vision, Dec. 2000, pp. 35– 40.
*8+ Kalyani Mali and Samayita Bhattacharya, “Soft Computing Approach towards Fingerprint Recognition”, Proc of National Conference on Recent Trends in Soft Computing (NCRTSC 2011), ISBN 978-93-81006-03-0, pp 95-
99.
IJSER © 2012