The research paper published by IJSER journal is about Robust Image Watermarking using DCT & Wavelet Packet Denoising 1
ISSN 2229-5518
Robust Image Watermarking using DCT &
Wavelet Packet Denoising
Mr.D.V.N.Koteswara Rao#1,Y.Madhuri#2, S.V.Rajendra Kumar#3 ,Y.V.Suresh Babu#4
#1Assistant Professor, Department of Electronics and Communication Engineering, SACET,Chirala
#2,3,4Department of Electronics and Communication Engineering, SACET,Chirala
Email: dvnkrao@gmail.com
Abstract
In this paper, a new robust digital image watermarking algorithm based on Joint DWT-DCT Transformation is proposed. A binary watermarked logo is scrambled by Arnold cat map and embedded in certain coefficient sets of a 3-level DWT transformed of a host image. Then, DCT transform of each selected DWT sub-band is computed and the PN-sequences of the watermark bits are embedded in the middle frequencies coefficients of the corresponding DCT block. In extraction procedure, the watermarked image, which maybe attacked, is pre-filtered by combination of sharpening and Laplassian of Gaussian filters to increase distinction between host image and watermark information. Subsequently, the same procedures as the embedding process is used to extract the DCT middle frequencies of each sub-band. Finally, correlation between mid-band coefficients and PN- sequences is calculated to determine watermarked bits. Experimental results show that high imperceptibility is provided as well as higher robustness against common signal processing attacks. In compare to current watermarking algorithms which are based on the joint of DWT-DCT, proposed system Is achieved significantly higher robustness against enhancement and noise addition attacks.
Keywords
Digital image watermarking, Discrete Wavelet Transform (DWT), Discrete Cosine Transform (DCT), Arnold Cat Map, Unsharp Filter, Laplassian of Gaussian Filter (LoG).
1. Introduction
The fast development of the Internet in recent years has made it possible to easily create, copy, transmit, and distribute digital data. Consequently, this has led to a strong demand for reliable and secure copyright protection techniques for digital data. Digital watermarking has
been proposed as valid solution for this problem. The purpose of the watermark is to embed some additional information about the digital data without visibly modifying it. In order to be successful, the watermark should be invisible
and robust to premeditated or spontaneous modification of the
image. It should be robust against common image processing operations such as filtering, additive noise, resizing, cropping etc and common image compression techniques. If the watermark is placed in perceptually significant coefficients of the image, the robustness against image distortion is better achieved. These coefficients do not change much after common image processing and compression operations. Also, if these coefficients are destroyed, the reconstructed image is different from the original image and the digital watermark become irrelevant. Although, embedding the watermark in perceptually significant coefficients could alter the perceived visual quality of the image. Thus, two essential prerequisites for a powerful watermarking scheme, robustness and invisibility conflict with each other .
Watermarking techniques can be categorized in different ways. They can be classified according to the type of watermark being used, i.e., the watermark may be a visually recognizable logo or a sequence of random numbers. Another classification is based on domain which the watermark is applied i.e., the spatial domain or the transform domain. The earlier watermarking techniques were almost in spatial domain. Spatial domain techniques are not resistant enough to image compression and other image processing . Transform domain watermarking schemes like those based on the discrete cosine transform (DCT) , the discrete wavelet transform (DWT) typically provide higher image imperceptibility and are much more robust to image manipulations. In these domain watermark is placed in perceptually significant coefficients of the image. However, DWT has been used more frequently in digital image watermarking due to its time/frequency decomposition characteristics, which resemble to the theoretical models of the human visual system .
In order to further performance improvements in DWT-based digital image watermarking algorithms could be obtained by jointing DWT with DCT . The reason of applying two transform is based on the fact that jointed transform could make up for the disadvantages of each other, so that effective watermarking approaches could acquire.
Fotopoulos and Skodras decompose the original image
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Robust Image Watermarking using DCT & Wavelet Packet Denoising 2
ISSN 2229-5518
into four bands using the Haar wavelet, and then perform DCT on each of the bands; the watermark is embedded into the DCT coefficients of each band. Serkan Emek and Melih Pazarci compared image dependent and additive blind watermarking algorithms that embed a watermark in the DWT-DCT domain by taking the properties of the HVS into account . The image dependent algorithm modulates the watermarking coefficients with original mid-frequency DWT-DCT coefficients . Ali Al-Haj described a combined DWT-DCT digital image watermarking algorithm that embed the watermark in the first and second level of DWT coefficient sets of the host image, followed by the application of DCT on the selected DWT coefficient sets. However, robustness of common DWT and DCT transform methods is increased by previous hybrid method; despite, their robustness against noise and blurring attack is not acceptable. In order to solve this problem, a new image watermarking algorithm based on jointed DWT-DCT method is presented in this paper. In proposed method, Watermarking is done by altering the wavelets coefficients of middle frequency coefficient sets of 3-levels DWT transformed host image, followed by the application of the DCT transform on the selected coefficient sets. Difference between Al-Haj’s method and proposed is in selection of sub-band for embedding watermark and novel preprocessing before extraction procedure. Al-Haj chosen HL sub-band in 2-level dwt transformed to performing block DCT on them, But proposed method use all of the HL frequency sub-band in the middle frequency coefficient sets LHx and HLx in 3-levels DWT transformed image. By this algorithm, coarser level of DWT in terms of imperceptibility and robustness is chosen to apply 4×4 block-based DCT on them, and consequently higher imperceptibility and robustness can be achieved. Also, pre- filtering operation is used before extraction of the watermark, sharpening and Laplacian of Gaussian (LoG) filtering, is used to increase different between information of watermark and hosted image. .
2.2. The DWT Transform
Wavelet transform decomposes an image into a set of band limited components which can be reassembled to reconstruct the original image without error. Since the bandwidth of the resulting coefficient sets is smaller than that of the original image, the coefficient sets can be down sampled without loss of information. Reconstruction of the original signal is accomplished by up sampling, filtering and summing the individual sub bands. For 2-D images, applying DWT corresponds to processing the image by 2-D filters in each dimension. The filters divide the input image into four non- overlapping multi-resolution coefficient sets, a lower resolution approximation image (LL1) as well as horizontal (HL1), vertical (LH1) and diagonal (HH1) detail components. The sub-band LL1 represents the coarse-scale DWT coefficients while the coefficient sets LH1, HL1 and HH1 represent the fine scale of DWT coefficients. To obtain the next coarser scale of wavelet coefficients, the sub-band LL1 is further processed until some final scale N is reached. When N
2. Common Frequency Domain Method (DWT and
DCT)
The DCT and DWT transforms have been widely used in many digital watermarking applications. In this section, we introduce the two transforms briefly, and outline their relatedness to the implementation of digital watermarking.
2.1. The DCT Transform
The discrete cosine transforms is technique for converting a signal into elementary frequency components [11]. It represents an image as a sum of sinusoids of varying magnitudes and frequencies. With an input image, x, the DCT coefficients for the transformed output image, y, are computed according to Equation.1 shown below. In the equation, x, is the input image having N x M pixels, x (m, n) is the intensity of the pixel in row m and column n of the image, and y (u, v) is the DCT coefficient in row u and column v of the DCT matrix.
The popular block-based DCT transform segments image non- overlapping blocks and applies DCT to each block. This results in giving three frequency coefficient sets: low frequency sub-band, midfrequency-sub-band and high frequency sub-band. DCT-based watermarking is based on two facts. The first fact is that much of the signal energy lies at lowfrequencies sub-band which contains the most important visual parts of the image. The second fact is that high frequency components of the image are usually removed through compression and noise attacks. The watermark is therefore embedded by modifying the coefficients of the middle frequency sub-band so that the visibility of the image will not be affected and the watermark will not be removed by compression .
is reached we will have 3N+1 coefficient sets consisting of the multi-resolution coefficient sets LLN and LHX, HLX and HHX where x ranges from 1 until N.
Due to its excellent spatio-frequency localization properties, the DWT is very suitable to identify the areas in the host image where a watermark can be embedded effectively. In particular, this property allows the exploitation of the masking effect of the human visual system such that if a DWT coefficient is modified, only the region corresponding to that coefficient will be modified. In general most of the image energy is concentrated at the lower frequency coefficient sets LLx and therefore embedding watermarks in these coefficient sets may degrade the image significantly. Embedding in the low frequency coefficient sets, however, could increase robustness significantly. On the other hand, the high frequency coefficient sets HHx include the edges and textures of the image and the human eye is not generally sensitive to changes in such coefficient sets. This allows the watermark to be embedded without being perceived by the human eye. The agreement adopted by many DWT-based watermarking
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Robust Image Watermarking using DCT & Wavelet Packet Denoising 3
ISSN 2229-5518
methods, is to embed the watermark in the middle frequency coefficient sets HLX and LHX is better in perspective of imperceptibility and robustness .
3. Embedding Algorithm
The main strength offered by transform domain techniques is that they can take advantage of special properties of alternate domains to address the limitations of spatial domain or to support additional features. The purpose of this paper is to use joint of the wavelet and cosine transform to embed watermark information in most robust and imperceptible part of image. The wavelet transform has a number of advantages over the other transforms, namely the DCT: The DWT is a multi- resolution description of an image: the decoding can be processed sequentially from low resolution to higher resolutions. The DWT is closer to human visual system than DCT. Hence, the artifacts introduced by wavelet domain coding with high compression ratio are less annoying than those introduced at the same bit rate by DCT.
In the propose method, we take these benefit of DWT to chose the most proper sub-bands in case of robustness and imperceptibility. Then, the block based DCT is applied on these selected band to embed watermark in middle frequencies of each block to augment further robustness of watermarked image against different attacks. In fact with utilizing joint of the two common frequency methods, we could take the advantageous of both two algorithms to increase robustness and imperceptibility. At the same time, we could suppress the effect of attack that designed for each of these frequency methods such as jpeg and jpeg2000 compression.
This algorithm has been implemented in MATLAB 7 using the wavelet, image processing and statistic toolboxes, and XnView and Photoshop image editing software.
3.1. Watermark Scramble
The embedded watermark in the algorithm is not a traditional one dimension pseudo-random sequence, but a meaningful two value image. The watermark in this paper is scrambled firstly in order to guarantee the embedded watermark against clipping, re-sampling and so on and improve the watermark’s robustness. Image scrambling is using some algorithm to scramble every pixel in one image, but the sum of pixels is invariable. Because watermark scrambling can eliminate watermark’s pixels of spacing relativity, the watermark’s robustness against image clipping operation will be improved. After the watermark processed by scrambling algorithm, even if some attacker can detect the watermark signal, he cannot recover the original watermark without the scrambling algorithm. Even if achieving the scrambling algorithm, he still does a great deal of test to recover the original watermark. In this way, the watermark of secrecy and security can be strengthened further. Image scrambling methods proposed already are Fass curve, Gray code, Arnold transform and
magic square method and so on. In this paper, Arnold transform is chosen as pretreatment method for watermark signal. This method is intuitionistic, simple, periodic and easy to use.
Through mapping, cat’s face image become from clear to blurry. In fact, this is the pixels’ position removing, and this algorithm is mapping one by one. From point of view of sample theory, digital image can be seeing as a two dimension discrete point array sampled according to certain interval and certain strategy in the two dimension continuous surface, that is to say, a image array.
3.2. Embedding Algorithm
The main strength offered by transform domain techniques is that they can take advantage of special properties of alternate domains to address the limitations of spatial domain or to support additional features. Watermarking process is started by applying 3-leveles DWT on the host image. The agreement adopted by many DWT-based watermarking methods is to embed the watermark in the middle frequency sub-bands HLx and LH x is better in perspective of imperceptibility and robustness.
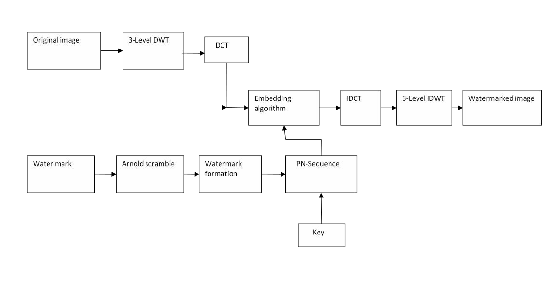
Consequently, HLx coefficient sets in level three is chosen to make to increase the robustness of our watermark against common watermarking attack, specially adding noise and blurring attacks, at little to no additional impact on image quality. Then, the block base DCT is performed on these selected DWT coefficient sets and embed pseudorandom sequences in middle frequencies. The watermark embedding procedure is represented in Figure 2 followed by a detailed explanation.
Step 1: Perform DWT on the host image to decompose it into four non-overlapping multiresolution coefficient sets: LL1, HL1, LH1 and HH1.
Step 2: Perform DWT again on two HL1, LH1, coefficient sets to get eight smaller coefficient sets and choose four coefficient sets: HL12, LH12 , HL22 and LH22 .
Step 3: Perform DWT again on four coefficient sets: HL12, LH12, HL22 and LH22 to get sixteen smaller Coefficient sets and choose four coefficient sets: HL13 , LH13, HL23 and LH23. Step 4: Divide four coefficient sets: HL13, LH13, HL23 and LH23 into 4 x 4 blocks.
Step 5: Perform DCT to each block in the chosen coefficient sets (HL13, LH13, HL23 and LH23). These coefficients sets are chosen to inquire both of imperceptibility and robustness of algorithms equally.
Step 6: scramble the watermark signal with Arnold algorithm for key times and gain the scrambled watermark Ws (i , j), key times can be see as secret key.
Step 7: Re-formulate the scramble watermark image into a vector of zeros and ones.
Step 8: Generate two uncorrelated pseudorandom sequences by a key. One sequence is used to embed the watermark bit 0 (PN_0) and the other sequence is used to embed the watermark bit 1 (PN_1). Number of elements in each of the
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Robust Image Watermarking using DCT & Wavelet Packet Denoising 4
ISSN 2229-5518
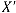
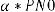
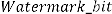


two pseudorandom sequences must be equal to the number of mid-band elements of the DCT-transformed, DWT coefficient

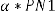
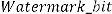


sets. 
Step 9: Embed the two pseudorandom sequences, PN_0 and
PN_1, with a gain factor a in the DCT transformed 4x4 blocks
of the selected, DWT coefficient sets of the host image. Instead of embedding in all coefficients of the DCT block, it applied only to the mid-band DCT coefficients. If we donate X as the matrix of the mid-band coefficients of the DCT
transformed block.
Step 10: Perform inverse DCT (IDCT) on each block after its mid-band coefficients have been modified to embed the watermark bits as described in the previous step.
Step 11: Perform the inverse DWT (IDWT) on the DWT transformed image, including the modified coefficient sets, to produce the watermarked host image.
4. Extracting Procedure
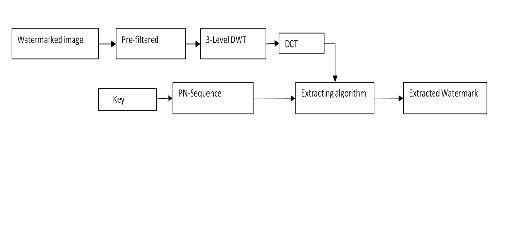
The joint DWT-DCT algorithm is a blind watermarking algorithm, and thus the original host image is not required to extract the watermark. Execration algorithm is the same as embedding one, and pre-filtering is used before applying Step1:perform combination of two filters as pre-filtering operation.
Combination of these two filters is helped to concentrate on finding information of watermark by degrading effect of one watermarked part of watermarked image and increasing watermarked part of it.
Step 2: Perform DWT on the pre-filtered watermarked image to decompose it into four non- overlapping multi-resolution coefficient sets: LL1, LH1 ,HH1 and HL1.
Step 3: Perform DWT again on two coefficient sets HL1 and
LH1 to get eight smaller coefficient sets and choose four coefficient sets: HL12 ,LH12, HL21and LH22.
Step 4: Perform DWT again on four coefficient sets: HL12, LH12, HL22 and LH22 to get sixteen smaller coefficient sets and choose four coefficient sets: HL13, LH13, HL23 and LH23 .
DWT transform to better separate watermark information from host image. The watermark extraction procedure is shown in Figure 4 and described in details in the following steps.
Step 5: Divide four coefficient sets: HL13, LH13, HL23 and
LH23 into 4 x 4 blocks.
Step 6: Perform DCT on each block in the chosen
coefficient sets (HL13, LH13, HL23 and LH23).
Step 7: Regenerate the two pseudorandom sequences (PN_0
and PN_1) using the same key which used in the watermark embedding procedure.
Step 8: For each block in the coefficient sets: HL13, LH13,HL23 and LH23 calculate the correlation between the mid-band coefficients and the two generated pseudorandom sequences (PN_0 and PN_1). If the correlation with the PN_0 was higher than the correlation with PN_1, then the extracted watermark bit is considered 0, otherwise the extracted watermark is
considered 1.
IJSER © 2012 http://www.ijser.org
The research paper published by IJSER journal is about Robust Image Watermarking using DCT & Wavelet Packet Denoising 5
ISSN 2229-5518
Step 9: The scrambled watermark is reconstructed using the extracted watermark bits.
Step 10: scramble the extracted watermark with Arnold algorithm with the same key times and gain the scrambled
watermark W (i, j), and compute the similarity between the original and extracted watermarks.
5. Experimental results
In this section the results of our study is shown. Several experiments are done to evaluate the effectiveness of the presented watermarking algorithm. In this experiment, a
32×32 binary image is taken as the watermark of images. By using a row-major algorithm, the scrambled watermark image can be transformed into a binary sequence with a length of
1024. Additionally, lena image of size 512×512 is taken respectively. Note that I and J are set to 512. In the proposed
method, the four selected 64×64 DWT sub-band is divided into 4×4 blocks giving a total of 1024 blocks. With this number of blocks we can embed 1024 bit in our image. The performance of the watermarking methods under consideration is investigated by measuring their imperceptible and robust capabilities. For the imperceptible capability, a quantitative index, Peek Signal-to-Noise Ratio (PSNR).

Original Image
Watermarked Image
IJSER © 2012 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 3, Issue 5, May-2012 6
ISSN 2229-5518

WATERMARKED IMAGE WITH GAUSSIAN NOISE
Extracted watermark with Guassian noise
.'d: :C:
..'.;;;;.:

SALT & PEPPER
t£:.
...t·'.+:..._:;

JPEG 75QUAL.
SCALING 200%
SAC
The research paper published by IJSER journal is about Robust Image Watermarking using DCT & Wavelet Packet Denoising 7
ISSN 2229-5518
6. Conclusion
Our study focused on presenting a joint DWT-DCT digital image watermarking algorithm. Proposed method exploits strength of two common frequency domains method; DCT and DWT, to obtain further imperceptibility and robustness. The idea of inserting watermark in the combined transform is based on the fact that jointed transform could eliminate the drawback of each other. then, an effective watermarking method could obtains. In this paper, watermark is embedded in most robustand imperceptible parts of image than previous methods. Watermarking is done with embedding the watermark in the special middle frequency coefficient sets of
3- levels DWT transformed of a host image, followed by computing 4×4 block-based DCT on the selected DWT coefficient sets. In extraction procedure, pre-filtering operation, sharpening and Laplasian of Gaussian (LoG) filtering, is used to better detect watermark information from host image. Then, the same procedure as embedding algorithm is applied on pre-filtered attacked image to extract middle frequency coefficients of each DCT block. Afterwards, bits of watermark are extracted by comparing correlation between PN- sequences and these coefficients. Implementation results show that the imperceptibility of the watermarked image is acceptable. Presented method is tested by most of the common image processing attack such as: different size of gaussian filtering as an enhancement attack, adding salt and paper noise, scaling with two common factors: 50% and 75%, cropping, and compression attack. Specially, in case of adding noise and enhancement attack, proposed method show a significant improvement in robustness compare to previous DWT-DCT based method. Inasmuch as, the watermarks can be extracted from the other image processing attack with lower MAE values, proposed method is more robust compare to previous method, in spite of having the same imperceptibility and complexity.
7. References
[1] Cox, I., M. Miller and J. Bloom,” Digital Watermarking,”
Academic Press, USA, 2002.
[2] Potdar, V., S. Han and E. Chang,” A Survey of Digital Image Watermarking Techniques,” in Proc. of the IEEE International Conference on Industrial Informatics, pp: 709-
716, Perth, Australia 2005.
[3] Chu, W, "DCT-Based Image Watermarking Using
Subsampling," IEEE Trans. Multimedia, 5(1): 34-38, 2003.
[4] Lin, S. and C. Chin, "A Robust DCT-based Watermarking for Copyright Protection," IEEE Trans. Consumer Electronics,
46(3): 415-421, 2000.
[5] Deng, F. and B. Wang, "A novel technique for robust image watermarking in the DCT domain," in Proc ofthe IEEE
2003 Int. Conf. on Neural Networks and Signal Processing, vol. 2, pp: 1525-1528, 2003.
[6] Hsieh, M., D. Tseng, and Y. Huang, "Hiding Digital Watermarks Using Multi-resolution Wavelet Transform," IEEE Trans. on Industrial Electronics, 48(5): 875-882, 2001. [7] Reddy, A. and B. Chatterji. "A New Wavelet Based Logo- watermarking Scheme," Pattern Recognition Letters, 26(7):
1019-1027, 2005.
[8] Tay, P. and J. Havlicek, "Image Watermarking Using Wavelets," in Proc. of the IEEE Midwest Symposium on Circuits and Systems, pp: 258-261, Oklahoma, USA, 2002.
[9] Vetterli, M. and J. Kovacevic, “Wavelets and Subband
Coding”. Prentice Hall, USA, 1995.
[10] Wolfgang, R., C. Podilchuk and E. Delp, "Perceptual Watermarks for Digital Images and Video," Proc. of the IEEE, vol. 87, no. 7, pp: 1108-1126, 1999.
IJSER © 2012 http://www.ijser.org





