International Journal of Scientific & Engineering Research, Volume 4, Issue 7, July-2013
ISSN 2229-5518
1
Richa Rawat , Anurag Jain
ABSTRACT— Network and host intrusion detection systems monitor malicious activities and the management station is a technique that generates reports. Security for all networks is becoming a big problem. Hackers and intruders higher number of successful efforts to bring down the company’s networks and web services. Intrusion detection system, the availability of an attack and to protect the integrity of the data used for the detection of attacks. In this paper, we use a variety of feature reduction techniques for intrusion detection system (IDS) to compare the performance of classifiers. There are two phases in certain ways, in the first phase will improve decision tree and SVM classifiers for best results and the second phase will boost both the decision tree and SVM classifiers, and detect more than a single class classifier system.
Keywords— Intrusion Detection System (IDS), Boosting, decision tree and support vector machine (SVM)
—————————— —————————
Computer security, privacy, reliability, and availability of a computer system and its resources to protect the ability of reference. Unauthorized access to a computer system, modification, and use of the refuse safely to protect data and resources. Infiltration of the security aspects of a computer system that tries to attack the type of tolerance. For network intrusion detection system, a number of researchers, the most powerful methods for extracting information hidden in large data sets from the data mining methods, implemented. Due to a large amount of processing required for network traffic, we can use data mining techniques. To apply data mining techniques in intrusion detection, preprocessing data collected by the first step. Then, in a special format for exchanging data mining process. After that, the configuration as is used for classification and clustering. Rule-based classification model, a decision tree-based, Bayesian network-based or based on the neural network.
————————————————
Richa Rawat, Department of Computer Science Engg., RGTU University, Radharaman Institute of Technology and Science, INDIA,
8989487055 (e-mail: er.richa22@gmail.com).
Anurag Jain, HOD, Department of Computer Science, RGTU University, Radharaman Institute of technology and science, INDIA, (e-mail: anurag.akjainr@gmail.com).
The data mining technology to ensure accuracy and efficiency in the search process, because any intrusion will not be missed, while ensuring real-time data from the network. Data mining approaches for intrusion prevention mechanisms to help. They have two models of attacks to identify known and previously unknown. Suspicious activities to our Internet or system if it is classified as an intrusion.
This paper is structured as follows: Section 2 gives the details of intrusion detection system. Section 3 gives the details of Decision Tree and SVM. Section 4 gives the details of ensemble techniques used in this paper Section 5 Conclusion.
When creating an IDS data collection, pre-processed data, invasive validation report, and respond to such problems, we need to consider. Among them, the most important is the recognition of the invasion. Audit information is compared with search models, harsh or mild description of behavior patterns, so that both successful and failed attempts can be recognizable. With Denning first proposed model of intrusion detection in 1987, many research efforts have focused on how to efficiently and accurately detect build models. Between the late 1980s and early 1990s, a combination of expert systems and statistical approaches have been very popular. Discovery models were formed from the domain over knowledge of safety experts. From mid 1990s to the late 1990s, acquiring knowledge about normal or abnormal behavior evolved from
IJSER © 2013 http://www.ijser.org
htemational..bumalof Scientiic & Blgineering Research,\A:IIume 4, Issue 7, JJiy-2013
ISSN2229-5518
2
manual to automatic A
leaming methods have be
a a setof training data.
![]()
(-- -.".:lc"

I lr.tllft
addne c model
As a novel attadc detectim possible intrusions of the state. Otanges within its causes and symptoms without getting re=gti.ed. User priv;Jeges of bad langusge is the ability to
make a sean::h. The biggest disadvantage a this method is an
impatmtsign of a false alann.
4.LITERATURE SURVEY
Wolz...g et Al[.14).In this
paper
, intrusion d""dion system
, I
Mnlir<'Ytlltll
,..----..,
·- ./ 
J1,.1,.,.....i.mr i.u

M1l1h
![]()
hlnl'hn
Jk,'l)}l:tkn
f

![]()
4.•omuqo•l
in the state of the art mmputational intelligence methods of researclt. The review of the evolution of artificial neural net.=b, fuzzy syst..m;, methods of calculation method of artificial immune systems in the core and the sec::ret to a range of opportunilios. However, this method of study that reveals the advantages and disadvantages of eac::h of them. Soft Computing It will be adjusled in sud\ a way that their disadvantages rothis method is the ability to a:mbine p r, thus offering Solutions. Scft Computing as a subject included in the we the:re:fore this survey. The contributions of the
Fit;1:Orgonhoa>nn.,aeloflDS
3. TYPES OF THE INTRUSION DETECTIOII
Intrusion deleclim can be a:msidered as a clasoification. Event a:mtrol process within a oompube::r system or network is located, and analyzing lhe dtaracte:ristiao of intrusions is known as intrusion detection. Here we describe two types of intrmims : signature based intrusion detectim and novel intrmim detection [14].
l.1Misuse intrusion detection
Through a well delined altack-p.,_s that u..v.eak system and applia tion software to identify invasion. These models are encoded inadvanced and were used for comparisonof user behavior for intrusion detection [15]. Misuse-based IDS are abo named as signature-l:esed or pattern l:esed IDS, which are used tomake lhe <tisa>Very of certain things beingforoed ink> l:esed on the -do; that stored in the knowledge-base with very-low falsethings greater than ...-o [1'7].
3.1.1 Advantage d Misuse (Signature) Detection
A very low rate of !:abe alanrs, simple algorithms,. it is not difficult work of art attack signatures,. implementation easy
and usually minimal use a system resou:r<&. Sane of the
disadvantages of Ibis type:of seardt;attacks on lhe lmowled.ge
of lhe changeto lhe new type of problems.
l.2 Anomaly intrusion detection
To go beyond thenamal usage behavior in the useofdesigt. Commonly used in the design a a user or program from the
O'U and 10 aclivilios, ror example, the syst.m !i.atures by the sl:alistia lmeasures [15].
3.2.1 Advantages of the anomaly detection
researcll work short and compared systematically, so that our dearly, lhe existing researd\ chsllonges, define and highlight promising the new researdt indicates. It is e:xpec:ted. that Ibis survey will serve Literature as a useful guide through the maze.
Ssuaihya PeddabuhigAri et Al. [15} The resean::h support vector madtines (SVM) and conducted experiments with this model compared with lhe decision tree pe:rfonnanoe. Empirical results suggest that the decision tree ve:rifia tion
U2R and R2L cla..,sror lhe aa:uracyofbettor than SVM when
beth the general clas; fa the fust dOG class decision tree to provide aoc.Lrale and slightly wotse than the aoc::u:raq- of the decision tree. The result also shaws that the testing and training from time to timeatSVM classifie:m are better than.
THAKARE S.P et Al [UJ This paper !""'P"Ge& a signature-based intrusion detec:tion system it is paosible that within the network detects intrusion behavior develops. Fade module is inserted into the system further investigate the decision obvious for lhe attac:k,. will be using lhe fuzzy inference approach.
Dewsut MA. Fs: .ridet Al. £1n In this paper,a new algorithm fa adaptive intrusion detection and naive Bayesian is bcmting dasoifier, which is the intrusion detection with !:abe positive detection rate for an ensemble approach based on
bcoGting ro improve the presentation. The main ol::jective of
Ibis paper improves the intrusim detection simple Bayesian
dasoifier resuHs.
S.D...grr .tt. Al[ll In this paper propooed a novel approach,of Ensemble Classilior. Comparing with other classifior. The Ensemble Oasoifier method ac::hieves distinct features as; it
USER ®2013 ht1p:Hwww.ijser.org
IInnteternrantaiotniaolnJaoluJrnoarl noaf Sl coifenSticfiicen&tEifnigcin&eeErinnggiRneeseerairncgh, RVoelsuemaerc4h, ,IVssouleu7m, Jeu4ly,-2Is0s1u3e 6, June 2013
ISSN 2229-5518
ISSN 2229-5518 3
detects correct class of attack if detected and it informs the user
about the attack with alert generation feature of the system.
Anazida Zainal et. al. [2] In this paper they have demonstrated an improved classification to the intrusion detection problem by performing two layer data reduction and ensemble classifiers.
Jashan Koshal et. al. [4] In this paper Framework defines the system as a core technology combines two classification algorithms. The test is performed on the NSL KDD dataset, the numerical results show that the system has the advantage of slightly over 99 KDD Cup. Low false alarm rate and higher accuracy and less time is required by the proposed architecture. However, the label was not an attack, the system is just a series of emergency or general connection.
We related to different techniques used to implement the process and IDS. Classification of these methods is very difficult because in the actual implementation of the system, the connection with this method can be used [17].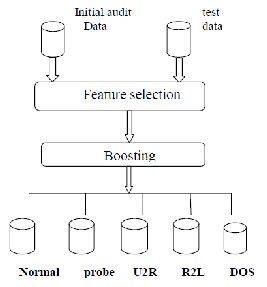
Fig 2 : Experimental Flow
There is a group of records (training set) each record has in it a group of attributes, one of the attributes is the class. Generally, certain the data set is separated into training and test sets, training set is used to make the model and test set is used to make validate it. We select different features to train different layers in our framework. The feature selection stage needs with the purpose of reducing audit data to be carefully looked at keep from unnecessary discovery and getting better, having no error. Each of the classifiers was trained using the same training data. The ensemble of classifiers is used to perform classification. Here we ensemble Decision tree and SVM by using boosting classifier. We construct different Connectional
models to get done better generalization performance of
classifiers in designing a classifier. Training knowledge was presented to the committee of classifiers. This training dataset divided into five classes, they are Normal, Probe, DOS, U2R and R2L.
5.1. Feature Selection
Attacked by two different forms for better or for different classes of attacks the identification should be noted separately. As a result, our system layer we were trained in a satisfactory manner for each layer separately determine single attack. We therefore select different features for different layers based upon the type of attack the layer is trained to detect [19].
1) Probe Layer - Probe attacks are aimed at getting knowledge about the target network from a source which is often outside of the network.
2) Dos Layer - Dos attack is mean to prevent the target from providing service to its users by flooding the network with illegitimate request.
3) R2L Layer - R2L attacks are used to detect the network
level and the host level features.
4) U2R Layer - U2R attack involve the semantic details which are very hard to take at any early stage at the network level. Such attacks are often content based and target an application.
5.2 Intrusion Detection using Decision Tree and
Support Vector Machine
5.2.1 Decision Trees
Where each connection or user problem or some kind of an attack based on current information known as decision trees as either. Decision trees can be used as a misuse intrusion detection because they learn a model based on training data and an attack based on the type or normal educated as a model in the future as a predictable.
Data mining in, a Decision tree induction classification algorithm. The Classification algorithm in a variety of information reclassified inductively learned how to create a model. Each data item attributes are defined by the values. The classification of a given class can be considered the application of a number of properties. This is given as the attribute values by using a decision tree to classify this item [15].
5.2.2 Support Vector Machines
Support Vector Machines have been projected as a novel technique for intrusion detection. A Support Vector Machine (SVM) maps input material valued point gives directions to be taken into a higher to do with measures point space through
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 7, July-2013
ISSN 2229-5518
4
some nonlinear mapping. SVM is a powerful tool for providing
solutions to the problem of estimating classification, regression
and density. It is growing on the principle of reducing the risk of the structure. They try to reduce the risk of finding an order that speculates the low probability of an error approaches. To reduce the risk of the structure can be done by finding a hyper plane to the amount inseparable greatest possible addition to information [15].
Using SVM binary classification problem, the answer can be found. Non-linear space is a linear map SVM algorithm. This mapping, a feature called kernel function, use the. Polynomial, radial basis function kernel functions such as hyperlane with a separate feature space is used. Kernel function classifiers that this function was used on the surface of the base vectors. SVM support vectors that characterize this space as classified using the hyperlink outline [16].
The ensemble approach to artificial intelligence is a relatively new trend in which several machine learning algorithms are combined. The main idea of the algorithm is to use the strength of a classifier is exciting. Ensembles mainly useful when the problem can be divided into subproblems. In this case, the actors in each module, which may include one or more algorithms assigned to a particular problem.
6.1 Boosting
Boosting algorithms combine the two main actors in the procurement and use of the techniques. Using an ensemble of boosting technique, the algorithms being used. First of all examples of algorithmic analysis of the dataset and assign them higher value for each weight with the weight of the examples that were incorrectly classified by the algorithm. Then, the next algorithm as well as the input dataset to dataset for all examples of the weight gain. Weight algorithm examples that were most difficult to classify it allows you to focus on. The weight of the second and third algorithm processing algorithm moves are updated according to the results. The sequence continues until the next the last algorithm as a process. The advantage of this method is that the most difficult examples without adding much computational load can be properly classified. Weight used, which are updated during the process because it reduces the computation time as it follows the chain of algorithms [20].
7. CONCLUSION
The aim of this paper is to present an overview that deal specifically with ids using data mining techniques. Many data mining algorithm that has been proposed towards the enrichment of IDSs. Here we present decision tree and svm techniques that is proposed by researchers to detect intrusion
in the network. But all of these data mining techniques are not
satisfactory throughout. So here we are presenting boosting
technique that detects better result than single classifier technique.
[1] Priyanka, S. Dongre,”Intrusion Detection through Ensemble
Classification Approach,” 2011, pp.11-15.
[2] Anazida Zainal,”Ensemble of One classifier for Improved Network
Intrusion Detection System,”.
[3] A. Jain, S. Sharma,”Network Intrusion Detection by using Supervised and Unsupervised Machine Learning Techniques: A Survey,” Vol. 1, pp. 14-20.
[4] J. Koshal,M. Bag,”Cascading of C4.5 Decision Tree and Support Vector Machine For Rule Based Intrusion Detection system,” Vol. 8,2012, pp. 8-20.
[5] http://en.wikipedia.org/wiki/intrusion_detection_system.
[6] http://www.cis.syr.edu/~wedu/Teaching/cis758/LectureNotes/Intrusio n_Detection.pdf.
[7] http://searchsecurity.techtarget.com/tip/IDS-Signature-versus-anomaly
[8] Ali Borji,”Combining Heterogeneous Classifiers for Network Intrusion
Detection,” Springer – 2007, pp. 254-260.
[9] Natesan, P.,”Improving the Attack Detection Rate in Network
Intrusion Detection using Adaboost Algorithm,” 2012, pp. 1041-1048.
[10] Wenke Lee,”A Data Mining Framework For Building Intrusion
Detection Models,”.
[11] D Nagaraju,”Classifying the Network Intrusion Attacks using Data
Mining Classification Method their Performance Comparision,” Vol.
9no.6, June 2009.
[12] D. vennila,”Correlated Alerts And Non-Intrusive Alerts,” Vol.14, no.
4, 2012, pp. 3-4.
[13] M. Khalilian, A. Mamma,”Intrusion Detection System with Data
Mining”, Vol. 11,, 2011, pp. 29-34.
[14] S. Xiaonan Wu*, W. Banzhaf,”The Use of Computational Intelligence in Intrusion Detection System: A Review,” springer – 2009.
[15] S. Peddabachigari, A. Abraham,”Intrusion Detection System using
Decision Tree and Support Vector Machine,”.
[16] Thakre S.P., Ali M.S.”Network Intrusion Detection System & Fuzzy
Logic”.
[17] D. MD. Farid,”Adaptive Intrusion Detection based on Boosting and
Naïve Bayesian Classifier”.
[18] Varun chandola and Vipin kumar,”Anomaly Detection:A Survey”.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 7, July-2013
ISSN 2229-5518
5
[19] Kapil Kumar Gupta,"Robust and Efficient Intrusion detection
System".
[20] A. Balon-Parin."Ensemble-Based Method for Intrusion Detection
System".
[21] P.R. Devale, G. V. Garje,"Intrusion Detection System using Support
Vector Machine and Decision Tree," val. 3- no. 3,2011, pp. 40-43.
IJSER © 2013