International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1
ISSN 2229-5518
RC-MAC Protocol Based On Congestion Avoidance in Wireless Sensor Networks Punitha R #1 , Ramkumar C #2, Velu G #3, Surya Theja M B #4
#1,2 Assistant professor ,SNS College of engineering ,Coimbatore-107, pu-
nitha.ece.snsce@gmail.com.ramkumar_957@yahoo.com.
#3,4 PG Scholar Dept of ECE, SNS College of Engineering,velug123@gmail.com, Coimbatore-107,
Abstract— Application for wireless sensor network is notably different in its characteristics and requirement from a standard W LAN. W hen a critical event triggers a surge of data generated by the sensor, congestion may occur as data packet converge toward a sink, which causes energy waste, throughput reduction, information loss, hidden terminal problem and link failure in contention based MAC protocol. Due to hidden terminal problem the RC-MAC and CSMA/CA protocol sensing is used to reduce the channel contention and radio collision. The formation of a new tree for avoiding link failure-a MAODV routing protocol was introduced in this paper, and the performance of this protocol is measured using the above parameters. The demonstration of a near optimal throughput at each sensor and to achieve congestion avoidance in presence of a multicast routing towards a multiple sink is also done.
Index Terms— CSMA/CA, RC-MAC, MAODV and W ireless Sensor Network, W LAN
—————————— ——————————
1. INTRODUCTION
[6],[8] A Wireless sensor network is a spatially distributed autono- mous sensor which is used to monitor physical or environmental conditions, such as health monitoring, object tracking etc., and to co- operatively pass their data through the network to a main location. The feasible usage of wireless sensor networks in real world applica- tion can only be maintained by overcoming a few technological chal- lenges. Among these challenges, the limited lifetime of the distribut- ed sensor nodes and user interfaces allows the technological utiliza- tion in different manner. [2],[3] The WSN usually consists of many number of small sensing devices that are powered by batteries, equipped with less capable processors and limited memory. Conges- tion is a problem that affects all types of network especially for the low- powered, unreliable wireless sensor networks the occurrence of congestion could negatively affect not only the performance of the network, but also the network parameters like throughput, delay, information loss, link failure.
A mote- the sensor node in a WSN is capable of performing some process. The main problem of congestion avoidance in sensor net- work remains largely open. When a sensor receives more data com- pared with the forward rate the limited buffer space is full and con-
————————————————
• R.Punitha is currently working as assistant professor in SNS College of Engieering, Coimbatore. She completed her masters degree program in ECE in Hindusthan College of Engineering and technology, anna University, india, and her under graduate degree in ECE in Maharaja Prithvi Engineering College in the year 2011. She has published 4 journals and 7 conferences. Her area of Interest is sensor Networks and Microwave Engi- neering. E-mail: punitha.ece.snsce@gmail.com
• C.Ram Kumar is currently working as assistant professor in SNS College of Engieering, Coimbatore. He completed her masters degree program in CS
- ECE in Sri Krishna College of Engineering and Technology. He has pub- lished 14 journals and 17 conferences.H is area of Interest is sensor Net- works and Microwave Engineering.
• Velu.G is currently pursuing masters degree program in electronic com- munication engineering in anna University, india, PH-9751762653.
sequently, the received data has to be dropped.[3],[4] The CSMA/CA
is (carrier sense multiple access / collision avoidance) a protocol for carrier transmission in wireless sensor network. In
CSMA/CA, as soon as anode receives a protocol that is to be sent, it checks to be sure the channel is clear i.e., no other node is transmit- ting at that time. If the channel is clear, then the packet is sent. Radio collision and buffer overflow are two main types of congestion in a sensor network, solutions against collision include CSMA, TDMA, RC-MAC etc...,
[8],[9] The RC-MAC protocol allows the nodes to effec- tively utilize multiple channels by reducing unnecessary channel switching and is used to improve the communication throughput of sensor network. The receiver-centric MAC protocol consists of two parts: the channel access scheduling and the lost packet re- transmission.
Figure: 1 RC-MAC utilizes
[1] For a multi-hop routing, the mobile nodes can be enabled by dynamically self-starting that is a Multicast Ad-hoc on Demand Dis- tance Vector (MAODV) routing protocol. [9] This also enables the mobile nodes to establish a tree connecting multicast group mem- bers. Mobile nodes will quickly respond to link breaks in multicast tree by repairing those breaks in a timely manner. In this event of
E-mail: velug123@mail.com
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 2
ISSN 2229-5518
network partition, multicast trees are established independently in each partition and trees for the same multicast group are quickly
connected, if the network components merge.
2. EXISTING METHOD
[6],[7] The challenges in wireless sensor network are conges- tion, information loss, reducing delay, link failure and power con- sumption. There are different technologies available in wireless sen- sor network, with the design, implementation and performance eval- uation of a different MAC protocol for WSN that combines the strengths of CSMA/CA[1], TDMA and RC-MAC while offsetting their weakness, like CSMA. TDMA, achieves high channel utiliza- tion and reducing throughput, low delay under low contention and like RC-MAC [4].
3. PROPOSED METHOD
A sensor network comprising of a number of sensors and multi- ple sinks also called base stations are used here. The assumptions include a set of stationary sensors distributed in a rectangular area and a collision free MAC. Packet loss due to collisions is independ- ent of design aspects and thus can be abstracted when studying a congestion avoidance and/or control protocol. Congestion causes energy waste, throughput, reduce information loss and link failure contention based MAC protocol, here RC-MAC and CSMA/CA protocol sensing is considered to reduce the channel contention and radio collision due to hidden terminal problems. In this method, we introduce a MAODV routing protocol, estimation routing with for- mation of new tree for avoiding the link failure. The performance is measured in terms of our MAODV protocol through measurement of parameters.
4. PROTOCOLS AND TECHNIQUES USED
4.1 CSMA/CA and CSMA with ACK:
[3],[2] CSMA/CA is a virtual carrier sensing which is used to reduce the probability of radio collision due to hidden terminal problem. Hidden terminals occur when two senders that are not in radio range transmit to a common receiver. One way of reducing collision between hidden terminal is to exchange RTS/CTS control packets, before communicating the RTS/CTS to exchange it elimi- nates most data packet collision. Data transmission requires RTS- CTS-DATA-ACK exchange between two neighbouring sensors. Now, consider the following two cases to avoid congestion.
[4],[5] Case1: B may not overhear packets sent by A due to temporary ratio interference. Therefore, its knowledge about A’s buffer may be state.
[3] Case2: when B wakes up from the sleeping mode its knowledge about A’s buffer may be state.
4.2 RC-MAC:
tree structure in WSN.
The RC-MAC protocol that allows node to efficiently uti-
lize multiple channel by reducing unnecessary channel switching. Receiver-centric MAC avoids the interference due to improve com- munication throughput of wireless sensor network.
It consists of two main part of RC-MAC:
• The channel access scheduling.
• Lost packet retransmission.
The RC-MAC is used to reduce collision and improve communica- tion throughput under heavy traffic loads by utilizing the underlying
4.3 MAODV routing protocol:
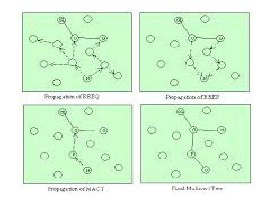
MAODV is intended for use by mobile nodes in an ad-hoc network. MAODV is a multicast extension of AODV. MAODV rout- ing protocol in Fig.2 explains how to form the tree and how to repair the tree, when link is broken and the merging two previously discon- nected tree into a new tree. A node monitors the link status of next hope on the multicast tree, when a link breaks the multicast tree is detected the tree branch should be immediately repaired through the use of the RREQ/RREP/MACT message.
Figure: 2 MAODV Routing Protocol
The message carries a multicast group, group number, cor-
responding group leader’s IP address, the information of the mul- ticast group for repairing multicast trees after a previously discon- nected part of the network becomes reachable once again.
4.4 Link Failure mechanism:
[1],[5] Branches of the multicast tree becomes invalid if a broken link result in an infinite metric which was associated with the next hop route table entry. When a broken link is detected between two nodes on the multicast tree, the nodes should delete the link from their list of next hops for the multicast group.
5. SIMULATION RESULTS
Implementation is done using Ns-2 software. Here there are some important sequence that are implemented with the simulator. The experimental set up contains 100 nodes. These 100 nodes are arranged randomly in positions. Since the environment is wireless, the nodes are given in a random motion. In this implementation, the throughput, congestion avoidance, packet loss and node energy con- sumption are measured.
5.1 Throughput Comparison
The number of packets that are transmitted in the network is shown in the following graph. Throughput is measured after the CSMA/CA, RC-MAC, and after the MAODV has been rectified. It is shown that the throughput after the tree formation has been over- come is high that is 11.5%.
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 3
ISSN 2229-5518
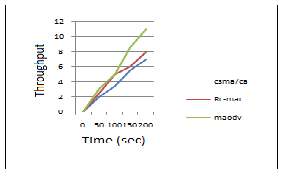
Figure:3 The graph representing throughput comparison
5.2 Congestion avoidance
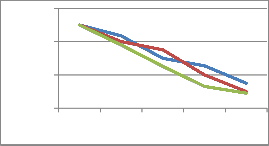
Fig.4 demonstrates, the congestion avoidance scheme. The buffer size at each sensor affects the total source rate over time. After time t=120 seconds, the source rates of all simulations are stabilized and they are very close to one another, which means that a small buffer size can achieve a suboptimal performance and gain. By fur- ther increasing the buffer size this is not significant, which agrees with our
analytical results.
600
400
200
0
Figure: 5 Comparison for packet lost
5.4 Energy expenditure:
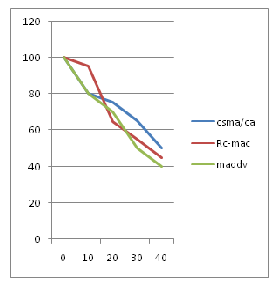
Energy expenditure is inversely proportional to the energy consumption. Energy consumption is measured before implementing RC-MAC and after implementing RC-MAC. First we measure for CSMA/CA and the its combined with RC-MAC and finally with the MAODV protocol. The energy expenditure is high in the case when MAODV protocol is applied in the network. By this the energy is improved by 20%.
Figure 6 Energy Expenditure per packet over time.
6. CONCLUSION:
Figure:4 The graph representing by congestion avoidance
5.3 Packet loss:
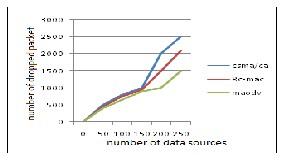
Fig.5 compares the number of packets dropped with respect to the initial rate. The packet loss is the rate at which the source generates a new data intuitively, when the initial source rate is high- er, whose number of dropped packet is roughly proportional to the initial source rate. Using MAODV protocol the packet loss can be reduced.
avoiding the link failure was done. We thoroughly evaluated the pre- sent method by NS-2 software, the simulation results and analysis of parameters like throughput, packet loss, energy consumption and link failure are shown and thus the performance with other protocols are compared and from the results its clear that the MAODV routing Protocol has High performance and efficiency.
7. REFERNECE
[1]C.Y Wan, S.B Eisenman and A.T Campbell,” CODA : Congestion Detection and Avoidance in Sensor Networks” ,Proc.ACM Sen- Sys `03, Nov. 2003.
[2]C.T. Ee and R. Bajcsy, “Congestion Control and Fairness for many-to-One Routing in Sensor Networks,” Proc.ACM SenSys
`04, Nov. 2004.
[3]S. Chen and N. Yang, “Congestion Avoidance Based on Light- Weight Buffer Management in Sensor Networks,” technical re- port, Dept of Computer and Information Science and Eng., Univ. of Florida, 2005.
[4]Shigang Chen Na Yang, “Congestion Avoidance Based on
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 4
ISSN 2229-5518
Light-Weight Buffer Management in Sensor Networks,” IEEE,
VOL. 17, NO.9, September 2006.
[5]Jeff Johnson, Mario Ruiz, Jonathan Lees and Matt Welsh, “Moni- toring Volcanic Eruptions with a Wireless Sensor Network” in proc, of EWSN 2007, pp.163.
[6]Y. Sun. O. Gurewitz. D. B. Johnson, “RI-MAC: A receiver- initiated asynchronous duty-cycle MAC Protocol for dynamic traffic loads in wireless sensor networks,” in Proc. Of Sen- Sys.2008, pp.1-14.
[7]Injong Rhee, Ajit Warrier and Mahesh Aia “Z-MAC:A Hybrid mac for wireless sensor network” dept CSE Raleigh, NC
27695.2013.
[8]Roman Lara Cueva, “Towards a new Volcano Monitoring system Using Wireless Sensor Network” Student Member, IEEE, Rodol- fo Gordillo Orquera, Member, IEEE.
[9]Nicosia and Cyprus “HRTC: A Hybrid algorithm for Efficient congestion control in WSN”, IEEE, Vol.3 , issue.2,April 2014
IJSER © 2015 http://www.ijser.org





