International Journal of Scientific & Engineering Research Volume 2, Issue 6, June-2011 1
ISSN 2229-5518
Performance Analysis of Routing Protocols
Using Different Environment in MANET
Rakesh kumar Yadav, Manish Bhardwaj, Sachi Pandey
Abstract— Mobile Ad hoc networks (MANET) represents complex distributed systems that comprise wireless ad hoc network that does not rely on any fixed infrastructure and has dynamic topology also called short lived networks. MANET is self-organized and self-configurable network where the mobile nodes move arbitrarily. The mobile nodes can receive and forward packets as a router. Routing is a critical issue in MANET; efficient routing protocols will make routing reliable. The most popular ones are AODV, DSDV and DSR. The performance mea- surements are based on the various performance metrics such as packet delivery fraction, average end to end delay. This paper also analy- sis the performance of using execution time by varying different MANET simulation parameters.
Index Terms— MANET, AODV, DSDV, DSR, GloMoSim 2.03, Transmission range, Topologies, Bandwidth.
—————————— • ——————————
obile Ad Hoc Network (MANET) is a collection of communication devices or nodes that wish to communicate without any fixed infrastructure and
pre-determined organization of available links. The nodes in MANET themselves are responsible for dynamically discovering other nodes to communicate. It is a self- configuring network of mobile nodes connected by wire- less links the union of which forms an arbitrary topology. The nodes are free to move randomly and organize them- selves arbitrarily thus, the network’s wireless topology may change rapidly and unpredictably. Routing is a core problem in networks for sending data from one node to another. Such networks are aimed to provide communica- tion capabilities to areas where limited or no communica- tion infrastructures exist. MANET’s can also be deployed to allow the communication devices to form a dynamic and temporary network among them. A mobile Ad Hoc network (MANET) is receiving attention due to many potential military and civilian applications. MANET’s have several salient characteristics: 1) Dynamic topologies
2) Bandwidth-constrained links 3) Energy constrained
operation 4) limited physical security. Therefore the
routing protocols for wired networks cannot be directly
used for wireless networks.
A MANET uses multi-hop routing instead of a static
network infrastructure to provide network connectivity.
Several routing protocols have been proposed for mobile
Ad Hoc networks. In this paper represents the execution
time analysis by varying different MANET simulation
parameters, because execution time is a main parameter
————————————————
• Rakesh Kumar Yadav, M.E, NITTTR, Chandigarh, India,E-mail:
• Manish bhardwaj, Pursuing M.Tech. in Computer Science & Engg, SRM
University, India, E-mail: simenscomputer4u@yahoo.com
• Sachi Pandey Pursuing M.Tech. in Computer Science & Engg, SRM Uni-
versity, India, E-mail: sachipandey_08@yahoo.co.in
for analyzing the performance of mobile ad-hoc network. Here we are using the simulation tool GloMoSim for large scale scenarios to obtain execution time analysis by vary- ing different simulation parameters. Because it is giving more accuracy while constructing large scale scenarios.
The AODV routing protocol shares features of both DSDV and DSR algorithms. AODV shares DSR’s on- demand characteristics in that it also discovers route as and when needed by initiating a route discovery process. It maintains one entry per destination in its routing tables unlike in DSR, which maintains multiple route entries for each destination in its route cache. In AODV, the packets carry the destination address and sequence number. In AODV, when a source requires a path to the destination, a route request (RREQ) message is flooded in the net- work.
When an intermediate node receives such a RREQ, it examines its local route cache to check whether a fresh route to the required destination is available or not. If a fresh route exists, then the node unicasts a route reply (RREP) message immediately back to the source. As an optimization, AODV uses an “expanding ring” flooding technique, where a RREQ is issued with a limited TTL only. If no RREP message is received within a certain time by the source node, then another RREQ is issued with a larger TTL value. If still no reply, the TTL is increased in steps, until a certain maximum value is reached. During route discovery process, all IP-Packets generated by the application for destination are buffered in the source node itself. When a route is established, then the packets are transmitted. An important feature of AODV is the maintenance of timer-based states in each node, regard- ing utilization of individual routing table entries. A routing table entry is said to be expired if not used within certain duration. These nodes are notified with route er- ror (RERR) packets when the next-hop link breaks. In the
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 6, June-2011 2
ISSN 2229-5518
situation of link break, each predecessor node, forwards the RERR to its own set of predecessors. In this way all routes, which contain the broken link, are removed.
DSDV is a hop-by-hop distance vector routing protocol. It is proactive; each network node maintains a routing table that contains the next-hop for, and number of hops to, all reachable destinations. Periodical broadcasts of routing updates attempt to keep the routing table completely up- dated at all times. To guarantee loop-freedom DSDV uses a concept of sequence numbers to indicate the freshness of a route. A route R is considered more favorable than R' if R has a greater sequence number or, if the routes have the same sequence number, R has lower hop-count.
The sequence number for a route is set by the destina- tion node and increased by one for every new originating route advertisement. When a node along a path detects a broken route to a destination D, it advertises its route to D with an infinite hop-count and a sequence number in- creased by one. Route loops can occur when incorrect routing information is present in the network after a change in the network topology, e.g., a broken link. In this context the use of sequence numbers adapts DSDV to a dynamic network topology such as in an ad-hoc net- work. DSDV uses triggered route updates when the to- pology changes. The transmission of updates is delayed to introduce a damping effect when the topology is changing rapidly. This gives an additional adaptation of DSDV to ad-hoc networks.
It is one of the most well known routing algorithms for ad hoc wireless networks. It was originally developed by Johnson, Maltz, and Broch. DSR is on demand, which reduces the bandwidth use especially in situations where the mobility is low. It is a simple and efficient routing protocol for use in ad hoc networks. It has two important phases, route discovery and route maintenance. The main algorithm works in the following manner. A node that desires communication with another node first searches its route cache to see if it already has a route to the desti- nation. If it does not, it then initiates a route discovery mechanism. This is done by sending a Route Request message. When the node gets this route request message, it searches its own cache to see if it has a route to the des- tination. If it does not, it then appends its id to the packet and forwards the packet to the next node; this continuous until either a node with a route to the destination is en- countered (i.e. has a route in its own cache) or the destina- tion receives the packet. In that case, the node sends a route reply packet which has a list of all of the nodes that forwarded the packet to reach the destination. This consti- tutes the routing information needed by the source, which can then send its data packets to the destination
using this newly discovered route. DSR can support rela- tively rapid rates of mobility.
In Mobile adhoc network (MANET) consist of mobile hosts without any infrastructure. Here the Execution time is the essential parameter in performance analysis for the research peoples. Execution time is the time for executing a particular scenario. Here in GloMoSim execution time is measured by
Global mobile information system simulator (GloMoSim) is a scalable simulation environment for large wireless and wire line communication networks. GloMoSim is a scalable simulation environment for mobile and wireless networks developed at UCLA Parallel Computing Labor- atory. GloMoSim is a discrete event simulator built using PARSEC a C based environment designed for parallel simulations also developed at UCLA Parallel Computing Laboratory. GloMoSim is built using a layered approach similar to the OSI seven layers network architecture, with standard APIs between layers. This makes it easy to im- plement and integrate new protocols and models at dif- ferent. GloMoSim is written in C and utilizes PARSEC (Parallel Simulation Environment for Complex Systems) which is a simulation environment developed for parallel and sequential execution of discrete event simulations. By discrete event it means that the execution is mainly based on event handling, i.e., the execution consists of set of events and as an event occurs, the appropriate action is taken in its response. An event is defined as an incident which results in the change of state of the system. A cer- tain event or combination of events may invoke other events and so on, and this is how the execution proceeds. Some examples are arrival of packet at a particular layer, expiry of a timer, etc. Events only occur at discrete units of time are not permitted to occur in between these units of time. GloMoSim is freely available for educational purposes. However the free version only supports the sequential execution of simulations.
GloMoSim simulates networks with up to thousand nodes linked by a heterogeneous communications capa- bility that includes multicast, asymmetric communica- tions using direct satellite broadcasts, multi-hop wireless communications using ad-hoc networking and traditional Internet protocols. The following table lists the GloMoSim
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 6, June-2011 3
ISSN 2229-5518
models currently available at each of the major layers mention in table 1.
TABLE 1
GLOMOSIM MODELS AT DIFFERENT LAYER
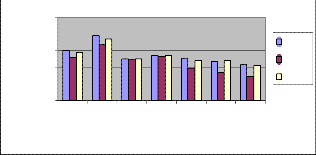
vering packets from source to destination. The higher for the value give use the better results. This metric characte- rizes both the completeness and correctness of the routing protocol also reliability of routing protocol by giving its effectiveness.
The node aggregation technique is introduced into GloMoSim to give significant benefits to the simulation performance. Initializing each node as a separate entity
1
0.8
0.6
0.4
0.2
0
O 5 10 15 20 25 30
NO. OF NODES
AODV DSDV DSR
inherently limits the the scalability because the memory requirements increase dramatically for a model with large number of nodes. With node aggregation, a single entity can simulate several network nodes in the system. Node aggregation technique implies that the number of nodes in the system can be increased while maintaining the same number of entities in the simulation. In GloMoSim, each entity represents a geographical area of the simula- tion. Hence the network nodes which a particular entity represents are determined by the physical position of the nodes.
Fig. 1. Packet delivery fraction vs No. of node
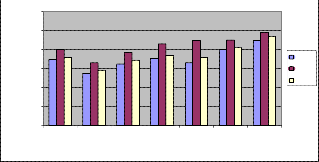
Average end-to-end delay is an average end-to-end delay of data packets. It also caused by queuing for transmition at the node and buffering data for detouring. Once the time difference between every CBR packet sent and re- ceived was recorded, dividing the total time difference over the total number of CBR packets received gave the average end-to-end delay for the received packets.
Below we mention parameters values in table 2 for routing protocols simulation.
TABLE 2
PARAMETER EVELUATION
30000
25000
20000
15000
10000
5000
AODV DSDV DSR
0
0 5 10 15 20 25 30
NO. OF NODES
Fig. 2. Average E2E delay vs No. of nodes
In order to evaluate the performance of ad hoc net- work routing protocols, the following metrics were con- sidered:
Also known as the ratio of the data packets delivered to the destinations to those generated by the CBR sources. The PDF shows how successful a protocol performs deli-
This graph shows that the com,parison between the three routing protocol like DSDV, AODV,and DSR.According to this graph the average end to end de- lay of two routing protocol like AODV and DSR are very similar or say that it contain very minute difference.
7.3.1 AODV, DSR, DSDV VS EXECUTION TIME
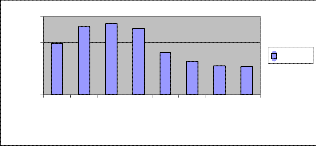
Here we compared the execution time analysis by using AODV, DSR and DSDV routing protocols. And we no- ticed the execution time varies as follows
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 6, June-2011 4
ISSN 2229-5518
2500
2000
1500
1000
500
0
25 75 150 225 275 300
NODE DENSITY RANGE
AODV DSDV DSR
tion times and it’s affected while changing network pa- rameters vs. real times in large scale scenario.
The authors would like to express their thanks to Mr. R.P.Mahapatra, H.O.D (C.S.E Dept.) of SRM University for support and environment provided for research.
[1] R.Balakrishna, M.V.Panduranga Rao, Dr.K.C.Shet,” Development of Scheduler for Real Time and Embedded System Domain”, in digital library at IEEE AINA-2008
Fig. 3. Execution time vs Node density range
7.3.2 TERRAIN RANGE VS EXECUTION TIME
In the same scenario we changed the terrain dimensions, the execution time varies or high for increasing the terrain dimension. The result is following in the figure
15
10
Series1
5
0
500 1000 1500 2000 2500 3000 3500 4000
TERRAIN RANGE
Fig. 4. Execution time vs Terrain range
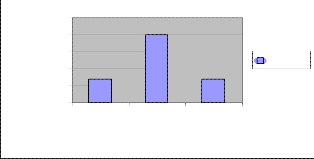
In Mobile Ad hoc Network the mobile nodes are battery constraint.so the transmission range is very essential pa- rameter to analyse the Execution time. The following graph has shown the analysis of execution time with va- rying transmission range.
10.15
10.1
10.05
Series1
10
9.95
9.9
15 30 75
TRANSMISSION RANGE
Fig. 5. Execution time vs Transmission range
The work was initiated with an intention of carrying out exhaustive study of the performance issues of large scale MANETs. We obtained convincing results for the execu-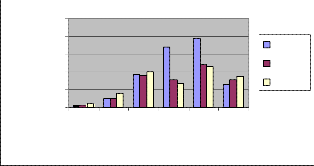
International Conference, JAPAN.The details about the
conference is available at http://www.aina-conference.org/2008
[2] A. K. Gupta “Performance analysis of AODV, DSR and TORA Routing Protocols” IACSIT international journal of Engineering and Technology, Vol. 2, No. 2, April 2010 ISSN: 1793-8236.
[3] C. E. Perkins and E. M. Royer, Ad hoc Networking, chapter Ad
hoc On-Demand Distance Vector Routing, Addison Wesley,
2009.
[4] Ahmed Al- Maashri and Mohamed Ould- Khaoua.“Performance Analysis of MANET Routing Protocols in the Presence of Self- Similar Traffic”. IEEE, ISSN- 0742-1303 . First published in Proc. of the 31st IEEE Conference on Local Computer Networks, 2006.
[5] Khan, Khaleel Ur Rahman; Zaman, Rafi U.; Reddy, A.
Venugopal,” Performance Comparison of On-Demand and Table Driven Ad Hoc Routing protocols Using NCTUns”,, UKSIM: IEEE Tenth International Conference on Computer Modeling and Simulation Volume , Issue , 1-3 , Page(s):336 –
341, April 2008.
[6] A.E. Mahmoud, R. Khalaf & A, Kayssi, Performance Comparison of the AODV and DSDV Routing Protocols in Mobile Ad-Hoc Networks, Lebanon, 2007.
[7] C. E. Perkins and E. M. Royer, “Ad-hoc On-Demand Distance Vector Routing,” Proc. 2nd IEEE Wksp. Mobile Comp. Sys. and Apps., Feb. 1999, pp. 90–100.
[8] GloMoSim: Global Mobile Information Systems Simulation
Library. http://pcl.cs.ucla.edu/projects/glomosim/
[9] IEEE 802.11: part 11: Wireless LAN Medium Access control
(MAC) and Physical Layer (PHY) specification, Aug.1999
[10] S. Bhatt, R. Fujimoto, A. Ogieski and K. Permalla. Parallel Simulation Techniques for Large Scale Networks. IEEE Communication Magazine, 98, pp. 42-47.
[11] Stuart Kurkowski, Tracy Camp, Michael Cologrosso, “MANET Simulation Studies: The Incredible”, Mobile Computing and Communications Review, Volume 9, Number 4, ACM, 2005.
[12] Tope. M.A, McEachen, J.C, and Kinney. A.C, “Ad-hoc net work routing using co-operative diversity", Advanced Information Networking and Applications, IEEEConference,
18-20 April 2006.
[13] A.Boomarani Malany, V.R.Sarma Dhulipala, and RM.Chandrasekaran “Throughput and Delay Comparison of MANET Routing Protocols” Int. J. Open Problems Compt. Math., Vol. 2, No. 3, September 2009.
[14] V.R. Sarma Dhulipala, RM.Chandrasekaran, R.Prabakaran " Timing Analysis and Repeatability Issues of Mobile Ad-Hoc Networking Application traffics in Large Scale Scenarios “ International Journal of Recent Trends in Engineering, Vol. 1, No. 1, May ,2009.
IJSER © 2011 http://www.ijser.org