Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 1
ISS N 2229-5518
Netflow method used for internet worm detetion
Ms. Vidya mhaske-Dhamdhere, Prof. G.A. Patil
Abstract— Due to easy access and requirement of the Internet make it more popular for research and information sharing. Because of this feature a malicious codes are also easily exchange. A worm (malicious codes) can disturb network and normal network operation. Internet worms are causes
significant worldwide disruption, a huge numb er of infected hosts generate traffic, which will impact the performance of the internet. Therefore this is one of the areas where researchers are concentrating to find effective detection system, which will presence the worms and reduce the worm’s spread. This paper deals with a classified study of most important and commonly used methods for detecting internet worms using Netflow, which can help network managers to monitor suspect Internet worm’s activities b y analyzing the source data from the router.
Inde x Term- Internet worms, anomaly detection, network intrusion detection, Netflow
—————————— ——————————
The Internet is persistently threatened by many types of attacks such as viruses, and worms. A worm is aself propagating program that infects other hosts based on a known vulnerability in network hosts. In contrast, a virus is a piece of code attached to another executable program, which requires human action to propagate. A major challenge in networking is how to detect new worms and viruses in the early stages of propagation in a computationally efficient manner.
The impact of worms and viruses on the Internet
include delays due to congestion, extensive waste of network bandwidth, as well as corruption of user’s compu ters and data. Furthermore, viruses and worms can carry software that ]enables attackers to gain access to the personal informa- tion of users. In addition, recent worms are capable of launching distributed denial-of-service (DDoS) attacks against
other hosts [1].
———— ——— ——— ——— ———
MS. Vidya Mhaske-Dhamdhere has Completed Master Degree in Computer Sci. & engg.And currently working in G.H.Raisoni college of Engg.pune. India Email :- vidya.dhamdhere@gamil.com Volume 4, Issue 1, January
2012.ail.com
Prof.G.A. patil is currently pursuing Phd degree program in CSE in India.
And currently working in D.Y. patil college of Engg. & tech, Kolh a-
pur,Maharasta,India as a HOD of computer dept and BOS of IT and CSE In
Kolhapur university E-mail: gasunikita@yahoo.com
During the past 20 years, thousands of different worms have been developed. Some of these worms have caused huge disruption to global networks. The most notable worms include Morris, Code Red and Code Red II, Nimda, Slapper, and Sapphire/Slammer worms, and recently, So- Big.F, MSBlast, and Mydoom. From the first worm that was released in 1988 (the Morris worm), the area of Internet worm detection has been a significant research problem. In order to understand the worm threat, it is neces sary toun- derstand the various types of worms, payloads, and
attackers. Taxonomy of the various possible worms, payl-
oads, and attackers as an initial guide to plausible defenses.
This taxonomy is necessarily incomplete, simply because new tactics, payloads, and attackers may arise. This taxon o- my is based on several factors: target discovery, carrier, acti- vation, payloads, and attackers. Target discovery represents the mechanism by which a worm discovers new targets to infect. The carrier is the mechanism the worm uses to trans- mit itself onto the target [5-9]. Activation is the mechanism by which the worm’s code begins operating on the target. Payloads are the various non-propagating routines a worm may use to accomplish the a uthor’s goal. Finally, the various possible attackers have different motives and would there- fore utilize different payloads.
In addition, it is important to note that worms
needn’t be confined to a single type within each category. Some of the most successful worms are multi-modal, em- ploying multiple means of target discovery, carrier, payload, etc, where the combination enables the worm to surpass de- fenses (no matter how effective) that address only a single type of worm. In this section, summary of previous a p- proaches to worm detection has been done [6-15]. Usually, the
detection methods are based on the feature of the Internet
worm such as abnormal network traffic, content comparison, process scanning and detecting network connection.
The current detection method for the Internet Worm
two general categories: Signature-based Detection and Ano- maly Detection. Signature-based detection is based on defin- ing malicious patterns that the system has to detect. Sign a- ture-based detection suffers from the problem that it requires a signature of each attack be known. In contr ast, anomaly detection differs by constr ucting a pr ofile of normal beh a- viors or activities on the netw or k, and then looking for activities that do not fit the normal pr ofile. Since not all the ab normal activities in the networ k ar e suspicious, anomaly detection has the pr oblem of r aising false alarms when it en- counters normal traffic.
The Connection-Or iented detection method Ob-
serves the number of connection w ith the tar get host and checks the connection behavior. Conditions ar e the cor e of
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 2
ISS N 2229-5518
Connection-Oriented detection method.
The Inter net worms diffuse quickly to infect servers,
destr oy information, embed backdoor , and consume r esour ce fr om netw or k bandwidth In the trap oriented detection m e- thod, the surveillance ar ea can be separat ed into single host and the several networ k segments on the Internet. In this method, the accuracy is quite high and it is easy to differ en- tiate betw een the normal and abnor mal tr affic. Ther efor e, the nodes have to collect the networ k flows (information which is pr oduced fr om r outer ), for finding abnormal tr affic.[17]
Every Inter net w orm has to have a certain minimal functio- nality in order to be viable:
• A w orm has to be able to identify possible infection tar gets.
• A w orm has to be able to tr ansfer its code to a selected tar-
get.
• A w orm has to be able to induce a vulnerable tar get to run the transferr ed w orm code.
• A w orm should be able to identify alr eady infected tar gets
and r efrain fr om r e-infecting them. Inter estingly, the fir st thr ee r equir ements ar e alr eady enough. The four th mer ely impr oves efficiency. Also, if a ser vice on the tar get system is capable and willing to pr opagate the w orm without having its security compr omised, then a worm can do without any kind of system compr omise at all. A compromise of the tar get system to some degr ee is customary nonetheless, especially when some other pur pose, like espionage, sending of spam or attacks on other systems is intended.[19-23] A second r ea- son for tar get system compr omise is that many worms use security vulnerabilities to obtain r esour ces on the tar get sys- tem. The advantage is that in this way the basic execution ser vices of the tar get system become available to the w orm and any functionality its designer wants can be easily im- plemented. The typical wor m uses a pr opagation mechanism that wor ks like this:
1. Select a potential tar get
2. Attempt to contact the tar get
3. Compr omise the tar gets secur ity in some way to obtain the r esour ces to transfer and execute a copy of itself.
4. If mor e infections ar e desir ed, goto step 1
5. Do damage on the local machine or do damage somewher e else using the local machine
The last step is optional and can also be done ear lier. How ev-
er , in or der for a w orm to pr opagate as fast as possible, it is a sound design choice to not impair the functionality of an i n- fected host until the w orm has completed most or all of its intended pr opagation activity from that host. In addition, the damage may be done later to delay the discovery of the worm or in or der to allow coor dinated attacks from several infection generations.
Note that w e also r egar d data collection activities, such as
looking for passwor ds or cr edit car d number s, as causing
“damage”
1.Target Selection Mechanism---- The tar get identification and selection mechanism a w orm uses, since tar get selection has by far the lar gest influence on the actual w orm traffic seen in the Internet dur ing an outbr eak. The r eason is that, while the tar get addr ess may or may not be assigned to a host and if ther e is a host, this host may or may not be vu l- ner able, the w orm code has to select tar gets and then try to contact them. These connection attempts, also called scan traffic is the most visible sign of a fast Inter net worm in its main pr opagation phase.
2. Random Scanning-
Per haps the most simple tar get selection strategy is pur ely random scanning. For this, the tar get selection code usually includes a Pseudo Random Number Generator (PRNG) or uses an OS ser vice w ith this functionality. Infection tar gets ar e then selected by generating a 32 bit random number and
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 3
ISS N 2229-5518
using that as the tar get IP addr ess. In a mor e advanced set- ting, r anges that do not contain normal hosts, such as mult i- cast-addr esses, can be excluded. Car e needs to be taken, that the random tar get selection is implemented corr ectly. Inter es- tingly, many w orm wr iters seem to get this wr ong Mistakes include constant PRNG seeding after pr opagation, use of infer ior PRNGs w ith non-even value distribution and even PRNGs that cannot generate all output values and hence miss many possible tar gets.
Pur e r andom scanning w or ks r easonably w ell, but one di s- advantage is that it does not take advantage of the better networ k connectivity to hosts in the same LAN or otherwise in close pr oximity. Local-pr efer ential scanning is very similar to random scanning, but it dedicates a portion of the scan activity to addr esses in the same subnet the attacking host is in. Typical implementations have pr efer ences for the /24 sub- net and the /16 subnet of the attacking host. One way to i m- plement this type of strategy is to randomly scan in mor e often in the local /16 subnet, but to scan the local /24 subnet fully. The latter can be done in a simple, linear fashion, a l- though this may tr igger IDS and/or IPS system sensors.[25] Local-pr efer ential scanning has sev eral advantages. One is that the pr obability of actually finding hosts w ith a ddr esses close to the attackers IP addr ess is usually far higher than for randomly selected addr esses. After all, the local subnet con- tains at least one host alr eady, namely the infected host. This means that it is not an unused subnet. The second advantage
is that the tr affic over the Inter net access and backbone net- wor ks is r educed. Pur e random scanners r un the risk of over- loading the Inter net access connection and ther eby hindering their own pr opagation. A further advantage is that the net- wor k latency to hosts in close pr oximity is lower , leading to faster scanning and infection per for mance.
A completely differ ent appr oach to random scanning is hit l- ist scanning. To implement this strategy, the w orm-designer pr ecomputes a list of vulnerable tar gets. This list is then i n- cluded in the worm when it is deployed. The w orm then not only pr opagates its ow n code, but also parts of the hitlist to be used by the r espective child instance. Pr opagation schemes with some degr ee of r edundancy ar e possible. For example, each so far unused tar get addr ess could be pr op a- gated to two or sever al child instances of the w orm, so that if a child instance cannot wor k thr ough its list fragment com- pletely, some other child instance may still be successful. With this type of r edundancy the individual copies should be wor ked thr ough in differ ent order s to maximize pr opagation speed. The use of a hitlist scanner for the full vulnerable population for a specific exploit only makes sense if this population is r elatively small. Otherwise the 24 3 Worm Tra f- fic tr ansfer of the hitlist w ill slow down the w orm consider a- bly. A second concern is that the hitlist needs to be obtained in a way that does not ar ouse suspicion. Otherw ise the w orm could find a situation w er e the potential tar gets have a lr eady been warned befor e its initial pr opagation. A typical use of hitlist scanning is to have a r elatively small hitlist of very attractive tar gets, e.g. hosts w ith high bandwidth or host that ar e geogr aphically w ell placed. The w orm then does its in i- tial pr opagation with a hitlist str ategy and then changes over to another str ategy after one or a few infection generations, e.g. r andom scanning.
Topological scanning bears some r esemblance to hitlist sca n- ning. How ever , the information about potential tar gets is not pr ecomputed, but instead extr acted fr om the data available on the local host. Possible sour ces of IP addr esses ar e ARP caches, contact lists of P2P applications, open Internet con- nections, br owser caches, addr ess books of any kind and ot h- er sour ces. Host names and URLs can also be used since they can be converted to IP addr esses by DNS lookup. It should be noted that worms that do DNS lookup will gener ally be quite slow and likely not qualify as fast Internet wor ms a c- cording to our definition. One pr imary example of topologi- cal worms ar e email worms. Although they ar e not Internet worms by our definition, they r epr esent a very important class of application layer w orms. Another class of application layer worms ar e IM (Instant Messaging) worms, that have also been observed in the w ild. P2P file shar ing
could pr ovide an equally viable platform for application
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 4
ISS N 2229-5518
layer w orms, but so far no P2P wor ms have been observed as to our know ledge.
Port Char acter istics
Scan traffic of a fast Inter net w orm has some limitations on
how sour ce and tar get ports can be selected. These ar e differ-
ent for TCP and UDP scan traffic. We will now discuss the differ ent possibilities.
In or dinary TCP traffic, the sour ce port for the connection
initiating host, i.e. the host that sends out the initial SYN
packet, is chosen at random by the networ k stack fr om a port range unlikely to be used as server ports. Each concurr ent connection gets its own source port, so that answ ering traffic can be identified by the port it is sent to. It is poss ible to dr op this r equir ement and match answer ing packets by r emote IP addr ess and port. This is, for example, done in servers that accept multiple connections on a single port, such as w eb server s. For a w orm, it would be possible to use a static sour ce port and match the
answ ering tr affic by r emote IP addr ess. How ever, this causes additional effort and does not have any r eal benefit. It also pr events the w orm fr om using the normal networ k stack, since the normal, OS integrated netw or k stack cannot do this type of matching.
The primary limitation for destination port selection in a worm is the exploit used. If an exploit wor ks only on a speci f- ic por t, then all attack tr affic has to be addr essed to that port. In addition, the connection initiating SYN packet in a TCP connection is unable to transpor t data. Even if a port ind e- pendent exploit was possible, the initial SYN would have to be sent to a por t wher e the r emote system sends an answer. With var iable ports, the worm w ould need to do a port scan in order to find such an open por t. This scan would slow the worm down significantly. In addition we ar e not awar e of any TCP exploits that can be used on a lar ger range of tar get ports. For these r easons a w orm using one or mor e TCP based exploits will likely tar get one or a small number of TCP ports on the tar get system.
Since UDP is connectionless, UDP based exploits can be and usually ar e single-packet exploits. This means the attacking host sends a single packet to the tar get host and is then either contacted back by the successfully executed exploit code or has to do a second polling step. For both options, the UDP sour ce port is immater ial and can be chosen in an arbitr ary fashion.
As in the case of TCP, the tar get port for an UDP exploit de- pends on the actual natur e of the exploit. If the vulner ability is pr esent in a service running on a specific port, the same rationale as for TCP destination ports applies and the tar get port will be fixed. Unlike TCP, UDP permits tr ansfer of data in the fir st packet sent. This allows exploit code to be sent to
random destination por ts, since establishing a connection is not needed. In or der for this to wor k, the vulnerability needs to be in a service that pr ocesses all UDP payloads, such as a fir ewall or a pr oxy.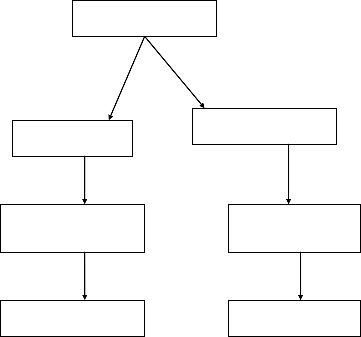
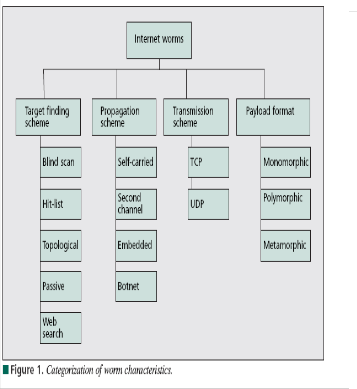
Fig. 2 shows internet worm detet ion algor iths.these algor ithms ar e allr eady implemnted.in this paper we ar e wor k on netflow method.
Detection Al gorithm
Connection -Orient ed
Packet-Ori ented
Pattern Matching Failed connection
Statistics Attempts Connection Rate
Fig.2 Detetion Algor ithm
Statistics: The packet flow is statistically analyzed. This analysis can be based on all packets or only on a selection. Connection-oriented: Connection-oriented detection methods inter pr et packets as part of a connection and base their ana l- ysis on the connections as a whole.
Failed attempts: The number of failed connection attempts is counted and compar ed to a fixed or dynamic thr eshold. Exceeding this thr eshold indicates an attack.
Connection rate: The number of connection attempts (suc- cessful and unsuccessful ones) is counted and compar ed to a thr eshold. Exceeding this thr eshold indicates an attack. Packet-oriented connection-oriented : A lot of computer worms and vir uses have been rapidly spr ea ding all over the wor ld in the last years.
II. METHODS FOR DET ECTING
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 5
ISS N 2229-5518
INTERNET W ORMS USING NETFLOW
A Netflow has been defined in many ways. The 7 tuple key, wher e a flow is defined as a unidir ectional s e- quence of packets with the following 7 values:
1. Sour ce IP
2. Destination IP
3. Sour ce port for UDP or TCP
4. Destination port for UDP or TCP
5. IP pr otocol
6. Ingr ess Inter face
7. IP type of service
Using this Netflow information differ ent systems ar e design for detecting internet w orm. We found out of these the following systems ar e mor e effective:-
1. Defending against Internet Worm- Infestation
2. FloWor M system
Defending against Internet Worm- Infestation:
To deal w ith Internet wor ms, a pr o-active r espond-
ing scheme consisting of detecting, blocking and n otifying
operations. The main goal of this scheme is to keep the net- wor k as healthy as possible dur ing the flooding period of Internet w orms. Inter net worms that generate extr eme high volume of pr obing packets and pose thr eats to normal net- wor k operations [4,28,29].The block diagram is shown in fig- ur e 3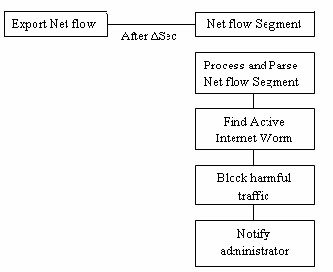
Figur e 3.Internet Worms Defending System
contains IP addr esses of endpoints, service port number s, IP pr otocol type, and the input inter face identifier. Router ex- port NetFlow information. Every Δt seconds, the NetFlow data is collected as a NetFlow segment.[32]
ar e har mful to the networ k (e.g. sending a flood of packets or high fr equent connection attempts). Netflow solution tec h- niques is used to monitor and analyze the networ k traffic ,the NetFlow solution is chosen because it pr ovides a simple and convenient way to obtain networ k flow information w ithout the needs to add additional passive monitoring devices to the networ k.
pr oceed and analyze the data to figur e out
what happened to the networ k.
as possible. Then it is to pr event other hosts fr om being i n-
fluenced by infected hosts.[35-38] The third one is to make an effor t to obey the policy that we should punish bad ones not all other innocent ones.
To keep a healthy networ k, the access contr ol fun c- tion on r outers and switches ar e used not only to pr otect the networ k devices themselves but also to block harmful traffic onto them. Ther e ar e two cases to be consider ed in the bloc k- ing operation:
• Hosts inside the network: W hen the virulent host is inside the networ k, it is best to isolate the infected host only w it h- out
affecting other hosts.
• Hosts outside the network: When ther e ar e j ust a few
Number of vir ulent hosts outside the networ k, then sim ply
blocks traffic fr om these hosts on the bor der r outer.
trators or persons r elative to the secur ity incidents. It can be
implemented by sending emails, short messages to pagers or mobile phones.
FloWorM System :
The pr evious system detects w orm, notify the net- wor k administrator to do further analysis or by coor dinating the NMS t o automatically pr ocess self-defense mechanism
.But the pr oblem w ith the system is that it gener ate false
alar m. FloWor M system [6] can gr eatly r educe false alarm and can efficiently detect the Internet worm activity. The Functioning of system is shown in figur e below:
In FloWor M System NetFlow data is collected fr om r outer because tr affic information w ill be r ecor ded on the r outers. Then use data fr om the NetFlow to analyze the flow and generalize four typical abnormal networ k behavior s, which ar e br iefly discussed below.
• The IP addr ess communicates w ith specific destination
ports in or der to infect other computer host, the Inter net worm w ill try to incr eases the number of IP a ddr esses that communicate with other hosts.
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 6
ISS N 2229-5518
• Failur e in the networ k connection is due lack of know ledge of tar get victim. The port service on the victim host is not pr evalence.
• Connecting unassigned IP addr ess use a particular algo-
r ithm to pr oduce the tar get IP addr esses.
• The netw or k packet which is pr oduced by the Inter net worm w ill follow the or der or content that w ill launch attack. System w or k in tw o stages using differ ent modules:
Stage 1:
The tracking module monitors abnor mal flow. Ab-
normal flows ar e mar ked w ith the tag while r elated inform a- tion ar e sent to another tracker to keep the r ecor d. The sus- pect tag flow w ill be sent to Analyzer module. The tracking module w or k in tw o steps:
1. Spr eading and Scanning
2. Repetitious Pattern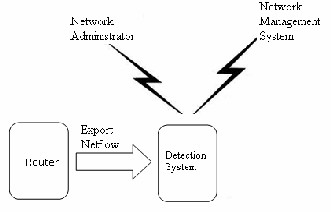
Figur e 2.FloWor M System Design
In Spr eading and Scanning stage Tracker detect the networ k worm. For detection of worm it finds out inform a- tion like:
• Connection w ith a specific pr otocol
• DstPort
• No of Connection
• Number of Fail connection
Using this infor mation the tracker find some limit
value. If specified connection values cr oss the limit value
such connection is detected as abnormal connection and mar k w ith TAG_SPREAD andTAG_SCAN and send to next tracker. In r epetitious pattern ,tracker collects the suspicious flow which is mar ked with TAG_SPREAD and TAG_SCAN by the Spr eading and Scanning for fur ther r ecognition and detection.
Stage 2:
In 2nd stage Analyzer is used identified the category of the networ k w orm and decide the networ k w orm behavior. The
Signatur e basedIDS system is used to compar e packets b e- tw een the normality and the abnormality. Usually, the net- wor k wor m has some specific attack techniques and the i n- fected behavior. The infected behavior [2] ar e in four phases: sending attack packet, connecting to backdoor , exchanging the connection information with the specific host, and
sending data by using specific communication port. Suppose
A is infected host w ith the w orm and B is infesting host by A.
Firstly, A tries to connect to B by using port. Analyzer has to captur e this kind of scanning behavior. When the connection is successful, A w ill tr y to exploit B and launch the attack. Scanning is the detection method in this system. After sca n- ning such connection r ecor d is maintain in the system. If coming connection matches w ith the entry alarm has been pr oduced to inform administrator.
This paper pr esents a classified study of internet worm detection system. Defending against Inter net Wor m- Infestation system is easy to implement but b ecause short holding time false alarm is the maj or dr awback of the system. Another method which described in the paper is FloWorm which pr ovides a high accuracy and it r educes detection rate. In the futur e, it is also possible to divide the w orm connec- tion into two differ ent categories like the connection which impersonate server and the connection which impersonate client.
Inte rne t Wo rm-like Infe statio ns”, the 18th ”2008, vol.15,pp.581 -586
Inte rnatio nal Co nfe re nce o n Adv anc e d Info rmatio n Ne two rking and
Applic atio ns, 2004 vo l.1 pp.152 -157.
Flo w Base d Inte rne t-wo rm De tec ting Syste m in Large Ne two rk
*7+ V. P. N. We ave r, S. S tanifo rd, and R. Cunning ham, “A Taxo no my
o f Co mpute r Wo rms,” Proc. ACM WORM ’03 , 2003.
[8] J. M. Nie ls Provo s and Ke Wang, “Se arc h Wo rms,” Proc. ACM
WORM ’06, 2006.
*9+ G. P. Sc haffe r, “Wo rms and V iruses and Bo tne ts, Oh My !
Ratio nal Re spo nses to Eme rg ing Inte rne t Thre ats,” IEEE Sec. &Privacy , vo l. 4, 2006, pp. 52 –58.
[10] J. Z. Mo hee b Abu Rajab, F. Mo nro se, and A. Te rzis, “A Multifac e te d
IJSER © 2012
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 7
ISS N 2229-5518
Appro ac h to Unde rstanding the Bo tne t Phe no me no n,”Proc. 6th ACM SIGCOMM on Internet Mea surement, 2006.
*11+ E. C. Ying Zhang and Z. Mo rley Mao , “Inte rne t-Sc ale Malware Miti- g atio n: Co mbining Inte llige nce o f the Co ntro l and Data Plane ,” Proc.
ACM WORM ’06, 2006.
[12] V . P. D. Moo re et a l., “Inside the S lamme r Wo rm,” IEEE Sec.
& Privacy, vo l. 1, 2003, pp. 33 –39.
*13+ D. G. Glaze r, “Co mpute r Wo rms,” May 2005, http://www. R
se arc h.umbc .e du/~dgo rin1/is432/wo rms.htm
*14+ “Mo rris (Co mpute r Wo rm),” re trieve d July 2007, http://e n. wikipe- dia.o rg/wiki/Mo rris_wo rm
*15+ “F-Sec ure V irus De sc riptio ns: Nimda,” re trieve d July 2007,
http://www.f-sec ure.co m/v -de scs/nimda.shtml, 2001
*16+ “CERT” Adv iso ry CA -2001-26 Nimda Wo rm,” re trieve d July 2007,
http://www.ce rt.o rg/adv iso ries/CA -2001-26.html, 2001.
*17+ “F-Sec ure Co mpute r V irus Info rmatio n Page s: S lamme r,” vo l.
May , 2005, http://www.f-sec ure .co m/v -de scs/mssqlm.shtml
*18+ “S asse r Wo rm Analy sis — LURHQ,” May 2005, http://www.
lurhq.co m/sasse r.html
*19+ “Sec unia — V irus Info rmatio n — S asse r.G,” May 2005, http://
sec unia.co m/v irus_info rmatio n/11515/sasse r.g
*20+ “F-Sec ure Co mpute r V irus Info rmatio n Page s: Witty,” May
2005, http://www.f-sec ure .co m/v -de scs/witty.shtml
*21+ C. S . D. Moo re , “The S pre ad o f the Witty Wo rm,” IEEE Sec. &
Privacy, vo l. 2, 2004, pp. 46 –50.
[22] R. A. et a l., Snort 2.1 Intrusion Detection, 2nd e d., Syng ress,
O’Re illy , 2004, pp. 490–91.
[23] S . E. D. Bo lzo ni and P. Harte l, “POSEIDON: A 2 -Tie r Ano maly -
Base d Ne two rk Intrusio n De tec tio n Syste m,” Proc. 4th IEEE Int’l Wksp.
Info. Assura nce, 2006.
*24+ “S no rt,” May 2005, http://www.sno rt.o rg
*25+ G. B. V. Be rk and R. Mo rris, “De sig ning a Frame wo rk fo r
Ac tive Wo rm De tec tio n o n Glo bal Ne two rks,” Proc. 1st IEEE
Int’l. Wksp. Info. Assura nce, 2003.
*26+ S . C. Y. Tang, “S lo wing Do wn Inte rne t Wo rms,” Proc. 24th
IEEE Int’l Conf. Distrib. Comp.. Sys., 2004.
*27+ S . C. S . Ranka, “An Inte rne t-Wo rm Early Warning Syste m,”
Proc. IEEE GLOBECOM, 2004.
*28+ S . S . J. Jung , A. Be rge r, “Fast De tec tio n o f Sc anning Wo rm Infe c tio ns,” Proc. 7th Int’l Symp. Recent Adva nces in Intrusion Detection, 2004.
[29] V . P. J. Jung et a l., “Fast Po rtsc an De tec tio n Using Seque ntial
Hy po thesis Te sting,” Proc. IEEE Symp. Sec. a nd Privacy , 2004.
*30+ D. E. N. We ave r, S. S tanifo rd, and V . Paxso n, “Wo rms vs.
Pe rime te rs — The Case fo r Hard-LANs,” Proc. 12th Annua l IEEE
Symp. High Perf. Interconnects, 2004.
[31] M. S. G. Gu et a l., “Wo rm De tec tio n, Early Warning and
Re spo nse Base d o n Loc al V ic tim Info rmatio n,” Proc. 20th
Annua l Comp. Sec. Apps. Conf., 2004.
[32] D. D. X. Qin et a l., “Wo rm De tec tio n Using Loc al Ne two rks,”
tec h. re p., Co llege o f Co mputing , Geo rg ia Tec h, 2004.
[33] C. E. S. S ing h, G. V arg hese , and S . S av ag e, “The EarlyBird
Syste m fo r Re al-Time De tec tio n o f Unkno wn Wo rms,” UCSD
tec h re p. CS2003 -0761, 2003.
*34+ L. G. Z. Che n and K. Kwiat, “Mo de ling the S pre ad o f Ac tive
Wo rms,” Proc. IEEE Comp. a nd Commun. Societies Annua l Joint Conf., 2003.
[35] S . V . J. Wu, L. Gao , and K. Kwiat, “An Effic ie nt Arc hitec ture
and Algo rithm fo r De tec ting Wo rms with V ario us Sc an Tec hniques,”
Proc. Network a nd Distrib. Sys. Sec. Symp., 2004.
[36] L. S pitzne r, Honeypot: Tracking Hackers, Addiso n-We sley , 2002.
[37] X. Q. D. Dago n et a l., “Ho neystat: Loc al Wo rm De tec tio n Using Ho ney po ts,” Proc. 7th Symp. Recent Adva nces in Intrusion Detection, 2004.
*38+ “Ho ney d V irtual Ho ney po t,” re trieve d Aug. 2005, http://
ho ney d.o rg
*39+ N. Provo s, “A V irtual Ho ney po t Frame wo rk,” Proc. 13th
USENIX Sec. Symp., 2004.
*41+ P. K. C. Matthe w V . Maho ney , “PHAD: Pac ke t He ade r Ano maly
De tec tio n fo r Ide ntify ing Hostile Ne two rk Traffic ,” FL Inst. Tec h. tec h.
re p. CS -2001-04, 2001.
*42+ S . J. S . Ke Wang , “Ano malo us Pay lo ad-Base d Ne two rk Intrusio n
De tec tio n,” Proc. Recent Adva nces in Intrusion Detection, 2004.
*43+ G. C. Ke Wang and S alv ato re J. S to lfo , “Ano malo us Pay lo adbase d Wo rm De tec tio n and S ig nature Ge ne ratio n,” Proc. 8th Int’l Symp. Recent Adva nces in Intrusion Detection, 2005.
*44+ B. M. J. Loc kwoo d, “Desig n o f a Syste m fo r Re al-Time Wo rm
De tec tio n,” Proc. 12th IEEE Annual Symp. High Perf. Interconnects,
2004.
*40+ J. C. C. Kre ibic h, “Ho neyco mb — Cre ating Intrusio n De tec tio n
S ig nature s Using Ho ney po ts,” Proc. 2nd Wksp. Hot Topics in Networks,
2003.
[45] B. K. H. Kim, “Autog raph: Toward Auto mate d, Distribute d Wo rm
S ig nature De tec tio n,” Proc. 13th USENIX Sec. Symp., 2004.
*46+ B. K. J. Ne wso me and D. So ng, “Po lyg raph: Auto matic ally
First A. MS. Vidya Mhaske -Dhamdhere has completed his master Degree In Computer Science and Engg. In year
2011.and currently working in G.H.Raisoni college of Engg, &
mgnt.pune; and association with IEEE International confe- rences reviewer. And published more than 5 paper. current research interests is in Data and network securi- ty,cryptoghaphy.
Second B. Prof. G.A. Patil is Pursing His Phd degree in computer sci. & engg, And currently working in D.Y. patil col- lege of engg. & tech .kolhaur.he has published more than 10 paper.he is also working as BOS chairman of IT and comput- er dept. in Kolhapur university,also He is LIC commity mem- ber.
IJSER © 2012