changed. The parallax RFID Reader Module initiates all communication.
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1899
ISSN 2229-5518
Mr. K.KANNAN
ABSTRACT:- In this project a highly secured ATM transaction system has been developed with the help of visual basic programming and Embedded C. The authenticator (Bank) generates a random number and provides that to the card user whenever the user inserts his card on the ATM machine. The random generated code will be send to the card user with the help of GSM technology. The user can provide this code on the ATM machine and can continue his transaction. Whenever they entered code gets wrong the door of the ATM machine gets locked and security alarms will bang. This system will help the user to secure his transaction and prevents the unauthorized usage of the card.
1. INTRODUCTION
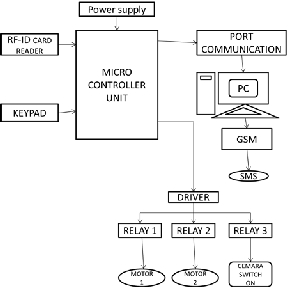
The Microcontroller based secure pin entry method is mainly developed for the prevention of theft of the ATM card and to control the usage of the ATM card by unauthorized person. The additional feature of this project is that no transaction can be done without the knowledge of the respective card holder. The main software’s that are using in this project are visual basic and embedded C. The main advantage of this project is it helps in the prevention of ATM looting. The main advantage of this system is that the card holder can remotely access hi ATM card and control the whole transaction process if his card is used by another known person who can’t be fully trusted. This system can be implemented in all the sectors where the ATM card is using. Like shopping, money transaction, online payments. Whenever the RF-ID Reader detects an active tag it generates an particular frequency digital signals and give these signals to the microcontroller whenever the microcontroller receives these digital signals from the RF-ID reader it will check for the list of mobile number that has been associated with the card frequency. Next the controller will generate a pin number of four digits and send this pin number to the visual basic interface. Each time whenever a transaction has to be done the pin number that are generating in the microcontroller will be different. The embedded C program implemented in the microcontroller mainly helps for generate pin number randomly. The pin number given to the visual basic interface will communicate with the GSM modem that has been connected with it and will give command to the
GSM modem to send the pin number to the
particular mobile number. The card user will
receive this pin number as text message on his
mobile. The pin number can be entered in the ATM
machine using 4*4keypad. Then the ATM machine
will move on to the next process. If the pin number
that has been entered in the ATM machine is
wrong the ATM card will get blocked. If the
entered pin number is correct, the user can move
on the next level of transaction. At this the
embedded C program in the microcontroller will
give command to the visual basic program to
continue the transaction and the visual basic
program will generate another message that ask
the card holder to enter the amount that the user
wants to withdraw from the ATM machine. So, at
this time the user has to enter the amount in the
mobile that has to be taken out from the ATM
machine. Then the ATM machine will continue to
next transaction level and completes the process.
On the other hand, if the entered pin number is
wrong the card will get blocked and the doors of
the ATM centre will get locked. A camera that is
provided with this will capture the image of the
person who is using that ATM card at that time.
Two motors are provided motor 1 and motor 2 for
representing the process that is happening in the
project. Motor 1 will rotate if the entered pin is
correct and if the transaction is successful. Motor 2
will rotate if the entered pin is wrong which
represents the blocking of ATM card and locking
the doors of the ATM center.
Input
SignalTransformerRectifierFilterRegulator
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1900
ISSN 2229-5518
To improve the security of money
inside the ATM machine a massage is received to the mobile phone of the actual card holder with a pin number of four digit. This number is entered in
transaction. For avoiding the chance of ATM
looting. To reduce the chance of ATM looting, each
time password is randomly generated. For higher
security aspect the password is entered in the ATM
via mobile. In the developed system there is no
chance of money transaction during shopping, e-
booking, without the knowledge of the card
holder. For improved security the whole
transaction process can be controlled through the
mobile.
Security in ATM network is necessary because ATM is widespread and many areas such as financial or medical applications, network administration, etc. Require very sensitive handling of the transmitted data. If we look at other fields of interest we see that ATM channels might be used for billing .Misuse of the ATM network, manipulation of the transmitted data, spoofing or repudiation would be fatal in billing-/ accounting system. Therefore the ATM forum, the most important committee in developing and enforcing new standard concerning ATM, introduced the ATM security specification 1.0 in
1998. The specification contains mechanism to protect transmitted data in the user- and the control plane. The management plane will be treated in phase two of the specification. The ATM security specification describes the securities that are necessary to protect the user and the control plane. Confidentially, data integrity, accountability and access control are the main objectives. In the ATM security Framework ten necessary function AF-SEC-1 to AF-SEC-10.
AF-SEC-2: controlled Access and Authorization; AF-SEC-3: Protection of confidentially;
AF-SEC-4: protection of data Integrity; AF-SEC-5: strong Accountability;
AF-SEC-6: Activity logging; AF-SEC-7: Alarm Reporting; AF-SEC-8: Audit;
AF-SEC-9: Security Recovery;
AF-SEC-10: Management of security.
However not all of those security
requirement will be discussed. AF-SEC-6 to AF-
SEC-8 are mainly logging - function that are not
subject of this review. AF-SEC-5 is essentially
accomplished using authentication and
authorization; thus it will be mentioned together
with AF-SEC-1 to AF-sec-2.
In our developed system whenever the transaction has to be done, once the card is inserted
the ATM machine using 4*4 keypad. It moves on to
the next process if the password is correct,
otherwise sends a wrong massage if the password
doesn’t match. On the password being right it
moves on to the next level of money transaction
asking for the money withdrawal. There also
would be a web camera which captures the photo
for further clarification in future if any. After the
transaction is over it display the balance amount in
the account. In the scenario where the password
doesn’t match the card would be blocked. There
would be 2 dc motors where one works on the next
process if the password is right for processing the
money and another dc motor works closing the
door if the password is wrong. If the account
holder wants to continue with the next transaction
a randomly generated password reaches his
mobile entering which he can continue the same.
• GSM Modem
• Personal computer
• Microcontroller
• RFID Reader
• Driver
• Relay
• Motor
• Keypad
• Power supply
• Embedded c
• Visual Basic
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1901
ISSN 2229-5518

changed. The parallax RFID Reader Module initiates all communication.
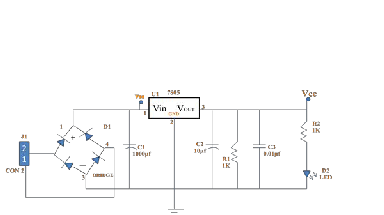
A 230v, 50Hz single phase AC power supply is given to a step down transformer to get supply. This voltage is converted to DC voltage using a Bridge Rectifier. The converted pulsating DC voltage is filtered by a 2200uf capacitor and then given to 7805 voltage regulator to obtain constant 5v supply. This 5v supply is given to all the components in the circuit. A RC time constant circuit is added to discharge all the capacitor quickly. A power supply sometimes known as a power supply unit or PSU is a device or system that supplies electrical or other types of energy to an output load or group of loads. The term is most commonly applied to electrical energy supplies, less often to mechanical ones, and rarely to others.
Radio frequency identification (RFID), an automatic recognition technology employing wireless communication, has recently drawn much attention. RFID which are electronic tags that employ RFID technologies, can be broadly classified into passive and active types of tags. Implementation and usage of the RFID reader module is straight forward. The RFID Reader Module is controlled with a single TTL-Level active-low ENABLE pin. When the/ENABLE pin is pulled LOW, the module will enter its active state and enable the antenna to interrogate for tags. The current consumption of the module will increase dramatically when the module is active .All communication is 8 data bits, no parity,1stop bit,non-inverted,least signification bit first(8N1
).The baud rate is configured for 2400bps,a standard communications speed supported by most any microprocessor or PC, and cannot be
The A89S52 is a low- power, high-performance CMOS 8-bit microcontroller with 8K bytes of in-system programmable Flash memory. The device is manufactured using Atmel’s high-density nonvolatile memory technology and is compatible with The Indus-try-standard 80C51 instruction set and pin out. The on –chip Flash allows the program memory to be reprogrammed in-system or by a conventional nonvolatile memory programmer. By combining a versatile 8-bit CPU with in-system programmable Flash on a monolithic chip, the Atmel AT89S52 is a powerful microcontroller which provides a highly –flexible and cost-effective solution to many embedded control applications. The AT89S52 provides the following standard features: 8K bytes of Flash, 256 bytes of RAM,32 I/O lines, watchdog timer ,two data pointer , three 16-bit timer/counter, a six- vector two-level interrupt architecture, a full duplex serial port, on-chip oscillator, and clock circuitry. In addition the AT89S2 is designed with static logic for operation down to zero frequency and supports two software selectable power saving modes. The Idle Mode stops the CPU while allowing the RAM, timer/counters, serial port, and interrupt system to continue functioning.
One of the most important conclusions from the early tests of new GSM technology was that the new standard should employ Time Division Multiple Access (TDMA) technology. This ensured the support of major corporate players like Nokia, Ericsson and Siemens, and the flexibility of having access to a broad range of
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1902
ISSN 2229-5518
suppliers and the potential to get product faster into the marketplace. After a series of tests, the GSM digital standard was proven to work in 1988. With global coverage goals in mind, being compatible with GSM from day one is a prerequisite for any new system that would add functionality to GSM. A data connection is established in just the same way as for a regular voice call; the user dials in and a circuit-switched connection continues during the enter session. If the user disconnects and wands to-connect, the dial-in sequence has to repeated.
A relay is an electrical switch that opens and closes under the control of another electrical circuit. In the original form, the switch is operated by an electromagnet to open or close one or many sets of contacts. It was invented by Joseph Henry in 1835.Because a relay is able to control an output circuit higher power than the input circuit, it can be considered, in a broad sense, to be a form of an electrical amplifier to make a relay operate, you have to pass a suitable pull-in and holding current (DC) through its energizing coil. And generally relay coils are designed to operate from a particular supply voltage-often 12V or 5V, in the case of many of the small relays used for electronics work. In each case the coil has a resistance which will draw the right pull-in and holding currents when it is connected to that supply voltage. So the basic idea is to choose a relay with a coil designed through the relay coil
By using the random pin number generation technique, each time when the transaction occurs a new pin number will be generated by the microcontroller. The embedded c coding done on the microcontroller helps to make this. By this each time the pin number generated will be entirely different from the previous one its helps to prevent the misuse of the ATM cart. This randomly generated is used for the transaction process in the ATM.
The Visual basic program has used here for producing the interface of secure pin entry. It mainly consists of the interface that connects the GSM modem and the ATM machine. The GSM modem and the ATM hardware is connected to the PC using the COM ports. COM ports of the GSM modem and ATM machine can be easily selected from the boxes provided on the interface. The Visual basic interface is as shown above The status of the transaction is given
through the box provided below the
ATMMACHINE text in the interface. In the Text
8box the randomly generated code will be shown
and the code that has been sended to the mobile
can be entered in the box just below of it. The
simulation can be started by clicking the START
button provided on the system.
The embedded c coding is used in the microcontroller for the random password generation during the transaction. Each time the password generated will be entirely different from the previous one. The passwords generated in the microcontroller will sended to the Visual basic interface and from there the password will give to the DSM modem as message and this message is given to the user’s mobile as message. A standard GSM modem is used here for the sending and receiving of the message. The operating frequency of the GSM modem using here is 900MHzto
1800MHz.
The progress in science &technology is a non-stop process. New things and new technology are being invented. As the technology grows day by day, we can imagine about the future in which thing we may occupy every place.
The proposed system based on Atmel microcontroller is found to be more compact, user friendly and less complex, which can readily be used in order to perform several tedious and repetitive tasks. Though it is designed keeping in mind about the need for security purpose, it extended for other purposes such as industrial & research applications. Due to the probability of Embedded technology and GSM technology made this project(“MICROCONTROLLER BASED SECURE PIN ENTRY METHOD FOR ATM”) a fully software controlled with less hardware circuit. The feature makes this system is the bass for future system. The principle of the development of science is that “nothing is impossible”. So we shall look forward to a bright
& sophisticated world.
The system did not work without the mobile network. If the users forget to bring the mobile phone, the transaction did not occur the system is work advance. So the illiterate peoples can’t use the system.
At present the transaction process in the ATM is not secured because of the same secure pin usage. So in this project a new secure pin entry method is introduced, which has
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1903
ISSN 2229-5518
improved the security of money transaction through ATM to a higher level. The GSM technology, Visual basic programming and embedded C coding has helped to improve the project.
Antovski, L. and Gusev,M.(2003) ‘A pin-Entry
Method Resilient Against Shoulder Surfing’,
vol. 04, pp. 236-245.
Stevenson, D. N. and Byrd, G. (1995) ‘Secure
Communications in ATM networks’ vol. 38,
pp. 45-52.
Kuhn, S. And Wollenweber, R. (1999) ‘ATM-
encryption with 155 Mbit/s in ATM Workshop.
Institution Electrical and Electronic Proceedings,
PP. 307-312.
Zhang, p.and Dou, j.h, and Pan, M(2008) ‘In
Information Theory, Institution Electrical and
Electronics Engineers, Transactions on, volume 13,
pages 21-27.
IJSER © 2013 http://www.ijser.org