4645667 E-mail: wasimahmad.ucitr@gmail.com
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 1271
ISSN 2229-5518
Intrusion Detection and Prevention in Cloud
Computing using Genetic Algorithm
Umar Hameed, Shahid Naseem, Fahad Ahamd, Tahir Alyas, Wasim-Ahmad Khan
—————————— ——————————
ntrusion detection systems (IDSs) are software or hardware mechanisms which helps the system to detect attacks against computer systems. IDS are composed different components such as sensors, console, and central engine. Sen- sors detect security events, console monitors events and Cen- tral Engine records events logged by the sensors in a database and use a system of rules to generate alerts from security
events received.
It is normally designed and used to monitor and detect the
invalid activities of the connected nodes and the users which
can harm the system resources, for the security of the system.
It can keep a track record of user applications, networks or
combination of activities to tack the known and unknown at-
tacks [1].
Mainly Intrusion detection system provides the following features,
• Monitoring and analyzing the user’s activities and abnormal activity.
• Auditing the system configuration and vulnerabilities.
• Critical System and data files integrity assessment and gen-
erating alarms.
• Operating System activities analysis.
• Umar Hameed is with computer science department as a research fellow at NCBA&E , Lahore, Pakistan his area of intrest is Artificial Intelligence. He is working as Deputy Controller Examination at UCEST (Lahore Leads Univer- sity), Lahore, Pakistan. Cell +92-300-4253292 E-mail: umfer@yahoo.com
• Shahid Naseem is is with computer science department as a PHD research
fellow at NCBA&E , Lahore, Pakistan his area of intrest is Artificial Intelli- gence. He is working as Assistant professor (IT) at UCEST (Lahore Leads Uni-
versity), Lahore, Pakistan. Cell +92-300-5305627
E-mail: shahid.naseem@gmail.com
• Fahad Ahmad is is with computer science department as a PHD research fellow
at NCBA&E , Lahore, Pakistan his area of intrest is Artificial Intelligence. He
is working as Hardware Enginee at PIMS, Lahore, Pakistan. Cell +92-333-
0969489 E-mail: fahadahmad84@gmail.com
• Tahir Alyas is with computer science department as a PHD research fellow at
NCBA&E , Lahore, Pakistan his area of intrest is Artificial Intelligence. He is
working as Lecturare (IT) at Garrision University, Lahore, Pakistan. Cell +92-
333-6106500 E-mail: tahir.alyas@gmail.com
• Waseem Ahmad Khan is with computer science department as a research fellow
at NCBA&E , Lahore, Pakistan his area of intrest is Artificial Intelligence. He is working as Faculty Member at NCBA&E Lahore, Pakistan. Cell +92-322-
![]()
4645667 E-mail: wasimahmad.ucitr@gmail.com
Anomaly Detection approach is based on the study of the “normal” behavior and creating a attributed model from this behavior. As abnormal behavior indicates the illegitimate use of the system so any behavior which deviates from the normal behavior is known as the anomalous [2]
Main drawback of Anomaly based approach are it often re- quires extensive training in order to find out the normal be- havior patterns and in many cases it provides the false alarms as particular normal user and system behavior can differ widely.
Misuse Detection approach is based on the principle that there exists a well defined record of already attempted intru- sion attacks. These could be matched with the current preced- ing and an exact type of attack can be detected easily. So in Intrusion detection systems that use Misuse or Signature based detection looks for a certain match from a predefined pattern of events to track the known attacks [3].
Main advantages of the misuse detection approach are that false alarms are not often occurs and it does not require exten- sive training to detect attacks.
Intrusion detection system is mainly classified in two cate-
gories based on the system monitoring.
Network Intrusion Detection System (NIDS) that monitors
the complete network traffic to track and detect proposed at-
tacks on the network and inform administrator about the at-
tack.
Another category is called Host Based Intrusion Detection
System (HIDS) that monitors a single host system. HIDS in-
volves installing an agent on the local host that monitors and
reports on the system configuration and application activity.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 1272
ISSN 2229-5518
Cloud computing is the mechanism of computing services delivery over the Internet. In cloud services individuals and businesses can use software and hardware facilities which are managed by third party at some remote locations. Some main examples of cloud services are online file storage, social net- working sites (Facebook, Twitter etc), webmail, and online business applications etc. Cloud computing model provides the facility of accessing information and sharing the computer resources from anywhere through a remote network connec- tion. Cloud computing provides a shared pool of resources, including data storage space, networks, computer processing power, and specialized corporate and user applications [4]
Main characteristics of the cloud computing are
and manage their own computing resources, like network re-
sources, storage, processing as per their requirements as
choice.
• Broad network Access: Provides the capabilities to access the
services on the internet and private networks thorough a
mechanism enables access to client platforms (e.g., mobile
phones, tablets, laptops, and workstations).
• Resource pooling: Provides the capabilities of accessing and
using the multiple pooled computing resources, from different
networks and remote data access points as required.
• Rapid elasticity: Services can be scaled and appropriated
according to the requirements in any quantity at any time.
• Measured Services: Cloud systems always provide a auto-
matic control of resources usage metering and billing accord-
ingly (eg. user accounts, storage, bandwidth usage, pro- cessing). Resources usage are monitored and controlled in accordance with the services provided and availed.
Fundamental service models of cloud computing include software-as-a-service (Saas), platform-as-a-service (Paas) and infrastructure-as-a-service (Iaas). Software as a service model provides the access of complete services like operating soft- ware, database etc. to the user managed by the cloud provid- ers. Cloud provider installs operating application software and provides the complete infrastructure platform. Cloud user can access the facilities without any installation of any kind. In business oriented models Saas provides pricing appli- cations to apply the subscription fee. Most commonly used Saas applications in use are salesforce.com, Google apps etc.
In Platform as a service cloud provider manage complete hardware, network and a platform encapsulating a layer of software and provides it as a service that can be used to build higher-level services. Cloud user can build and run their own software solutions and applications according their own re- quirements without bothering about the basic requirements of hardware and operating layers and their maintenance. PaaS offerings can provide for every phase of software develop- ment and testing, or they can be specialized around a particu- lar area such as content management.
In Infrastructure as a service model provides computers Physical or (more often) virtual machines (including storage and compute capabilities as standardized services over the network. Servers, storage systems, switches, routers, and other systems are pooled and made available to handle workloads
to the cloud users. Could users run their own operating sys- tems and applications to perform their tasks [5].
Moreover, cloud services can be made available mainly by three ways that include public clouds where cloud provider provides the storage, server and network resources to use for users. These are normally used to deploy the services which may be made available to all the general (possible) cloud us- ers. Email services, social networking sites and online photo storages are normally deployed through public cloud. Private cloud are built and deployed for some particular client or or- ganization providing the utmost control over data, security, and quality of service to the user. Weather the infrastructure is maintained in own premises or by the cloud provided, the organization have the significant control on the resources of the Private cloud. Hybrid cloud combines the characteristics of both public and private models. The ability to supplement a private cloud with the resources of a public cloud can be used to maintain service levels for rapid workload fluctuations.
Genetic algorithm is the most popular type of evolutionary algorithm. In a genetic algorithm, a population of candidate solutions (called individuals, creatures, or phenotypes) to an optimization problem is evolved toward better solutions. Each candidate solution has a set of properties (its chromosomes or genotype) which can be mutated and altered; traditionally, solutions are represented in binary as strings of 0s and 1s, but other encodings are also possible.
The evolution usually starts from a population of randomly generated individuals, and is an iterative process, with the population in each iteration is called a generation. In each generation, the fitness of every individual in the population is evaluated; the fitness is usually the value of the objective func- tion called “fitness function” in the optimization problem be- ing solved. During the process of evaluation “Crossover” is used to simulate natural reproduction and “Mutation” is used to mutation of species. The more fit individuals are stochasti- cally selected from the current population, and each individu- al's genome is modified (recombined and possibly randomly mutated) to form a new generation. The new generation of candidate solutions is then used in the next iteration of the algorithm. Commonly, the algorithm terminates when either a maximum number of generations has been produced, or a satisfactory fitness level has been reached for the population.
Although crossover and mutation are known as the main genetic operators, it is possible to use other operators such as regrouping, colonization-extinction, or migration in genetic algorithms [6].
A typical genetic algorithm requires:
1. A genetic representation of the solution domain,
2. A fitness function to evaluate the solution domain.
A standard representation of each candidate solution is as
an array of bits. Arrays of other types and structures can be
used in essentially the same way. The main property that
makes these genetic representations convenient is that their
parts are easily aligned due to their fixed size, which facilitates
simple crossover operations. Variable length representations
may also be used, but crossover implementation is more com-
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 1273
ISSN 2229-5518
plex in this case. Tree-like representations are explored in ge- netic programming and graph-form representations are ex- plored in evolutionary programming; a mix of both linear chromosomes and trees is explored in gene expression pro- gramming.
Once the genetic representation and the fitness function are defined, a GA proceeds to initialize a population of solutions and then to improve it through repetitive application of the mutation, crossover, inversion and selection operators. Gen- eral working of genetic algorithm is shown figure 1.
Figure 2: Existing Cloud IDS Model
Developing an Intrusion detection mechanism for cloud environment is quit challenging and motivated for both cloud user and cloud providers. It should cover all the normal fea- tures of a network based IDS there must exist the security fea- tures for fast and secure access to applications and data.
We propose a three layers method to detect the intrusion. The design is relaying on Software-as-a service model for provid-
Initialization Parent Selection
Parents
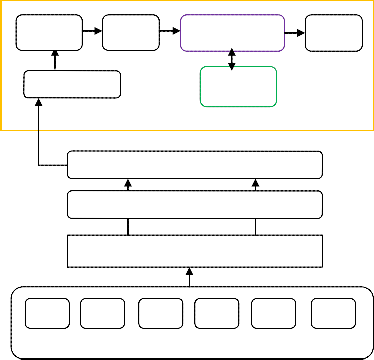
ing the security to the cloud based users.
Mutation
Segregate
Voice GeneticAlgorithm
Notifier
(Fitness Function)
Off springs
IDS Controller
Knowledge
Base
Intrusion Detection System Layer
Figure 1: General Scheme of Genetic Algorithm
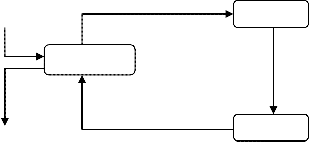
Currently used system is shown in Figure 2, which elabo- rates that in the current system users groups and cloud users, information is monitored by the agent groups and then for- warded to the cloud computer service components which fur- ther forwards information to the collectors which are respon- sible to forward the information to the appropriate analysis engine for detection.
Intrusion detection service component is mainly responsible for detection with its three main components. Detection En- gine is a sophisticated decision and pattern matching mecha- nism. It analysis data came from the collector and matches it to known patterns of activity stored in the signature database. Event Publisher provides the results reports to the users. IDS
Users
Event Service Layer
Secure Connection
Hardware Layer
Cloud Network Users
Figure 3: Proposed Framework of IDS
Collector
Event Publisher
IDS Controller
Detection Engine
Collector
Intrusion Detection Service Component
Cloud Computer Service Components
Secure Connection
Agents Groups
User Internal Network
flexibility. It forwards the request to the event service layer through the secure connection. The hardware is just like an agent.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 1274
ISSN 2229-5518
ternal intrusion) checks message and forwards these messages to the intrusion detection layer.
Genetic Algorithm unit.
ing and decision making unit performs these tasks by using the genetic algorithm technique. It analysis data (voice data) in details and matches the same with known behaviors stored in the existing knowledge base. Fitness Function “X=δX0 ” is the
key for checking the match.
Knowledge
Base
START
Initialize Population
NO Check
Existence
Set generation counter
Fitness Function
X = δX0
First of all it checks the existence by matching the location in knowledge base. If the location is not matched with any exist- ing details in the Knowledge base it provides an exit from the system. If existence check is passed it analysis and matches the voice records for the proper recognition based on the fit- ness function X=δX0.
If the fitness is proved then different authentication checks are implemented to reach the result at each step it apply genetic algorithm.
If the desired record is not matched it reproduces the new rec- ord by mutation, performs fitness test X=δX0 and rechecks from the data in knowledge base. Same is continued for three generations as per termination criteria. Based on the said re- sults it identifies the malicious behavior, provides access or exit and generates the alerts through the notifier.
Knowledge
Base
Generation Counter Check t > 3
Match condi- tion with KB data
Reproduction through
Mutation process
Generation counter t = t+ 1
YES
YES
Working of the genetic unit is displayed in figure 4.
(Go to next level check)
or
(Give access / Terminate )
STOP
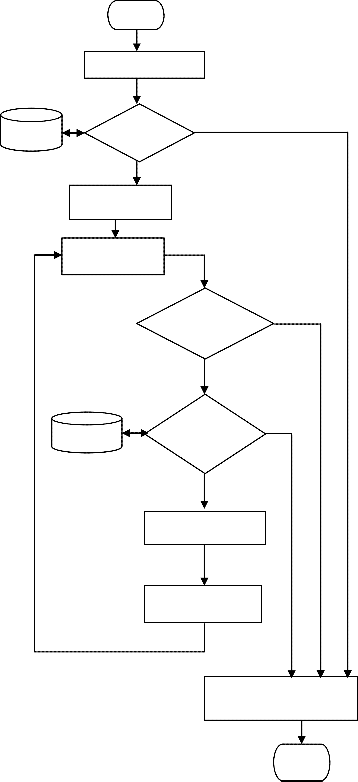
Figure 4: Working of Genetic Algorithm Unit
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 1275
ISSN 2229-5518
It is concluded that use of genetic algorithm with fixed genera- tional iteration in intrusion detection system helps in enhanc- ing the security features in cloud computing. As genetic unit checks and restricts intrusion attacks for certain threshold lev- el of generations and thus do not provides access to the data unless security checks are completed. The proposed model is focused on voice data validity, genetic algorithm is a signifi- cant approach to detect, prevent and thus reduce the intrusion in this regard.
Our current proposed framework for IDS is handling voice intrusion only. An enhanced implementation of model to take care of all other data aspects for IDS, like high definition visual or biometric data and simulation test is prospective goals. IDS system can be enhanced further by encapsulating the adaptive data mining features with the efficient evolutionary compu- ting methods for effective intrusion detection model based on the large adaptive knowledge base.
[1] S. INSTITUTE, "Understanding Intrusion Detection System," SANS INTITUTE INFO SECTION READING ROOM, 2001.
[2] A. Zarrabi and A. Zarrabi, "Internet Intrusion Detection System Ser- vice in a Cloud," IJCSI International Journal of Computer Science, vol. 9, no. 5, 2012.
[3] C. Lawrence, "Intrusion Prevention Systems: The Future of Intrusion Detection," in Intrusion Prevention Systems: The Future of Intrusion Detection, Auckland, 2004.
[4] Office of Privacy Commissioner Of CANADA, "www.priv.gc.ca,"
Introduction to Cloud Computing. [Online].
[5] M. Boniface, B. Nasser, J. Papay and S. C. Phillips, "Platform-as-a- Service Architecture for Real-Time Quality of Service Management in Clouds," in Internet and Web Applications and Services (ICIW), 2010
Fifth International Conference on, Barcelona, 2010.
[6] A. Ziarati, ""A multilevel evolutionary algorithm for optimizing nu- merical functions"," IJIEC, vol. 2, 2011.
IJSER © 2014 http://www.ijser.org