International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1424
ISSN 2229-5518
Impact of Node Mobility of Routing
Protocols on MANET
Shekhar Srivastava 1, Akhilesh Yadav 2, Ajay Kumar 3
1, 2 Department of Computer Science and Engineering
Kanpur Institute of Technology, Kanpur
3 Institute of Technology & Management Gida, Gorakhpur shekharsri@gmail.com1, akhil_jnp@rediffmail.com2, ajay.4cse@gmail.com3
Abstract - A Mobile Ad-Hoc Network (MANET) is a self-configuring network of mobile nodes connected by wireless links to form an arbitrary topology without the use of existing infrastructure. In this dissertation, we studied the effects of various mobility models on the performance of three routing protocols Dynamic Source Routing (DSR), Ad hoc On-Demand Distance Vector (AODV) and Wireless Routing Protocol (W RP). For experiment purposes, we have considered the following three metrics to compare the routing protocols: Packet Delivery Ratio, Average End to End Delay and Drop Ratio. Performance comparison has been conducted across varying the mobility of nodes. Experiment results illustrate that performance of the routing protocol varies across different mobility models.
Keywords: MANET, AODV, DSR, W RP, PDR.
—————————— ——————————
1. INTRODUCTION
Mobile hosts and wireless networking hardware are becoming widely available. There are currently two variations of mobile wireless networks. The first is known as infrastructure networks, i.e. those networks with fixed and wired gateways. The bridges for these networks are known as base stations. A mobile unit within these networks connects to, and communicates with, the nearest base station that is within its communication radius. The second type of mobile wireless networks is the infrastructure less mobile network, commonly known as an ad hoc network. A mobile ad hoc network is a network in which a group of mobile computing devices communicate among themselves using wireless radio, without the aid of a fixed networking infrastructure[1][2].
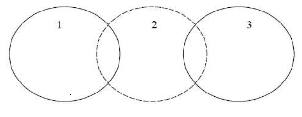
A Mobile Ad Hoc Network generally does not have any infrastructure and each mobile host also acts as a router. Communication between various hosts takes place through wireless links. Direct communication can take place between hosts that are within the communication range of the antennas of the respective hosts; otherwise, communication is achieved through multi-hop routing. Figure 1 represents a MANET of 3 nodes. Node 2 can communicate directly with Node 1 and Node 3. But any communication between Nodes 1 and 3 must be routed through Node 2[1].
Figure 1: A MANET of 3 Nodes
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1425
ISSN 2229-5518
2. ROUTING PROTOCOLS FOR
MANETS
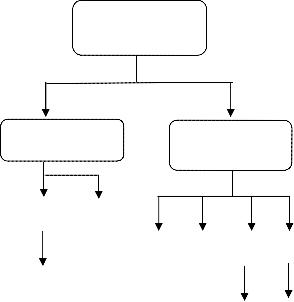
Multihopping, mobility, large network size combined with device heterogeneity, bandwidth and battery power limitations make the design of adequate routing protocols a major challenge. In recent years, various different routing protocols have been proposed for wireless ad hoc networks [2].
AdHoc Routing
Protocols
2.2 On-Demand or Reactive Protocols
Reactive protocols discover routes only as needed. When a node wishes to communicate with another node, it checks with its existing information for a valid route to the destination. If one exists, the node uses that route for communication with the destination node. If not, the source node initiates a route request procedure, to which either the destination node or one of the intermediate nodes sends a reply back to the source node with a valid route. A soft state is maintained for each of these routes – if the routes are not used for some period of time, the routes are considered to be no longer needed and are removed from the routing table; if a route is used before it expires, then the lifetime of the route is extended [2].
Table Driven
DSDV WRP CGSR
On-Demand
Driven
AODV DSR LMR ABR TORA SSR
2.3 Dynamic Source Routing (DSR)
Dynamic Source Routing (DSR) [5], as the name suggests, is based on the concept of source routing. There are no periodic routing advertisements; instead, routes are dynamically determined based on cached information or on the result of a route discovery process. In source routing, the sender of the packet specifies the complete sequence of the nodes that the packet has to take. The sender explicitly lists this route in the packet’s header, identifying each forwarding “hop” by the address
of the next node to which the packet must be sent
Figure 2: Categorization of Routing Protocols
2.1 Table Driven or Proactive Protocols
Table-driven protocols (proactive protocols) generate frequent updates of network topology information to maintain a consistent view of the network at all nodes. These nodes are required to maintain tables containing topology information, so that any node wishing to communicate with any other node may do so by computing a route to the destination node from the table. It is fairly expensive in terms of table size and control overhead to maintain a table of topological information of all nodes. The chief disadvantage of this method is that the nodes may be maintaining topological information about nodes with which it
may never communicate [1] [3].
on its way to the destination host. A key advantage of source routing is that intermediate hops do not need to maintain routing information in order to route the packet they receive, since the packets themselves already contain all the necessary routing information. Unlike conventional routing protocols, the DSR protocol does not periodically transmit route advertisements, thereby reducing control overhead, particularly during periods when little or no significant host movement is taking place. The DSR protocol consists of two mechanisms: Route Discovery and Route
Maintenance. When a mobile node wants to send a
packet to some destination, it first consults its route cache for a non-expired route. If the node does not
have such a route, it will initiate route discovery by
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1426
ISSN 2229-5518
broadcasting a route request (RREQ) packet, which contains the addresses of the source node and the destination, and a unique sequence number “request id”, which is set by the source node. Each node in the network maintains a list of (source address, request id) pair that it has recently received from any host in order to detect duplicate route requests received. On receiving a RREQ, a node checks to see if it has already received a request with the same (source address, request id) pair (duplicate RREQ). In such an event, or if the node sees its own address already recorded in the request (routing loop), it discards the copy and does not process it further. Otherwise, it appends its own address to the route record in the route request packet and re-broadcasts the query to its neighbors.
When the request packet reaches the destination, the destination node then sends a route reply packet to the source with a copy of the route. If a node can complete the query from its route cache,
node’s route cache is no longer valid. Each node along the route, when transmitting the packet to the next hop, is responsible for detecting if its link to the next hop has broken. Many wireless MAC protocols, such as IEEE 802.11, retransmit each packet until a link-layer acknowledgement is received, or until a maximum number of retransmission attempts have been made. Alternatively, DSR may make use of a passive acknowledgement. When the retransmission and acknowledgement mechanism detects that the link is broken, the detecting node unicasts a Route Error packet (RERR) to the source of the packet. Every hop en-route to the source that received or overheard the RERR removes the broken link from any route caches and truncates all routes that contain this hop. The source can then attempt to use any other route to the destination that is already in its route cache, or can invoke Route Discovery again to find a new route.
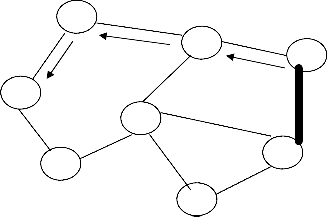
N1-N2-N5-N8
it may unicast a route reply (RREP) packet to the source without propagating the query packet further. Furthermore, any node participating in route discovery can learn routes from passing data packets and gather this routing information into its route cache. Figure 3 (a) and 3 (b) is an example of
the creation of a route record in DSR [5].
N2
S N1-N2-N5-N8
N1
N4
D
N5
N8
N1-N2-N5-N8
N2 N1-N2
N1
S
N1-N3-N4
N1
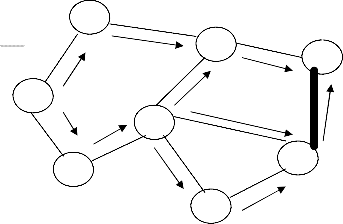
N7
D N3
N5 N1-N2-N5
N8 N6
N1-N3-N4-N
N4
N1 N1-N3-N4
N7
Figure 3(b): Propagation of the Route Reply with
the Route Record
N3 N1-N3
N1-N3-N4 N6
N1-N3-N4-N6
The DSR protocol is intended for networks in which the mobile nodes move at a moderate speed with respect to packet transmission latency [5]. An advantage of DSR over some on-demand protocols
Figure 3(a): Building the Route Record during the
Route Discovery
Route Maintenance is used to detect if the network topology has changed such that the route in the
is that DSR does not use periodic routing advertisements, thereby saving bandwidth and reducing power consumption. On the other hand, as the network becomes larger, control packets and
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1427
ISSN 2229-5518
data packets also become larger because they need to carry addresses for every node in the path. Also, aggressive use of route cache and the absence of any mechanism to expire stale routes will cause poor delay and throughput performance in more stressful situations.
2.4 Ad-hoc On-Demand Distance Vector
Routing (AODV)
Ad-hoc On-Demand Distance Vector Routing (AODV) [6] is essentially a combination of both DSR and DSDV. It borrows the conception of sequence numbers from DSDV, plus the use of the on-demand mechanism of route discovery and route maintenance from DSR. It is called a “pure on-demand route acquisition system”; nodes that do not lie on active paths neither maintain any routing information nor participate in any periodic routing table exchanges. It is loop-free, self- starting, and scales to a large number of mobile nodes. When a source node needs to send a packet to a destination node for which it has no routing information in its table, the Route Discovery process is initiated. The source node broadcasts a route request (RREQ) to its neighbors. Each node that forwards the RREQ packet creates a reverse route for itself back to source node. Every node maintains two separate counters: a node sequence number and a broadcast id. Broadcast id is incremented when the source issues a new RREQ. Together with the source's address, it uniquely identifies a RREQ. In addition to the source node's IP address, current sequence number and broadcast ID, the RREQ also contains the most recent sequence number for the destination which the source node is aware of. A node receiving the RREQ may unicast a route reply (RREP) to the source if it is either the destination or if it has a route to the destination with corresponding sequence number greater than or equal to that contained in the RREQ. Otherwise, it re-broadcasts the RREQ. Each node that participates in forwarding a RREP packet back to the source of RREQ creates a forward route to the source node. Each node remembers only the next hop unlike source routing which keeps track of the entire route. Nodes keep track of the RREQ’s source IP address and broadcast ID. If they receive a RREQ
packet that they have already processed, they
discard the RREQ and do not forward it. As the RREP propagates back to the source, nodes set up forward pointers to the destination. Once the source node receives the RREP, it may begin to forward data packets to the destination. At any time a node receives a RREP (for any existing destination in its routing table) containing a greater sequence number or the same sequence number with a smaller hop count, it may update its routing information for that destination and begin using the better route. Routes are maintained as follows: If an upstream node in an active route senses a break in the active route, it can reinitiate the route discovery procedure to establish a new route to the destination (local route repair) or it can propagate an unsolicited RERR with a fresh sequence number and infinity hop count to all active upstream neighbors. Those nodes subsequently relay that message to their active neighbors. This process continues until all active source nodes are notified. Upon receiving notification of a broken link, source nodes can restart the discovery process if they still require the destination. Link failure can be detected by using Hello messages or by using link-layer acknowledgements (LLACKS). The main benefit of AODV over DSR is that the source route does not need to be included with each packet, which results in a reduction of routing protocol overhead. Because the RREP is forwarded along the path established by the RREQ, AODV requires bidirectional links.
2.5 Wireless Routing Protocols (WRP)
WRP uses an enhanced version of the distance- vector routing protocol which uses the Bellman- Ford algorithm [9] to calculate paths. Because of the mobile nature of the nodes within the MANET, the protocol introduces mechanisms which reduce route loops and ensure reliable message exchange. WRP, similar to DSDV, inherits the properties of the distributed Bellman-Ford algorithm. To counter the count-to-infinity problem and to enable faster convergence, it employs a unique method of maintaining information regarding the shortest distance to every destination node in the network and the penultimate hop node on the path to every destination node. Since WRP, like DSDV, maintains an up-to-date view of the network,
every node has a readily available route to every
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1428
ISSN 2229-5518
destination node in the network. It differs from DSDV in table maintenance and in the update procedures. While DSDV maintains only one topology table, WRP uses a set of tables to maintain more accurate information. The tables that are maintained by a node are the following: distance table (DT), routing table (RT), link cost table (LCT), and a message retransmission list (MRL).
The DT contains the network view of the neighbors of a node. It contains a matrix where each element contains the distance and the penultimate node reported by a neighbor for a particular destination. The RT contains the up-to-date view of the network for all known destinations. It keeps the shortest distance, the predecessor node (penultimate node), the successor node (the next node to reach the destination), and a flag indicating the status of the path. The path status may be a simple path (correct), or a loop (error), or the destination node not marked (null). The LCT contains the cost (e.g., the number of hops to reach the destination) of relaying messages through each link. The cost of a broken link is infinity. It also contains the number of update periods (intervals between two successive periodic updates) passed since the last successful update was received from that link. This is done to detect links breaks. The MRL contains an entry for every update message that is to be retransmitted and maintains a counter for each entry. This counter is decremented after every retransmission of an update message. Each update message contains a list of updates. A node also marks each node in the RT that has to acknowledge the update message it transmitted. Once the counter reaches zero, the entries in the update message for which no acknowledgments have been received are to be retransmitted and the update message is deleted. Thus, a node detects a link break by the number of update periods missed since the last successful transmission. After receiving an update message, a node not only updates the distance for transmission neighbors but also checks the other neighbors’ distance, hence convergence is much faster than DSDV.
3. SIMULATION ENVIRONMENT
Simulation is based on the same environment for AODV, DSR and WRP Routing Protocols in GloMoSim version 2.02. Because mobility is the key reason for packet losses, we design the scenarios for comparing the performance of AODV, DSR and WRP based on different mobility patterns. The mobility pattern can be determined by max movement speed and the pause time during simulation. So the scenarios combining four different max movement speeds and three different pause times will be simulated. The max movement speeds are 1m/s, 15m/s, 30m/s and
45m/s; the pause times are: 0, 50 seconds, and 100 seconds. Table 1 summarizes other scenario parameters for AODV, DSR and WRP.
3.1 SIMULATION MODEL
The wireless network consists of 30 numbers of nodes which are distributed uniform in a grid area of 1000m X 1000m. The data packet size is of 512 bytes. The simulation time is 600sec. The simulation model [8] with parameters is listed in table 1.
Table 1: Simulation Parameters
Traffic Pattern | CBR |
Simulation Time | 600 seconds |
Simulation Area | 1000m*1000m |
Total Nodes | 30 |
The Data Packet Size | 512 byets |
Node Placement | Uniform |
Speed of Node | 1,15, 30 and 45 m/s |
Pause Time | 0, 50 and 100 sec. |
3.2 TRAFFIC MODEL
The traffic model used is CBR (Constant Bit Rate). CBR Model generates traffic at a constant rate of
512 Byte each at the start of the simulation up to
the end of the simulation. The interdeparture time for each item is 1 second.
4. RESULTS
Three performance metrics are used for measuring the performance of AODV, DSR and WRP Routing Protocols. The simulation results are shown in the
form of graph that represents (i) Packet Delivery
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1429
ISSN 2229-5518
Ratio, (ii) Average End to End Delay and (iii) Drop
Ratio.
(i) Packet Delivery Ratio: Number of Data Packets Delivered over Number of Data Packets Generated. “Number of Data Packets Delivered” is the total number of received data packets by destinations; “Number of Data Packets Generated” is the total number of generated data packets by sources.
Figure 4.1 (a), (b) and (c) shows the graph of AODV, DSR and WRP routing protocol for packet delivery ratio [9] between the speed of the node by varying pause time.
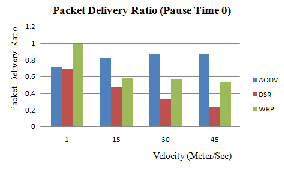
Figure 4.1 (a): PDR Vs Mobility (Pause Time 0)
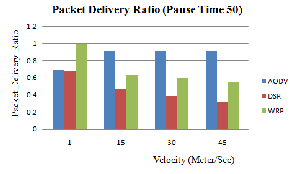
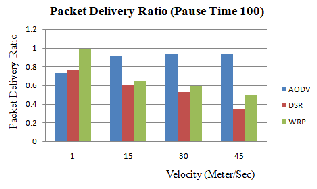
Figure 4.1 (b): PDR Vs Mobility (Pause Time 50)
Figure 4.1 (c): PDR Vs Mobility (Pause Time 100)
(ii) Average End to End Delay: average packet delivery time from a source to a destination. First for each source-destination pair, an average delay for packet delivery is computed. Then the whole average delay is computed from each pair average delay. Figure 4.2 (a), (b) and (c) shows the graph of AODV, DSR and WRP routing protocol for end to end delay [9] between the speed of the node by varying pause time. End-to-end delay includes the delay in the send buffer, the delay in the interface queue, the bandwidth contention delay at the MAC, and the propagation delay.
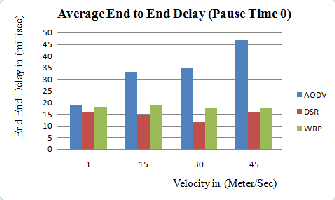
Figure 4.2 (a): Average End to End Delay Vs
Mobility (Pause Time 0)
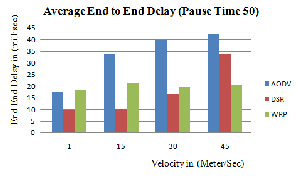
Figure 4.2 (b): Average End to End Delay Vs
Mobility (Pause Time 50)
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1430
ISSN 2229-5518
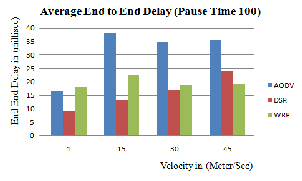
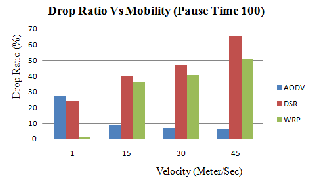
Figure 4.2 (c): Average End to End Delay Vs
Mobility (Pause Time 100)
(iii) Drop Ratio: Packet Drop rate is one of the indicators for network congestion. In wireless environment, due to the physical media and bandwidth limitations, the chance for packet dropping is increased. Therefore we choose it as one metric.
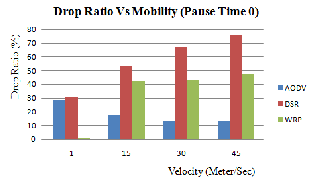
Figure 4.3 (a): Drop Ratio Vs Mobility (Pause
Time 0)
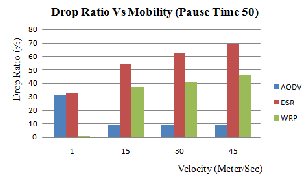
Figure 4.3 (b): Drop Ratio Vs Mobility (Pause Time
50)
Figure 4.3 (c): Drop Ratio Vs Mobility (Pause
Time 100)
Figure 4.3 (a), (b) and (c) shows the graph of AODV, DSR and WRP routing protocol for drop ratio [9] between the speed of the node by varying pause time.
4. CONCLUSION
In this paper we have simulated the AODV, DSR and WRP routing protocols on GloMoSim Simulator. The performance of the protocols was measured with respect to metrics like Packet delivery ratio, end to end delay and Drop Ratio. Simulations were carried out with identical networks and running different protocols on the mobile node. The simulation is divided in three parts basis on the pause time (i.e. 0, 50 and 100 second). Here we conclude as:
1. AODV performs well than DSR and WRP (in reference to packet delivery ratio) if the node mobility is high.
2. WRP has performed well when the node mobility is less.
3. Packet delivery ratio is decreases as the pause time decreases for all the protocols.
4. WRP and DSR have slightly different in end to end delay with varying the speed of the node while AODV varying highly with the mobility.
5. WRP has lower end to end delay in comparison to DSR and AODV.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1431
ISSN 2229-5518
6. DSR has higher drop ratio in comparison to
AODV and WRP.
5. REFERENCES
[1] S. Corson and J. Macker, Mobile Ad hoc Networking (MANET): Routing Protocol Performance Issues and Evaluation Considerations, RFC: 2501, January 1999.
[2] Carlo Kopp, “Ad Hoc Networking”, Systems Journal, pp 33- 40, 1999.
[3] F.Bai, A.Helmy, “A Survey of Mobility Modeling and Analysis in Wireless Adhoc Networks” in Wireless Ad Hoc and Sensor Networks, Kluwer Academic Publishers, 2004.
[4] F. Bai, N. Sadagopan and A. Helmy, "IMPORTANT: A framework to systematically analyze the Impact of Mobility on Performance of Routing protocols for Adhoc Networks, IEEE INFOCOM, pp. 825-835, 2003.
[5] David B. Johnson, David A. Maltz, Yih-Chun Hu, The Dynamic Source Routing (DSR) Protocol for Mobile Ad Hoc Networks.draft-ietf-manet-dsr-10.txt, July
2004.
[6] Charles E. Perkins and Elizabeth M. Royer, “Ad hoc On- Demand Distance Vector Routing”, Proceedings of the
2nd IEEE Workshop on Mobile Computing Systems and Applications, New Orleans, LA, February 1999.
[7] Bhavyesh Divecha , Ajith Abraham, et al, “Impact of
Node Mobility on MANET Routing Protocols Models”
[8] Ajay Kumar and S.P.Singh, “Performance Evaluation of
Multicast Routing Protocols”
[9] D. Cavendish and M Gerla,”Internet QoS Routing using the Bellman Ford Algorithm”
IJSER © 2013 http://www.ijser.org












