International Journal of Scientific & Engineering Research, Volume 3, Issue 10, October-2012 1
ISSN 2229-5518
Face Detection and Tracking System
Susmit Sarkar, Arindam Bose
Abstract— Security Measures are one of the things in which technology had entered long time back. Security without Technology cannot be thought of in modern times. Be it in any Bank, Corporate buildings, Educational Institute, anywhere the utilization of vis ion based sys- tems are used in order to keep a check over the activities going at that place. Robomaniac Intelligent Tracking System is an intelligent sys- tem which can be used for security purposes. This project combines the joint venture to capture the frames from a camera, det ect the fac- es, saves the detected faces and tracks the faces.
Index Terms— Artificial intelligence, Database management, Face detection, Image processiong, Microcontroller, Security system, Tracking system, USART.
1 INTRODUCTION
—————————— ——————————
OBOMANIAC Intelligent Tracking System is an intelli- gent system which can be used for security purposes. This project combines the joint venture to capture the frames
from a camera, detect the faces, saves the detected faces and tracks the faces.
This project has six distinct modules:
1. Face detection from the frame and creation of image
and video database.
2. Movement of camera as per movement of person.
3. Counter for how many persons are inside the room.
4. Natural Language Processing
5. Face Recognition System and
6. User interface
In this project we have used a Digital camera to acquire the
image. Then we detected the face from the image and stored
the face in a database for future use. The system tracks the face by the camera and it stores all the frames in a high FPS MPEG
movie.
2 PROJECT DESCRIPRION
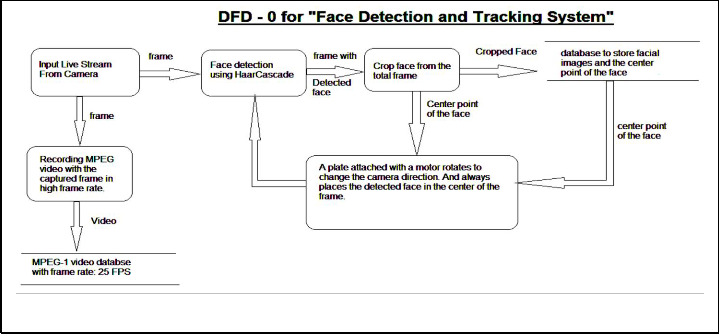
2.1 Data Flow Diagram
Fig. 1 shows the Data Flow Diagram of the whole objective. Live stream is input as frames and MPEG video is recorded from the captured frame in high frame rate. Those MPEG vid- eos are stored in the video database with frame rate of 25 FPS. Now from the previously captured frame, faces are detected using HaarCascade algorithm. If an impression of face is de- tected from any of the image the face will be cropped from the total frame. The image and the centre point of the face is then stored in the facial image database. Now a plate attached to the motor is rotated to change the camera direction and it al- ways places the detected face in the centre of the frame to track the person.
Fig. 1. Data Flow Diagram
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about Face Detection and Tracking System 2
ISSN 2229-5518
2.2 The Face Detection
The basic idea behind the Face detection is facial color de- tection. We all know that human skin consists of a wide range of colors. If by any means we could detect those ranges of col- ors, we can detect a face. This is the basic idea behind face de- tection. But as the range is too high we cannot put all the data just by coding. So we have to take certain idea from the field of Artificial Intelligence. We developed a Simple algorithm of learning. The idea was that we will choose some random faces and the computer will take their picture, detect the compo- nents of their skin color separately as RGB and stores those data in a table known as a Look up table. This look up table is maintained in a XML file and is incorporated into the code by use of a classifier.
After the face is detected by the color threshold, we draw a rectangle box around the detected face. (In our system, it is a
25,000 line long XML file (Look-up table). So; we ensured the accuracy as 92 %)This rectangle now becomes our Region of Interest (ROI). We store this ROI in a Database, so that later we can access the database to see the people who came to the room. At the same time the frames where we get the ROI is joined to form a High FPS Mpeg Video. As we will send the video over internet, so we recorded the video in high frame rate to decrease the video size. But in case of face images we used lossless format .bmp. So, the image size will be increased, but a lossless image format is always better for a future analy- sis. Though the space complexity will increase, but the time complexity will decrease. And in a security system, system speed is a notable issue. Detected faces and videos are shown in Fig. 2 and Fig. 3 respectively.
Fig. 2. Tracking videos
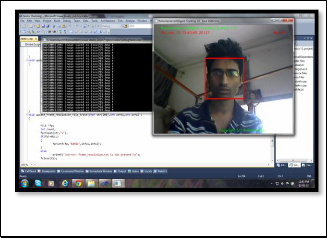
Then from the ROI the centre of the face is detected by the meeting point of the diagonals of the rectangle box. But this position is with respect to the ROI and not with respect to the original picture. So we have to again convert them with re- spect to the whole frame. After that the modified coordinate is written in a text file in a queue fashion.
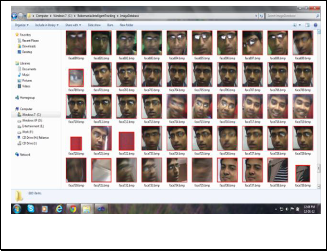
Fig. 3. Face is detected through the program running behind
Fig. 1. Detected faces stored as images
2.3 Hardware and Tracking
After detection of the face we need to trace that by the camera. So we set the camera on plate fitted with a stepper motor at the base. For controlling the motor we build a con- troller board with ATMega16 microcontroller, Motor Driver and RS232 USART IC. The motor Driver consisted of TIP122
Darlington-Pair Transistors. RS232 is used in order to access the serial port with the controller.
The tracking part is done in MATLAB. After detection as
mentioned earlier the data is written in a text file. Through
MATLAB we read the data and check whether the coordinate
is greater than the screen’s centre. If it is greater then write an
‘R’ in the serial port and if it is less we write an ‘L’ in the port.
Now via the microcontroller we are continuously checking the serial port and whenever the USART finds any data in the port
it sends that data to the microcontroller. The Microcontroller is
IJSER © 2012
http://www.ijser.org
The research paper published by IJSER journal is about Face Detection and Tracking System 3
ISSN 2229-5518
programmed with a Case structure which states that if ‘R’ is detected in the port, then the motor will rotate to the right and if it detects ‘L’ then the motor will move towards the left.
2.4 Software
Any security device consists of a database which can be viewed later. Here also we store the ROI’s in a database, for accessing the database software is being made so that just by entering the date we can find the peoples who entered the room on that date. The software is prepared in C# in visual studio. Using this system we can query over the image data- base as per the creation date of the images. So, this interface makes the total detection, database management and query system easy and user friendly. Also we have included a sys- tem that the databases will be mailed as an attachment to a particular mail address after a certain interval. If there is any physical damage to the total hardware system, also then we can retrieve the images and videos via internet.
2.4 Problems
Though we are using OpenCv, we can reduce the pro- cessing lag to a large scale but as we are using a single webcam to reduce the project cost, certain lag will always be there. Another important problem is that as the detection is based on color, the whole system becomes light dependent and for that the size of the look up table increases exponential- ly.
3 APPLICATION
We can use this system in a robot eye to track any particular human face when the robot is talking with a human being. In any examination hall, movie hall or product release house, we can use this system to record human activities. From which later the emotion can be detected. As this system is made only using a single camera so the set-up cost is very low. For higher technology (face tracking) we were able to short-sized the pro- ject cost as only USD 50.
4 CONCLUSION
Although a conclusion may review the main points of the pa- per, do not replicate the abstract as the conclusion. A conclu- sion might elaborate on the importance of the work or suggest applications and extensions. Authors are strongly encouraged not to call out multiple figures or tables in the conclusion— these should be referenced in the body of the paper.
ACKNOWLEDGMENT
We wish to thank Dr. Alok Ghosh, Principal of Future Insti- tute of Engineering and Management, Prof. Tapas Roy, head of the department of computer science engineering and Prof. Debasish Chakraborty, head of the department of electronics and communication engineering of Future Institute of Engi- neering and Management for their sincere help.
REFERENCES
[1] G. Bradsky, A. Kaehler, Learning OpenCV: Computer Vision with the
OpenCV Library.
[2] RC. González, RE. Woods, Digital Image Processing.
[3] Tim Morris, Computer Vision and Image Processing. Palgrave Macmil- lan. ISBN 0-333-99451-5, 2004.
[4] R. Fisher, K. Dawson-Howe, A. Fitzgibbon, C. Robertson, E. Trucco, Dictionary of Computer Vision and Image Processing. John Wiley. ISBN
0-470-01526-8, 2005.
[5] Tinku Acharya and Ajoy K. Ray, Image Processing - Principles and
Applications. Wiley InterScience, 2006.
[6] ATmega16 Datasheet, 2466N–AVR–10/06.
[7] TIP122 Datasheet, Rev. 1.0.0, October 2008.
[8] MAX232 Datasheet, SLLS047I – February 1989 – revised October
2002.
[9] Image Processing, http://en.wikipedia.org/wiki/Image_processing
2012.
[10] OpenCV, http://opencv.willowgarage.com/wiki, 2012.
————————————————
Susmit Sarkar is a B.Tech student of computer science engineering in Fu- ture Institute of Engineering and Management of West Bengal University of Technology, India, PH-+918961459411. E-mail: susmit.srkr@gmail.com
Arindam Bose is a B.Tech student of electronics and communication engi- neering in Future Institute of Engineering and Management of West Ben- gal University of Technology, India, PH-+919051320505. E-mail: adam- bose1990@gmail.com. He is the author of several article papers published in International Journals.
IJSER © 2012
http://www.ijser.org