International Journal of Scientific & Engineering Research Volume 2, Issue 4, April-2011 1
ISSN 2229-5518
Enhancement of Person Identification using Iris
Pattern
Vanaja roselin.E.Chirchi, Dr.L.M.Waghmare , E.R.Chirchi
Abstract — The biometric person identification technique based on the pattern of the human iris is well suited to be applied to access control. Security systems having realized the value of biometrics for two basic purposes: to verify or identify users. In this busy world, identification should be fast and efficient. In this paper we focus on an efficient methodology for identification and verification for iris detection using Haar wavelet and the classifier used is Minimum hamming distance, even when the images have obstructions, visual noise and different levels of illuminations.
Index Terms—Biometrics, Iris identification, Haar wavelet, occluded images, veriEye.
—————————— • ——————————
1. Introduction
iometrics which refers to identifying an individual by his or her physiological or behavioral characteristics has capability to distinguish between authorized user and an imposter. An advantage of using biometric authentication is that it cannot be lost or forgotten, as the person has to be physically present during at the point of identification process [9].Biometrics is inherently more reliable and capable than traditional knowledge based and token based techniques. The commonly used biometric features include speech, fingerprint, face, Iris, voice, hand geometry, retinal identification, and body odor
identification [10] as in Fig.1

Fig. 1: Examples of Biometrics
To choose the right biometric to be highly fit for the particular situation, one has to navigate through some complex vendor products and keep an eye on future developments in technology and standards. Here comes a list of Biometrics with comparatives:
Facial Recognition: Facial recognition records the spatial geometry of distinguishing features of the face. Different vendors use different methods of facial recognition, however, all focus on measures of key features of the face. Facial recognition has been used in projects to identify card counters or other undesirables in casinos, shoplifters in stores, criminals and terrorists
in urban areas. This biometric system can easily spoof by
the criminals or malicious intruders to fool recognition system or program. Iris cannot be spoofed easily.
Palm Print: Palm print verification is a slightly modified form of fingerprint technology. Palm print scanning uses an optical reader very similar to that used for fingerprint scanning; however, its size is much bigger, which is a limiting factor for use in workstations or mobile devices.
Signature Verification: It is an automated method of
examining an individual’s signature. This technology is dynamic such as speed, direction and pressure of writing, the time that the stylus is in and out of contact with the “paper”. Signature verification templates are typically 50 to 300 bytes. Disadvantages include problems with long-term reliability, lack of accuracy and cost.
Fingerprint: A fingerprint as in Fig.1 recognition
system constitutes of fingerprint acquiring device, minutia extractor and minutia matcher. As it is more common biometric recognition used in banking, military etc., but it has a maximum limitation that it can be spoofed easily. Other limitations are caused by particular usage factors such as wearing gloves, using cleaning fluids and general user difficulty in scanning.
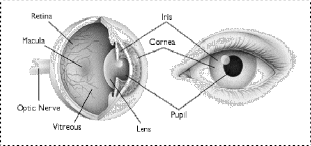
Iris Scan: Iris as shown in Fig.2 is a biometric
feature, found to be reliable and accurate for authentication process comparative to other biometric feature available today. As a result, the iris patterns in the left and right eyes are different, and so are the iris patterns of identical twins. Iris templates are typically around 256 bytes. Iris scanning can be used quickly for both identification and verification applications because of its large number of degrees of freedom. Iris as in Fig. 2 is like a diaphragm between the pupil and the sclera and
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 4, April-2011 2
ISSN 2229-5518
its function is to control the amount of light entering through the pupil. Iris is composed of elastic connective tissue such as trabecular meshwork. The agglomeration of pigment is formed during the first year of life, and pigmentation of the stroma occurs in the first few years [7][8].
further implementation we will be using Chinese academy of science-Institute of automation (CASIA) iris image database available in the public domain [7].
3. Preprocessing
3.1 Locating Iris
The first processing step consists in locating the inner and outer boundaries of the iris and second step to normalize iris and third step to enhance the original image as in Fig.4 [4][6]. The Daugman’s system, Integro differential operators as in (1) is used to detect the center
and diameter of iris and pupil respectively.
=
21t e e
max(r, x0, y0)
H r f0
I (r * cos
+ x0, r * sin
+ y0) --- (1)
Fig. 2: Structure of Eye
The highly randomized appearance of the iris makes its use as a biometric well recognized. Its suitability as an exceptionally accurate biometric derives from [4]:
i. The difficulty of forging and using as an
imposter person;
ii. It is intrinsic isolation and protection from the external environment;
iii. It’s extremely data-rich physical structure;
iv. Its genetic properties—no two eyes are the same. The characteristic that is dependent on genetics is the pigmentation of the iris, which determines its color and determines the gross anatomy. Details of development, that are unique to each case, determine the detailed morphology;
v. its stability over time; the impossibility of surgically modifying it without unacceptable risk to vision and its physiological response to light, which provides a natural test against artifice.
After the discovery of iris, John G. Daugman, a professor of Cambridge University [8] ,[9], suggested an image-processing algorithm that can encode the iris pattern into 256 bytes based on the Gabor transform.
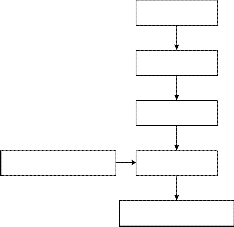
In general, the iris recognition system is composed
of the following five steps as depicted in Fig. 3
According to this flow chart, preprocessing including
Where (x0, y0) denotes the potential center of the searched circular boundary, and r its radius.
3.2 Cartesian to polar reference transform
Cartesian to polar reference transform suggested by J.Daugman authorizes equivalent rectangular representation of the zone of interest as in Fig.4, remaps each pixel in the pair of polar co-ordinates(r, 8) where r
and 8 are on interval [0,1] and [0,n] respectively. The
unwrapping in formulated as in (2) [1].
I ( x(r,e ), y(r,e )) I (r,e ) --- (2) Such that
x(r,e ) = (1 - r )xp(e ) + rxi(e ),
y(r,e ) = (1 - r) yp(e ) + ryi(e ) --- (3)
where I(x, y), (x, y), (r, B), (xp, yp), (xi, yi) are the iris region, Cartesian coordinates, corresponding polar coordinates, coordinates of the pupil, and iris boundaries along the B direction, respectively.
Image Acquisition Preprocessing Feature Extraction
image enhancement.
2. Image Acquisition.
An image of the eye to be analyzed must be acquired first in digital form suitable for analysis. In
IJSER © 2011 http://www.ijser.org
Data Base : Reference Code
Pattern Matching
Identify or Reject Subject
International Journal of Scientific & Engineering Research Volume 2, Issue 4, April-2011 3
ISSN 2229-5518
Fig. 3: General steps of the iris recognition system




(a) (b) (c)
(d)
Fig.4: (a) Original image; (b) localized iris; (c) normalized iris; And (d) enhanced iris.
4. Feature Extraction
The most important step in automatic iris
process will be fast and simple accordingly. Performance of classifiers is based on minimum Hamming Distance (MHD) as in (4).
HD=XOR (codeA, codeB) --- (4)
Where codeA and codeB are the templates of two images. When an iris image is captured in system, the designed classifier compares it with the whole images in each class. The Hamming distance (HDs) between input images and images in each class are calculated, then the two different classifiers are being applied as follows [1][4].
I. In the first classifier, the minimum HD between input iris code and codes of each class is computed.
II. In the second classifier, the harmonic mean of the n HDs that have been recorded yet is assigned to the class as in (5)[4].
length(code)
recognition is the ability of extracting some unique attributes from iris, which help to generate a specific code for each individual. Gabor and wavelet transforms
HM =

length(code)
i=1
(1/ code(i))
--- (5)
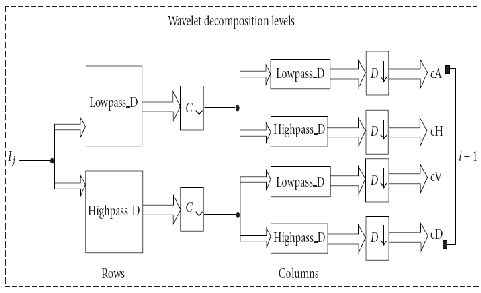
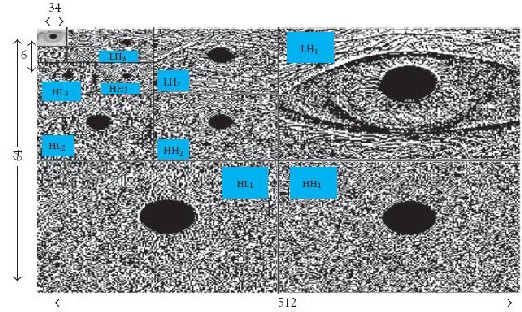
are typically used for analyzing the human iris patterns and extracting features from them, In Fig. 5(a) [1],[2] ,[4] a conceptual chart of basic decomposition steps for an image is depicted. The approximation coefficients matrix cA and details coefficients matrices cH, cV and cD (horizontal, vertical, and diagonal, resp.) Obtained by wavelet decomposition of the input image are shown in Fig. 5(b) [4],[11],[12]. The definitions used in the chart are as follows.
(i) C J denote downsample columns—keep the even
indexed columns.
(ii) D J denote downsample rows—keep the even- indexed rows.
(iii) Lowpass D denotes the decomposition lowpass filter.
(iv) Highpass D denotes the decomposition highpass filter.
(v) The blocks under “Rows” convolve with filter of block the rows of entry.
(vi) The blocks under “Columns” convolve with filter of block the columns of entry.
(vii) Ii denotes the input image.
5. Pattern Matching
By comparing similarities between feature vectors of two irises to determine that they are accepted or
rejected. Since feature vector is binary, the matching
6. Identification and Verification
Identification and verification modes are two main goals of every security system based on the needs of the environment. In the verification stage, the system checks if the user data that was entered is correct or not (e.g., username and password) but in the identification stage, the system tries to discover who the subject is without any input information. Hence, verification is a one-to- one search but identification is a one-to-many comparison.
7. Application
Implementations of image processing above five steps as in Fig.3 is used in veriEye iris recognition technology for healthcare patient identification system in 2008[5].Algorithm advanced iris segmentation, enrollment and matching which is as follows [5].
Robust eye iris detection: Irises are detected even when
the images have obstructions, visual noise and different levels of illumination. Lighting reflections, eyelids and eyelashes obstructions are eliminated. Images with narrowed eyelids or eyes that are gazing away are also accepted using wavelet algorithm[5].
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 4, April-2011 4
ISSN 2229-5518
Automatic interlacing detection and correction: The correction results in maximum quality of iris features templates from moving iris images.
Gazing-away eyes: A gazing-away iris image is
correctly detected, segmented and transformed as if it were looking directly into the camera.
Correct iris segmentation: is achieved under these
conditions:
i. P erf ect circles fa il. VeriEye uses active shape models that more precisely model the contours of the eye, as perfect circles do not model iris boundaries.
ii. The centers of the i ri s inner and outer
bounda ri es are diff erent Fig. 8. The iris inner
boundary and its center are marked in red; the iris outer boundary and its center are marked in green.
iii. I ri s bou nda ri e s ar e d efi nit el y no t ci rcl e s a nd
e v en not ellip s es Fig. 9.and especially in gazing-
away iris images.
iv. I ri s bo unda ri e s s eem to be pe rf ec t cir cl es. The recognition quality can still be improved if boundaries are found more precisely Fig.10. Compared to perfect circular white contours
v. Fast matching. Configurable matching speed
varies from 50,000 to 1 50,0 00 c omparison s per s ec ond. The highest speed still preserves nearly the same recognition quality Fig. 11.
vi. R elia bili ty. VeriEye 2.0 algorithm shows
excellent performance when tested on all publicly available datasets
7.1 Technical Specification[5]
Size of one record in a database | 2.3 Kbytes |
Maximum database size | Unlimited |
8. CONCLUSION
The research work is to enhance the algorithm for efficient person identification for other area of applications by increasing FRR more than 0.33% as the VeriEye algorithm results with FRR 0.32% and FAR
0.001%. Wavelets iris recognition algorithm is suitable for reliable, fast and secure person identification. Wavelet, Gabor filter and hamming distance are used in veriEye algorithm for robust and fast matching for healthcare application for patient identification. Research work will also focus on the algorithm for rapid and accurate iris identification even if the images are occlude further algorithm will also focus on robust iris recognition, even with gazing-away eyes or narrowed eyelids which solves all the security related problems.
Reference:
[1] Christel-loïc TISSE1, Lionel MARTIN1, Lionel TORRES 2, Michel ROBERT “Person identification technique using human iris recognition”.
[2] D.E.Benn, M.S.Nixon and J.N.Carter, “Robust eye
Extraction using H.T. “ AVBPA’99
[3] D.Gabor, “theory of communication”, journal IEEE.
[4] A.Poursaberi and B.N.Araabi, “iris recognition for partially occluded images: methodology and sensitivity Analysis” Hindawi Publishing Corporation EURASIP Journal on Advances in Signal Processing Volume 2007, Article ID 36751, 12 pages…
[6] John Daugman. “Recognizing persons by their iris patterns “Cambridge University, Cambridge, UK.
[7] L.M. Waghmare, S. P. Narote, A.S. Narote,
“Biometric Personal Identification Using IRIS”, Proceedings of International Conference on Systemics, Cybernetics and Informatics, ICSCI -
2006, Pentagram Research Centre – Hyderabad, pp.
679-682, Jan 2006
[8] E. Wolff, Anatomy of the eye and orbit, H. K. Lewis, London, UK, 7th edition, 1976.
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 4, April-2011 5
ISSN 2229-5518
[9] John Daugman,”How Iris works” IEEE Transaction on circuit and systems for Video Technology, VOL.14, No.1, January 2004.
[10] D.Zang Automated biometrics technologies and
systems Klumer Academics, Boston, Mass, USA,
2000.
[11] A.S. Narote, S.P. narote, M.B. Kokare, L.M.
Waghmare, “An Iris Recognition Based on Dual Tree
Complex Wavelet Transform” published in the proceedings of IEEE International Conference TENCON 2007, Taiwan during Oct. 30-Nov. 02,
2007.
[12] R.W.Conners and C.A.Harlow, “A theoretical
comparison of texture algorithms”, IEEE transactions
on Pattern Analysis and Machine Intelligence, vol2,no.
3,pp.204-222, 1980.
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 4, April-2011 6
ISSN 2229-5518
(b)
(a)
Fig.5 :( a) wavelet decomposition steps diagram and (b) 4-level decomposition of typical image with db2 wavelet




Fig.8 Fig.9 Fig.10 Fig.11
IJSER © 2011 http://www.ijser.org










