International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 72
ISSN 2229-5518
Mr. Rajesh K M1, Dr. Manjunatha Rao L2
1Research Scholar, CMJ University, Meghalaya, India
Wireless sensor network is the collection of sensors where all the sensors are interconnected to perform a common function co-operatively. Here sensors are considered as nodes which have computing capability with some memory. Energy utilization in wireless network is the main consideration because one main constraint in these types of networks is limited source of energy. Therefore protocols designed for these networks should be energy efficient.
Wireless networks are based on co-operative transmission technique. In general data can be transmitted directly between neighboring nodes. But if there are intermediate nodes between source and destination, co-operation among the nodes are required to transmit the data. In this paper, a new protocol called as energy efficient protocol is designed. Here a packet is transmitted only once per hop, thus reducing the energy consumption.
------------------------ ---------------------------
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 73
ISSN 2229-5518
The main problem that the wireless sensor network faces is limited source of energy. So care must be taken such that energy is utilized efficiently. The main problem in the existing system is transfer of the same packet more than once .It results in flooding. And another problem is with respect to multistage decisions which results in ambiguity during the file transfer. This in turn will consume more amounts of energy and time. One main solution for this type of problem is to design a protocol such that only less amount of energy is consumed in the transmission phase. Here the cooperation among nodes is used to find the efficient path. Further a packet is transmitted only once per node. Here as a solution to multistage decisions at a stretch path computation is done with respect to target node and is stored for future reference in order to avoid re- computation.
One existing cooperative scheme is cooperation along non- cooperative path (CAN).As the name itself indicates here there is cooperation among the nodes only in the transfer of packets. But, there is no cooperation among the nodes during the routing phase. That is, there no cooperation among the nodes during the computation of the efficient path. In this protocol there is no storage and retrieval of the efficient path for the future requests which is made to the same destination.
The CAN protocol made multistage decisions along with cooperation from all the predecessor nodes in order to transfer the data. Since CAN makes multistage decisions
here packets are flooded to all the nodes in the same radius.
So, even though there is no full-fledged flooding, there is some sought of flooding that exists in the existing CAN protocol.
This in turn will lead to various drawbacks such as the increased time consumption and increased network traffic. All these factors will lead to the increased energy consumption, which is the major drawback of the existing system.
In the proposed system a protocol called as the energy efficient protocol is designed, where in limited energy consumption is the major constraint. The major drawback of the existing system (CAN) was that there was no cooperation among the nodes in computation of the path. This drawback is overcome by the proposed system by the recruiting phase in our protocol.
The proposed system will avoid the flooding of packets to all the nodes by the cooperation of the neighboring nodes in the path computation. That is, here neighboring nodes will be assigned the task of path computation, so that all possible paths are computed and the best one among them is selected. The Multi stage decisions in existing system which lead to ambiguity in the existing system is replaced here with the single stretch path computation with respect to destination node.
It is assumed that each node in the network is equipped with a single Omni directional antenna and that multiple
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 74
ISSN 2229-5518
nodes are allowed to coordinate their transmissions in order to obtain energy savings. Analytical results are derived for achievable energy savings for both line and grid network topologies. It is shown that the energy savings of and are achievable in line and grid networks with a large number of nodes, respectively. Dynamic-programming- based algorithm for finding the optimal route in an arbitrary network is developed, as well as suboptimal algorithms with polynomial complexity. It uses the Co- operation Along Non co-operative path (CAN) scheme. We show through simulations that these algorithms can achieve average energy savings of about in random networks, as compared to the other schemes.
In wireless LANs that provide multi-rate support stations that experience poor channel quality tend to use low transmission rates to reduce the bit-error-rate of each transmission. This phenomenon usually leads to a throughput fairness problem between the stations with good channel quality and those without. This fairness problem has been shown to result in throughput degradation for the whole network. The MAC protocol proposed in addresses this issue using an efficient cooperative scheme. Under this scheme, low rate stations are assisted by a high rate station, referred to as helper stations, in its transmissions. With such assistance, the low rate station will be able to transmit data at a higher rate in a two-hop manner using the helper station. They implemented new protocol in a Linux test bed. This paper describes the assumptions, the implementation process and
the challenges we were presented with. The
implementation of the protocol shows that it performs efficiently in supporting TCP applications.
Cooperative transmission can obtain spatial diversity without using multiple antennas, thus achieving more reliable transmission or consuming less power. To realize cooperative communication in a distributed wireless network, two key questions need to be answered, namely when to cooperate and whom to cooperate with. In this paper, they propose a distributed MAC protocol with automatic relay selection to address these questions. They show by theoretical analysis and simulation results that the proposed solution outperforms conventional noncooperation transmission by 8 to 10 dB, for various target outage probabilities.
They develop and analyze low-complexity cooperative diversity protocols that combat fading induced by multi path propagation in wireless networks. The underlying techniques exploit space diversity available through cooperating terminals' relaying signals for one another. They outline several strategies employed by the cooperating radios, including fixed relaying schemes such as amplify-and-forward and decode-and-forward, selection relaying schemes that adapt based upon channel measurements between the cooperating terminals, and incremental relaying schemes that adapt based upon limited feedback from the destination terminal.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 75
ISSN 2229-5518
Performance characterizations in terms of outage events and associated outage probabilities are developed, which measure robustness of the transmissions to fading, focusing on the high signal-to-noise ratio (SNR) regime. Except for fixed decode-and-forward, all of our cooperative diversity protocols are efficient in the sense that they achieve full diversity and, moreover, are close to optimum in certain regimes. Thus, using distributed antennas we can provide the powerful benefits of space diversity. Applicable to any wireless setting, including cellular or ad hoc networks wherever space constraints preclude the use of physical arrays-the performance characterizations reveal that large power or energy savings result from the use of these protocols.
This paper investigates the diversity gain offered by implementing network coding over wireless communication links. The network coding algorithm is applied to both a wireless network containing a distributed antenna system (DAS) as well as one that supports user cooperation between users. The results show that network- coded DAS leads to better diversity performance as compared to conventional DAS, at a lower hardware cost and higher spectral efficiency. In the case of user cooperation, network coding yields additional diversity, especially when there are multiple users.
This paper analyzes space-time coded cooperative diversity protocols for combating multipath fading across multiple
protocol layers in a wireless network. The protocols exploit spatial diversity available among a collection of distributed terminals that relay messages for one another in such a manner that the destination terminal can average the fading, even though it is unknown a priori which terminals will be involved. In particular, a source initiates transmission to its destination, and many relays potentially receive the transmission. Those terminals that can fully decode the transmission utilize a space-time code to cooperatively relay to the destination. They demonstrate that these protocols achieve full spatial diversity in the number of cooperating terminals, not just the number of decoding relays, and can be used effectively for higher spectral efficiencies than repetition-based schemes.
Transmit diversity generally requires more than one antenna at the transmitter. However, many wireless devices are limited by size or hardware complexity to one antenna. Recently, a new class of methods called cooperative communication has been proposed that enables single- antenna mobiles in a multi-user environment to share their antennas and generate a virtual multiple-antenna transmitter that allows them to achieve transmit diversity. This article presents an overview of the developments in this field.
We consider a cluster-based cooperative transmission scheme where the source node and destination node form clusters for transmission. Instead of using perfect synchronization technique, we assume the cooperative
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 76
ISSN 2229-5518
transmission is asynchronous. Each member in transmitting cluster relays signal to the receiving cluster after obtaining information from source node.
A general decision feedback equalizer is used in the receiving cluster members to equalize the received MISO signal and detect as soft symbols. The receiving cluster members send the soft- decision outputs to the destination node. Thus, the decision node combines the soft-decision outputs and makes hard-decision detection for the transmitted information. The performance of proposed system is shown and compared with conventional MIMO system. Major factors for system performance are discussed. The over-sampling rate plays an important role in system performance. They also present a simple capacity analysis for proposed cooperative transmission system.
Networking together hundreds or thousands of cheap micro sensor nodes allows users to accurately monitor a remote environment by intelligently combining the data from the individual nodes. These wireless networks require robust routing protocols that are energy efficient and provide low latency. Starting from the basic idea of classical LEACH (Low Energy Adaptive Clustering Hierarchy), in this paper we introduce some innovations in the algorithm giving origin to LEACH-B. LEACHB presents a new strategy of cluster heads election and cluster formation. Our results show that LEACH-B optimizes system lifetime in a large range of situations and applications.
Wireless distributed micro sensor systems will enable the reliable monitoring of a variety of environments for both civil and military applications. In this paper, we look at communication protocols, which can have significant impact on the overall energy dissipation of these networks. Based on our findings that the conventional protocols of direct transmission, minimum-transmission-energy, multi hop routing, and static clustering may not be optimal for sensor networks, we propose LEACH (Low-Energy Adaptive Clustering Hierarchy), a clustering-based protocol that utilizes randomized rotation of local cluster base stations (cluster-heads) to evenly distribute the energy load among the sensors in the network. LEACH uses localized coordination to enable scalability and robustness for dynamic networks, and incorporates data fusion into the routing protocol to reduce the amount of information that must be transmitted to the base station. Simulations show that LEACH can achieve as much as a factor of 8 reductions in energy dissipation compared with conventional routing protocols. In addition, LEACH is able to distribute energy dissipation evenly throughout the sensors, doubling the useful system lifetime for the networks we simulated.
In the paper, we compare several clustering protocols which significantly affect a balancing of energy consumption. And we propose an Energy-Efficient Distributed Unequal Clustering (EEDUC) algorithm which provides a new way of creating distributed clusters. In EEDUC, each sensor node sets the waiting time. This waiting time is considered as a function of residual energy,
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 77
ISSN 2229-5518
number of neighborhood nodes. EEDUC uses waiting time to distribute cluster heads. We also propose an unequal clustering mechanism to solve the hot-spot problem. Simulation results show that EEDUC distributes the cluster heads, balances the energy consumption well among the cluster heads and increases the network lifetime.
Energy efficiency is the key problem in wireless sensor networks. We address this issue through cooperative protocols and extend our theory with computational techniques. In this paper, we present a clustered cooperative communication protocol for establishment of cooperative clusters during transmission of data in a cooperative way. First, we propose the cooperative cluster model, detail the operation process. The packet failure probability of our clustered cooperative protocol is optimized.
The implementation phase of software development is concerned with translating design specification into source code. The primary goal of software implementation is production of source code that is easy to read and understand. Source code clarity is enhanced by structural coding techniques, by good coding style, by appropriate supporting documents, by good internal comments etc.
Program codes are written following the structured coding technique, which laniaries the control flow, so that the execution sequence follows the sequence in which codes are written. This enhances the readability of code, which eases understanding, debugging, testing, documentation, and modification of the programs.
File Transfer
File transfer module uses the socket programming to transfer the data in the file. That is, a port is dedicated for the file transfer functionality. Here the efficient path is fetched from the xml file and using this path, the file is transferred. This module mainly consists of three functions. One to check the existence of the xml file, if the file does not exits, then it begins with the first phase of the algorithm. The other function is to send the file info and the data through the efficient path until it reaches the destination specified in the efficient path.
The network system module is implemented by passing the hello packets. The hello packets contain information like the name of the cluster to which a particular node belongs. By using this technique, the network system module will keep track of all the systems in the vicinity of the particular cluster. Using this information, the cluster head recruits its neighboring nodes in order to cooperate in the efficient path computation. So that, cooperative path can be found.
This module uses hello packets to know whether a particular node is attached or detached from its vicinity. The refresh list module continuously updates the network systems module, so that the availability of a particular node at a particular point of time is reflected in the network systems list in order to make sure that the transferred file will reach the specified destination.
This is the main module wherein various phases of the cooperative transmission algorithm such as request,
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 78
ISSN 2229-5518
recruit, grant, clear, confirm are actually implemented. And
finally the efficient path is found and it is stored in the xml
Initially, when a request for file transfer is made,
file for future reference, thus reducing the energy consumption.
Request phase is implemented by making the request to the next cluster head by using the source and destination IP as parameters.
Recruit phase is implemented by making the request to the neighboring nodes, by using the IPs in the list view.
Grant phase is implemented by returning the computed paths to the corresponding cluster heads. This is done by adding the objects to the
the xml file is checked first for its existence. If xml file exists, then the path directly retrieved for the file transfer. This module creates an xml file and it stores the computed efficient path in the xml file. The xml file is created in the same path as that of the application. It is done so because the xml file should be accessible by all the nodes in a cluster. The xml file in turn consists of several nodes, which is mainly used store the data in an organized way. Here the xml file contains a node called the fullpath, which in turn contains the efficient path.
object list present in cluster head. Each object in turn consists of the distance of each path.
Clear phase is implemented by forwarding the object list to the requesting IP.
Confirm phase is implemented by choosing the best path from the object list and storing it in the xml file.
Status tracking module is implemented by using a function which takes the messages as parameters. Then each message includes the information about the current happenings of the algorithm. Status tracking module works in parallel with all the other modules, so that it continuously displays the current happenings of the cooperative transmission algorithm module and the file transfer module. This module works by displaying the messages of each and every stage of the protocol on a separate tab called as status.
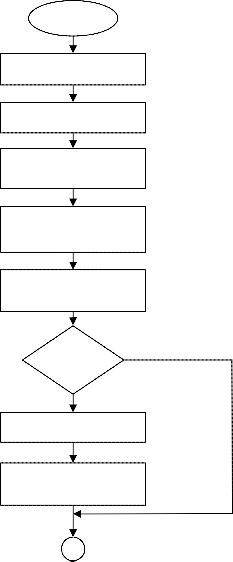
START
Run Client application
Select the cluster name
Select the Position of the node
Enter the destination IP At the sender side
Choose the file to transfer
Ye
If xml
file
No
Compute the efficient
Store the efficient path in the xml file
IJSER © 2013 http://www.ijser.org
A
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 79
ISSN 2229-5518
A
Retrieve the path from the xml file for future use
File transfer using efficient path
STOP
Figure Control Flow Diagram
Figure shows the control flow diagram. It shows the flow of control through a program as a graph. Each node in the graph represents a statement in the flow.
private void MainForm_Load(object sender, EventArgs e)
private void btnOpenFile_Click(object sender, EventArgs e
)
public void RefreshNeighbourNodeList()
public void RefreshList()
public void ReceiveBroadcastAsClusterHead()
private void AddStatus(string status)
public void CreateXML(string xmlPath ,string fullPath)
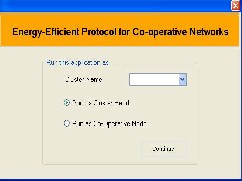
Figure I.1 Main form after deploying the application
Initially when the application is deployed, the main form is displayed. The Figure I.1 shows the first form of the application. This form has a combo box from which the cluster name can be selected and it also has two radio buttons from which the position has to be selected. It also has a Continue button to navigate to the next form.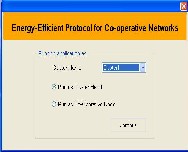
Figure I.2 Selecting the name and position in cluster1
The Figure I.2 shows the mode in which the application runs. That is, the application can either run as a cluster head or it can run as a co-operative node. Here, the system
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 80
ISSN 2229-5518
is deployed as the cluster head within the cluster 1. This is done by checking the first radio button.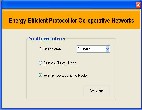
Figure I.3 Selecting the name and position in cluster 2
The Figure I.3 shows the mode in which the application runs. That is, the application can either run as a cluster head or it can run as a co-operative node. Here, the system is deployed as the cooperative node within the cluster 2
.This is done by checking the second radio button.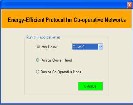
Figure I.4 Selecting the name and position in cluster 3
This Figure shows the mode in which the application runs. Here, the system is deployed as the cluster head within the cluster 3 which is the destination node with respect to whom the path has to be computed. And the continue button is clicked so that the current form is navigated to next form.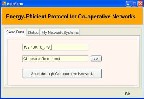
Figure I.5 Entering Destination IP
This Figure shows the navigated form with three tabs. Where the status tab displays the current happenings, My Network Systems tab displays the systems in the vicinity of the cluster and Send Data tab is used to enter the destination IP. Choose the file to send and a button to start file transfer.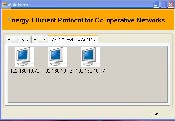
Figure I.6 Displaying systems in vicinity
The navigated form has three tab controls: Send Data, Status and My Network Systems. The My Network Systems tab is one among the three tabs. The Figure I.6 shows how the My Network Systems tab shows the systems that are in the vicinity of the cluster 2 .That is it displays all the nodes that are present within the cluster.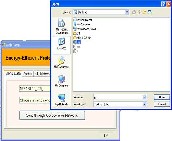
Figure I.7 Selecting a file
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 81
ISSN 2229-5518
The Figure I.7 shows how a file to be transferred is selected from the dialog box containing the files. First we will enter the destination ip to which the file has to be sent. Then the file to be transferred is selected from the dialog box and the open button is clicked.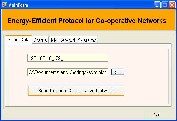
Figure I.8 Path of the chosen file
The Figure I.8 shows path of the chosen file. Once the file is chosen from the dialog box and the open button is clicked, the path of the selected file will be retrieved and it will be displayed in the text box as shown in the snapshot.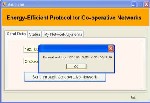
Figure I.9 Request to immediate cluster head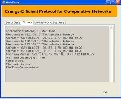
The Figure I.9 shows that initially when the Send through Co-operative Network button is clicked, a message box is displayed saying that a request has been sent from the source node to the immediate cluster head. And then the OK button in the message box is clicked.
Figure I.10 Status at the head node of Sender cluster 1
The Figure I.10 shows how the sender cluster node will participate in the path computation process by responding to its neighboring cluster nodes. Later when all the cooperative paths are returned, the efficient path is selected among them. It also displays file transfer information.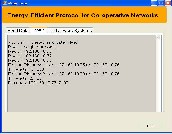
Figure I.11 Status at the cluster head of intermediate cluster 2
The Figure I.11 shows how the intermediate cluster head recruits its neighboring nodes for the path computation process and it also shows how this node in turn will compute the cooperative path. Finally, it shows the total distance of the computed co-operative path.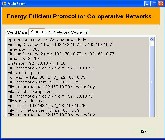
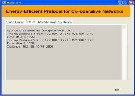
Figure I.12 Status at the node 1 of cluster 2
The Figure I.12 shows the status of one of the cooperative nodes in cluster 2, which shows the computed distances through that node. Later it also shows how the file transfer takes place through this node, when the path via this node
is selected as the best path.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 82
ISSN 2229-5518
Figure I.13 Status at the node 2 of cluster 2
The Figure I.13 shows the status of one of the cooperative nodes in cluster 2, which shows how it computes the co- operative path through that node to destination. It also shows the computed distances through that node.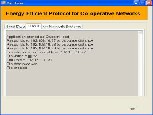
Figure I.14 Status at head node of cluster 3
The Figure I.14 shows how the receiver node at cluster 3 will receive the selected file through the efficient path. It also shows how the destination node responds to the intermediate node in order to cooperate in the path computation. And it shows the status File created when the file is created at the specified path.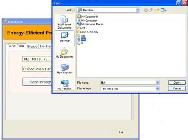
Figure I.16 sending the file through pre computed path
Once the efficient path is computed, then the request to transfer a file again to the same destination does not require any computation. The above Figure I.16 shows how another file is selected from the dialog box for sending it through the pre computed path.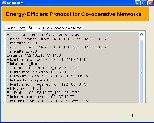
Figure I.16 Status at co-operative node of cluster 2
When the request to transfer a file to the same destination arrives, then the file is transferred directly without any re- computation. This is done by fetching the pre-computed path. The Figure I.16 shows how the file is transferred through the pre computed path without any re computation.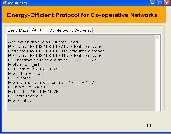
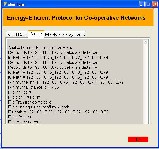
Figure I.17 Status at head node of cluster 3
The Figure I.17 shows how the receiver node at cluster 3 will receive the selected file through the pre computed path. It displays the node from which the file has been received. And it shows the status File created when the file is created at the specified path.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 83
ISSN 2229-5518
transmission algorithm wherein the co-operative path is calculated with the cooperation of all the neighboring nodes and the data is transmitted through the efficient path only once .So this in turn reduces time and energy consumption and also avoids flooding.
Figure I.18 Status at sender node at cluster 1
The Figure I.18 shows the status at the sender node when another file is sent through the pre computed path. It displays all the co-operative paths and the selected efficient path. It also displays the distance of the selected efficient path. Finally, the Exit button is clicked to close the application.
The wireless sensor networks have been extensively deployed and researched. One of the major issues in wireless sensor networks is a developing energy-efficient clustering protocol. Clustering algorithm provides an effective way to prolong the lifetime of a wireless sensor networks. The proposed system will avoid the flooding of packets to all the nodes by the cooperation of the neighboring nodes in the path computation. That is, here neighboring nodes will be assigned the task of path computation, so that all possible paths are computed and the best one among them is selected. The Multi stage decisions in existing system which lead to ambiguity in the existing system is replaced here with the single stretch path computation with respect to destination node.
Through energy consumption analysis of our clustered cooperative protocol and comparison with some of the non- cooperative schemes, we can verify the effectiveness of our
protocol. In this protocol we propose co-operative
[1] Amir Ehsan Khandani, Jinane Abounadi, Eytan Modiano, and Lizhong Zheng: Cooperative Routing in Static Wireless Networks. IEEE Transactions on Communications 55(11) : 2185-
2192 (2007)
[2] P. Liu, Z.Tao, S. Panwar, “A cooperative MAC Protocol for wireless local area networks”, Proc. Of IEEE ICC’05, June 2005
[3] Agnes Pinter-Bartha, Anita Sobe, Wilfried Elmenreich: Towards the light-Comparing evolved neural network controllers and Finite State Machine controllers. WISES 2012:83-87
[4] A. Narula, M. D. Trott, and G.W.Wornell, “Performance limits of coded diversity methods for transmitter antenna arrays,” IEEE Trans. Inform. Theory, Vol.45, PP. 2418-2433, Nov.1999
[5] Giuseppe Bianchi, “Performance analysis of the IEEE 802.11 Distributed Coordination Function”, IEEE Journal on Selected Areas in Communications VOL.18, NO.3, March 2000
[6] A. Sendonaris, E. Erkip, and B. Aazhang, “Increasing uplink capacity via user cooperation diversity,” in Proc. IEEE Int. Symp. Information Theory (ISIT) , Cambridge, MA, Aug. 1998, P.156.
[7] V.Hayes, IEEE Standard for Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications, 1997.
[8] B. Schein and R.G.Gallager, “The Gaussian parallel relay network,”in Proc. IEEE Int. Symp. Information Theory (ISIT), Sorrento, Italy, June
2000, p.22
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 84
ISSN 2229-5518
[9] A. Sendonaris, E. Erkip, and B. Anzhang, “User cooperation diversity, Part I: System description,” IEEE Trans. Commun., vol.51, pp.1927-1938, Nov.
2003
[10] J.N.Laneman and G.W. Wornell, “Distributed space-time coded protocols for exploiting cooperative diversity in wireless networks,” IEEE Trans. Inform. Theory, vol. 49, pp. 2415-2525, Oct.2003
[11] Daji Qiao, Sunghyun Choi, Kang G. Shin, “Goodput analysis and link adaption for IEEE
802.11a wireless LANS”, IEEE Transactions on
Mobile Computing, VOL.1, NO.4, October- December 2002.
IJSER © 2013 http://www.ijser.org