1 shows the architecture of heterogeneous sensor networks
(HSNs).
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 720
ISSN 2229-5518
Dynamic key establishment and management to improve the scalability in heterogeneous sensor networks (HSN) Premamaydu B, Venkatarao K, Suresh varma P
—————————— ——————————
A wireless sensor networks build with a large number of sensors, which are equipped with batteries, sensing, communication unit, data processing and radio communication unit. At present any real time applications implementing on wireless sensor networks, like home automation, environment monitoring, military or security
management systems [2, 3, 4, 6]. Depending on the ability
of the key management scheme that can be classified into two different categories: Static and Dynamic. The static key management, the keys are fixed for the entire life of the network. This idea may increase the probability of attacks significantly. Instead, in dynamic key management, the keys used for cryptographic operations are modified
IJSER
areas, targeting and target tracking systems, agriculture
monitoring system and battlefield surveillance. However
all the applications need protection in all the level of the
sensor network.
Key management is the mechanism to provide the security
in all the levels of the wireless sensor networks. Since sensor nodes in WSNs have constrains in their computational power and memory capability and security. The solutions of traditional networks like computer networks, ad hoc networks, and wired networks are not suitable for WSNs. The goal of key management in WSNs is to solve the problem of creating, distributing and protecting those secret keys. Hence, the feasible and reliable techniques for key management and distribution of these keys are of major importance for the security in WSNs.
Due to their importance, numerous key management schemes have been introduced or proposed for WSNs and many researches are proposed the different key
————————————————
• Premamayudu B is currently pursuing Ph.D. in Computer Science and
Engineering in JNT University, Kakinada, India, PH-919440006478. E-
mail: prem_it@vignanuniversity.org .
• Venkata rao is working as Prof. and HOD Department of CSE, Vignan’s
Institute of Information Technology, Visakhaptnam (Dt), Andhra
Pradesh, India, E-mail:vrkoduganti@gmail.com.
• Suresh Varma p is currently working as Dean CDC & Professor, Adikavi
Nannaya University, Rajahmundry, W. Godavari (Dt), Andhra Pradesh,
India. E-mail: vermaps@yahoo.com.
throughout the lifetime of the sensor network. Dynamic
key management is the most suitable key management in sensor networks. Dynamic key management schemes adopt many processes form the traditional network key management, but those processes are light weight in terms of processing, consuming memory and power, and computing needs. They perform rekeying either periodically or on demand as needed by the network. Since the keys of compromised sensor nodes are revoked in the rekeying phase. The dynamic key management schemes enhance the network survivability, stability, scalability and resilience of network dynamically.
Eschenauer and Gligor[2] first introduced a key management procedure for sensor networks based on probabilistic key predistribution. Chan et al. [8] extended this scheme and improved the metrics of key management. Liu et al. [9] proposed two key distribution schemes based on bivariate polynomials. They use the random subset assignment scheme and key predistribution scheme in which the key pool contains multiple instances of selected polynomial. Oliveria et al. [10] proposed random key predistribution for secure message and data communication in hierarchical (Cluster-based) protocols such as LEACH. Du et al. [3] implemented the asymmetric predistribution method for heterogeneous sensor networks which gives tuff security with less complexity and storage space enough for more number of keys. Liu et al. [11]
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 721
ISSN 2229-5518
propose a complete framework for key management in distributed wireless networks and heterogeneous wireless
sensor networks. Bulusu et al. [12] propose two key predistribution based schemes for heterogeneous networks which contain the static and mobile sensor nodes.
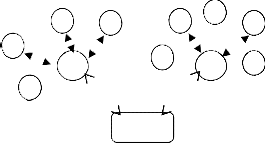
This paper proposes a Dynamic key management that is designed for heterogeneous sensor networks (HSNs). Each cluster head generates its own key-chain, which encrypts messages and communicates with the other sensor nodes in the cluster. In this architecture, each cluster consists of several sensor nodes and cluster head. Many clusters and a base station form the heterogeneous sensor networks. Fig.
1 shows the architecture of heterogeneous sensor networks
(HSNs).
L
L L L L
L
L
H H L
L
sensor node will preload from Base Station through a secure channel before deployment.
Step 1: H-sensor HIDj broadcast the sample message to the entire cluster L-Sensors using the maximum power. The position of H-Sensor and random number RH is encrypted by session key KT . The format of the sample message is as follows.
HIDj ∥ sample message ∥ Position of the H-Sensor ∥ {RH }
Step 2: The L-Sensor LIDi may receive one or more sample
message offers from H-Sensors. The LIDi sensor selects an H-Sensor as its cluster head based on the signal strength of message and distance of H-Sensor to it. L-Sensor backups all other H-Sensors information which are offer the sample messages. These H-sensors are used in case the selected H- Sensor is disabled or compromised. After selecting the H- Sensor, L-Sensor LIDi generates a pairwise key LKij ={H(RH
∥ LIDi)}K T and send to the H-sensor in the following format
HIDj ∥ replay message ∥ position of the LIDi ∥ {MAC(LKij ) ∥
LIDi}KT
Step 3: After getting the replay message from the L-Sensor
LIDi, the H-Sensor HIDj generates the pairwise key
IJSER
BS
Fig. 1: Architecture of heterogeneous Sensor Networks
(HSNs)
All the nodes are randomly distributed in the environment. They are static and their locations are identified using any one localization technique.
3.1 Initialization Phase: the Base Station generates a very large key pool of size S ≅ 220 before deployment of sensor
nodes in the network. The base station selects the distinct key for each cluster head (H-Sensor), which is referred as HK. After that Base Station generates the sub key
Ksub =HK⊕Rs using HK and random number Rs . Using sub
key Ksub and R1 Rn to generate key chain with n keys for
each H-sensor as given below
Kn-1 =(Ksub ⊕Rn )
Kn-2 =(Kn-1 ⊕Rn-1 )
.
.
.
.
K1 =(K2 ⊕R2 ) K0 =(K1 ⊕R1 )
Hence, each H-sensor will get the unique key chains, Ks
and random numbers R1 Rn from Base Station Bs. All the nodes the network store the same hash function and temporary session key KT . Here session and HK are not same in the Cluster Head. All the generated stuff for each
HKij ={H(RH ∥ LIDi }KT . if MAC(LKij )=MAC(HKij ) is
satisfied, then the H-Sensor authenticate validity of the L-
Sensor LIDi . Hence HKij =LKij becomes the pairwise key
between HIDj and LIDi. This key is used to establish confidentiality between cluster head and sensor node over the data transmission.
3.3 Group Key Establishment
Step 1: The H-Sensor HIDj selects the group key K0 in the
cluster and transmits using the associate pairwise key of L- Sensor. The format of Group key message is as follows
HIDj ∥ position of the L-Sensor ∥ {K0 }LKij
Step 2: After identifying all the clustering sensor nodes, the
H-Sensor HIDj broadcast the ID of members to all the sensor nodes using the Group key K0. The format of members ID message as follows.
HIDj ∥ {list of all neighboring nodes ID}K0
3.4 Normal Operation of HSNs: In the proposed method,
the BS generates the pairwise keys and groups keys between BS and Cluster Heads. This process is similar to the above process which is used between cluster heads and sensor nodes. For example, in this scheme the Base station Generated HKj as a pairwise key and KBS as Group key for all cluster heads.
We address two normal operations in the Heterogeneous
wireless sensor network. Operation 1 is that BS asks the H-
Sensors to get the data from all the sensor nodes. Operation 2 is that BS asks the H-Sensor to get the data from particular L-Sensor node.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 722
ISSN 2229-5518
Operation 1:
Step 1: BS Sends the request message to all its H-Sensors
using group key KBS
BS ∥ request message { MAC(M) ∥ M} KBS
Step 2: H-Sensor HIDj forwards the request message to all
cluster nodes using Group key Ki (i.e K0 )
HIDj ∥ request message {MAC(M) ∥ M}Ki
Step 3: Each L-Sensor replys the data to its cluster head
using Group key Ki
LIDi ∥ reply message { MAC(M ∥ C) ∥ M ∥ C}Ki
Step 4: Finally H-Sensor HIDj sends gathered data from all
L-Sensors to Base Station Using Group key KBS
HIDj ∥ {MAC(C1 ∥ C2 ∥ C3 ….)∥ C1 ∥ C2 ∥ C3 …..}KBS
Operation 2:
Step 1: Base Station BS Sends request message to a particular Cluster Head using pairwise key HKj
BS ∥ request message { MAC(LIDi) ∥ LIDi}HKj
Step 2: H-Sensor HIDj forward the request message to a
specific L-Sensor using pairwise key KHij
HIDj ∥ request message ∥ {MAC(M) ∥ M}HKij
Step 3: L-Sensor LIDi sends the data to a requested cluster
head HIDj using pairwise key LKij
the environment, this new node preloads with hash function and session key KT . After deployment of new
node, Bs broadcast the addition of new node message to all
H-Sensors.
Addition of new node ∥ {MAC(LIDx) ∥ LIDx ∥ KT }KBS
In this method, L-Sensor LIDx placed randomly in the
network. After that L-Sensor LIDx broadcast a request
message to all its neighboring H-Sensor. One or more H- Sensors may give reply to the LIDx sensor. L-Sensor LIDx selects the one of H-Sensor as a cluster head based on the signal strength and distance of cluster head, other H- Sensors are make them as backup cluster heads. H-Sensor HIDJ will reply with random number RH to the node x using KT . Hence, H-Sensor j and L-Sensor x generates the pairwise key LKxj =HKxj using RH, LIDx and KT . After generating pairwise key LKxj , H-Sensor sends the group key K0 (i.e Ki ) to the L-Sensor LID x using LK xj . Finally H- Sensor broadcast the neighbor message to all the members of the cluster once again.
sufficient power, it generates a new key-chain for the L-
IJSER
LIDi ∥ {MAC(M∥C)∥M∥C}LKij
Step 4: H-Sensor HIDj forward the received data from L-
Sensor LIDi to Base Station using pairwise key HKj
HIDj ∥ {MAC(M ∥ C) ∥ M ∥ C}HKj
Our proposed Scheme addresses the adaptability of the Proposed Scheme, which includes the Key Revocation (resiliency), Adding new node (Scalability) and Extending the key chain.
4.1 Key Revocation: Base Station has the capability of identifying compromised sensor nodes or adversary. When the BS identified the malicious sensor node, it broadcasts the malicious message to the entire H-Sensors using group key KBS .
Malicious node message ∥ {MAC(LIDx) ∥ position of the node x ∥ LIDx } KBS
H-sensor HIDj will transmit the revocation message to all
the members of its own cluster. After that, H-Sensor HIDj sends the revocation message to malicious sensor node using pairwise key. The old key of compromised sensor will be revoked with new key using new random number.
HIDj ∥ revocation message ∥ {Ri+1 }LKxj
node is deployed in the network, it needs to establish the pairwise and group keys with its cluster head. Firstly new L-Sensor node establishes the pairwise key with its H- Sensor node. Hence, H-Sensor forwards the group key of cluster using pairwise key. Before placing the new node in
Sensor in the cluster. The H-Sensor HIDj uses the pairwise
key LKij to send the new key for the L-Sensors. The format
of the new extended key-chain message that H-Sensor j
sends to the L-Sensor i is as follows
HIDj ∥ position of L-Sensor ∥ {MAC(k0 ) ∥ k0 }LKij
In our Experiment, they are 1000 L-Sensor nodes and 50 H- Sensors in the network. The ration between these two types is 20:1. The key-chain length of H-Sensor is 50 keys. L-Sensors gather the data from the environment and send to the H-Sensor nodes. Then H-Sensor nodes forward the data to Base Station.
In the group key establishment, H-Sensor uses the pairwise
key to transmit group key K0 form the key-chain of H-
Sensor. H-Sensor only sends to messages to the L-Sensor using pairwise key: one message for group key and other for broadcasting all members IDs to their neighbors in the cluster. Total number of messages required to establishing broadcast and unicast communication is 6 messages. This
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 723
ISSN 2229-5518
number is very less compare with other key establishment methods of HSN. Hence, this scheme consumes very less power. This method will give the long life for the HSN.
Table 2: Number of messages required for key establishment
Sensor node has an average of 24+n Keys, where 20 keys for pairwise keys for its L-Sensors, 4 keys are HK, KBS , KT , Ksub and n is the length of the key-chain. The length of key- chain at most 50 keys in H-Sensor. Therefore, H-Sensor should store 77 keys. The L-Sensor needs only 3 keys, which are KT , LKij , Ki (Session Key, Pairwise key, and Group key).
[2] Eschenauer L, Gligor V. A Key management scheme for distribution sensor networks. Smart wireless sensor networks. In TechOpen;2010;p18:1-18:6
[3] Du W, Deng J, Han YS, Varshney PK, Katz J, Khalili A. A pairwise key predistribution scheme for wireless sensor networks. ACM Transactions on information and system security 2005:8(2):228-58.
[4] Kim JM, Cho TH. A*-based key tree structure generation for group key management in wireless sensor networks. Computer and communications. 2008:31:2414-9
[5] Zhang X, He J, Wei Q. EDDK:energy-efficient distributed deterministic key management for wireless sensor networks, EURASIP Journal on wireless communications and networking
2011:1-11
[6] Zhou B, Li S, Li Q, Suna X, Wang X. An efficient and scalable pairwise key predistribution scheme for sensor networks using deployment knowledge. Computer and communication
2009:32:124-33.
[7] Xiaobing He, Michael Niedermeier, Hermann demeer. Dynamic key management in wireless sensor networks: A survey. Journal of network and computer applications. 36(2013):611-622.
[8] H Chan, A Perrig, and D song. Random key predistribution schemes for sensor networks. Proceedings 9th ACM conference computer and communication security. November 2002. 41-47
[9] Liu D, Ning P, Li R. Establishing pairwise keys in distributed sensor networks. ACM Transactions Information Systems Security.
2005.8(1):41-77
[10] Oliveira LB, Worg HC, Bern M, Dahab R, Loureiro. A Random key distribution solution for security clustered sensor networks. 5th
Table 3: The number of functions & keys required for each
member of HSN
6. Conclusion
This paper proposes the dynamic pre key distribution in
HSN. The network itself divides into the clusters and headed by one cluster sensor to manage cluster. Cluster heads can generate the key-chain. Cluster heads and their sensor nodes themselves generate the pairwise key and group key provide the secrecy in the data transmission. The key-chain consists of continuous keys, and each key is dependent. This makes it possible for the sensor node to confirm the validity of each key. Sensor nodes or cluster heads change the key, and then sensor nodes can confirm the identity of cluster head and the validity of new key. This scheme uses the hash function to avoid the data collision while making the compressions. Sensor nodes themselves calculating the group key with the help of preloaded keys and hash function which is stored at the time of deployment. This scheme improves the scalability of the scheme and reducing the memory requirements of sensor nodes and ensuring the key security.
[1] Hu W, Tan H, Corke C, Shih WC, Jha S. Toward trusted wireless sensor networks. ACM Transactions on Sensor Networks
2010;7:5:1-25
IEEE international symposium on network computing and applications. 2006.pp 145-154
[11] Perrig A, Szewczyk R, Tygar JD, Victorwen. Security protocols for sensor networks. Seventh annual conference on mobile computing and networks. July 2001
[12] Bulusu V, Durresi A, Paruchuri V, Durresi M, Jain R. Key distribution in mobile heterogeneous sensor networks. Global telecommunications conference. 2006:1-5
IJSER © 2013 http://www.ijser.org