Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 1
ISS N 2229-5518
Dynamic Adaptive Topology Control in Highly
Mobile Environment
Diya Ann Kuruvila, Jennifer S Raj
Abs tract - One of the important f actors that aff ect the connectivity of a netw ork is transmission pow er. As the node moves connectivity gets aff ected. Hence netw ork lif etime and capacity gets aff ected. Netw ork partioning can occur if a loss in connectivity occurs. Planar structures helps to overcome the connectivity problems to certain extend but they do not take into account netw ork dynamics. Hence in order to improve the netw ork perf ormance an adaptive dynamic topology control is presented in w hich netw ork is div ided into various zones and in accordance w ith the netw ork dynamics, the nodes adjust their topology independently . Netw ork perf ormance is ensured w ith best quality of service by selecting the links based on the transmission pow er of nodes. Perf ormance of the algorithm is w itnessed by setting the node mobility at diff erent speeds. Simulation results show s that t he proposed w ork out perf orms existing w ork in terms of 1)improved connectivity 2)less packet drop 3) greater throughput .
Inde x Terms - Dynamic Adaptive Topology Control (DATC), Gabriel Graph (GG), Relative Neighborhood Graph (RNG), Local Minimu m Spanning
Tree (LMST), Topology Control, Topo logy Construction, Topology maintenance
1. INTRODUCTION
—————————— ——————————
It is needed as power contr ol affects the traffic carrying capacity of a networ k. But her e considerable message
The main aim of topology contr ol is to r educe the number
of active nodes and active links in a networ k for further use in a networ k. Topology contr ol aims in efficient use of scar ce ener gy r esour ces for incr easing the capacity and life time of a networ k. Featur es of topology contr ol include (i) it must be fully distributed, asynchronous and localized (ii) topology gener ated must pr eserve connectivity and r elies on bi dir ectional links only (iii) must generate a topology
with small node degr ee. Topology contr ol includes topology constr uction and topology maintenance. Topology construction helps in constructing the r educed topology and topology maintenance is in char ge of maintaining the r educed topology so that character istics like connectivity and coverage is pr eser ved. One way of constr ucting the topology is by changing the tr ansmission range of nodes. Tr ansmission ranges ar e set in such a way that connectivity is pr eserved and ener gy is saved. It stands for common pow er . COMPOW [1] is a r outin g based approach. Her e the nodes closed to each other will be transmitting at a low er pow er such that it w ill not affect traffic carrying capacity of other nodes.
———— ——— ——— ——— ———
Diya Ann Kuruvila is currently pursuing ma sters degree progra m in communica tion systems from Ka runya University, Coimba tore, India.
Ema il: diyaa nnkuruvila @gma il.com
Jennifer S. Ra j working a s a Assista nt Professor in Dept of Electronics a nd Communica tion Engineering in Ka runya University, Coimba tore, India.Ema il: jennifer.ra j@gmail.com
over head is ther e and r equir es knowledge of r outing table. Transmission ranges ar e set in such a way that connectivity is pr eser ved and ener gy is saved. It stands for common pow er . COMPOW [1] is a r outing based appr oach. Her e the nodes closed to each other will be tr ansmitting at a lower pow er such that it will not affect traffic carrying capa city of other nodes. It is needed as pow er contr ol affects the traffic carrying capacity of a networ k. But her e considerable message overhead is ther e and r equir es knowledge of r outing table. Cone based topology contr ol (CBTC)[2] is a dir ection based transmission range appr oach wher e the nodes should have dir ectional information
Her e w e should not transmit at higher pow er as power
incr eases w ith distance. Also message exchange needs to be ther e for finding dir ectional information . XTC[3] is a neighbor based tr ansmission range appr oach wher e every node sends its or der s its neighbors based on some cr iter ion
for e.g., link quality . This will be sent at maximum pow er . Based on its own or der , and the or ders of its neighbor s, the node determines the set of ‚logical‛ links. It does not r equir e dir ectional information and w or ks without GPS. But her e the pr oblem is that ther e is no limit on the number of physical neighbors and ther e is no guar entee for connectivity. Local minimum spanning tr ee (LMST) [4] was designed as some of the algorithms like CBTC, ar e based on some message exchanges and some r equir e explicit pr opagation channel modes. In LMST ever y node collects information about one hop neighbor and forms a set called N1[u]. MST is then calculated using Kr uskal algor ithm or Prims algor ithm. It uses a tr ee based appr oach .
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 2
ISS N 2229-5518
In this paper dynamic adaptive topology contr ol is pr esented wher e the nodes adjust their topology independently inaccor dance w ith the networ k dynamics. The contr ibutions of the paper include: (i) pr eserves networ k connectivity ther eby maintaining the lifetime of the netw or k (ii) small node degr ee r educes MAC contention and inter fer ence (iii) better packet deleivery ratio than pr evious w or ks by r educing the number of loops.
The r est of the paper is or ganized as follows: In section 2
r elated wor ks is pr esented.In section 3 pr eliminar ies is
descr ibed. In section 4 pr oposed w or k is pr esented. In section 5 per formance analysis and simulation r esults ar e shown. Section 6 concludes the paper .
2. RELATED WORK
The paper is being influenced by lot of r esear ch effor ts. Ther e has been gr eat deal of w or k in the ar ea of topology contr ol of which some has been summar ized below .
Common Pow er [1] is a r outing based appr oach. Power contr ol affects the traffic carrying capacity of the networ k. If pow er control is not ther e inter fer ence w ill be w orse and also if the sour ce is closer to destination transmitting at higher pow er leads to wastage. For choosing transmit pow er bi- dir ectionality of the link is cr itical. Nodes should find a way to ensur e bi dir ectionality w ithout br eaking existing pr otocols. This leads to COMPOW. If the nodes ar e closer to each other it is better to transmit at low pow er . Her e w e assume that all the nodes oper ate at common pow er ther eby incr easing netw or k lifetime, traffic carrying capacity. The need for bi dir ectional links is that w e cannot guarantee that by single hop packet w ill r each destination. Hence acknowledgements should be ther e. Thus bi dir ectional links should be ther e.
Cone Based Topology Control [2] is a dir ection based topology contr ol algor ithm. The main aim is that node ‘u’
transmits with minimum pow er Pu,α which is r equir ed to ensur e that in every cone of degr ee α ar ound ‘u’ ther e is some node which ‘u’ can r each with Pu,α.. Networ k connectivity pr eserved by taking α=5π/6. CBTC r equir es only dir ectional information that is it must be possible to estimate the dir ection fr om which another node is transmitting. Dir ectional information is found out by using dir ectional antenna. The netw or k is divided into small cones w ith angle α. In each cone ther e should b e a neighb or node. The algor ithm takes a parameter α and each node tr ies to find at least one neighb or in every cone of degr ee α center ed on ‘u’. Node ‘u’ starts the algorithm by running HELLO message using low transmission power and collecting r eplies it gradually incr eases tr ansmission power to discover mor e and mor e neighbors and keeps a list of
nodes that it has discover ed and also the dir ection in which they ar e located. It then checks whether each cone of degr ee α contains a node. The check per for med by arr anging nodes accor ding to their angles based on some r efer ence node. The algor ithm ter minates when ther e is no gap α or the maximum pow er has r eached. Her e also w e can’t transmit at higher power as power incr eases with the nth pow er of distance. Also message exchange needs to be ther e for finding dir ectional information .
Rogen Wattenhofer et al. [3] pr esented XTC which is a
neighbor based appr oach. It is a simple and local algorithm and does not r equir e the node position. It can wor k w ithout GPS. Nodes or der their neighbor as per the link quality (Euclidean distance fr om node) Ther e is no upper bound on the number of neighbor . The basic idea is that at the beginning every node or ders its neighbors (set of nodes in the maximum tr ansmitting r ange) accor ding to some criterion (e.g., link quality) then, every node transmits its
or der at maximum pow er , based on its own order , and on the or ders of its neighbors, every node deter mines the set of
‚logical‛ links. The algor ithm involves 3 main steps a) neighbor or dering) Neighbor or der exchange c) Edge selection. First the node ‘u’ br oadcasts its or der to its neighbor s. The neighbor s also br oadcast ther e order to ‘u’. Node ‘u’ arranges or ders in the decr easing or der in terms of link quality. If a node order appear s ear lier in the or der than another node first one will be pr ocessed first.
Li, .Hou et al.[4] pr esented local minimum spanning tr ee (LMST) which is a span ning tr ee based appr oach. In topology contr ol netw or ks nodes determine their
transmission pow er and define netw or k topology by forming neighbor r elation. In MST nodes will be collecting information about neighbors. Degr ee of node is bounded by 6. Unidir ect ional links ar e r emoved so that r esulting topology contains bidir ectional links. If the node degr ee is small, it r educes contention and inter fer ence. Average node degr ee is small. The MST of a graph defines the smallest subset of the edges that keeps the gr aph in connected. MST is a sub gr aph of RNG. Ther e ar e tw o main algor ithms- Kr uskal algor ithm and Prims algor ithm. Kruskal algorithm chooses edges of a gr aph that has minimum w eight. The edges (E) ar e arranged in an incr easing order . In Pr ims algor ithm MST is built by putting an arbitrary node in the tr ee. This eliminates the sear ch step r equir ed in Kr uskal algor ithm. The edges ar e added to the graph if they ar e smaller than the pr evious edges alr eady in the gr aph.
Li, Wan et al.[5] pr esented a pow er efficient sparse
spanner for wir eless ad-hoc netw or ks. Scalability is impor tant due to limited number of r esour ces. One approach is to maintain linear number of links. This is
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 3
ISS N 2229-5518
called sparseness. Power str etch factor is a measur e of efficiency. Pow er str et ch factor is defined as the ratio of minimum pow er needed to support any link to the least necessary. Pow er str etch factor for Gabriel graph is 1, for Yao graph it is bounded and for r elative neighbor hood graph it can as long as netw or k size-1. No geometr ic structur e with the constant degr ee bound has the least ener gy consumption path for all nodes. To gener ate a bounded degr ee graph with constant length str etch factor r eplace dir ected star consisting of all nodes towar ds a node
’u’ b y a dir ected T(u) of a b ounded degr ee w ith ‘u’ as sink
K-neigh[6] is also a neighbour based appr oach. Nodes do
not know their positions ,they j ust calculate the distance betw een itself and its neighbours.This assumes continuous communication r ange and defines it untill it r eaches k neighbour s. Connectivity is not guaranteed. W e estimate the value of k that guarantees connectivity of the communication gr aph with high pr obability,pr eferr ed
value of this 9. It is a fully distributed, asynchr onous, and localized pr otocol that follows the above appr oach and uses distance estimation
Alexis Papadimitriou et al.[7] pr esented a survey on topology contr ol algorithm in w ir eless sensor netw or ks .In
wir eless ad-hoc networ ks ther e is a possibility of deploying so many nodes in r elatively small ar ea. The nodes inter fer e with each other and sometimes use lar ge tr ansmission pow er to r each r emote nodes. These pr oblems can be solved by topology contr ol techniques wher e a deliberate attempt is made to r educe the initial topology of the networ k. Gabr iel graph is one hop r ealizable, planar ,
connected and localized algor ithm. Pow er str etch factor is bounded by one but the maximum node degr ee is unbounded. Relative neighbour hood gr aph is also one hop r ealizable, planar , and connected and dir ection based approach. Her e power str etch factor is unboun ded.
Kar p et al.[8] pr esented Gr eedy Per imeter Stateless Routing. It is based on planar graph traversal. Planar graphs ar e gr aph with no intersecting edges .It is per formed on per packet basis and does not r equir e nodes to stor e additional infor mation . The packet forwar ding technology used is gr eedy packet forwar ding. Sender
forwar ds the packet to an intermediate node which then forwar ds the packet position information r egar ding location of destination is included in the packet header . Gr eedy packet forwar ding includes 1) most forwar d w ithin transmission range 2) Near est with forwar d pr ogr ess (NFP). In most forward w ithin transmission range sender sends the packet to a node which is at the end of the transmission range.
In near est w ith forwar d pr ogr ess [NFP] packet is transferr ed to near est neighbour . But the main dr awback is that it may fail to find a path between sender and destination even if a r oute exists. To counter this pr oblem packet should be forwarded to the node with least backwar d pr ogr ess. But her e ther e is a possibility for looping. It enter s into gr eedy mode when it r eaches a node closer to its destination and enters into r ecovery mode when it arr ives at local maximum.
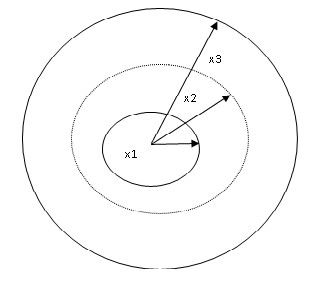
3. PRELIMIN AR IES
Figur e:1 Transmission pow er needed to locate nodes
Netw or k connectivity is affected by the tr ansmission range of the nodes. Tr ansmitting at high pow er w ill affect the transmission range of other nodes if the sour ce node is closer to destination node. By adjusting the tr ansmission pow er dur ing transmission a node can r each the next node. But fr equently adjusting the transmission pow er will not be suitable for nodes in most of the netw or ks. Netw or k may get congested if the tr ansmission r ange is high. But the transmission r ange cannot be too small. If it is too small traffic can incr ease in the given ar ea.
The above figur e shows the transmission pow er needed
to locate the nodes. Her e x3>x2>x1. Whenever a node wants to communicate to other nodes, it uses tr ansmission power to locate other nodes. For this it uses tr ansmission pow er . The nodes gradually incr ease the tr ansmission pow er to locate mor e and mor e nodes. If the node located at the innermost cir cle wants to locate its neighbor s, it has to adj ust its transmission power . By using x1 the node w i ll not be able to locate those neighbor nodes that ar e outside the coverage r egion. Hence it gr adually incr eases the
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 4
ISS N 2229-5518
transmission power fr om x1 to x2 . The node then stor es this information and tr ies to access other nodes that need to be communicated. Hence the pow er is incr eased fr om x2 to x3. This pr oceeds till the node is able to discover those nodes that need to be communicated. Networ k dynamics w er e not taken into account in the pr evious w or ks and hence they suffer ed fr om certain drawbacks. (i) Traffic load and channel status w er e not consider ed. Hence the nodes suffer ed fr om lar ge amount of r etransmissions when the channel status was deter iorated. As a r esult thr oughput and ener gy efficiency w er e also affected. (ii) Ener gy of the nodes w as not consider ed. In or der to impr ove networ k lifetime nodes should not lose their ener gy un necessar ily.
Thus the need for adaptive topology contr ol comes in to
the pictur e wher ein the nodes ar e able to adj ust their topology independently in accor dance w ith the changing networ k dynamics but at the same time maintaining the connectivity and lifetime of the netw or k.
4. PROPOSED WORK
In dynamic adaptive topology contr ol (DATC) networ k is divided into zones. Communication betw een differ ent zones takes place thr ough a central node which acts as a head node. When the ener gy of the head node dr ops r e- election of head node takes place and the node having higher ener gy b ecomes the new ‘head node’. Dynamic adaptive topology contr ol is based on thr ee w ell known planar str uctur es which ar e descr ibed as follows.
4.1. Relative Neighbourhood Graph [22] denoted by RNG is a dir ection based pr otocol and has an edge u,v if and only if||uv||<= 1 and the intersection of two open disks centr ed at u, v with radius ||uv|| contains no other node. RNG is the subset of GG and is planar and one hop r ealizable. It uses a cone based appr oach. Her e also the node ‘u’ gr ows its tr ansmission pow er until it finds a neighbour ‘j ’ which is then added to its neighb our list. It is mor e sparser when compar ed to GG. The power str etch factor is unbounded .It is a distrr ibuted pr otocol which pr eserves connectivity. The degr ee of the node is n-1.
4.2. Gabriel Graph [15] Gabr iel Graph denoted by GG has an edge uv if and only if ||uv||<=1 and the open disk using ||uv|| as diameter contains no other node. It is a planar and localzed algorithm and is also one hop r ealizable, symmetric and connected. Pow er str etch factor which is a measur e of efficiency is unity in Gabriel graph. Also the pow er consumption is given by |uv|2. The power str etch facto bounded by one but the maximum node degr ee is unbounded(<=n-1).
4.3 Lo cal Minimum Spanning Tree [3] denoted as LMST builds a connected global MST like topology w ith only bidir ectional links. Each node constr ucts the topology independently with the information that is locally collected and keeps one–hop on-tr ee nodes as neighbors. Topology constr uct ed pr eserves the netw or k connectivity but r equir es location information and the r esultant topology gets converted into a one with only bi-dir ectional links (after the r emoval of unidir ectional links). The bi dir ectionality of links is essential when the packets ar e to be transferr ed in an unr eliable wir eless medium. It is also impor tant in link level acknowledgements and also for medium access contr ol mechanisms like RTS/CTS in IEEE
802.11. The degr ee of the node is bounded by 6. Small node degr ee r educes contention and inter fer ence. LMST delivers most of the data.
Let G=(V,E) be an undir ected simple graph. The set of
nodes that node ‘k’ can r each by using the maximum transmission pow er can be given as NV k(G)={l ɛ V(G) : d(k,l) <=dma x } LMST involves 3 phases (i) information exchange: Each node ‘k’ collects information r egar ding other nodes in the networ k. This is done usually by br oadcasting ‘HELLO’ message at maximal tr ansmission pow er . Information in the hello message includes node id and node position. The interval between the br oadcast of HELLO messages depends on the mobility of nodes..Node
‘k’ gradually incr eases its transmission power to r each other nodes in its neighborhood (ii) topology construction: It is done based on Pr ims algorithm. The spanning tr ee
constr ucted using this is found to be pow er efficient. (iii) determination of transmission power : This is done usually by measuring the r eceived pow er of ‘HELLO’ messages. In or der to locate other nodes transmission pow er is gradually incr eased. This can be applied to pr opagation models like fr ee space pr opagation model and tw o ray gr ound model .
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 5
ISS N 2229-5518
while R is not empty do{
take an edge (i,j ) such that i ɛ S and j ɛ R and (i,j ) is the shortest edge
add (i,j ) to A r emove j fr om R and add j to S
}
else if(signal str ength is high and links ar e mor e)
{
foreach k ɛ V foreach l ɛ N(k) foreach o ɛ N(k)
if lar gest d(k,o)2 + d(l,o)2 < d(k,l)2
Figur e:2 A Zone Based Appr oach
4.4 Algorithm De scription
First the node determines the minimum tr ansmission pow er r equir ed to r each each neighbor in N(i) in its r espective zones. This information is stor ed in its neighbor list Nm(i). Then depending on the number of nodes links ar e selected and topology is constructed. Topology is constr ucted based on the thr ee planar str uctur es- Gabriel Graph, Relative neighborhood graph and Local minimum spanning tr ee. Gabr iel graph is used w ith nodes having lesser number of links as with gr eater number of links it will become less ener gy efficient. Relative neighbor hood graph can support lar ger number of links w hen compar ed to Gabr iel graph, but fails to maintain connectivity w ith lar ge number of nodes. Hence for nodes having lar ger number of links local minimum spanning tr ee is used to maintain connectivity betw een the nodes and incr easing networ k lifetime.
4.5. Algorithm for DATC
Let G(u)= (V(u),E(u)) be the input
If (signal str ength is high and links ar e mor e)
{
A= { }
S ={w } (w is an arbitrary node in V) R = V-{w }
remove l fr om N(k)

remove [k >l] fr om Nm(k)
}
else
{
foreach k ɛ V foreach l ɛ N(k) foreach o ɛ N(k)

if d(k,o)2 + d(l,o)2 < d(k,l)2 remove l fr om N(k) remove[k ->l] fr om Nm(k)
}
5. SIMULATION RESU LTS
In this section simulation r esults to demonstrate the effectiveness of ZBTC is pr esented. The pr otocol used is DSDV and the simulation tool used is NS2. A 500*500m
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 6
ISS N 2229-5518
r egion is consider ed and 20 nodes ar e deployed in the r egion. MAC scheme used in this approach is IEEE 802.11. The metrics used in this paper ar e listed as follows.
5.1 Number o f active links This parameter decr eases as
various algorithms ar e applied. But connectivity was found to be maintained
5.2 Number of loop s smaller number of loops indicate
gr eater packet delivery r atio.
5.3. Packet drop Smaller packet dr op indicates gr eater delivery of packets
In the simulation study the per formance of DATC is compar ed w ith the individual per formance of Gabriel graph, r elative neighborhood graph and local minimum spanning tr ee based on the above metr ics at differ ent speeds of 10m/s and 15m/s. The r eason for selecting Gabriel Graph, r elative neighbor hood Gr aph and LMST for comparison is that GG has an edge length that is r elatively long and pr eserv es all minimum ener gy paths when the
path loss exponent is 2. RNG is a sub graph of GG. LMST pr eserves node connectivity while pr eserving low transmission power .
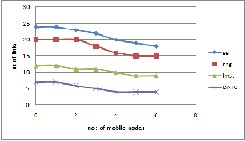
Figur e: 3 Number of active links versus mobility at 10m/s
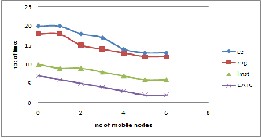
Figur e: 4 Number of active links versus mobility at 15m/s
Topology of a netw or k is defined by the set of active nodes and active links thr ough which communication occurs. But the set of active links can be contr olled. Instead of using all the links in the netw or k, the communication can be limited to some cr ucial links ther eby maintaining the connectivity of the networ k. Figur e 3 and 4 shows the comparison of active links betw een Gabr iel graph, r elative
neighbor hood graph, local minimum spanning tr ee and DATC and shows that number of links is found to be less in DATC.
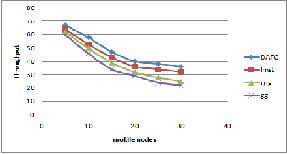
Fig.5 Thr oughput ver sus mobility at 10m/s
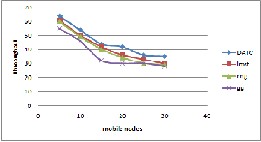
Fig.6 Thr oughput ver sus mobility at 15m/s
Thr oughput is the average r ate of successful message delivery over a communication channel. This data may be deliver ed over a link, or pass thr ough a certain networ k node. The thr oughput is usually measur ed in bits per second (bit/s or bps), and sometimes in data packets per second or data packets per time slot. The system throughput or aggr egate thr oughput is the sum of the data rates that ar e deliver ed to all terminals in a netw or k. Thr oughput is compar ed for Gabr iel Graph, Relative neighbour hood graph, localized minimum spanning tr ee and dynamic adaptive topology contr ol and found that throughput is mor e in dynamic adaptive topology control and least in Gabriel Graph
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 7
ISS N 2229-5518
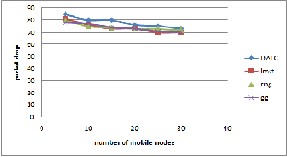
Fig.7 Packet dr op ver sus mobility at 10m/s
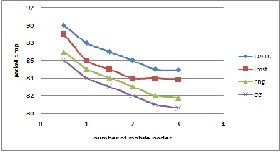
Fig.8 Packet dr op ver sus mobility at 15m/s
Packet loss usually occurs when the packets traveling through a channel fails to r each the destination. It is one of the important err ors that ar e encounter ed in digital communication. Figur e 7 and 8 compar es packet dr op for Gabr iel Gr aph, Relative neighbor hood Graph, Local minimum spanning tr ee and DATC and found out that DATC has less packet dr op when compar ed to other graphs. This is because number of loops is less in DATC when compar ed to Gabriel Graph, Relative neighbor hood Graph, Localized minimum spanning tr ee. This can affect networ k thr oughput as w ell. If a r outing loop occurs the packets will not be r outed pr oper ly due to some incorr ect r outing information cir culating in the networ k. One such symptom is count to infinity pr oblem wher e the older r outing information r eplaces the r outing updates for an un r eachable netw or k. The metric when passed fr om r outer to r outer incr eases gr adually. The routing loop will become infinite unless some limit is put on it. Routing loops ar e usually solved by on demand r outing. Pr otocols like DSDV, BGP, and EIGRP have built in loop pr evention.
6. CONCLUSION
In this paper a dynamic adaptive topology contr ol has been pr oposed. Var ious r outing pr otocols have been studied in the literatur e. In most of the existing w or ks connectivity is not pr eserved and also the networ k l ifetime is not guar anteed. In ad-hoc netw or ks nodes can move anywher e at any time. As a r esult topology has to be contr olled. The main featur es of this paper can be summarized as follows: (1) Networ k is divided into zones (2) nodes can adaptively adj ust t heir topology (3) connectivity is pr eser ved.
One of the main question that needs to be addr essed is
how to pr ovide seamless services as the nodes pr oceed
through the networ k. Hence mobility management is
consider ed for futur e w or k consider ing both layer 2 r outing and layer 3 r outing.
7. REFERENC ES:
[1] S. Narayanaswamy, V. Kawadia, R. S. Sr eenivas, and P.
R. Kumar , ‚Pow er contr ol in ad-hoc networ ks: Theory, ar chitectur e, algor ithm and implementation of the COMPOW pr otocol,‛ in Proc. European Wireless 2002 (EWC’02), Febr uary 2002, pp. 156–162
[2] L.Li,J.Y Halper n, P.Bahl, Y.M.Wang, and R.
Wattenthofer ,‛Analysis of a cone b ased Distr ibuted
Topology Contr ol Algor ithm for W ir eless Multi hop networ ks‛ Proc.20th ACM Symp. Principles of distributed computing (PODC ‘01), pp.264 -273,2001
[3] Rogen Wattenhofer and Aar on Zollinger ,‛ XTC: A
topology contr olalgor ithm for Ad-hoc networ ks‛, Proc.18th Int’l Parallel and distributed P rocessing Symp.(IPDS ‘04),pp.26-30,2004.
[4] N.Li, J.C.Hou and L.Sha,‛ Design and analysis of an
MST- based topology control algor ithm ,‛in Proc .IEEE INFOCOM, San Fransisco, CA, Apr.2003,pp.1702 -1712..
[5] LI, X.-Y., W AN, P.-J., AND W ANG, Y. Pow er efficient
and spar se spanner for wir eless ad hoc networ ks. In
IEEE ZC3N, 2001.
[6] LI, X.-Y., WAN, P.-J., AND W ANG, Y. Power efficient and sparse spanner for wir eless ad hoc networ ks. In IEEE ZC3N, 2001
[7] B. Kar p and H. Kung, ‚ GPSR: Gr eedy Perimeter Stateless Routing for W ir eless Netw or ks ‛ , In Proc. Of the 6th Annual International Conference on Mobile Computing and Networking (MOBICOM), pages243–254,
2000.
[8] Guangquan Zhang, Zhaoliang Zhang, Jianxi Fan,‛ A locally adjustable planar structur e for adaptive topology contr ol in wir eless ad hoc networ ks‛, in Proc. IEEE transactions on parallel and dis tributed systems, pp. 1387-
1487,Oct .2010.
[9] Volkan Rodoplu and Ter esa H. Meng, ‚Minimum ener gy mob ile w ir eless networ ks,‛ in Proceedings of the
1998 IEEE International Conference on Communications,
ICC’98, 1998, vol. 3.
[10] Xiang-Yang Li and Peng-Jun Wan, ‚Constr ucting minimum ener gy mob ile wir eless netw or ks,‛ Submitted to for publication, 2001.
IJSER © 2012 http :// www.ijser.org
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 8
ISS N 2229-5518
[11] Roger Wattenhofer , Li Li, Paramvir Bahl, and Yi -Min Wang, ‚Distr ibuted topology contr ol for wir eless multi hop ad-hoc netw or ks,‛ in IEEE INFOCOM’01,
2001.
[12] R. Ramanathan and R. Rosales -Hain. ‚Topology Contr ol of Multi hop Wir eless Networ ks Using Transmit Pow er Adj ustment‛, Proc. IEEE INFOCOM
2000, Tel Aviv, Isr ael, Mar ch 2000, pp. 404 –413.
[13] M. Mauve, J. W idmer , and H. Hartenstein, ‚A sur vey on position-based r outing in mobile ad-hoc networ ks,‛ IEEE Network Magazine, 15(6):30{39, November .
[14] ‚Routing with guar anteed delivery in ad hoc wir eless networ ks, 3rdint. Workshop on Discrete Algorithms and Methods for Mobile Computing and Communications, Seattle, August20, 1999, 48-55.
[15] K. Gabriel and R. Sokal,‛ A New Statistical Appr oach
to Geographic Var iation,‛ Analysis. Systematic Zoology,
18:259–278, 1969.
*16+ X.Y.Li and P.J.Wan, ‚Constr ucting Minimum Energy
Mob ile W ir eless Networ k‛in ACM MobiHoc’01 , pp.
55–67
[17] R. Banner and A.Or da, ‚Multi Obj ective Topology Contr ol in Wir eless Netw or ks,‛ Proc. IEEE Compute r and Communications Societies (INFOCOM), 2008,pp. 26-
30,2004
[18] J.Cartigny, F.Ingel r est, ‘‘localised LMST and RNG based Minimum Ener gy Br oadcast Pr otocols in Ad- hoc networ ks,’’ Ad-Hoc Networks, vol 3, pp. 1-16, Jan.
1996.
[19] F.P Pr eparata and M.I.Shamos,‘‘Computational geometry
an Introduction’’ Ad-Hoc Networks, vol 3, pp. 1-16, Jan.
1996
[20] A.C.Yao, ‘‘On Constructing Minimum Spanning Tr ees in K- Dimensional Spaces and Related Pr ob lems,’’ SIAM .J.Computing, vol 11, pp. 721-736, Nov. 1986
[21] D. Blough, M. Leocini, G. Resta and P.Santi, ‚The k-
neigh Pr otocol for Symmetric Topology Contr ol in Ad- Hoc Networ ks,” Proc ACM MOBI-HOC ’03 pp.141-152
*22+ A.K.Jeng ‚ The r-neighbour hood graph: An Adj ustable

planar Str uctur e for topology contr ol in mobile
adhoc networ ks‛. In proc IEEE INFOCOM, apr 2007 pp
536- 549
[23] A. Kar pa and D . Estr in,‛ A ASCENT : Adaptive Self
Configur ing Sensor Networ ks,‛. in Proc IEEE pp 24-
60, 2002
[24] C.R Lin and M. Ger la, ‚Adaptive cluster ing for mobile wir eless networ ks,‛ Mobile Netw or ks and Applications,‛Proc. IEEE Computer and Communications Societies (INFOCOM), 1997,pp. 1265-1275
[25] I. Stojmenovic, editor , Handbook of Wireless Networks
and Mobile Computing, chapter 18, pages 393 {406} John Wiley & Sons, 2002.
[26] J. W u, H. Li, ‚A dominating-set-based r outing scheme
in ad hoc wir eless networ ks‛, in: Proceedings of the Third Inte rnational Workshop Discrete Algorithms and Methods for Mobile Computing and Communication (DIALM_99), Seattle, WA, USA, 1999, pp. 7 –14
*27+ A. Clementi, P. Penna, R. Silvestr i, ‚The pow er r ange assignment pr oblem in radio netw or ks on the plane,‛ in: H. Reichel, S. Tison (Eds.), Proceedings of 17th Symposium on Theoretical Computer Science (STACS_00), Lecture Notes in Compute r Science, vol. 1770, Springer , Ber lin, 2002, pp. 651–660.
[28] E. Lloyd, R. Liu, M. Mar athe, R. Ramanathan, S. Ravi
,‛Algor ithmic aspects of topology contr ol pr ob lems for adhoc netw or ks,‛ in: Proceedings of the Annual Workshop on Mobile and Ad Hoc Networking and Computing (Mobi-Hoc_2002), Lausanne, Switzer land,
2002
*29+ W . Liang, ‚Constructing minimum-ener gy br oadcast tr ees in wir eless ad hoc netw or ks,‛ in: Proceedings of the Annual Workshop on Mobile and Ad Hoc Networking and Computing (MobiHoc_2002 ), Lausanne, Sw itzer land, 2002
[30] J. Cartigny, D. Simplot, I. Stojmenovi_c, ‚Localized minimum- ener gy br oadcasting in ad hoc networ ks,‛ in:Proceedings of the IEEE INFOCOM_2003, San Francisco, CA, USA, 2003.
Author ’s B iogr aphy
Ms. Diya Ann Kur uvila r eceived B.Tech degr ee in Electr onics and communication fr om Mahatma
IJSER © 2012 http:// www.ijser.o
Inte rnatio nal Jo urnal o f Sc ie ntific & Eng inee ring Re se arc h Vo lume 3, Issue 3, Marc h -2012 9
ISS N 2229-5518
Gandhi University, in 2010. Since July 2011, she has been a student of M.Tech in Communication systems in Karunya Univer sity, Coimbator e. Her r esear ch inter est includes topology control in w ir eless netw or ks.

Mrs. Jennifer S Raj r eceived the Masters degr ee in communication System fr om SRM University, India. Curr ently she is pur suing Ph.D in Information and Communication Engineer ing at Anna Univer sity of Technology, Coimbator e, India and
wor king as a Assistant Pr ofessor at Kar unya University,
Coimbator e, India. Her inter ests ar e in w ir eless netw or ks with self or ganization and topology contr ol str uctur es. She is a life member of ISTE, India. She is book r eview er for Tata Mc Gr aw hill publication and publishes mor e than fifteen r esearch articles in the j ournals and IEEE
confer ences.
IJSER © 2012 http :// www.ijser.org









