The research paper published by IJSER journal is about Digital watermarking using DWT-SVD 1
ISSN 2229-5518
Digital Watermarking Using DWT-SVD
P.Tejaswini, K.Manjunath, A Mahendran
ABSTRACT -This project proposes the embedding is done by modifying the specific bits of the singular values of the transformed host ima ge with the bits of the watermark image’s singular values. First, the DWT-SVD transform is applied to each sub-band of the transformed image and the singular values of each sub-band and the singular values of the watermark image are converted to semi-binary arrays.
Finally, the bits of the singular values of the watermark image are inserted into the selected bits of the singular values of decomposed host image’s sub-bands. The experimental results show that the proposed method is more robust against different geometric and non geometric at tacks and the watermarked image looks visually identical to the original one. Resizing of the geometric and non geometric attacks to the image.
Robust Image W atermarking, Blind image W atermarking, Discrete Wavelet Transform, and Singular Value Decomposition.
With the spread of editing software and the Internet, illegal operations, such as replication, forgery, and the like have become hard to prevent. These illegal operations not only invade the property rights of the authors of the digital content but also reduce motivation for their construction.
In today’s age of the internet and computers,
multimedia data can easily be copied and circulated
illegally. Therefore copyright protection of multimedia plays an essential role. One of the best methods to protect copyright and proof of ownership is digital image watermarking. Digital image watermarking is a process of modifying the host image with embedding an invisible mark data such as a binary or grey scale logo.
Good watermarking methods for copyright protection applications need to fulfil some important requirements, first of all robustness is very important that means the proposed methods must resist against different kinds of attacks. Second the watermarked image need to have a good transparency. Finally the watermark extraction process should be blind which means that it doesn’t need to the original host image for watermark extraction.
Digital image Watermarking algorithms can be divided into two main categories according to the embedding domain: spatial or transform domain schemes. Although, the spatial domain watermarking methods are simpler, these methods are not robust against different geometric and non geometric attacks. Unlike, the transform domains watermarking methods are more complex and provide more robustness against different attacks.
watermarking method is introduced by Gorodetski et al. They embedded the watermark into the singular values of the host image.
Most of SVD-DWT based image watermarking methods are semi or non blind which need reference or original image for their watermark extraction process. In this paper, we propose a new robust SVD based method that acquits needing the original or reference image in extraction process. In the proposed method, singular values of a grey scale watermark image and singular values of decomposed image’s sub-bands are converted into the specific semi-binary arrays. To achieve higher robustness and transparency, the bits of singular values of watermark image are embedded into the specific bits of the singular values of decomposed host image’s sub-bands.
The main objective of this project is to:
The image is divided into two different watermarks are inserted into the horizontal and vertical sub-bands of wavelet coefficients. It is recognized that Human Visual System (HVS) is less sensitive to the removal of smaller.
The DWT is applied to the host image. Then, the SVD transform is applied to each sub-band of the transformed image and the singular values of each sub-band and the singular values of the watermark image are converted to semi-binary arrays.
Finally, the bits of the singular values of the watermark image are inserted into the selected bits of the singular values of decomposed host image’s sub-bands.
IJSER © 2012
The research paper published by IJSER journal is about Digital watermarking using DWT-SVD 2
ISSN 2229-5518
The singular value decomposition (SVD) is an important factorization of a rectangular real or complex matrix.
An image could be regarded as a matrix of nonnegative scalar entries. Assume B is M×N image; the SVD of B is defined as:
B= USV' (1) U'.U = I, V'.V= I (2) S = diag(σ , σ2 ,σ3 ,…) (3)
B=σ 1U 1V1 + σ 2U2 V2 + σ 3U3 V 3…
+ σ P U PV P , P=min(M,N) (4)
Where p is the rank of matrix B. σi are the singular values and sorted in descending order.
The main advantage of using SVD in
watermarking is insignificant changes of the singular
values of watermarked image under the common image processing attacks.
Assume X M×N and W M1×N1 are the grey scale original and watermark image, respectively. To embed the grey scale watermark image, the watermark embedding algorithm is formulated as follows:
(1) Perform K levels of DWT on the original image. The four sub-bands obtained in the last decomposition level are labeled LLK, LHK, HLK and HHK.
![]()
![]()
![]()
![]()
(2) Perform SVD transform to the four top sub-band of the decomposed host image,
![]()
![]()
X k=U kS k (V k)'
Where β i are singular values of S x , i = {1,2,..., p}
,θ = {LLK , LHK , HLK and HHK} and p is the rank of
matrix
(3) Apply SVD transform to the watermark image and convert the singular values of the watermark image to real numbers in [0 255] domain,
W=UW SW (VW)' (6)
βiW=α× βiW , α=255/β1, i={1,2,….,p} (7)
Where βi are the singular values of SW, p is the rank of
matrix.
![]()
![]()
(4) Using Algorithm1, convert βiW and βi to semi binary arrays which are denoted by βiWar and β i ar, respectively.![]()
(5) Insert βiWar bits into βi aras follows (see Fig 2):
βiLLar (1)= βiWar (1), βiHLar (2)= βiWar (5)
βiLLar (2)= βiwar (2), βiHLar (4)= βiWar(6) (8)
βiLHar (2)= βiWar (3), βiHHar(2)= βiWar(7)
βiLHar (4)= βiWar(4), βiHHar(4)= βiWar(8)
6) Using algorithm 2, construct the new singular values of each sub-band which are denoted by SX*θ![]()
![]()
![]()
![]()
(7) Obtain the four sub-bands of the modified decomposed reference image as,
X k=U kS k (V k)’
(8) Perform K levels of inverse discrete wavelet transform to get the watermarked image (X* M×N ).
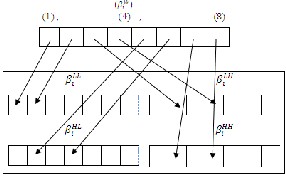
FIG.1: THE BITS INSERTING PROCESSES
(1)Perform K levels of DWT on the watermarked image. The four sub-bands obtained in the last decomposition level are labeled LLK, LHK, HLK and HHK.
(2) Apply SVD transform to each sub-band’s of![]()
![]()
![]()
![]()
decomposed watermarked image,
![]()
X * k=U* XS* X (V* X)' (10)
Where β i* are singular values of S X *θ , i = {1,2,..., p} , θ =
{LLK , LHK , HLK and HHK} and p is the rank of matrix.
(3) Convert the singular values of all sub bands (βi*θ) to semi-binary arrays, using Algorithm1, which are denoted by
β i* θ ar.
IJSER © 2012
The research paper published by IJSER journal is about Digital watermarking using DWT-SVD 3
ISSN 2229-5518
(4) Extract the singular values of watermark image’s bits
from βi θ*ar according to Fig. 3,
βiextar(1)= βi*LLar(1), βiextar(5)= βi*HLar(2) βiextar(2)= βi*LLar(2), βiextar(6)= βi*HLar(4) βiextar(3)= βi*LHar(2), βiextar(7)= βi*HLar(2) βiextar(4)= βi*LHar(4), βiextar(8)= βi*HLar(4)
(11)
(5) Using Algorithm2, The extracted singular values bits from sub bands are converted to real numbers, which are denoted by βiext and reconstruct the singular values as:
βiext = βiext /α, i {1,2,..., p} (12)
(6) Apply inverse SVD to construct the watermark image
using the singular vectors which saved in embedding process.
Wext = UW S W ext (VW)’ (13)
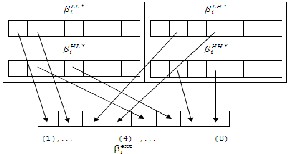
FIG.2: THE BITS EXTRACTION PROCESSES
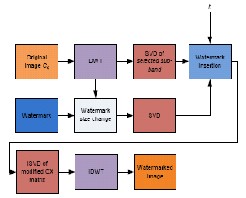
FIG.3: Water mark insertion using DWT-SVD
There exist two groups of invisible digital image watermarking systems [2]. The first group, spatial watermarking, uses the spatial (time) domain of an original image for watermark insertion, the second group, frequency watermarking, uses the frequency domain for it. The frequency domain based watermarking systems are in principle more resistant to a bigger group of possible attacks [3], [4]. The frequency domain transformations, namely the discrete cosine transformation (DCT) and discrete wavelet transformation (DWT), are very popular because the JPEG (Joint Picture Expert Group) and JPEG-
2000 image compression standards use these transformations in their compression schemes. We will concentrate on watermarking techniques that already use the 2D-DWT. New methods based on frequency domain watermarking techniques and SVD will be presented in the following chapters along with testing and comparing. A binary image or a binary representation of some message can be used as a watermark.
Bag | Circles | |
PSNR(dB) | 41.6256 | 44.1607 |
Table.I: PSNR Values of Original image
Image Attacks | Bag | Circles |
Cropping | 0.3051 | 0.6469 |
Resizing | 0.5006 | 0.6181 |
Median Filtering | 0.6207 | 0.2625 |
Row-Column Blanking | 0.2268 | 0.2684 |
Row-Column Copying | 0.3202 | 0.2740 |
Brightness | 0.1429 | 0.4384 |
Bit Plane Removal | 0.2940 | 0.3620 |
Table.II Correlation Coefficient on Watermarked image
IJSER © 2012
The research paper published by IJSER journal is about Digital watermarking using DWT-SVD 4
ISSN 2229-5518
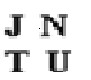

FIG. 4: ORIGINAL TEST IMAGE FIG.5. Watermark Gray Scale (JNTU)
The image is divided into two different watermarks are inserted into the horizontal and vertical sub-bands of wavelet coefficients. It is recognized that Human Visual System (HVS) is less sensitive to the removal of smaller. In this paper, a new blind digital image watermarking scheme using SVD in DWT domain is presented.
The transparency and robustness of the proposed
method is investigated with extensive experiments. The
experimental results show that the proposed method offers
good transparency for the watermarked images, which is evaluated by PSNR. The performance of the proposed method against different attacks of the watermarked image is evaluated by correlation coefficients of extracted watermark logos and some subjective image tests. The experimental results show that the proposed method can effectively resists against geometric and non geometric attacks
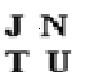
FIG.6: Extracted watermarked Images FIG.7. Extracted Gray Scale (JNTU)
[1] C. C. Chang, P. Tsai, and C. C. Lin, "SVD-based digital image watermarking scheme," Pattern Recognition Letters,
vol. 26, pp. 1577–1586, 2005.
[2] R. Liu, T. Tan, “A SVD-based watermarking scheme for protecting rightful ownership,” IEEE Transactions on Multimedia, vol.4, pp. 121-128, 2002.
[3] G. Bhatnagar and B. Raman, "A new robust reference watermarking scheme based on DWT-SVD," Computer Standards & Interfaces, vol. 31, pp. 1002–1013, 2009.
[4] E. Ganic, A. M. Eskicioglu, “Robust DWT-SVD domain image watermarking: embedding data in all frequencies,” ACM Multimedia and Security Workshop 2004, Magdeburg, Germany, 2004, pp. 20-21.
[5] C.H. Lin, J.C. Liu, P.C. Han, “on the security of the full- band image watermark for copyright protection,” IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, 2008, pp. 74-79.
IJSER © 2012
International Journal of Scientific & Engineering Research Vo lume 3, Issue 8, August-2012 5
ISSN 2229-5518
IJSER ©2012