International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 1
ISSN 2229-5518
Digital Video Watermarking : A Retrospective
Dixa Patel, Nehal Chitaliya, Manoj Pandya, Parth Trivedi, M.B.Potdar, Parul Thakkar
Abstract—Due to the ease of availability for multimedia content over the Internet, it is too easy for the owners to transfer the data (audio or video) over the internet, and hence it can be copied and stored easily without any loss in fidelity. These leads to serious problem of Copyright Infringe- ment, Ownership Protection. Digital Watermarking is the technique to address such issues. This paper incorporates the detail study of Video wa- termarking techniques, various type of watermarking Attacks & Application.
Index Terms— Digital Multimedia, Fidelity, Spatial Domain, DCT, DWT, Robust
—————————— ——————————
approaches of data security. Digital content is encrypted at
In the past several years there has been an explosive growth in multimedia and network technology which leads to the neces- sity of developing some secure methods for legal distribution of the digital content. As digital multimedia works (video, audio and images) become available for retransmission, re- production, and publishing over the Internet, a real need for protection against Lossless and unlimited duplication, arbi- trarily modification, unauthorized uploads, illegal redistribu- tion is increasing day by day. Digital watermarking is the technology that provides and ensures security, data authenti- cation and copyright protection to the digital media. Digital watermarking is the embedding of secret information (i.e. Wa- termark) into the digital media (Image, audio or video) in such a way that any attacker can’t remove or replace it. Application for Digital watermarking involves Copyright protection, Fin- gerprinting, Broadcast monitoring, Video Authentication etc. For the protection of confidential and sensitive data from un- authorized access and tampering various methods for data hiding is used. Cryptography technique includes the encryp- tion & decryption process. Encryption Process converts mes- sage into unreadable format which is known as Cipher text. Transmitted Cipher text can be decrypt into original message by only those for whom it is intended. So, Cryptography mainly provides security to message [18] [30] While steganog- raphy is mainly used to hide any secret information within the original message. Steganography is a combination of two words, which are taken from Greek Language: ‘stegano’ means cover and graphie means writing, so called as Cover writing. Secret information can only identify and extract by intended recipient [28]. Watermarking is the direct embedding of additional information (Watermark) into the original con- tent or host signal in a way that any attacker cannot remove or replace it [19][4]. Steganography is useful when the protection of secret information is the required while watermarking is more useful to protect the original content from illegal use. The concept of cryptography is totally different then these
transmitter using a key and can be decrypted at receiver if and only if the correct key is available. Cryptography gives ad- vantage only through the channel. Once encrypted content is decrypted using a key at receiver, no means of security is available for protecting digital content from copyright. There- fore, encryption must be replaced by some method which pro- tects digital content after decryption and there concept of wa- termarking comes [18].
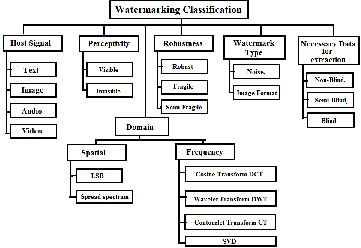
Watermark can be classified according to host signal, percep- tivity, robustness, and watermark type, Domain of watermark embedding, application and according to data required for watermark extraction. Fig.1 gives overall idea about watemark classification.
Fig 1 : Watermarking Classification
IJSER © 2014
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 2
ISSN 2229-5518
Watermarking technique can be classified depending on the media into which watermark is embedded. Text watermarking inserts a watermark in the font shape and the space between characters and line spaces. This has some disadvantages that one cannot detect the watermark in case of modulating the fonts.[7] Image watermarking embeds a special Information (Logo, Stamp, Label etc.) to an image and detects or extracts it later for ownership confirmation. This approach is most wide- ly used and it utilizes the characteristics of human visual sys- tem.[19][4][25].Video watermarking is an extension of image watermarking. This method requires real time extraction and robustness for compression. Video is a three dimensional sig- nal having 2D in space (Image) and 1D in time. Time synchro- nization is one of the most important parameter which differs Video Watermarking from Image Watermarking. Interest in Audio watermarking increases because of the internet music, MP3. This approach needs watermark robustness and inaudi- bility like other cases.[18][2][16]
According to human visual perception, Watermark can be classified as Visible or Invisible. In visible watermarking, Wa- termark is transparent. As the watermark is visible to viewer, it cannot remove the copyright illegally. It confirms the au- thentication and mainly used in logo or trademark label. Dis- advantage of visible watermark is its fragility to attack. Also, watermark embedding process degrades quality of original content in some cases. Another type of watermarking is Invis- ible which is mainly used as a proof of ownership. Invisible watermark is very robust as compared to visible.[18]
Watermarks need robustness to protect the ownership from various attacks. There are mainly three type of watermark: Robust, Semi-Fragile and Fragile. Robust watermark is very difficult to extract and so cannot remove or replace easily. Semi-fragile watermark is capable of tolerating some degree of the change to a watermarked frame, such as the addition of quantization noise from lossy compression. Fragile watermark is designed to be easily destroyed if a watermarked frame is manipulated in the slightest manner. This watermarking method is mainly used for the protection and the verification of original contents.[18]
Stamp or Label. Visual degradation of original watermark is possible to observe once it is extracted. [18]
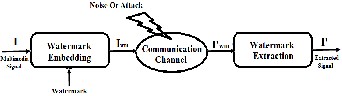
Fig 2: General Framework of watermarking System[25]
As shown in Fig 2. , The general framework of watermark- ing contains three main components: Embedding, attacker, and Extraction. The embedding algorithm accepts the multi- media signal I, and the watermark, and generates a water- marked signal Iwm. The watermarked signal is then commu- nicated to another person via the communication channel. If third person or the communicated one, makes any changes whether malicious or not, then it is termed as an attack. But the term is mainly used when intruder attempts to remove the watermark by changing the contents of multimedia by using common signal processing operations or some intentional at- tacks like adding noise to the multimedia content. Detecting/ extracting algorithm is used by detector/extractor which is then applied over the attacked signal I’wm to detect the pres- ence or extract the watermark from it. If the signal does not undergo any change during transmission, then the watermark will be present and can be extracted easily . The extracted sig- nal is represented as I’[25].Attacks can be intentional or unin- tentional. The unintentional attacks involve lossy copying, Compression of video, Change of frame rate or Change of Resolution. The intentional watermark attack include various frame attacks like filtering attacks, Geometrical attack and noise adding attack.[16] Table 1. Shows various type of inten- tional attack with examples [15][20].
Table 1: Various type of attack.
The watermark which is embedded into original multimedia content are of various type. Embedded Watermark can be Noise or Image. Noise can be randomly generated PN se- quence, Gaussian Sequence or can be Chaotic sequence.PN sequence is widely used watermark having a good feature of self-correlation function. It is robust against cryptographic attack but weak for image processing, noise & compression attack. Gaussian sequence is a random generation with Gauss- ian distribution N(0,1).It is mainly used for extracting multiple inserted watermark. Chaotic sequence is very easy to generate. New chaotic sequence can be generate by simply modifying initial values. Image watermark can be Binary Image, logo,
IJSER © 2014
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014 3
ISSN 2229-5518
These are some parameters needs to consider for implementa- tion of watermarking techniques are :
1. Transparency
2. Security
3. Ease of embedding and retrieval
4. Robustness
5. Effect on bandwidth
6. Interoperability
1. Transparency:
The most fundamental requirement for any Watermarking method shall be such that it is transparent to the end user. The watermarked content should be consumable at the intended user device without giving annoyance to the user. Watermark only shows up a watermark-detector device[18][30].
2. Security:
Watermarked information shall only be accessible to only authorized parties. They only have the right to alter the Watermark content. Encryption can be used to prevent unauthorized access of the watermarked data[18][30].
3. Ease of embedding and retrieval:
Ideally, Watermarking on digital media should be possible to be performed on the fly. The computation needed for the selected algorithm should be least[18].
4. Robustness:
Watermarking must be robust enough to withstand all kinds for signal processing operations attacks or unauthorized access. Any attempt, whether intentionally or unintentionally, that has a potential to alter the data content is considered as an attack. Robustness against attack is a key requirement for Watermarking and the success of this Technology for copyright protection depends on its stability against attacks[18].
5. Effect on bandwidth:
Watermarking should be done in such a way that it does not increase the bandwidth required for transmission. If Watermarking becomes a burden for the available bandwidth, the method fails.[18]
6. Interoperability:
Digitally watermarked content shall still be interoperable so that it can be seamlessly accessed through heterogeneous networks and can be played on various plays out devices that may be aware or unaware of watermarking techniques.[18]
Current video watermarking techniques can be classified into two major types: spatial-domain watermarking techniques and Frequency domain watermarking techniques.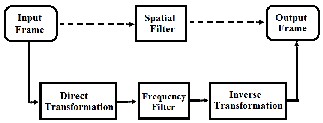
Fig 3 : Brief Idea of Spatial and Frequency Domain
As shown in Fig.3, In Spatial-domain techniques watermark is embedded in the frames of given video by modifying its pixels directly. These techniques are easy to implement and require few computational resources but not much robust against at- tacks. In case of transform-domain techniques, first step is to implement any transform (Fourier, Cosine, Wavelet etc.) on extracted Video Frames and then watermark can be embed by modifying the coefficients of the transformed video frames. Compared to spatial-domain techniques, frequency-domain watermarking techniques proved to be more effective with respect to achieving the imperceptibility and robustness re- quirements of digital watermarking algorithms.[16]
Spatial domain digital watermarking algorithms directly load the raw data into the original video frame [13]. Spatial water- marking technique embed the watermark in only one of the colour band (either Red, Green or Blue Channel) of video frame using colour separation. So, it is difficult to detect em- bedded watermark under regular viewing [9]. Some of its main algorithms are as discussed below:
The type of inserted watermark is Image for LSB meth- od. For embedding the watermark, a subset of image pixels is selected and then Least Significant Bit (LSB) of each of the selected pixels is substituted by watermark bits. The watermark may be spread throughout the frame or in the selected locations of the frame. Ad- vantage of this method is that it is easy to implement and does not generate serious distortion to the video; however, it is vulnerable to attacks and watermark can be easily destroyed.
IJSER © 2014
4
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014
ISSN 2229-5518
Patchwork is a data hiding technique developed by Bender et alii and published on IBM Systems Journal, 1996[3]. It is based on a pseudorandom, statistical model. It works by invisibly embedding a specific statistic, with a Gaussian distribution, into the host image. Two sets of pixel, or patches, of the image are chosen, the first A and the second B. Then the algorithm works by slightly brightening points in A, while darkening of the same factor those in B. One of the most important characteristics of patchwork is its resistance to cropping and to gamma and tone scale corrections [27]
In Correlation based technique, type of watermark used is Noise and Image both. A pseudo-random noise (PN) pattern is added to the extracted video frame. In this technique, there is a major trade-off between robustness and quality of watermarked image. Watermark can be extract by generating the same pseudo-random noise pattern at the receiver end, and using correlation technique, similarity between the extracted watermark and original watermark is computed. [16]
Frequency-domain methods are more widely used as com- pared to spatial-domain methods. Here, the watermark is em- bedded in the spectral coefficients of the original video frame. the Discrete Cosine Transform (DCT), Discrete Fourier Transform (DFT), and Discrete Wavelet Transform (DWT) are widely used transforms. The reason for watermarking in the frequency domain is that the characteristics of the Human Visual System (HVS) are better captured by the spectral coeffi- cients [10][12][15]. Some of its main algorithms are discussed below:
DCT like a Fourier Transform, represents data in terms of frequency space rather than an amplitude space. DCT based watermarking techniques are ro- bust compared to spatial domain techniques. Such al- gorithms are robust against simple image processing operations like low pass filtering, brightness and con- trast adjustment, blurring etc. However, they are dif- ficult to implement and are computationally more ex- pensive. At the same time they are weak against ge- ometric attacks like rotation, scaling, cropping etc. DCT domain watermarking can be classified into Global DCT watermarking and Block based DCT wa- termarking. Embedding in the perceptually signifi- cant portion of the image has its own advantages be- cause most compression schemes remove the percep- tually insignificant portion of the image [16][31].
IJSER © 2014
Wavelet Transform is a modern technique frequently used in digital image processing, compression, watermarking etc. The transforms are based on small waves, called wavelet, of varying frequency and limited duration. The wavelet transform decomposes the image into three spatial directions, i.e. horizontal, vertical and diagonal. Hence wavelets reflect the anisotropic properties of HVS more precisely. Magnitude of DWT coefficients is larger in the lowest bands (LL) at each level of decomposition and is smaller for other bands (HH, LH, and HL) [9]. Robustness of embedded watermark can be increase at the cost of visible distortion [9]. However, DWT is much preferred because it provides both a simultaneous spatial localization and a frequency spread of the watermark within the host image. [5].DWT is more advantageous than DCT as it is multi-resolution transform and hence provides resolution from lower level to higher level which facilitates various levels to embed the watermark as compared to DCT. Also, Wavelet transform provides better HVS than the DCT. [8] But Computational complexity & hence time complexity of DWT is more compared to DCT and it is more time consuming for video watermarking. As Feig (1990) pointed out it only takes 54 multiplications to compute DCT for a block of 8x8, unlike wavelet calculation depends upon the length of the filter used, which is at least 1 multiplication per coefficient [8]
Transforms a continuous function into its frequency components. It has robustness against geometric at- tacks like rotation, scaling, cropping, translation etc. DFT shows translation invariance. Spatial shifts in the image affects the phase representation of the image but not the magnitude representation, or circular shifts in the spatial domain don't affect the magnitude of the Fourier transform. DFT is more robust against geometrical attacks as compared to DWT and DCT because DFT is rotation, scaling and translation (RST) invariant. The spatial domain techniques, DCT and the DWT are not RST invariant and hence it is diffi- cult to overcome from geometric distortions. [8]
5
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014
ISSN 2229-5518
Contourlet transform uses Pyramidal Directional Fil- ter Bank structure, which represents an image, multi- resolutionally and multi-directionally to capture the contours and fine details for image analysis. This Py- ramidal Directional Filter comprises of Laplacian Pyr- amid (LP) and Directional Filter Bank (DFB) Struc- ture. Laplacian Pyramid used to capture the discon- tinues at edge point and Directional Filter Bank links these point discontinues into linear structure and re- sults in a contour segments and thus this process called as Contourlet Transform. This can be carried up to multiple levels [24].The two-dimensional singu- larities found in images cannot be captured easily by wavelets. Therefore, contourlet transforms is used to achieve directionality and multi resolution for image signals. The contourlet transform efficiently repre- sents contours and textures are in an images [24].
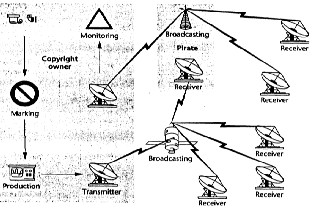
Fig 4. : Broadcasting environment for the Watermarking algorithm.[2]
Figure 4 sketches the basic scenario for which the watermark- ing algorithm was designed. A video stream acquired using a digital device is subsequently processed in the TV production chain and finally broadcast as an MPEG-2 bit stream. The digi- tal data is marked directly after recording and before entering the production chain. The data is not necessarily recorded in a closed studio environment; it can be recorded in the field and subsequently transmitted to the broadcaster’s headquarters. The raw material is cut and assembled during the production process. Other parties can digitally record the data and broad- cast it again instantly, or with some delay, as a digital video stream without any loss of quality. The watermark monitoring process can check for the watermark and automatically detect unauthorized use of copyrighted material.[2]
Table 2. Video watermarking : Application & Associated purpose[7]
Application | Purpose of the Embedded watermark |
Copy Control | Prevent unauthorized copying |
Broadcast Monitoring | Identify the video item being broadcasted |
Fingerprinting | Trace back a malicious user |
Video Authen- tication | Insure that the original content has not been altered |
Copyright Protection | Prove Ownership |
Enhanced Video Coding | Bring additional information E.g. for error correction |
In order to evaluate the performance of the watermarked frames, there are some quality measures such as SNR, PSNR, MSE, and NC.
The MSE (mean square error) is defined as average squared difference between a reference video frame and watermarked frame. It is calculated by the formula given below
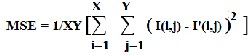 (1) In eq.1, X and Y are height and width respectively of the video frame, I (i, j) is the pixel value of the watermarked frame and I’(i, j) is the pixel value of the original frame. [22]. Ideally, Val- ue of MSE should be minimum.
(1) In eq.1, X and Y are height and width respectively of the video frame, I (i, j) is the pixel value of the watermarked frame and I’(i, j) is the pixel value of the original frame. [22]. Ideally, Val- ue of MSE should be minimum.
SNR (Signal to Noise ratio) measures the sensitivity of the im- aging. It provides the strength of signal against the back- ground noise. It is calculated by the formula given below, [9]
![]() (2)
(2)
The PSNR (peak signal to noise ratio) is used to determine the degradation in the watermarked video. It is calculated by the formula as
![]() (3) In eq. 3 , L is the peak signal value of the watermark image which is equal to 255 for 8 bit images. [3] Ideally, PSNR value should be in between 40 to 60.Higher value of PSNR indicates that quality of watermarked video is maintained as original one.
(3) In eq. 3 , L is the peak signal value of the watermark image which is equal to 255 for 8 bit images. [3] Ideally, PSNR value should be in between 40 to 60.Higher value of PSNR indicates that quality of watermarked video is maintained as original one.
IJSER © 2014
6
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014
ISSN 2229-5518
NC (Normalized correlation) is the similarity measurement of the extracted and referenced watermarks which is used for objective judgment of extraction fidelity [12].Ideally, Value of NC should be 1 which indicates exact similarity between ex- tracted and referenced watermark.
The purpose of this paper is to evaluate different techniques for video watermarking. Watermark in the video can be em- bed using spatial or frequency domain technique. Frequency- domain watermarking techniques are more efficient for im- perceptibility and robustness requirements but time consum- ing while Spatial-domain techniques are easy to implement and less time complex. Digital watermarking for real time ap- plication like video broadcasting and monitoring demands less time consuming techniques. So, Spatial Domain tech- niques are more useful for such application.
Firstly, I would like to thank Dr.Nehal Chitaliya from Sardar Vallabhbhai Patel Institute of Technology,vasad for her aspir- ing guidance,constructive criticism and valuable Suggestion for my ongoing research work ,as well as to publish this re- view paper.She kindly read this review paper and offered val- uable detailed suggestion on grammar, organization, and the theme of the paper.
Secondly, I would like to thank Dr.M.B.Potdar who allowed me to carry out the research work in Bhaskaracharya Institute For Space Applications and Geo-Informatics(BISAG), Ghandhinagar. I would also like to give my sincere gratitude to Dr.Manoj Padya and Mr. Parth Trivedi from BISAG for their exemplary guidance, valuable feedback , constant en- couragement and for sharing their truthful and illuminating views on a number of issues related to the research work.
Finally, I sincerely thank to my parents, family, and friends for their contionuous support. The product of this research paper would not be possible without all of them.
[1] G. V. A. I. Pitas, "“The use of watermarks in the protection of digital multime-
dia products" in Proceedings of the IEEE, vol. 87, no. 7, pp. 1197 - 1207, Jul
1999.
[2] Christoph Busch, Wolfgang Funk, "Digital Watermarking : From concepts to real-time video applications" in IEEE Computer Graphics and Applications, vol.19, Issue 1, pp. 25 - 35, Jan/Feb 1999.
[3] Zhu, Wenwu ; Zixiang Xiong ; Ya-Qin Zhang , "Multiresolution watermark- ing for images and video" in Circuits and Systems for Video Technology,
IEEE Transactions on , vol. 9 , no. 4, pp. 545- 550 , 1999.
[4] Lee, S.-H. J. Sin-Joo, "A survey of watermarking techniques applied to multi- media" in IEEE International Symposium on Industrial Electronics.(ISIE), vol.
1, pp. 272 - 277, 2001.
[5] Ingemar Cox,Matthew L. Miller,Jeffery A. Bloom, “Digital Watermarking”,
Morgan Kaufmann, 2001.
[6] Piva, A., Bartolini, F. and Barni, "A Hybrid Digital Video Watermarking
Scheme" in IEEE Transactions on Internet Computing, vol. 6, no. 3, pp. 18-26,
2002
[7] Gwenael, and J. L. Dugelay, "A guide tour of video watermarking" in Signal
Processing: Image Communication , Elsevier, vol. 18, pp. 263-282, 2003.
[8] Potdar, V.M. ; Song Han ; Chang, E., "A survey of digital image watermarking techniques " in 3rd IEEE International Conference on Industrial Informatics (INDIN’05), pp.709-716,2005.
[9] Evelyn Brannock, Michael Weeks, Robert Harrison, "Watermarking with wavelets: Simplicity leads to robustness"in IEEE Southeastc on, pp.587-592,3-6
April, 2008.
[10] Sadik. A.M .Al-Taweel , Putra, Sumari , Hailiza Kamarulhaili, "Digital Video Watermarking Based on 3D-Discrete Wavelet Transform Domain" in IEEE In- ternational Conference on Signal and Image Processing Applications, pp.352-
356, Malaysia, 2009
[11] S. Al-Taweel and P. Sumari, " Robust Video Watermarking Based On 3D- DWT" in TENCON, IEEE Region 10 Conference, pp.1-6, 2009.
[12] A. Zamanidoost, S. Mirzakuchaki, R. Atani, Z. Hesabi and M. Ayat, "A novel
3D wavelet-based method for blind digital video watermarking" in IEEE Symposium on Industrial Electronics & Applications (ISIEA), pp.186-189, Pe- nang, 2010
[13] Jiang Xuehua,"Digital Watermarking and Its Application in Image Copyright Protection‖" in IEEE International Conference on Intelligent Computation Technology and Automation (ICICTA), vol.2, pp.114-117, 2010.
[14] Rama kurupati ,Venkata Rama Prasad,Vaddella,Govardhan Pacha, "Im- proved Imperceptibility of watermarked Images using DWT & DCT Trans- form" in National Conference on Imaging,Computing,Object & Mining (ICOM'10), Tamil Nadu,India, May,2010.
[15] Kamble, S. ; Maheshkar, V. ; Agarwal, S. ; Srivastava, V.K., "DWT-based mul- tiple watermarking for privacy and security of digital images in e-commerce" in IEEE International Conference on Multimedia, Signal Processing and Communication Technologies (IMPACT), pp.224-227, 2011.
[16] Rini T Paul, "Review of Robust Video Watermarking Techniques" in IJCA Special Issue on Computational Science - New Dimensions & Perspectives, vol. 3, pp. 90-95, 2011.
[17] Satendra Kumar, Ashwini Kumar Saini and Papendra Kumar, "SVD based Robust Digital Image Watermarking using Discrete Wavelet Transform" in International Journal of Computer Applications, vol. 45, pp. 7-11, May 2012.
IJSER © 2014
7
International Journal of Scientific & Engineering Research, Volume 5, Issue 12, December-2014
ISSN 2229-5518
[18] Amit Joshi, Vivekanand Mishra and R. M. Patrikar, "Real Time Implementa- tion of Digital Watermarking Algorithm for Image and Video Application" in Watermarking, vol. 2, pp. 67-90, Dr. Mithun Das Gupta, Ed., Intech, 2012.
[19] Ensaf Hussein,Mohamed A. Belal, "Digital Watermarking Techniques, Appli- cations and Attacks Applied to Digital Media: A Survey"in International Journal of Engineering Research & Technology, vol.1,Issue 7, pp. 1-8, Septem- ber – 2012
[20] Tabassum, T. ; Islam, S.M.M., "A digital video watermarking technique based on identical frame extraction in 3-Level DWT" in 15th IEEE International Conference on Computer and Information Technology (ICCIT),pp.101-106,
2012.
[21] Manpreet kaur, Sonia Jindal, Sunny behal, "A Study of Digital image water- marking" in International Journal of Research in Engineering & Applied Sci- ences , Vol.2, Issue 2, pp.126-136, Feb 2012.
[22] Amit Kumar Singh, Nomit Sharma, Mayank Dave, Anand Mohan, "A Novel Technique for Digital Image Watermarking in Spatial Domain" in 2nd IEEE International Conference on Parallel, Distributed and Grid Computing, pp.
497-501, 2012.
[23] S. Moon, K. Yoon and H. Kim, "Identifying Manipulations with Dual Video Watermark" in IEEE 15th International Conference on Advanced Communi- cation Technology (ICACT), pp. 660-663, 2013.
[24] Gopika V. Mane, G. G. Chiddarwar, "An Imperceptible Video Watermarking Algorithm using Fusion of Wavelet Based Contourlet Transform & Sparse Non Negative Matrix Factorization" in IEEE International Conference on Computational Intelligence and Computing Research, pp.1-7, Enathi, 2013.
[25] Bajaj, "Review on Watermarking Techniques: A Unique Approach for Digital Image Protection" in International Journal of Advanced Research in Comput- er Science and Software Engineering, vol. 4, Issue 5, pp. 763-773, May 2014.
[26] W. contributors, "Signal-to-noise ratio (imaging)," Wikipedia, The Free Ency clopedia., [Online]. Available:http://en.wikipedia.org/w/index.php?title
=Signal-to-noise_ratio_(imaging)&oldid=615129307. [Accessed 20th August
2014].
[27] "Patchwork," [Online]. Available:
http://www.lia.deis.unibo.it/Courses/RetiDiCalcolatori/Progetti98/Fortini
/patchwork.html. [Accessed 20th October 2014].
[28] W. contributors, "Steganography," Wikipedia, The Free Encyclopedia, [Online]. Available: http://en.wikipedia.org/w/index.php?title= Steganog raphy&oldid=633683001. [Accessed 15th August 2014].
[29] Srinivasa Rao Chalamala, Krishna Rao , Kakkirala, Bala Mallikarjuna Rao G, "Analysis of Wavelet and Contourlet Transform Based Image Watermarking Technique" in IEEE International Advance Computing Conference (IACC), pp.1122- 1126, 2014.
[30] InTech — Open Access Company, 2004–2014 . [Online]. Available:
http://www.intechopen.com/about-intech.html. [Accessed 10th September
2014]
[31] Signal Processing and Computing Technologies, pp.140-144 , 2014. Anita Jadhav, Megha Kolhekar, "Digital Watermarking in Video for Copy Right Protection" in IEEE International Conference on Electronic Systems, Signal Processing and Computing Technologies, pp.140-144 , 2014.
IJSER © 2014