easy to analyze which makes it resistant to implementation errors [1391].
4. Variably Secure. Blowfish’s key length is variable and can be as long as 448 bits.
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013
ISSN 2229-5518
669
Design and Implementation of Hybrid Encryption Algorithm
Ali E. Taki El_Deen
IEEE Senior Member, Alexandria University, Egypt.
A_takieldeen@yahoo.com
Abstract – In today’s world 99% people are more interested in sending and receiving data through internet and mobile data storage devices. But among those people don’t encrypt their data though they know that data contains personal information and the chances of data lose or hacking is very high. Information security has always been important in all aspects of life. It can be all the more important as technology continues to control various operations in our day-to-day life. Cryptography provides a layer of security in cases, where the medium of transmission is susceptible to interception, by translating a message into a form that cannot be read by an unauthorized third party. The ultimate objective of the research presented in this paper is
to develop both AES and Blowfish to be low power, high-
Hybrid Encryption Algorithm requires fast processing techniques. Hybrid Encryption Algorithm is a high encryption security.
Blowfish has a 64-bit block size and a key length of anywhere from 32 bits to 448 bits (32-448 bits in steps of 8 bits; default 128 bits).
It is a 16-round Feistel cipher and uses large key- dependent S-boxes. It is similar in structure to CAST-128, which uses fixed S-boxes.
throughput, real-time, Ireliable Jand extremSely secure ER
cryptography algorithm and in addition to making estimation of both AES and Blowfish more difficult seems impossible.
Keywords: Blowfish, AES, DES, RSA
Hybrid Encryption Algorithm is a keyed, symmetric block cipher, designed in 2012. It is a combination of two known algorithms ( Blowfish & AES 128 ) .
Hybrid Encryption Algorithm takes the advantages of blowfish algorithm and Advanced- Encryption-Standard (AES) algorithm makes it harder for
any attacker to try to decrypt the cipher text.
There are two parts here:
A part that handles the expansion of the key.
A part that handles the encryption of the data. The expansion of the key:
Breaking the original key into a set of subkeys. Specifically, a key of no more than 448 bits is separated into 4168 bytes. There is a P-array and four 32-bit S- boxes. The P-array contains 18 32-bit subkeys, while each S-box contains 256 entries.
The encryption of data:
The encryption of the data: 64-bit input is denoted with an x, while the P-array is denoted with a Pi (where i is the iteration).
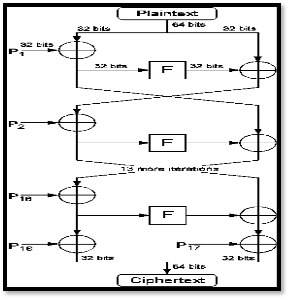
Figure1 shows the action of Blowfish. Each line represents 32 bits. The algorithm keeps two subkey arrays: the 18-entry P-array and four 256-entry S-boxes.
The S-boxes accept 8-bit input and produce 32- bit output. One entry of the P-array is used every round, and after the final round, each half of the data block is XORed with one of the two remaining unused P-entries.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013
ISSN 2229-5518

easy to analyze which makes it resistant to implementation errors [1391].
4. Variably Secure. Blowfish’s key length is variable and can be as long as 448 bits.
Fig. 1 Blowfish algorithm
Initialize the P-array and S-boxes.
XOR P-array with the key bits. For example, P1
XOR (first 32 bits of key), P2 XOR (second 32 bits of key). Use the above method to encrypt the all-zero string.
This new output is now P1 and P2.
670
Encrypt the new P1 and P2 with the modified subkeys.
This new output is now P3 and P4.
Repeat 521 times in order to calculate new
subkeys for the P-array and the four S boxes.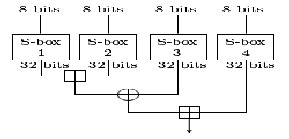
Fig. 2 Blowfish F function
1. Fast. Blowfish encrypts data on 32-bit microprocessors at a rate of 26 clock cycles per byte.
2. Compact. Blowfish can run in less than 5K of memory.
3. Simple. Blowfish uses only simple operations: addition, XORs, and table lookups on 32-bit operands. Its design is
Fig. 3 AES flowchart
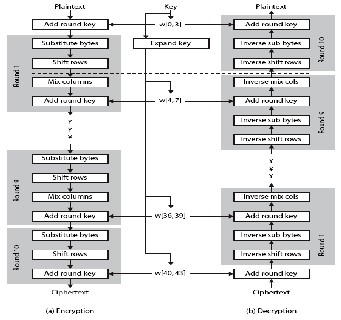
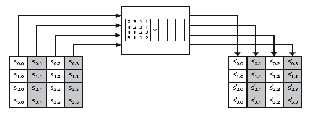
Figure 3 shows the structure of AES in more detail. The cipher consists of N rounds, where the number of rounds depends on the key length: 10 rounds for a 16- byte key; 12 rounds for a 24-byte key; and 14 rounds for a
32-byte key. The first N – 1 rounds consist of four distinct transformation functions: SubBytes, ShiftRows, MixColumns, and AddRoundKey, which are described subsequently. The final round contains only 3 transformations, and there is a initial single transformation (AddRoundKey) before the first round, which can be considered Round 0. Each transformation takes one or more 4 x 4 matrices as input and produces a
4 x 4 matrix as output. Figure 4 shows that the output of each round is a 4 x 4 matrix, with the output of the final round being the ciphertext. Also, the key expansion function generates N + 1 round keys, each of which is a distinct 4 x 4 matrix.
Each round key serves as one of the inputs to the
AddRoundKey transformation in each round.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013
ISSN 2229-5518
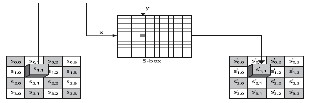
5. AES is strong enough to be certified for use by the US
government for top secret information.
671
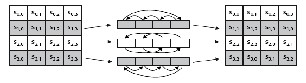
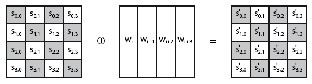
IJSERFig. 5 AES round
Fig. 4 The output of each round
1. Advanced Encryption Standard (AES) algorithm works on the principle of Substitution Permutation network.
2. AES has more elegant mathematical formulas behind it, and only requires one pass to encrypt data. AES was designed from the ground up to be fast, unbreakable and able to support the tiniest computing devices imaginable. The big differentiators between AES and Triple-DES are not strength of security, but superior performance and better use of resources.
3. Advanced Encryption Standard not only assures security but also improves the performance in a variety of settings such as smartcards, hardware implementations etc.
4. AES is federal information processing standard and there are currently no known non-brute-force direct attacks against AES.
Table 1: Comparison between AES, DES, RSA, Blowfish
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013
ISSN 2229-5518
672
Let s = s0; s1; s2; ….. ; sn−1 be a binary sequence of length n. This subsection presents four statistical tests that are commonly used for determining whether the binary sequence s possesses some specific characteristics that a truly random sequence would be likely to exhibit. It is emphasized that the outcome of each test is not definite, but rather probabilistic. If a sequence passes all four tests, there is no guarantee that it was indeed produced by a random bit generator [19]. These tests are:
Frequency test (Monobit test).
Serial test.
Poker test.
Run test.
For a significance level of α = 0.05, the threshold
values for freq., serial, poker, and run tests are 3.8415,
5.9915, 14.0671, and 9.4877 respectively [10]. Our tests results are given in figure 3.
Blowfish key: break the original key into a set of subkeys. Specifically, a key of no more than 448 bits is separated into 4168 bytes. There is a P-array and four 32- bit S-boxes. The P-array contains 18 32-bit subkeys, while each S-box contains 256 entries.
AES key: expansion of 128 bit only from the key whish will give 10 partial keys used in the initial round, 9 main rounds and one final round.
Make the encryption of 128 bit from plain text using blowfish by making encryption to the first 64 bit then to the second 64 bit.
Take the output of the encrypted 128 bit that comes from making blowfish twice and make this output the input plain text to AES algorithm.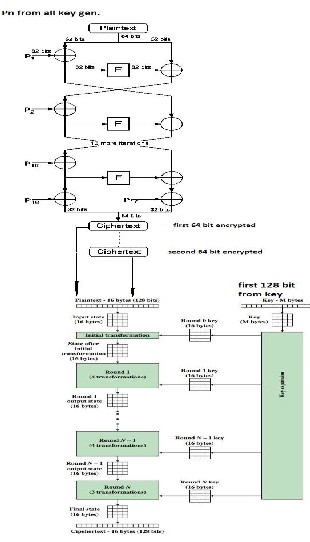
NOTE: The following is first idea but we still developing our algorithm.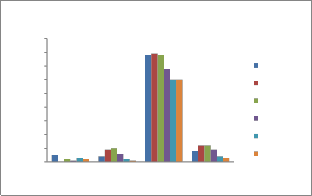
Statistical Tests
90
80
70
60
50
40
30
20
10
0
Frequency
Test
Serial Test Poker Test Run Test
128-Bit-AES
192-Bit-AES
256-Bit-AES RSA BlowFish DES
Fig. 6 Tests values
There are four parts to this algorithm:
1. Part that handles the expansion of the key used in blowfish.
2. Part that handles the expansion of the key used in AES.
3. Part that handles the encryption of the data using blowfish.
4. Part that handles the encryption of the encrypted data from blowfish using AES128.
Fig. 7 Hybrid Encryption Algorithm
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013
ISSN 2229-5518
673
1. Part that handles the expansion of the key used in blowfish.
2. Part that handles the expansion of the key used in AES.
3. Part that handles the decryption using AES128 to the encrypted data using blowfish.
4. Part that handles the decryption of the data using blowfish.
In decryption part one and part two are the same as there is no change in key generation for both blowfish and AES. For part 3 and 4 we will start with part 4 then part 3.
Figure 7 describes the main steps of Hybrid Encryption Algorithm encryption and how it start normally with the input key from user and make blowfish encryption two times to get 128 bit encrypted then we make AES encryption one time to the 128 bit output from the two times blowfish encryption. using only the first 128 bit from key as the key may get too long as we can use up to 448 bit or 576 bit key in
blowfish , then finally we get the 128 bit encrypted .
Institute of Standards and Technology, October 2, 2000.
IJSE[17] Wenbo RMao, Modern Cryptography: Theory and
In this paper, Hybrid Encryption Algorithm has been introduced. The proposed technique of Hybrid Encryption Algorithm combines between difficulty of estimation the original text and verity of using the different key on blowfish and AES encryption that we introduce cipher text more difficult for estimation so our algorithm is at high level of security and we need that to use it in specific applications like military applications, hardware and software companies that need security in their products, banks, networks companies, big websites that have big databases and mobile networks. Also a comparison between AES, DES, RSA, and Blowfish encryption algorithms are discussed. Statistical tests of AES, DES, RSA, and Blowfish algorithms have been examined.
2011.
Practice: By Hewlett-Packard Company, Publisher: Prentice Hall PTR, Pub Date: July 25, 2003, ISBN: 0-13-
066943-1.

Ali E. Taki El_Deen (IEEE Senior Member) received the PhD degree in Electronics and Communications Engineering in “Encryption and Data Security in Digital Communication Systems”. He has a lot of publications in
various international journalsand conferences. His current research interests are in multimedia processing, wireless communication systems, Microcontroller and Field Programmable Gate Array (FPGA) applications.
IJSER © 2013 http://www.ijser.org