International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1248
ISSN 2229-5518
DS-AKA: Dynamic and Secure Authentication
and Key Agreement Protocol for UMTS Networks
Mustafa A. AL-Fayoumi
Abstract—The authentication and key agreement (AKA) protocol of Universal Mobile Telecommunication System (UMTS) adopts the security features of Global System for Mobile (GSM) in order to interwork with GSM compatibility. Furthermore, the UMTS increases more security features than GSM to design an authentication and key agreement protocol, which is called UMTS AKA protocol. The UMTS AKA is still vulnerable to redirection and man-in-the-middle attacks, which allow an adversary to redirect user traffic form a network to another and eavesdrop or mischarge the subscribers in the system. Moreover, UMTS AKA protocol has performance problems, including bandwidth consumption between a serving network and user’s home network and space overhead of the serving network. In this paper, by using a key hash chaining authentication technique an innovative contribution introduces a dynamic and secure AKA protocol, called DS- AKA to resolve the security issue and cope with performance problems. A security analysis and comparison with related work shows that DS-AKA protocol is more secure and the network can be operated in a more efficient way.
Index Terms— Authentication Protocol, Key agreement protocol, Universal Mobile Telecommunications Systems (UMTS), Security, Mobile
Station, and Authentication Vector, W ireles communication.
—————————— ——————————
1 INTRODUCTION
ith the advancement of wireless communication and computer technologies, mobile communication pro-
UMTS architecture [6].
vides more versatile, portable and affordable networks than ever [1], [2]. Therefore, the number of users of mobile communication networks has increased rapidly. The conven- ience of communication not only brings a new set of technical problems, but also raises a new class of interesting applica- tions. This is due to the change in communication from single- medium oriented into multimedia communication such as image, computing data, internet services, e-commerce [3], and so on. At the same time, how to decrease the risk of masquer- ading legal users, and protect privacy on the radio channels are becoming a very important issues [4].
Since the transmission interfaces are over insecure communi- cation channels, security is one of the most important re- quirements for the exchange of user's or systems' private data. Therefore, precautionary security measures for mobile com- munication systems should be provided. As a solution to pre- vent the illegal access of frauds and eavesdroppers, authenti- cation and confidentiality are essential security services to subscribers and the service provider [5]. Take cellular mobile communication systems for example, entities of a cellular mo- bile communication system. There are three entities participat- ing in the UMTS security architecture. Firstly, a home envi- ronment (HE), with which the MS contracts. Secondly, a for- eign network, which is called serving network (SN). An MS can connect to an HN or an SN. Thirdly, a mobile station (MS), which is on behalf of a user. Figure 1 illustrates the
————————————————
• Mustafa A. Al-Fayoumi, Assistant Professor of computer science. Cur- rently he is the Dean Assistant for Quality and Development at College of Computer Engineering and Sciences in Prince Sattam bin Abdulaziz Uni- versity, Saudi Arabia, P.O. Box 151, Al-Kharj 11942, Saudi Arabia. E- mail: fayoumi66@yahoo.com
Fig. 1. Mobile network architecture
The GSM was introduced in 1990 by the European Tele- communication Standard Institute [7]. The GSM takes account of security issues and employs some security measures in de- signing the 2G to provide user authentication and data confi- dentiality [8]. Improved versions of the GSM protocol were subsequently proposed [9], [10], [11], [12]. However, the secu- rity features of the GSM are gradually insufficient for the cur- rent demands of the mobile system. A more powerful security mechanism is essential to address and improve current GSM security.
The UMTS AKA authentication protocol holds the frame- work of the GSM but provides new and significant enhance- ment features such as mutual authentication, agreement on an integrity key between the user (MS) and the serving network (SN), and assured freshness of agreed cipher key and integrity key. In the UMTS authentication protocol, according to the properties of the Message Authentication Code (MAC), the mobile station and the Home Location Register and Authenti-
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1249
ISSN 2229-5518
cation Centre (HLR/AuC) in the home network can perform mutual authentication by sharing the same secret key in ad- vance.
The UMTS AKA protocol is still vulnerable to security at- tack, such as redirection attack and man-in-the-middle (MITM) attacks. The redirection attack allows an adversary to redirect user traffic to an unwanted serving network and im- personating uncorrupted networks using authentication vec- tors from corrupted networks since the authentication vectors could be used by any serving network.. In this case, a false base station impersonates a serving network and then redirect user traffic from one SN to a SN of their choosing with lower security. UMTS AKA procedure will normally succeed and neither the home network nor the victim user can detect this attack.
Since the user will not notice being connected to another network and could cause billing problem to get unusually high bills as the service rates offered by different networks are not always the same. Additionally it might be used to redirect traffic to networks with lower security, causing an incorrect impression of the security level to be applied [13].
The MITM attack can occur when an adversary eavesdrops the data communication prior transmission at the session ini- tiated by a valid MS. This attack occurs while a valid MS con- necting to a GSM BSS. In this case, the adversary can inter- cept and inject some data. In UMTS, an adversary hides him- self between the MS and Visit Location Register/Serving GPRS Support Node (VLR/SGSN) and tries to bypass the UMTS security and forces the victim MS to use the less secure GSM authentication and the obtains AUTN.
However, the UMTS AKA protocol has some shortcomings in the performance and complexity of operations. Firstly, the bandwidth consumption between visitor serving network and home network is inadequate when MS requests to authenti- cate itself for the VLR/SGSN in serving network (SN) and no authentication vectors are available the VLR/SGSN must turn back to HLR in the Home Network (HN) to make a registra- tion request to generate another array of n authentication vec- tors. Moreover, when the subscriber roams to a newly visited VLR/SGSN within a different serving network domain the authentication vectors in the old VLR/SGSN are deleted, which is called an unused authentication vectors problem. Subsequently, as a lot of data being sent between VLR/SN and HLR/HN, this has impact on the performance of AKA protocol.
Secondly, as the generation of authentication vectors (AV) is expensive and which require the generation of five records in each AV will increase the delay time in home network.
Thirdly, the storage space overhead occurs if there are 𝑚 sub- scribers, and an array of n authentication vectors for each sub- scriber in SN, then the SN must wastefully store 𝑛 × 𝑚 authen-
tication vectors. Fourthly, the management of sequence num-
ber (SEQ) which is needed for synchronization between mo-
bile station and its home network, and the periodical authenti-
cation is achieved by comparing a SEQ counter value between an MS and a VLR/SGSN periodically. The SEQ is susceptible to synchronization failure. Therefore, both MS and HN are needed to maintain SEQ to accomplish that process between
them [13].
To alleviate the weaknesses of the existing UMTS AKA pro- tocol, this paper proposes a dynamic and secure authentica- tion and key agreement protocol for UMTS. Therefore, the aims of the enhancement protocol are listed as follows.
1. To achieve bilateral authentication between MS and
HLR in the home network.
2. To achieve bilateral authentication between MS and
VLR in the serving network.
3. To reduce the stored space in VLR in the serving net-
work.
4. To reduce the bandwidth consumption by reducing
the authentication transmission overhead between
VLR/SN and HLR/HN.
5. To provide stronger key agreement to protect the
communication between the MS and the VLR/SGSN.
6. To defeat redirection and man-in-the-middle attacks
and partially prevent DoS attacks
The remaining part of this paper is organized as follows.
Section 2 , gives the literature review and related work. Sec- tion 3 describes detailed UMTS AKA protocol. The proposed protocol DS-AKA is presented in section 4. In Section 5, the security analysis for the proposed protocol is presented. The
comparison with related work is presented in section 6. The paper is concluded in Section 7.
2 RELATED WORK
Several authentication schemes have been proposed for mobile networks to enhance the security of mobile communication sys- tems based on several authentication techniques. These tech- niques only provide some security features and have some weaknesses. Most of these schemes are based on the use of symmetric key cryptosystems and a challenge-response ex- change. In this context, Many symmetric key based AKA proto- cols were proposed for UMTS network to improve the security of UMTS AKA and effective utilization of bandwidth during the authentication.
In 2005, Zhang and Fang [14] proposed a new authentica- tion and key agreement protocol, which overcomes redirection attack and drastically lowers the impact of network corrup- tion. The protocol is called adaptive protocol AKA (AP-AKA). They solve these problems by eliminating the need for syn- chronization between a mobile station and its home network and providing a way for the MS to verify if AV's are indeed coming from SN and have not been used before (i.e., The MS can verify for itself if an AV used by the VLR is a fresh one). This is achieved by sending additional identity information from the user and the serving network along with the authen- tication data. So if an attacker redirects messages of the MS the
wrong 𝐼𝐼𝑆𝑁 will be used and the 𝐼𝐼𝑆𝑁 sent by the MS will not match the 𝐼𝐼𝑆𝑁 sent by the VLR. However, AP-AKA protocol
is still vulnerable to the middle-in-the- attack.
However, both UMTS-AKA and AP-AKA protocols have
the problem of the bandwidth consumption between SN and
HN. It is attractive to choose a suitable length (L) value for AV
in the third generation mobile networks. So, many techniques
are developed to minimize the authentication signalling cost
and network bandwidth with consumption by selecting the
dynamic length (L) for an authentication vector. Yet with this
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1250
ISSN 2229-5518
improvement, Lin and Chen [15] and AL-Saraireh and Yousef [16] are still there are bandwidth consumption. Unfortunately, the performance drawbacks still strike as follows. First, the space overhead strikes when n AVs in the SN are being stored. Second, there is bandwidth consumption between SN and HN since HN needs to pass n AVs to SN. The two problems can be solved by several techniques.
Harn and Hsin [17] proposed an enhanced registration and AKA scheme for UMTS. By introducing a combination of hash-chaining and keyed HMAC techniques, in their pro- posed protocol they claim it can provide strong periodically mutual authentication, strong key agreement, and a non- repudiation service in a simple and elegant way. However, due to the underlying hash chaining technique [18], the securi- ty was enhanced while more computation overhead of hash chaining was incurred at MS and SN in each session. This could have a negative impact on the performance of this pro- tocol. However, this protocol also does not clear the security issues against various attacks.
X-AKA protocol [19] was proposed an extension of the
UMTS-AKA protocol to prune off the transmission of authen-
tication vectors (AV) and improves its bandwidth utilization.
In X-AKA, SN must continually generate random numbers to
challenge MS to reply corresponding responses for every au-
thentication. It is noticeable, random challenge generation
overhead occurs in SN.
Both Harn-Hsin’s and Huang-Li’s protocols, the security
for MS to identify the active SN is not mentioned so that an
adversary can redirect the user traffic from the active SN to
another SN. The redirection and man-in-the-middle attacks
are not prevent in the two protocols.
Al-Saraireh and Yousef’s protocol [20] primary emphasis
on reducing the bandwidth for transmitted authentication
vectors during authentication and therefore, the AVs are only
generated by the MS instead of by the VLR. Al-Saraireh and
Yousef’s protocol eliminates the cost of delivering AVs . the
protocol does not clear the security issues with redirection as
well as man-in-the-middle attacks.
Ou, Hwang, and Jan [21] proposed a new protocol COCK-
TAIL-AKA, to overcome the congenital defects of UMTS AKA
protocol. In this protocol, each service network produces its
own AVs (MAVs) in advance. These MAVs are produced only
once but can be reused later. While authenticating the MS, the HLR/AuC calculates a private authentication vector (PAV) for MS. The PAV is transferred to the SGSN. Then, the SGSN uses the PAV and MAV to generate several effective AVs for sub-
sequent authentications. Cocktail-AKA is penetrable to DoS attack and impersonation attack [22]. It also does not solve the synchronization problem between MS and HLR.
Huang and et al [23] proposed a new protocol namely S- AKA, to defeat the redirection, man-in-the-middle and denial of service attacks. However, the S-AKA reduces bandwidth consumption up to 38% and also decreases the number of messages required in authenticating mobile subscribers. In S- AKA, SN must continually generate random numbers to chal- lenge MS to reply corresponding responses for every authenti- cation. It is noticeable, random challenge generation overhead occurs in SN. The NS-AKA protocol in [24] reduces the over- heads, and is free from redirection and MITM attacks, but
does not provide resistance against denial of service attack.
3 DESCRIPTION OF UMTS AKA PROTOCOL
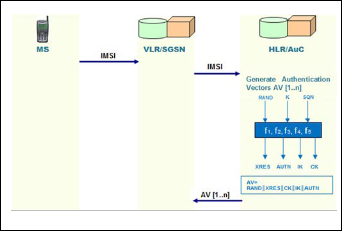
The UMTS AKA protocol is performed in two procedures, as shown in figure 2 and 3 respectively. Firstly, Registration and Distribution Vectors which is called Authentication vectors from the home network (HN) to the serving network (SN): the MS reg- isters with its HLR/AuC in the HN and then generate and dis- tributes authentication vectors from the HLR/AuC to the VLR/SGSN in the SN. Secondly, Authentication and Key Agreement procedure runs between MS and VLR/SGSN. When the protocol is executed in the home network or when the serving network has unused authentication vectors for the user, the first phase is not executed.
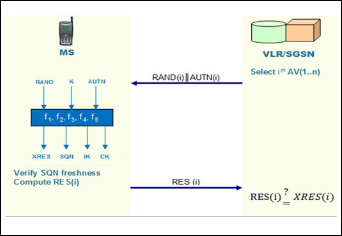
Fig. 2. UMTS AKA Phase1 – Distribution of Authentication Vectors
Fig. 3. UMTS AKA Phase1 – Distribution of Authentication Vectors
3.1 Distribution of Authentication Vectors
1. The MS sends a registration request to visitor location register/serving GPRS support node VLR/SGSN in the SN. The registration request includes an MS’s IMSI.
2. Upon receiving the registration request, the VLR/SGSN in the SN passes the registration authenti- cation request that is generated in step 1 to MS’s HLR in the HN.
3. Upon receipt of a request from the VLR/SGSN, the
HLR/AuC in the HN generates an ordered array of n
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1251
ISSN 2229-5518
authentication vectors 𝐴𝐴(1 ⋯ 𝑛) whose order is based on 𝑆𝑆𝑆𝐻𝑁 . It sends an authentication data response as an ordered array of 𝑛 authentication vectors to the VLR/SGSN in the SN via a secure channel. The 𝐴𝐴𝑆 is generated by using the secret key 𝐾𝑖 which is pre-
shared with the subscriber. Each AV consists of
𝑅𝐴𝑆𝐼, 𝑋𝑅𝑋𝑆 (Expected Response), 𝐶𝐶 (Cipher Key), 𝐼𝐾
(Integrity Key) and AUTN (Authentication Token).
4. Upon receipt of 𝐴𝐴𝑆 , the VLR/SGSN in the SN stores
AND SECURE AUTHENTICATION AND KEY
AGREEMENT PROTOCOL (DS-AKA)
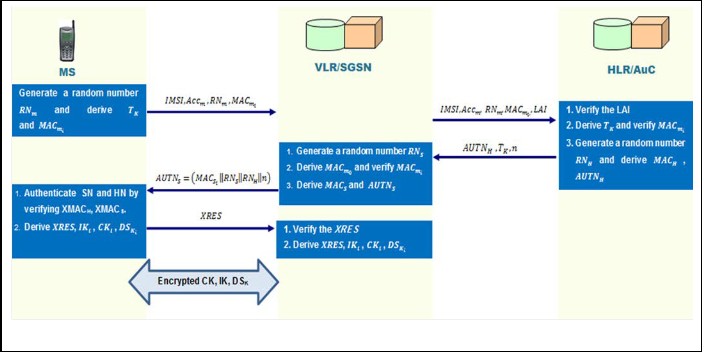
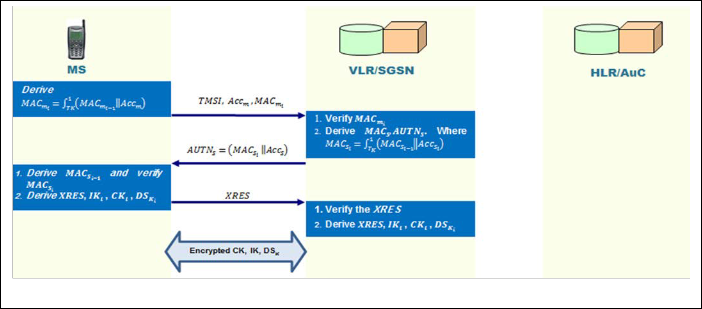
The proposed authentication protocol is divided into two proce- dures; the first one is called the initial authentication procedure, which flow from MSVLRHLR. The second one is limited between MSVLR and is called the subsequent authentication procedure, as shown in Fingers 4 and 5, respectively.
4.1 First Procedure: DS-AKA-I
the authentication vectors for performing the subse-
Step 1: M1
𝑚 𝑚 𝑚
I : �𝐼𝐴𝑆𝐼, 𝐴𝐴𝐴
⊕ 𝐴𝐾, 𝑅𝑆
, 𝐴𝐴𝐶
�, MS sending a
quent authentication and key agreement procedure.
Each 𝐴𝐴 is used for one authentication and key agree-
ment between the VLR/SGSN in the SN and the MS.
3.2 Authentication and Key Agreement
1. In the 𝑖𝑡ℎ performance of the second procedure,
VLR/SGSN in the SN initiates an authentication and
key agreement to authenticate the MS, the VLR/SGSN
selects the next authentication vector from the ordered
array. It selects the 𝑖𝑡ℎ 𝐴𝐴 to run this procedure on a
first-in/first-out (FIFO) basis. SN sends the parameters
RANDi and AUTHi to the mobile station (MS). Therefore,
one authentication vector is needed for each authenti-
cation instance. This means that the signaling between
the VLR and AuC is not needed for every authentica-
tion event.
2. Upon receipt of 𝑅𝐴𝑆𝐼𝑖 and 𝐴𝐴𝐴𝐴𝑖 where (𝐴𝐴𝐴𝑆 =
𝑆𝑆𝑆 ⊕ 𝐴𝐾‖𝐴𝐴𝐴‖𝐴𝐴𝐶), the MS performs six steps.
• Computes the anonymity key 𝐴𝐾 = ∫5(𝑅𝐴𝑆𝐼).
• Retrieves the sequence number 𝑆𝑆𝑆 = (𝑆𝑆𝑆 ⊕
𝑖
registration request to VLR/SN
When an MS needs to authenticate itself to all entities of network
to access or utilize network services, the MS invokes the distribu-
tion of authentication procedure by sending the authentication
request messages to the HLR/AuC through VLR in the serving
network. In 𝐴𝐼 , MS’s IMSI represents the identity of a subscriber,
LAI represents the identifier of the location area of the BSS, and it
indicates the physical connection between the MS and BSS and
𝐴𝐴𝐴𝑚 represents the number of successful MS authentication and
is used to guarantee the freshness of authentication request. 𝐴𝐴𝐴𝑚
, which is initially set to 0, increase on each successful authentica-
tion. Furthermore, in order to accomplish the authentication re-
quest message the MS will do the following processes:
1. Generate a random number 𝑅𝑆𝑚 .
𝑥
2. Compute the temporary key 𝐴𝐾 = ∫𝐾 (𝑅𝑆𝑚 ‖𝐿𝐴𝐼)
3. AK represents the anonymity key to provide user iden-
5
tity confidentiality and computed as ∫ 𝑚 .
𝐾
4. MAC is the message authentication code for the MS
and computed as: 𝐴𝐴𝐶𝑚𝑖 = ∫𝑇 (𝐴𝐴𝐴𝑚 ‖𝐿𝐴𝐼).
I : �𝐼𝐴𝑆𝐼, 𝐴𝐴𝐴
⊕ 𝐴𝐾, 𝑅𝑆
, 𝐴𝐴𝐶
, 𝐿𝐴𝐼�, SN passing
𝐴𝐾) ⊕ 𝐴𝐾.
Step 2: M2
𝑚 𝑚
𝑚𝑖
• Computes expected message authentication code
1
the authentication Request Message to MS’s HN.
𝑋𝐴𝐴𝐶 = ∫𝐾 (𝑆𝑆𝑆, 𝑅𝐴𝑆𝐼, 𝐴𝐴𝐴)
and compares this
When the VLR/SN receives the message from the MS, the
with MAC which is included in AUTN.
• If they are different, the MS sends the user authen-
tication rejection back to the VLR/SGSN with an
indication of the cause and the user abandons the
procedure
• Otherwise, the MS confirms whether the freshness
that the received sequence number 𝑆𝑆𝑆 is in the
VLR/SN is able to recognize the HLR/HN to which MS belongs
by reading the IMSI; and then it passes the 𝐴𝐼 to the intended
HLR/HN together with BSS’s LAI. The VLR/SN maintains a
profile for that MS under the identity of user (IMSI) which con-
tains the privileges of a registered user for subsequent authentica-
tion. So, The VLR/SN waits to receive the authentication result
from HLR/HN.
correct range (i.e., 𝑆𝑆𝑆𝐻𝑁 > 𝑆𝑆𝑆𝑀𝑆 ) or not. If the re-
Step 3: M3
𝐻 𝐾
sult is negative, the MS sends synchronization fail- ure back to the VLR/SGSN including an appropri- ate parameter, and abandons the procedure.
• Otherwise, the MS computes 𝑅𝑋𝑆 = ∫2(𝑅𝐴𝑆𝐼) and
sends it back to VLR/SGSN in the SN. Meanwhile
MS computes the cipher key 𝐶𝐾 = ∫𝐾 (𝑅𝐴𝑆𝐼) and the integrity key 𝐼𝐾 = ∫𝐾 (𝑅𝐴𝑆𝐼).
3. The VLR/SGSN makes verification by comparing the
I : {𝐴𝐴𝐴𝑆 , 𝐴 , 𝑛}, Verifying the MS and sending au-
thentication token and temporary key to SN.
Upon receipt of the 𝐴𝐼 , the HLR/AuC in the home network veri-
fy the MS according to the information that have been received,
and then builds the Authentication Data Response message for
MS and VLR/SN. In order to accomplish the authentication pro-
cess, HLR/AuC will do the following:
1. Compute the temporary key 𝐴𝐾 = ∫K (RNm‖LAI)
2. Computes the anonymity key 𝐴𝐾 = ∫𝑇 (𝑅𝑆𝑚 ).
received RES with 𝑋𝑅𝑋𝑆. If they match, the mutual au-
3. Retrieves the 𝐴𝐴𝐴𝑚
= (𝐴𝐴𝐴𝑚
⊕ 𝐴𝐾) ⊕ 𝐴𝐾
thentication and key agreement between the MS and
4. Computes expected message authentication code
1
the VLR/SGSN is completed successfully. The estab-
𝑋𝐴𝐴𝐶𝑚𝑖 = ∫𝑇 (𝐴𝐴𝐴𝑚 ‖𝐿𝐴𝐼)
and compares this with
lished keys 𝐶𝐾 and 𝐼𝐾 are stored in the VLR/SGSN
𝐴𝐴𝐶
whic is included in 𝐴𝐼 . By checking 𝐴𝐴𝐶 ,
𝑚 𝑖 h 2
𝑚𝑖
and will then be transferred to the RNC when needed.
4. If a VLR/SGSN runs out of 𝐴𝐴𝑆 , it can request another ordered array of 𝐴𝐴𝑆 from the HLR/AuC.
4 DESCRIPTION OF PROPOSED PROTOCOL: DYNAMIC
the HLR/AuC can verify whether the LAI reported by the VLR/SGSN is the same as that recognized by the MS. If they are different, the HLR/AuC rejects the re- quest with an indication of the cause and the user abandons the procedure.
5. Otherwise, the HLR/AuC confirms whether the fresh-
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1252
ISSN 2229-5518
ness that the received 𝐴𝐴𝐴𝑚 is in the correct range (i.e.,
𝐴𝐴𝐴𝐻 > 𝐴𝐴𝐴𝑚 ) or not. If the result is positive, the
HLR/AuC considers it a replay and abandons the pro-
cedure.
6. Otherwise, HLR/AuC generates a random number
𝑅𝑆𝐻 and derive a message authentication code by hash-
on UMTS network due to its interoperability with GSM network. The security weaknesses of GSM expose the en- tire mobile system to this attack. To prevent the man-in- the-middle attack, the DS -AKA protocol employs an ex-
tra key 𝐼𝑆𝐾 when the GSM BSS involved in a conversa- tion. Both the MS and the VLR/SGSN compute 𝐼𝑆𝐾𝑖 =
6 6
ing 𝑅𝑆𝐻 and 𝐴𝐴𝐴 (authentication management field)
∫𝑇 �𝐼𝑆𝐾𝑖−1 ‖𝐴𝐴𝐴𝑆 �, where 𝐼𝑆𝐾0 = ∫𝑇 (𝑅𝑆𝑆 ‖𝐴𝐴𝐴𝑆 ) and can
1 𝐾 𝐾
as: 𝐴𝐴𝐶𝐻 = ∫𝐾 (𝑅𝑆𝐻 ‖𝐴𝐴𝐴). After that, the HLR/HN
concatenates the aforementioned token to derive
𝐴𝐴𝐴𝑆𝐻 = (𝐴𝐴𝐶𝐻 ‖𝑅𝑆𝐻 ‖𝐴𝐴𝐴) and send it to VLR/SN together with 𝐴𝐾 and n via secure channel, where n is the life time of the 𝐴𝐾 .
Step 4: MI : {𝐴𝐴𝐴𝑆 }, generating challenge information for MS
When the VLR/SN receives the response message from
HLR/HN, it means that the MS has proved itself to its HN suc-
cessfully. Therefore, the VLR/SN stores the authentication vector
for performing the subsequent authentication. In order for the MS
use 𝐼𝑆𝐾 key to protect the confidentiality of the data pass-
ing through the GSM BSS and prevents the communica-
tion from being eavesdropped.
4.2 Second Procedure: DS-AKA-II
After the initial authentication, both MS and VLR/SN possess
authentication information and the temporary key 𝐴𝐾 that it share
with each other and subsequently can accomplish the mutual
authentication by itself without intervention of HLR/AuC. That
is, subsequent authentication only happens between the MS and
𝑡ℎ
to verify the authenticity of the SN in the subsequent authentica-
the SGSN/VLR using three message exchanges. In the 𝑖
per-
tion AKA procedure, the SN generates response information for the MS and sends them to MS. The VLR/SGSN performs the
forming the second procedure, the authentication is described as
follows:
II: �𝐴𝐴𝑆𝐼, 𝐴𝐴𝐶
, 𝐴𝐴𝐴𝑚 ⊕ 𝐴𝐾}
following steps:
Step 6: M1
𝑚𝑖
1. The VLR/SGSN increments its 𝐴𝐴𝐴𝑆 by 1 and generates
a random number 𝑅𝑆𝑆 .
MS increments its 𝐴𝐴𝐴𝑚 by 1
1. Compute reclusively a hash chaining authenticators
1
5 𝐴𝐴𝐶𝑚𝑖 = ∫ �𝐴𝐴𝐶𝑚𝑖−1 ‖𝐴𝐴𝐴𝑚 �, where 𝐴𝐴𝐶𝑚𝑖−1
has been
2. Computes the anonymity key 𝐴𝐾 = ∫ (𝑅𝑆𝑆 ).
𝐾
3. Compute reclusively a hash chaining authenticators
𝐴𝐴𝐶 = ∫1 �𝐴𝐴𝐶 ‖𝐴𝐴𝐴 �, where 𝐴𝐴𝐶 =
∫𝑇𝐾(𝐴𝐴𝐶𝐻 ‖𝑅𝑆𝑆 ‖𝑅𝑆𝐻 ‖𝑛).
4. Construct 𝐴𝐴𝐴𝑆𝑆 = �𝐴𝐴𝐶𝑆𝑖 ‖𝑅𝑆𝑆 ‖𝑅𝑆𝐻 ‖𝐴𝐴𝐴‖𝐴𝐴𝐴𝑆 ⊕
𝐴𝐾‖𝑛� and sent it to MS.
I
𝑇𝐾
computed in step 1 of the first procedure.
2. Construct 𝐴𝐼𝐼 : �𝐴𝐴𝑆𝐼, 𝐴𝐴𝐶 , 𝐴𝐴𝐴 ⊕ 𝐴𝐾} and send it
to VLR/SGSN.
Step 7: MII: {𝐴𝐴𝐴𝑆 }
1. VLR/SGSN retrieves the 𝐴𝐴𝐴𝑚 = (𝐴𝐴𝐴𝑚 ⊕ 𝐴𝐾) ⊕ 𝐴𝐾
and increments its 𝐴𝐴𝐴𝑆 by 1 and compares it with the
Step 5: M5: {𝑋𝑅𝑋𝑆}, SN authenticating the MS.
Upon receipt of 𝐴𝐴𝐴𝑆𝑆 from VLR/SGSN, the MS authenticates
𝐴𝐴𝐴𝑚
to check if it is a replay.
VLR/SGSN, HLR/AuC by deriving and verifying 𝐴𝐴𝐶𝑆 and
𝐴𝐴𝐶𝐻 . The deriving and verifying steps are as follows:
2. On behalf of the HLR/AuC, the VLR/SGSN verify
whether the equation the recursive hash chaining au-
1
thenticators 𝑋𝐴𝐴𝐶𝑚𝑖 = ∫𝑇𝐾 �𝐴𝐴𝐶𝑚𝑖−1
‖𝐴𝐴𝐴𝑚 �
is hold,
VLR/SGSN updates 𝐴𝐴𝐶𝑚𝑖 and store it for the next
1 visit to generate the 𝐴𝐴𝐶𝑚𝑖+1 .
𝑋𝐴𝐴𝐶𝐻 = ∫𝐾 (𝑅𝑆𝐻 ‖𝐴𝐴𝐴), where 𝑅𝑆𝐻 and 𝐴𝐴𝐴 are
retrieve from 𝐴𝐴𝐴𝑆𝑆 in step 4.
3. If the XMACmi
is legitimate, the VLR/SGSN computes a
3. Compute the hash chaining authenticators 𝑋𝐴𝐴𝐶𝑆𝑖 =
∫𝑇𝐾�𝐴𝐴𝐶𝑆𝑖−1 ‖𝐴𝐴𝐴𝑆 �, where
new sequence of hash chaining authenticator 𝐴𝐴𝐶𝑆𝑖 =
∫𝑇 �𝐴𝐴𝐶𝑆𝑖−1 �𝐴𝐴𝐴𝑆𝑖 �, where 𝑖 ≤ 𝑛 and 𝐴𝐴𝐶𝑆𝑖−1 computed
in the previous visit.
𝐴𝐴𝐶𝑆𝑖−1 = ∫𝑇𝐾(𝐴𝐴𝐶𝐻 ‖𝑅𝑆𝑆 ‖𝑅𝑆𝐻 ‖𝑛).
4. MS sets the new 𝐴𝐴𝐴𝑠 to its 𝐴𝐴𝐴𝑚 .
5. Compute an expected response message as: 𝑋𝑅𝑋𝑆 =
2
∫ 𝑆 𝑆 for mutual authentication and sent
𝐾
4. Construct 𝐴𝐴𝐴𝑆𝑆
MS.
Step 8: MII: {𝑋𝑅𝑋𝑆}
= �𝐴𝐴𝐶𝑆𝑖
‖𝐴𝐴𝐴𝑆
⊕ 𝐴𝐾� and sent it to
𝑋𝑅𝑋𝑆 to VLR/SGSN. Meanwhile the MS Computes
1. MS retrieves the 𝐴𝐴𝐴𝑆 = (𝐴𝐴𝐴𝑆 ⊕ 𝐴𝐾) ⊕ 𝐴𝐾
𝐼𝐾 = ∫3 (𝐼𝐾 ‖𝐴𝐴𝐴 )
and 𝐶𝐾𝑖 = ∫𝑇 (𝐶𝐾𝑖−1 ‖𝐴𝐴𝐴𝑆 )
2. MS authenticate VLR/SGSN by verifying 𝑋𝐴𝐴𝐶𝑆𝑖 =
𝐾 3
𝐾 4 1
where 𝐼𝐾0 = ∫ (𝑅𝑆𝑆 ‖𝐴𝐴𝐴𝑆 )
𝐾
and 𝐶𝐾0 = ∫ (𝑅𝑆𝑆 ‖𝐴𝐴𝐴𝑆 )
𝐾
∫𝑇𝐾 �𝐴𝐴𝐶𝑆𝑖−1 �𝐴𝐴𝐴𝑆𝑖 �. 2
respectively.
3. MS computes 𝑋𝑅𝑋𝑆 = ∫𝑇 �𝐴𝐴𝐶𝑆𝑖−1 ‖𝐴𝐴𝐴𝑆 � and send it to
6. Upon receipt of 𝑋𝑅𝑋𝑆, VLR/SGSN authenticates the
MS by verifying the 𝑋𝑅𝑋𝑆 ? = 𝑅𝑋𝑆 = ∫ (𝐴𝐴𝐶𝑖−1 ‖𝐴𝐴𝐴𝑚 )
𝐾
. If the MS is successfully authenticated, then the
VLR/SGSN computes 𝐼𝐾𝑖 and 𝐶𝐾𝑖 to protect the
communication between the MS and the VLR/SGSN
subsequently.
7. As aforementioned, the man-in-the-middle attack occurs
VLR/SGSN.
4. On receiving, the VLR/SGSN authenticates the MS by
verifying the freshness and correctness of 𝑋𝑅𝑋𝑆. Now, both the MS and VLR/SGSN can use 𝐼𝐾, 𝐶𝐾 and 𝐼𝑆𝐾
keys for the purpose of confidentiality, integrity and
encryption.
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1253
ISSN 2229-5518
Fig. 4. DS-AKA Phase I – Initial Authentication Procedure
Fig. 5. DS-AKA Phase II – Subsequent authentication procedure
5 SECURITY ANALYSIS FOR PROPOSED PROTOCOL
The proposed DS-AKA protocol adopts the framework of UMTS AKA, and thus it also inherits the security issues of UMTS AKA such as entity authentication between an MS and an VLR/SGN, data integrity and user traffic confidentiality. Furthermore, the transmitting channel between VLR/SGSN and HLR/Auc is as- sumed to be secure. The adopting the same architecture of UMTS helps DS-AKA resist various network attacks.
The proposed DS-AKA protocol has been developed with the aim of keeping the complexity of this function as low as possible, and providing a high level of security and efficiency for the bandwidth used. A detailed analysis has been made of how the proposed scheme meets the security requirements and how ex- amine additional security issues in the proposed DS-AKA proto- col. Furthermore, explain how DS-AKA deters intruders from redirection, man-in-the-middle and DoS attacks.
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1254
ISSN 2229-5518
5.1 Mutual Authentication
• Mutual authentication between MS and its HN: The UMTS AKA provides procedure for mutual authentication of the MS and serving system. It is clear in the UMTS AKA pro- tocol, HLR/AuC in HN has no mechanism to authenticate MS. In contrast, the DS-AKA protocol, HLR/AuC authenti- cate MS. In step 3 of the DS-AKA protocol, the HLR/AuC au- thenticates and confirm the identity of the MS by verifying
𝐴𝐴𝐴𝑚 and the Ms’ message authentication code 𝐴𝐴𝐶𝑚𝑖 on re- ceipt 𝐴𝐼 . Note that the 𝐴𝐴𝐴 is used to guarantee the freshness of the authentication request and 𝐴𝐴𝐶𝑚𝑖 is used to protect the integrity of 𝐴𝐴𝐴𝑚 and 𝐿𝐴𝐼. Therefore, the verifying the 𝐴𝐴𝐶𝑚𝑖
can resist the replay and redirection attacks.
In step 5 of the DS-AKA protocol, the MS authenticates
VLR/SGSN, HLR/AuC by deriving and verifying 𝐴𝐴𝐶𝑆 and
𝐴𝐴𝐶𝐻 . The MS checks 𝐴𝐴𝐴𝑆𝑠 that received in 𝐴𝐼 which is
5.2 Temporary Key
The DS-AKA protocol employs a key authentication as a tem- porary key, which is generated during the execution of the registration process and caches in the MS and VLR/SGSN in the serving network for the subsequent authentication process (intra-network). The new mechanism significantly reduces the communication overhead between home and serving net- works for roaming authentication.
The DS-AKA protocol allows the VLR/SGSN to perform most of the authentication and agreement procedure. The temporary key is generated during registration and both the HN and MS can compute this key. The temporary key can then be used by the SN as A-Key, effectively reducing the need for subsequent communications with the HN. In addi- tion the SN will not have to store a number of AV’s, because it can calculate them when needed. Therefore, the proposed pro-
𝑥
contained 𝐴𝐴𝐶𝑆𝑖 , 𝑅𝑆𝑆 , 𝑅𝑆𝐻 , 𝐴𝐴𝐴, 𝐴𝐴𝐴𝑆 , 𝑛. The MS can com-
tocol uses another key generation function 𝑓
, which gener-
pute expected authentication code of HLR/AuC as 𝑋𝐴𝐴𝐶𝐻 =
∫𝐾 (𝑅𝑆𝐻 ‖𝐴𝐴𝐴), and then compute expected authentication
code of VLR/SGSN as 𝑋𝐴𝐴𝐶𝑆𝑖 = ∫𝑇𝐾�𝐴𝐴𝐶𝑆𝑖−1 ‖𝐴𝐴𝐴𝑆 �, where
𝐴𝐴𝐶 = ∫1 (𝐴𝐴𝐶 ‖𝑅𝑆 ‖𝑅𝑆 ‖𝑛). If the 𝑋𝐴𝐴𝐶 is equal to
𝐴𝐴𝐶𝑆𝑖 , it means that VLR/SGSN and HLR/AuC are authenti-
cated successfully.
Therefore, the MS confirms the authenticity of the
VLR/SGSN and HLR/AuC together. After the initial authen-
tication during the origination and termination call, the
VLR/SGSN gets a secret temporary key 𝐴𝐾 that it shares with
the MS and subsequently can accomplish the mutual authenti-
cation by itself even when the HLR/AuC is not involved, the
MS can recursively calculate the hash chaining authenticator
𝐴𝐴𝐶 = ∫1 (𝐴𝐴𝐶 ‖𝑅𝑆 ‖𝑅𝑆 ‖𝑛). Therefore, the MS is still authenticate the HLR/AuC with MII in the subsequent authen-
tication procedure.
ates a 128-bit or higher hash result, to get a better security lev-
el.
The temporary key 𝐴𝐾 is generated as 𝐴𝐾 = ∫𝐾 (𝑅𝑆𝑚 ‖𝐿𝐴𝐼). The parameter 𝐾 is the secret shared key by MS and its HN. Although the 𝑅𝑆𝑚 is transmitted as cleartext and the key gen- eration function 𝑓 𝑥 is a public cryptography generator and the
𝐴𝐾 is assumed to be securely sent from HLR/AuC to
VLR/SGSN, the temporary key cannot be generated without
knowing the secret key 𝐾 shared by MS and HLR/AuC. After the initial authentication, the VLR/SN gets a temporary key 𝐴𝐾
that it shares with the MS and subsequently can accomplish
the mutual authentication by itself. Therefore, VLR/SGSN
owns the temporary key to authenticate MS on behalf of the
HLR/AuC.
In the DS-AKA protocol, the temporary key is used for cal-
culating a recursive hash chaining authenticators 𝐴𝐴𝐶𝑆𝑖 =
1 1
• Mutual authentication between MS and its SN: Similar to
∫𝑇𝐾�𝐴𝐴𝐶𝑆𝑖2−1 ‖𝐴𝐴𝐴𝑆 �, 𝐴𝐴𝐶𝑚𝑖 = ∫𝑇𝐾�𝐴𝐴𝐶𝑚𝑖−1 ‖𝐴𝐴𝐴𝑚 �
and
authenticating the HLR/AuC, on receiving 𝐴𝐴𝐴𝑆𝑠 that re- ceived in 𝐴𝐼 , the MS computes expected authentication code of HLR/AuC 𝑋𝐴𝐴𝐶𝐻 and the expected hash chaining authen- ticator 𝑋𝐴𝐴𝐶𝑆𝑖 and compares it with the received 𝐴𝐴𝐶𝐻 , XMACSi . If both are equal then the authentication of SN is suc- cessful. In step 5 of the DS-AKA protocol upon receipt of 𝐴𝐼 , VLR/SGSN authenticates the MS by verifying the 𝑋𝑅𝑋𝑆 ? =
𝑅𝑋𝑆. If the equation is hold then MS is successfully authenti-
cated. This ensures mutual authentication between MS and
VLR/SGSN.
• Freshness of session keys: The DS-AKA protocol provide
𝑋𝑅𝑋𝑆 = ∫𝑇 �𝐴𝐴𝐶𝑆𝑖−1 ‖𝐴𝐴𝐴𝑆 �. The 𝐴𝐴𝐴𝑚 and 𝐴𝐴𝐴𝑆 are accumu-
lated on each successful authentication and the anonymity
key 𝐴𝐾 is used to conceal these parameters, the 𝐴𝐴𝐴𝑚 and
𝐴𝐴𝐴𝑆 can be used to guarantee the freshness of authentication
request.
Since 𝐴𝐴𝐶𝑆𝑖 , 𝐴𝐴𝐶𝑚𝑖 and 𝑋𝑅𝑋𝑆 are derived from the previ-
ous visit, , the freshness of hash chaining authenticators can
be guaranteed by 𝐴𝐴𝐴𝑚 and AccS. Therefore, 𝐴𝐴𝐶𝑆𝑖 , 𝐴𝐴𝐶𝑚𝑖
and 𝑋𝑅𝑋𝑆 are changed in each authentication. If an intruder
eavesdrops these authenticators to generate the expected hash
chaining authenticators such as 𝐴𝐴𝐶𝑆𝑖+𝑖 = ∫𝑇 �𝐴𝐴𝐶𝑆𝑖 �𝐴𝐴𝐴𝑆𝑖 �,
1 2 𝐾
stronger key agreement to protect the communication be-
tween the MS and the VLR/SGSN. In the DS-AKA-I proce-
dure, the 𝐶𝐾𝑖 and 𝐼𝐾𝑖 are generated in step 4 and step 5,
whereas in DS-AKA-II procedure they are generated in step 7
and step 8. Since the composition of session keys 𝐶𝐾 and 𝐼𝐾
are based on the previous hash changing output and the ac-
cumulated AccS, the freshness of these keys can be guaranteed by 𝐶𝐾𝑖−1 . and 𝐼𝐾𝑖−1 . The 𝐶𝐾𝑖−1 and 𝐼𝐾𝑖−1 can be taken as
the new random challenge for the input of the current hash
𝐴𝐴𝐶𝑚𝑖+1 = ∫𝑇𝐾�𝐴𝐴𝐶𝑚𝑖 ‖𝐴𝐴𝐴𝑚 �, 𝑋𝑅𝑋𝑆 = ∫𝑇 �𝐴𝐴𝐶𝑆𝑖 ‖𝐴𝐴𝐴𝑆 �, its infeasible without knowing the temporary key 𝐴𝐾 . Moreover,
if an intruder eavesdrops these authenticators to reverses
them to derive the temporary key, it is infeasible because all
cryptography function that used are a one way function.
5.3 Resistance to Attacks
• Redirection Attack: In UMTS-AKA, an authentication vector (AV) can be used by any SN. This situation can be
chaining 𝐶𝐾𝑖 and 𝐼𝐾𝑖 . The 𝐴𝐴𝐴𝑆 in 𝐴4
or 𝐴2
is accumulated on
abused to redirect data to an SN. This is called a redirection
each successful authentication and the anonymity key 𝐴𝐾 is used to conceal these parameters. Therefore, the 𝐴𝐴𝐴𝑆 can be
used to guarantee the freshness of these keys.
attack. In this case a false base station impersonates a SN. The
false base station will then redirect all traffic to a SN of their
choosing. The AKA procedure will normally succeed and the
user will not notice being connected to another network. This
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1255
ISSN 2229-5518
can cause the user to get unusually high bills. Additionally it might be used to redirect traffic to networks with lower securi- ty, causing a wrong impression of the security level applied.
In DS-AKA protocol, an authentication vector (AV) gener- ated by the user's HN can only be used by a particular serving network (SN). This is achieved by involving the identity of
location area LAI of the BSS for SN in the generation and veri- fication of the message authentication code 𝐴𝐴𝐶𝑚. Whenever
an MS enters a new SN will get the identity of that SN, and
then start a registration process to register itself to the network
by replying with a 𝐴𝐴𝐴𝑚 and 𝑅𝑆𝑚 together with 𝐴𝐴𝐶𝑚𝑖 =
use of its message authentication code 𝐴𝐴𝐶𝑚𝑖 which involved in 𝐴𝐼 . This message provides the legal proof of the MS's intent
to register itself. In SD-AKA-I procedure, the HLR/AuC
could check the integrity of code 𝐴𝐴𝐶𝑚𝑖 , so the forged mes- sage generated by a malicious using 𝐴𝐼 can be detected by HLR/AuC on receipt of 𝐴𝐼 from VLR/SGSN. Therefore, the
DoS attack will be recognized at step 3 by HLR/AuC side and
no more traffic would be procreated in the network.
Secondly, after the initial authentication, the VLR/SN gets
a temporary key 𝐴𝐾 and other authentication information that
it shares with the MS and subsequently can accomplish the
1 𝐼
∫ (𝐴𝐴𝐴𝑚 ‖𝐿𝐴𝐼) providing integrity of 𝐴𝐴𝐴𝑚 , 𝐿𝐴𝐼 in 𝐴1 and
𝐾
store a profile of the new SN in its database, which includes
𝐴𝐴𝐴𝑚 and 𝑅𝑆𝑚 .
mutual authentication by itself without intervention of the
HLR/AuC. That is, subsequent authentication (SD-AKA-II)
only happens between the MS and the SGSN/VLR using three
𝐼 𝐼𝐼
𝐼𝐼
𝐼𝐼
Since the SN knows the 𝐿𝐴𝐼 of the BSS forwarding 𝐴1, then forward that message together with BSS’s 𝐿𝐴𝐼 to HN. When
message exchanges 𝐴1 , 𝐴2 , and 𝐴3 . Consequently as ex-
plained in SD-AKA-II procedure at step7, the VLR/SGSN
𝐼𝐼
the HN receives the user's authentication request from the SN,
checks the integrity of the 𝐴𝐴𝐶𝑚𝑖 in the message 𝐴1
with the
the HN verifies the 𝐴𝐴𝐶𝑚𝑖 to ensure that the user is indeed in
temporary key 𝐴𝐾 authorized by the HLR/AuC. In this case, if
𝐼𝐼
the territory of the SN by matching the 𝐿𝐴𝐼 that reported in
𝐼
a malicious forges 𝐴1
and then send it to VLR/SGSN, the
𝐴2
from VLR/SGSN. When the HN begins to generate the
forged message can be immediately detected by the
authentication vector, it should insert 𝐴𝐾 , 𝑛 and 𝐴𝐴𝐴𝐴𝐻 =
(𝐴𝐴𝐶𝐻 ‖𝑅𝑆𝐻 ‖𝐴𝐴𝐴) into the authentication vector 𝐴𝐴, where
𝐴𝐾 is a temporary key and 𝑛 is the life time of the 𝐴𝐾 . Further-
VLR/SGSN and then rejects the forged messages.
In the DS-AKA protocol, the temporary key is used for cal-
culating a recursive hash chaining authenticators 𝐴𝐴𝐶𝑆𝑖 =
𝑥 1 1
more, the 𝐿𝐴𝐼 embedded in 𝐴𝐾 = ∫𝐾 (𝑅𝑆𝑚 ‖𝐿𝐴𝐼) which is com-
∫𝑇𝐾�𝐴𝐴𝐶𝑆𝑖2−1 ‖𝐴𝐴𝐴𝑆 �, 𝐴𝐴𝐶𝑚𝑖 = ∫𝑇𝐾�𝐴𝐴𝐶𝑚𝑖−1 ‖𝐴𝐴𝐴𝑚 �
and
puted both in MS and HN.
Therefore, the DS-AKA protocol prevent the redirection at-
tack by preventing a user from being tricked and redirect traf-
fic to a network with lower security and solve the mischarged
billing problem.
• Man-in-the middle Attack: In DS-AKA, a new key 𝐼𝑆𝐾 is
used to encrypt and decrypt the communicated information
between the MS and its BTS. Since the original UMTS AKA
does adopted a key generation for such key, a new key gener-
ation function 𝑓6 is used to generate 𝐼𝑆𝐾 key between the MS
and VLR/SGSN to prohibit the communication from being
eavesdropped or altered. The new key 𝐼𝑆𝐾 is generated after
𝑋𝑅𝑋𝑆 = ∫𝑇 �𝐴𝐴𝐶𝑆𝑖−1 ‖𝐴𝐴𝐴𝑆 �. The 𝐴𝐴𝐴𝑚 and 𝐴𝐴𝐴𝑆 are accumu-
lated on each successful authentication and the anonymity
key 𝐴𝐾 is used to conceal these parameters, the 𝐴𝐴𝐴𝑚 and
𝐴𝐴𝐴𝑆 can be used to guarantee the freshness of authentication
request. In the 𝑖𝑡ℎ performing the DS-AKA protocol, the
VLR/SGSN accumulate the 𝐴𝐴𝐴𝑆 by 1 and send it to the MS
together with the 𝐴𝐴𝐶𝑆𝑖 . The MS retrieves the 𝐴𝐴𝐴𝑆 and
checks if it is a replay and sets the new the 𝐴𝐴𝐴𝑆 to 𝐴𝐴𝐴𝑚 for
synchronizing the 𝐴𝐴𝐴𝑚 and 𝐴𝐴𝐴𝑆 . the MS will set the new the
𝐴𝐴𝐴𝑆 to 𝐴𝐴𝐴𝑚 . Moreover, the management of synchronized
𝐴𝐴𝐴𝑆 to 𝐴𝐴𝐴𝑚 is needed for synchronization between an MS
and a VLR/SGSN periodically and could them decide about
𝐼 𝐼
exchanging the messages 𝐴4 , 𝐴5 in initial authentication pro-
the genuineness the messages by verifying the recursive hash
𝐼𝐼
𝐼𝐼
cedure and 𝐴2 , 𝐴3
in subsequent authentication procedure.
chaining authenticators integrity. Meanwhile, the synchroni-
Therefore, the DS-AKA prevents the man-in-the-middle attack
zation procedure could be used to detect the forged message
𝐼𝐼
by encrypting the information communication before the
of the 𝐴1
initiated by a malicious entity at VLR/SGSN side in
transmission and then the data confidentiality of the commu-
nication channel between the MS and the VLR/SGSN can be
DS-AKA-II.
Therefore, the DS-AKA can partially prevent DoS attacks .
𝐼𝐼
guaranteed.
The forged message of the 𝐴1
can be immediately detected
• DoS Attack: When an MS needs to authenticate itself to
all entities of network to access or utilize network services, the
MS invokes the distribution of authentication procedure by
sending the authentication request messages to the HLR/AuC
through VLR/SGSN in the serving network. Firstly, The au-
thentication between the MS and his HLR/AuC relies on the
6 COMPARISON WITH RELATED WORK
As described in section 3, the UMTS AKA protocol consists of two procedures. First, the user registers with its HN, and then distributes an authentication vector (AVs) from the HLR/AuC in the home network to the VLR/SGSN in the serving network (SN). An AV is temporary authentication data which enables a VLR/SN to engage in UMTS authentication and key agree- ment with a particular user. Second, the authentication and
by the VLR/SGSN side in the subsequent authentication pro-
cedure DS-AKA-II, and then rejects the forged messages.
While as, the forged message of 𝐴𝐼 can only be detected by
the HLR/AuC side in the initial authentication procedure DS-
AKA-I.
key agreement procedure runs between MS and SN. The SN uses the authentication information of the first procedure to carry out the bilateral authentication between MS and SN and then an agreed key and a cipher key are provided. In UMTS, Obviously, the UMTS AKA protocol has the problems of the bandwidth consumption between SN and HN and the stor- age space overhead for SN’s database.
Firstly, the bandwidth consumption between SN and HN occurs when MS requests to authenticate itself for the VLR/SGSN in serving network (SN) and no authentication
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1256
ISSN 2229-5518
vectors are available the VLR/SGSN must turn back to HLR in the Home Network (HN) to make a registration request to
generate another array of n authentication vectors. Moreover,
when the subscriber roams to a newly visited VLR/SGSN
within a different serving network domain the authentication
vectors in the old VLR/SGSN are deleted, which is called an
unused authentication vectors problem. Subsequently, as a lot of data being sent between VLR/SN and HLR/HN, this has impact on the performance of AKA protocol.
Since the UMTS AKA, AP-AKA and Harn&Hsia protocols
are restricted to n times, the n authentication vectors are nec-
essarily transferred from HN to SN for authentication. Obvi-
ously, these protocols have the problem of the bandwidth con-
sumption between SN and HN. Whereas, the proposed DS-
AKA, X-AKA and S-AKA protocol employ the temporary key
technique to solve the reduction of bandwidth consumption
problem by sending SN a temporary key, SN can directly au-
thenticate MS without intervention of HN. Therefore, it is un-
necessary for the VLR/SN to request another set of authentica- tion vectors from HN and then reduce the network traffic.
Secondly, the storage space overhead occurs if there are m subscribers, and an array of n authentication vectors for each subscriber in SN, then the SN must wastefully store n × m
authentication vectors. In UMTS AKA, AP-AKA protocols do
not consider storage space overhead for SN’s database, where
an array of 𝑛 authentication vectors for each MS must be stored in the VLR/SN. So if there are 𝑚 MSs in a VLR/SN, then the VLR/SN must store 𝑛 × 𝑚 authentication vectors.
Therefore, a space overhead occurs. In contrast, the proposed
DS-AKA, X-AKA and S-AKA protocols employ the temporary
key technique which make VLR/SN store only one copy of
authentication vectors to authenticate MS instead of n copies
of authentication vectors. Moreover, in Harn&Hsia only stores
the authenticator ℎ𝑛−𝑖 (𝑚) to authenticate MS. Therefore, the
DS-AKA protocol reduces the storage space overhead for SN’s
database and then attains the reduction of VLR storage.
Thirdly, the design of the X-AKA and S-AKA protocol have
a shortcoming in the complexity of operations in terms of ran-
dom number generation overhead. In the 𝑖𝑡ℎ performing of
the second procedure for both protocols, SN must continually
generate a random number 𝑅𝑆𝑠 and computes the correspond- ing message authentication code 𝐴𝐴𝐶𝑠 as a challenge infor- mation for MS as well as computes cipher key 𝐶𝐾 and integri- ty key 𝐼𝐾. Therefore, the generation random number for each
authentication has a negative impact on the performance of
AKA protocol by increasing the computation and storage cost
on SN side. Whereas the proposed DS-AKA protocol employs
the key hash chaining technique. This technique does not
need to continuously generate a new random challenge for
each authentication iteration. In the 𝑖𝑡ℎ performing of the se-
cond procedure, SN produces a new sequence of hash chain-
ing authenticator 𝐴𝐴𝐶𝑆𝑖 by computing
𝐴𝐴𝐶 = ∫1 �𝐴𝐴𝐶 �𝐴𝐴𝐴 �, where 𝑖 ≤ 𝑛 and 𝐴𝐴𝐶 com-
puted in the previous visit. Therefore, The 𝐴𝐴𝐶𝑆𝑖−1 can be used
as a new random challenge for the input of a new sequence
for keyed hash chaining. So, performing the AKA procedure
between MS and SN for 𝑖𝑡ℎ times without intervention of the
HLR in the home network and continuously generation a new
random challenge.
As Table 1 shows, several authentication schemes had been proposed. All schemes have the properties, including mutual authentication between MS and HE, mutual authentication between MS and SN, reduction of bandwidth consumption between SN and HN, reduction of storage space for SN’s da- tabase, Random Number Generation, Redirection Attack, Man-in-the middle Attack and DoS Attack.
TABLE 1
A Comparison among the AKA Protocols
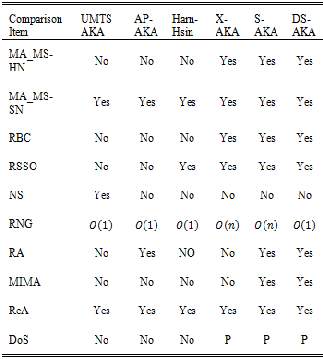
MA_MS-HN: Mutual Authentication between MS and HN; MA_MS-SN: Mutual Authentication between MS and SN: RBC: Reduction of bandwidth consumption between SN and HN; RSSO: Reduction of storage load for SN’s database; NS: Need Synchronization between MS and HN; RNG: Random Number Generation Load , RA: Redirection Attack, Y: Robust; N:Not robust; P: Partially, MIMA: Man-in-the middle Attack, ReA: Replay Attack, DOS: DoS Attack
7 CONCLUSION
In this paper, the security vulnerabilities of UMTS AKA protocol are analysed and proposed a new dynamic and secure Authenti- cation and Key Agreement Protocol by using the key hash chain- ing technique and the temporary key mechanism, called DS- AKA for UMTS networks.
Comparing with other protocols, the results shows that the proposed DS-AKA protocol improve the performance AKA protocol by reducing the communication times and fulfil the security requirements of the third generation mobile systems. The proposed protocol significantly reduces the communica- tion overhead between the home network and the visited net- work, reduces the storage space overhead for SN’s database and reduces the random number generation overhead. In ad- dition, the proposed DS-AKA protocol can not only improve the performance of UMTS AKA but also withstand for both
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1257
ISSN 2229-5518
redirection and man-in-the-middle attacks and can partially prevent DoS attacks. Future work will provide a performance analysis of DS-AKA protocol.
REFERENCES
[1] K. Passerini,, K., Bartolacci, R., and J. Fjermestad, “Reflections and Trends in the Expansion of Cellular Wireless Services in the U.S. and China,” Proc. com- munications of the ACM. 50(10), 2007.
[2] S. Yuan, B. Elizabeth, Gao, X., and K. James, “Real-time traffic sup- port in heterogeneous mobile networks,” Proc. Springer Science + Business Media, Wireless Network13, pp.431–445, 2007.
[3] M. Iftikhar, B. Landfeldt,, and M. Caglar, “Traffic Engineering and QoS Control between Wireless DiffServ Domains Using PQ and LLQ,” Proc. ACM 978-1-59593-809-1, MobiWac’07, Chania, Crete Island, Greece, 2007.
[4] 3GPP, “3G Security; Security Threats and Requirements: 3rd Genera- tion Partnership Project (3GPP),” Technical Specification Group Ser- vices and System Aspects, 3GPP TS 21.133, 4.1.0 (2001-12) (Release 4),
2001.
[5] W. Stalling, Cryptography and Network Security: Principles and Practice.
6th edition. USA: Prentice Hall, 2014.
[6] M. Al-Fayoumi, N. Shilbayeh, “Cloning SIM Cards Usability Reduc- tion in Mobile Networks,” Springer’s Journal of the Network and Sys- tems Management, Vol. 22, no. 2, pp. 259-279, April 2014, doi:
10.1007/s10922-013-9299-8.
[7] ETSI,. “Recommendation GSM 03.20: Security related network func- tions”, Technical report. European Telecommunications Standards Institute, ETSI, 1993.
[8] M. Rahnema., “Overview of the GSM System and Protocol Architec- ture,” IEEE Communication Magazine, Vo. 31, no. 4, pp.92-100, 1993.
[9] L. Harn, and H.Y. Lin, “Modification to enhance the security of the GSM protocol,” Proc. 5th National Conference on Information security, Taipei, Taiwan, pp. 41-20, 1995.
[10] K. Al-Tawil, A. krami, and H. Yousef, “A New Authentication Proto- col for GSM Networks,” Proc. 23rd Annual IEEE Conference on Local Computer Networks (LCN’98), pp. 21-30, 1998.
[11] C.C. Lo, and Y.J. Chen, “Secure communication mechanisms for GSM networks,” IEEE Transactions on Consumer Electronics, Vol. 45, no. 4, pp.1074-1080, 1999.
[12] C. Lee, M. Hwang, and W. Yang, “Extension of Authentication Pro- tocol for GSM.,” Proc. IEE Communication, Vol. 150, no. 2, pp.91-95,
2003.
[13] M. Al-Fayoumi, M. Alnababteh, M. Daoud, M. Alhawarat, “Dynam- ic Authentication Protocol for Mobile Networks Using Public-Key Cryptography,” International Journal of Science and Research (IJSR), Vol. 4, no. 1, January 2015.
[14] M. Zhang, Y. Fang, “Security analysis and enhancements of 3GPP authentication and key agreement protocol,” IEEE Transactions on Wireless Communication, Vol. 4, no. 2, pp. 734–742, 2005.
[15] Y. Lin, Y. Chen, “Reducing Authentication Signaling Traffic in Third-
Generation Mobile Network,” IEEE Transactions on Wireless Commu- nications, Vol. 2, no. 3, pp. 493-501, 2003.
[16] J. Al-Saraireh, S. Yousef, “Analytical Model: Authentication Trans- mission Overhead Between Entities in Mobile Networks,” Elsevier, Computer Communications Journal, Vol. 30, no. 9, pp. 1713-1720, 2007.
[17] L. Harn, W. Hsin, “On the Security of Wireless Network Access with
Enhancements,” Proc. 2003 ACM workshop on Wireless Security, San
Diego, USA, pp. 88-95, 2003.
[18] L. Lamport, “Password authentication with insecure communica- tion,” Communication of ACM, Vol. 24, no. 11, pp. 770-772, 1981.
[19] C. Huang C., J. Li, “Authentication and Key Agreement Protocol for UMTS with Low Bandwidth Consumption,” Proc. 19th International Conference on Advanced Information Networking and Applications (AINA'05), pp. 392-397, 2005.
[20] J. Al-Saraireh, S. Yousef, “A New Authentication Protocol for UMTS
Mobile Networks,” EURASIP Journal on Wireless Communications and
Networking, Vol. 2006, no. 2, pp. 19-30, 2006.
[21] H. H. Ou, M. S. Hwang, J. K. Jan, “A cocktail protocol with the au- thentication and key agreement on the UMTS,” Journal of Systems and Software, Vol. 83, no. 2, pp. 316–325, 2010.
[22] S. Wu, Y. Zhu, Q. Pu, “Security analysis of a cocktail protocol with the authentication and key agreement on the UMTS,” Communication Letters, Vo. 14, no. 4, pp. 366–368, 2010.
[23] Y. L. Huang, C. Y. Shen, S. W. Shieh, “S-AKA: A provable and secure authentication key agreement protocol for UMTS networks,” IEEE Transactions on Vehicular Technology, Vo. 60, no. 9, pp. 4509–4519,
2011.
[24] N. Saxena, N. S. Chaudhari, “NS-AKA: An improved and efficient AKA protocol for 3G (UMTS) networks,” Proc. International conference on advances in computer science and electronics engineering (CSEE’14), Kuala Lampur, Malaysia, pp. 220–224, 2014.
IJSER © 2015 http://www.ijser.org





