
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 131
ISSN 2229-5518
Credit Card Fraud Detection Using Iris
Biometrics Technique
Mrs Sayalee P. Deshmukh, Dr S.H.Patil
Abstract— A new architecture based on Iris Biometric Technique is a very recent concept and it is very useful for decrease Credit Card Frauds over Internet. . This technique is use for the security purpose. The non-intrusive property of iris recognition leads to several problems to the images of natural-open eyes and it is hard to increase the accuracy of iris recognition because of these problems. In order to ensure the non-intrusive property as well as achieve an iris recognition which has high accuracy simultaneously, this paper presents a novel iris recognition method based on the natural-open eyes. Firstly, makes pre-process to iris image, ensures the effective iris area adaptively. Secondly, finds all iris feature points by directional information, length information, and width information of texture, the neighbouring gray information and relativity in the effective iris area. Thirdly, makes codes to feature points and figures the iris pattern by iris codes. Finally, sorts the different iris patterns by auto accommodated pattern matching method and gives the recognition results. Many experiments show the recognition rates of this method can reach 99.687% that can meet the demand of iris recognition. As compare to other methods proposed mostly this method is used for iris recognition.
Key word –iris biometrics, security, feature points, iris localization, iris normalization, feature extraction, unwrapped iris image, iris matching
—————————— ——————————
As an important and distinct characteristic for status, the Iris has many advantages such as uniqueness, stability, may gather and so on. Non-contacting biometrics is the
inevitable trend for the research and the development of status identification. The error rate of iris recognition is the lowest in all the biometrics according to the statistics [1]. Daugman [2-
4]presented an algorithm that needs to process the two dimen- sional information of the texture, and increases feature extrac- tion time; Wildes[5,6] used the Gauss-Laplace filter to decom- pose the iris image under the different resolution, and carried on the correlation comparison for the corresponding images, the computation is huge; Boles and Boashash [7] proposed a novel iris recognition algorithm based on zero crossing detec- tion of the wavelet transform, this method has only obtained the limited results in the small samples, and this algorithm is sensitive to the grey value changes, thus recognition rate is lower.
This paper presents a novel iris recognition method based on the natural-open eyes. Firstly, it makes pre-process to iris im- age, ensures the effective iris area adaptively. Secondly, it finds all iris feature points by directional information, length infor- mation, and width information of texture, the neighbouring gray information and relativity in the effective iris area. Third- ly, it makes codes to feature points and figures the iris pattern by iris codes. Finally, it sorts the different iris patterns by auto
————————————————
• Sayalee.P. Deshmukh is currently pursuing masters degree program in Computer in Bharati Vidyapeeth Deemed University College Of Engineer- ing Pune, India.
• Prof. Dr.S.H.Patil, has received his B.E degree in Computer from Walchand
Institute Of Technology Sangli, India in 1989, the M.E degree from COEP, India in 1992, the Ph. D from BVDU, Pune, COE in 1991 and is working
with BVDUCOE Pune till date. )
accommodated pattern matching method and gives the recog- nition results.
Biometrics is the science of automated recognition of per- sons based on one or multiple physical or behavioural charac- teristics. Among several biometrics, iris biometrics have gained lots of attention recently because it is known to be one of the best biometrics. Also, iris patterns possess a high degree of randomness and uniqueness even between monozygotic twins and remain constantly stable throughout human‟s life. Additionally, encoding and matching are known to be reliable and fast. One of the most crucial steps in building an iris secu- rity system is iris segmentation in the presence of noises such as varying pupil sizes, shadows, specular reflections and high- lights. The step definitely affects the performance of the iris security system since the iris code is generated from the iris pattern and the pattern is affected by iris segmentation
When we carry on the recognition experiment, we weigh
the algorithm with false acceptance rate(FAR), false rejec-
tion rate(FRR), equal error rate(EER), and correct recognition
rate(CRR). Simultaneously we inspect the algorithm with the
execution time, including feature extraction time, match time.
We use the CASIA in the iris database [9] 567 images, includ-
ing 81 different irises of eyes, each eye had 7 8-bit images, the resolution is320×280. When the size of block is 3*4, the exper- imental result is best. The threshold of match distance is
0.22922, CRR=99.687%, FAR=0.313051%, FRR=0.293945%, namely the correct recognition results are 159959 times, the
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 132
ISSN 2229-5518
false rejection results are 5 times, the false acceptance results are 497 times. We carry on the duplicated experiments for two previous mentioned methods in the same image samples, the experimental results are listed as follows
Table 1: The accurate recognition rate of difference algo- rithm The CRR of this article under the threshold value is slightly lower than the Daugman’but is higher than boles algorithm.
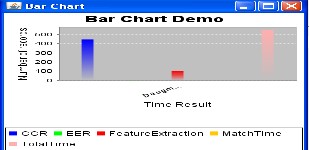
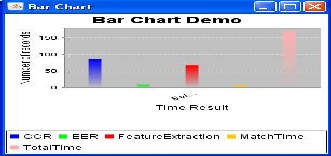
Method | CRR (%) | EER (%) | Feature extraction time (ms) | Match time (ms) | Total Time (ms) |
Daugman | 100 | 0.08 | 682.5 | 4.3 | 686.8 |
Boles | 92.64 | 8.23 | 170.3 | 11.0 | 181.3 |
Proposed | 99.687 | 0.303 | 8.3 | 7.2 | 15.5 |

Usually an iris image impossibly contains the iris merely, there are also other parts of the eye Such as the eyelid, the eye- lash. This point may be seen clearly from Figure 1. The interior Boundary of iris can change, and make the texture of iris dis- tort. In order to realize exactly matching, it must eliminate these factors through the image pre-processing. Iris image Pre- processing includes iris localization, eyelid fitting, eyelash detection and normalization.
Firstly, it finds the sketchy pupil center through the gray projection and the pupil center detection operator; Secondly
,finds four iris inner boundary points by the direction edge detection operator and the voting mechanism beginning from the sketchy pupil center, and locates the iris inner boundary according to these four points; Finally finds four iris outer boundary points by the direction edge detection operator and the voting mechanism beginning from the center of pupil, and locates the iris outer boundary according to these four points. Localization accuracy rate of this method is high, the speed is quick. The detail contents can be seen from literature.
Firstly it uses Canny operator to extraction edge infor- mation of iris image, then uses the parabolic equation as for- mula to fit the lower eyelid: y _ a ( x _ b ) 2 _ c (1) a is the pa- rabola curvature; b, c are the horizontal and vertical coordi- nates of parabola apex respectively. Through establishing dif- ferent a, b, and c it may fit the lower eyelid well, thus it can eliminates influence of the lower eyelid for the effective iris region. It finds the parabola apex. The resultant images of Fig-
ure 1 are shown in Figure 2.
Firstly, it makes sure the search area. The parameters of in- ner boundary and outer boundary are and respectively. It chooses two rectangles of the left and right sides of the pupil as the possible area covered by the eyelash . The four vertexes of right area are ( , , ) p p p x y r ( , , ) i i i x y r ( , ) p i i x y _ r (
1, i i ) lWidth _ y _ r ( , ) p i i x y _ r ( 1, i i ) lWidth _ y _ r .The lWidth is the width of the image. The four vertexes of left area are (0, i i ) y _ r ( , ) p i i x y _ r (0, i i ) y _ r ( , ) p i i x y _ r Be- cause the gray of eyelash is low, so a template of detection eyelash is designed, its shape is shown in Figure3.Each sub- template X1 X X2 may compose by a single pixel or multiple pixels. If a sub-template is composed by a single pixel, this pixel corresponds the center of the sub template; if a sub- template is composed by N(N>=2) pixels { , ,... },the center pix- el locates at n=ceil(N/2) and a 1 2 N a a a n is the center pixel of the corresponding sub-template. It looks the center of X as the current point and sums the gray difference with X1,X2 respectively, if two difference is less than 0, the current point is taken as the candidate eyelash point. It searches in two rec- tangles and finds all candidate eyelash points according with conditions. Then it carries on thinning to the image that can ensure the directions, curvature and connectivity of eyelash, show the shape of eyelash well and delete some non-eyelash area. The gray of all candidate eyelash points are set 0, the gray of other points are set 255, so it gets the binary eyelash image. Figure 3 Eyelash detection template The found candi- date eyelash points include true eyelash and false eyelash, so it needs to eliminate these false eyelash. It includes two steps:(1)because eyelash mainly tends to vertical direction and has certain length, it can use the template shown in Figure 4. According to the length information and direction information of the eyelash it eliminates some false eyelash points. In Figure
4 point A is the current candidate eyelash point, if one of these points B L locating at the next line of point A is candidate eye- lash point, the corresponding length of eyelash adds 1. It makes recursion for this operation until it reaches the bottom of eyelash. If the length of the curve is longer than T, it is re- garded as eyelash and kept, otherwise the curve is eliminated. (2)Because the beginning point of eyelash is located near up- per eyelid, the beginning point of the kept curve does not lo- cate near the upper eyelid, the curve is eliminated too.
An iris image contains much detail texture, the texture is composed by many shape blocks such as strip and speckle, the gray differences are big and distribute unevenly, these blocks with irregular shape can be as distinguish characteristics for iris recognition.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 133
ISSN 2229-5518
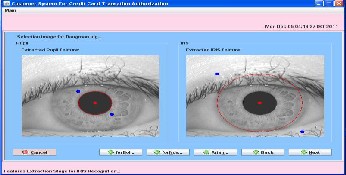
In the collective and effective area, we make match to the entering iris and registering iris. When we compare with two iris codes, because the anterior normalized operation cannot solve the revolving invariable problem, we need to carry on certain revolving match for registering iris and entering iris. The revolving can be compensated even the corresponding code of the registering iris and the entering iris can not corre- spond completely. This article solves the revolving invariable problem in the normalized image, this may transform the re- volving operation in the annular iris to the translation opera- tion in the rectangular iris. The concrete method is as follows: when it compares with two iris codes, maintains the code of the registering iris motionless, and the code of the entering iris is translated several pixels to left or right along horizontal di-
rection (because the angles of rotation of image is not big, translation pixels are small), it calculates a match value with the registering iris code after translating one pixel, after the translation ends, we keep the maximum of all the match val- ues as the final match value of the registering iris and the en- tering iris. Formula is given below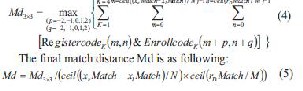

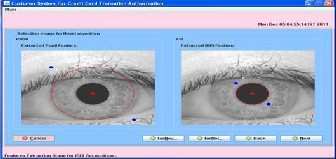
Select image from image database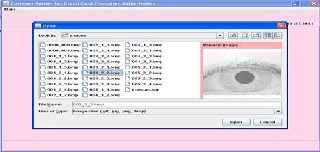
Select image for daugman algorithm.
Here in the screen the unwrapped iris image, mask for cur- rent iris, iris code get from the unwrapped image and also shown iris code represent image pattern.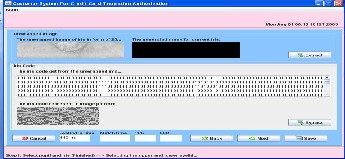
Here save the all information which fill in the screen to the database.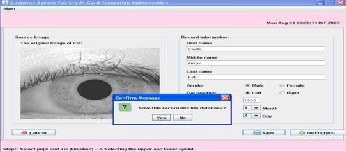
This screen is for the encryption .here source image is encrypt
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 134
ISSN 2229-5518
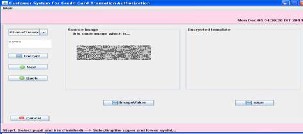
This screen is for the decryption .Here decrypt encrypted im- age
If record saved in the database then matching process is suc- cessfully done then shows the following Message Authentica- tion successfully, images are not matched and give different process values.
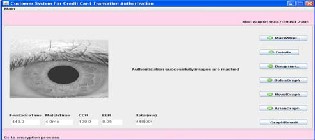
Here for daugman algorithm add the details.
Select image for boles algorithm.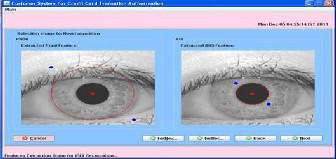
Here in the screen the unwrapped iris image, mask for current iris, iris code get from the unwrapped image and also shown iris code represent image pattern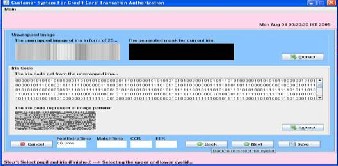
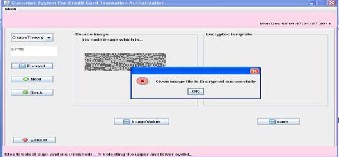
This screen is for the encryption .here source image is encrypt
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 135
ISSN 2229-5518
This screen is for the decryption .Here decrypt encrypted im- age.
Here for Boles algorithm add the details.
Select image for Novels algorithm.
Here in the screen the unwrapped iris image, mask for cur- rent iris, iris code get from the unwrapped image and also shown iris code represent image pattern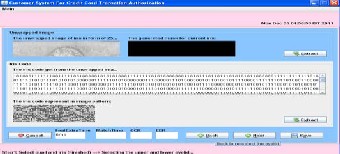
This screen is for the encryption .here source image is ecrypt and give the message encryption successfully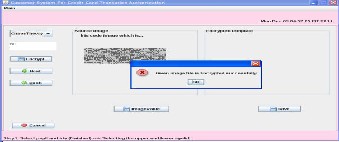
Here for Novels algorithm add the details.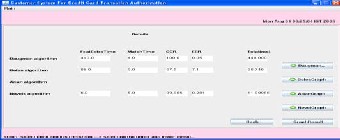
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 136
ISSN 2229-5518
Select image for Arian algorithm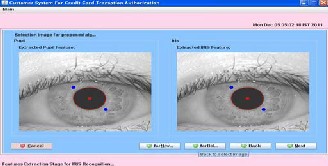
Here in the screen the unwrapped iris image, mask for current iris, iris code get from the unwrapped image and also shown iris code represent image pattern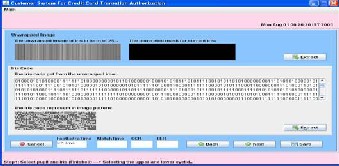
Here for Arian algorithm add the details.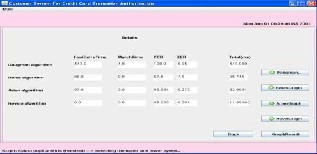
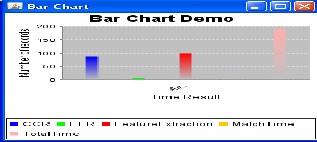
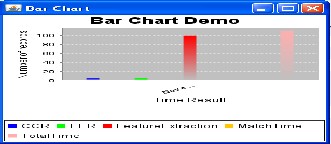
For All four means Daugman, Boles, Novels and Arian graph result shown in below graph.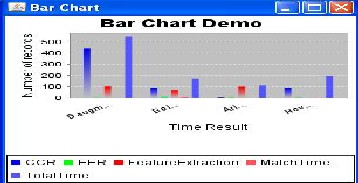
Proposed iris recognition method find the iris characteristic point in a short time, the recognition rate is high, and the recognition speed is guaranteed. Automatic iris recognition has been studied for more than a decade. Many recognition techniques have been developed and some commercialized systems are available now.In this it inner pupil part and outer iris part in the iris images. Experimental results show that the proposed localization algorithm is efficient and improves the accuracy of iris recognition. Our method achieves an accuracy of 99%.it also runs faster than other. This method is particular- ly suitable for implementing high-accuracy iris verification
/identification systems, we tested the iris recognition system on CASIA iris images database.
[1] L. Flom, A. Safir, “Iris Recognition System,”U.S.
Patent 4641349, Patent and Trademark Office, Washing-
ton, DC, 1987.
[2] J. Daugman, “High confidence visual recognition of per- sons by a test of statistical independence, ” IEEE
Transactions on Pattern Analysis and Machine Intelligence,
1993, 15(1): 1148–1161J. Daugman, “Statistical richness of visu-
al phase information: update on recognizing persons by iris
patterns, ” Int. J.Comput. Vis, 2001, 45(1):25–38
[3] J. Daugman, “Demodulation by complex-valued wavelets for stochastic pattern recognition,” Int.
J. Wavelets, Multi-Res. and Info. Processing, 2003, 1(1): 1–17
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 137
ISSN 2229-5518
[4] R. Wilde, J. Asmuth, G. Green, “A machine-vision system for iris recognition, ” Mach. Vis. Applic, 1996, 9: 1–8
[5] R. Wildes, “Iris recognition: an emerging biometric tech- nology, ” Proc. IEEE, 1997, 85(9): 1348–1363.
[6] W.Boles, B. Boashash,“A human identification technique using images of the iris and wavelet transform” IEEE Transaction on Signal Processing, 1998, 46(4) 1185–1188
[7] W. Yuan, Z. Lin, L. Xu, “A rapid and accurate Iris Locali- zation algorithm” Journal of Optoelectronics Laser,2007,
18(6): 729-733
[8] Institute of Automation, Chinese Academy of Sciences.
CASIA Iris Image Database (ver1.0)
[9] Vagala,R.R, Sasi,S., “Biometric Authenrication for ecom- merce Transaction” published in the proceeding of inter- national workshop on Imaging Systems and Tech- niques(IEEE IST),2004
[10] Daugman JG (1993) “High confidence visual recognition of persons by a test of statistical independence”. IEEE- PAMI, 15: 1148-1161.
[11] Daugman JG (2002) “How Iris recognition works”. The Computer Laboratory, Cambridge, Iridian Technologies, U.K.
IJSER © 2014 http://www.ijser.org