International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 674
ISSN 2229-5518
Comparison between AODV, TORA and DSR for Providing QoS Guarantees in Mobile Adhoc Network
Rakhi Vijayvargiya, Nishith Anand, Vishnu Dhakad
Abstract- In this Paper, multimedia wireless network simulation models have been developed to evaluate the proposed bandwidth adaptation schemes. In the simulation experiments, a part from the traditional performance metrics of wireless networks, e.g. call blocking probability and handoff dropping probability; several new utility based performance metrics are also introduced. Simulation results have clearly demonstrated the superior performance of the proposed bandwidth adaptation schemes by comparing them with some existing ones. W e studied three routing protocols AODV, DSR and TORA. It investigates the factors affecting the performance criteria and working architecture of Ad hoc on-demand Distance Vector (AODV), Dynamic Source Routing (DSR) and Temporally Ordered Routing Algorithm (TORA). The simulation results show that throughput for AODV is better than both DSR and TORA by 50%.
Index Terms- AODV, TORA, DSR, MANET, QoS, Simulation, Hotspots.
—————————— ——————————
1. Introduction:
reliability, scalability, effectiveness,
IJSER
There is several challenge issue for future wireless
mobile communications, including more efficient
utilization of the available bandwidth, lower
power consumption, QoS-guarantee provisioning, as well as killer applications and service that can further lift the industry. In particular, wireless network architectures and protocols that can achieve higher throughput are urgently demanded since the radio frequency bands available for wireless networks are limited and the number of mobile users and their bandwidth demands are still rapidly increasing. Also, energy is a limited resource for mobile users since mobile devices are powered by battery. Moreover, QoS provisioning is crucial to future wireless networks since voice and multimedia will be among the most important applications for them, while mobility and the fluctuation of bandwidth requirement due to handoffs make it challenging to guarantee QoS in such networking environments.
In packet-switched networks, QoS is affected by various factors, which can be divided into “human” and “technical” factors. Human factors include: stability of service, availability of service, delays, user information. Technical factors include:
maintainability, grade, etc.
Many things can happen to packets as they travel from origin to destination, resulting in the following problems as seen from the point of view of the sender and receiver:
Low throughput
Due to varying load from other users sharing the same network resources, the bit rate (the maximum throughput) that can be provided to a certain data stream may be too low for real-time multimedia services if all data streams get the same scheduling priority.
Dropped packets
The routers might fail to deliver (drop) some packets if their data is corrupted or they arrive when their buffers are already full. The receiving application may ask for this information to be retransmitted, possibly causing severe delays in the overall transmission.
Errors
Sometimes packets are corrupted due to bit errors caused by noise and interference, especially in wireless communications and long copper wires.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 675
ISSN 2229-5518
The receiver has to detect this and, just as if the packet was dropped, may ask for this information
to be retransmitted.
Latency
It might take a long time for each packet to reach its destination, because it gets held up in long queues, or takes a less direct route to avoid congestion. This is different from throughput, as the delay can build up over time, even if the throughput is almost normal. In some cases, excessive latency can render an application such as VoIP or online gaming unusable.
Jitter
Packets from the source will reach the destination with different delays. A packet's delay varies with its position in the queues of the routers along the path between source and destination and this position can vary unpredictably. This variation in delay is known as jitter and can seriously affect the
quality of streaming audio and/or video.
an appropriate shape for each class of traffic according to its adaptive characteristics.
• A novel utility-maximization bandwidth adaptation scheme is proposed from the perspective of network operators. Depending on the network load, the utility-maximization scheme dynamically degrades or upgrades the allocated bandwidth of ongoing calls to maximize the total utility of all calls in the network.
• A novel utility-fair bandwidth adaptation
scheme is proposed from the perspective of
end-users. The scheme aims to treat end-users in a fair manner, i.e. it enables all ongoing calls in each individual cell of the network to receive fair utilities. It solves the utility unfair distribution problem caused by the utility- maximization bandwidth adaptation scheme.
• A novel utility-based multi-objective
bandwidth adaptation scheme is proposed from the perceptive of both network operators
and end-users. As mentioned earlier,
IJSEmultimediRa traffic is classified into different
Out-of-order delivery
When a collection of related packets is routed through a network, different packets may take different routes, each resulting in a different delay. The result is that the packets arrive in a different order than they were sent. This problem requires special additional protocols responsible for rearranging out-of-order packets to an isochronous state once they reach their destination. This is especially important for video and VoIP streams where quality is dramatically affected by both latency and lack of sequence.
Contribution:
The major contributions of the paper are summarized as follows:
• Utility functions are formulated explicitly for multimedia traffic so that they can be applied to the bandwidth adaptation in wireless networks. The advantage of using utility functions is that they can capture the adaptability of multimedia applications and empower end-users to give guidance on their perceived QoS. The Paper classifies multimedia traffic into different classes and formulates the utility function with
classes according to their adaptive
characteristics. It is assumed that each traffic class contains one or more groups of calls, and all calls within the same group have the same bandwidth requirements and utility function. The proposed scheme is designed to meet two objectives in the preference order: 1) All calls within the same group receive fair utilities; and
2) the total utility of all different groups of calls
is maximized.
• Several new utility-based performance metrics
including average cell utility, average call degradation ratio, utility fairness deviation and average intra group utility fairness deviation are introduced to evaluate the performance of the proposed bandwidth adaptation schemes.
2. Problem Statement:
This paper investigates the fundamental issues found in wireless ad hoc networks i.e. Mobile Ad hoc NETwork (MANET: a network of mobile devices connected by wireless which is self- configuring infrastructureless network, Where Each device is free to move independently in any direction, and will therefore change its links to other devices frequently.) First, we address the
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 676
ISSN 2229-5518
problem of quality of service in MANETs. We address the issue of congestion conditions in
wireless ad hoc networks called ‘hotspots’. We observed the hotspots in the process of studying the QoS issues.
After thorough investigation and detailed analysis
of extensive simulation data, it is determined that
these conditions can be prevented, identified, and mitigated (when created) through fairly simple manipulations at the routing and MAC layer. We argue that Hotspot Mitigation Protocol (HMP) is one of the generic approaches to address hotspots in MANET.
Although substantial work has been done for
quality of service in the Internet, none of the existing proposals can be readily applied to MANETs due to limitations and constraints intrinsic to MANETs. Supporting QoS requires the link state information such as delay, bandwidth, cost, loss rate, and error rate to be available and manageable. However, satisfying these
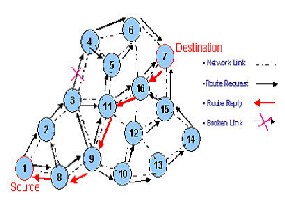
requirements is very challenging in MANET
via a similar route discovery process. However, AODV adopts a very different mechanism to
maintain routing information. It uses traditional routing tables, one entry per destination. This is in contrast to DSR, which can maintain multiple route cache entries for each destination. Without source routing, AODV relies on routing table entries to propagate an route reply (RREP) back to the source and, subsequently, to route data packets to the destination. AODV uses sequence numbers maintained at each destination to determine freshness of routing information and to prevent routing loops. All routing packets carry these sequence numbers.
because the quality of a wireless link can abruptly change with the dynamic of surrounding circumstances.
The traditional QOS approaches are loosely based
on the virtual circuit model that requires explicit connection management and the establishment of hard-state in the network prior to communication. The virtual circuit model also assumes the route and the reservation between source-destination pairs remain fixed for the duration of a session. However, the virtual circuit lacks the intrinsic flexibility needed to adapt to the dynamics found in MANETs where the path and reservation need to dynamically respond to topology and resource changes in a timely manner.
3. AODV, DSR, TORA Routing
Protocols:
For make a scheme or protocol that provides better QoS to the cellular networks (mobile phones), we describe AODV, DSR, TORA:
Ad hoc On Demand Distance Vector
(AODV) Routing
AODV shares DSR’s on-demand characteristics in that it also discovers routes on an as needed basis
An important feature of AODV is the maintenance of timer-based states in each node, regarding utilization of individual routing table entries. A routing table entry is expired if not used recently. A set of predecessor nodes is maintained for each routing table entry, indicating the set of neighboring nodes which use that entry to route data packets. These nodes are notified with route error (RERR) packets when the next-hop link breaks. Each predecessor node, in turn, forwards the RERR to its own set of predecessors, thus effectively erasing all routes using the broken link. In contrast to DSR, RERR packets in AODV are intended to inform all sources using a link when a failure occurs. Route error propagation in AODV can be visualized conceptually as a tree whose root is the node at the point of failure and all sources using the failed link as the leaves.
AODV maintain that it is a pure distributed on- demand approach that minimizes routing table information. However, this also means, that more route requests are generated. This compounded with the periodic ‘hellos’ can increase routing
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 677
ISSN 2229-5518
overhead. The advantage of AODV is its use of destination numbers and replies to the first
arriving RREQ implies that AODV favors the least congested route instead of the shortest route. Furthermore, another advantage is that the drafted standard supports both unicast and multicast packet transmissions.
Dynamic Source Routing (DSR)
The key distinguishing feature of DSR is the use of source routing. That is, the sender knows the complete hop-by-hop route to the destination. These routes are stored in a route cache. The data packets carry the source route in the packet header. When a node in the ad hoc network attempts to send a data packet to a destination for which it does not already know the route, it uses a route discovery process to dynamically determine such a route. Route discovery works by flooding the network with route request (RREQ) packets. Each node receiving an RREQ rebroadcasts it, unless it is
the destination or it has a route to the destination
and route caching. No special mechanism to detect routing loops is needed. Also, any forwarding
node caches the source route in a packet it forwards for possible future use.
DSR has the advantage that no routing tables must be kept to route a given packet, since the entire route is contained in the packet header. The caching of any initiated or overheard routing data can significantly reduce the number of control messages being sent, reducing overhead. Using only triggered updates furthers that same goal.The primary disadvantages are two-fold. DSR is not scalable to large networks. The Internet Draft acknowledges that the protocol assumes that the diameter of the network is no greater than 10 hops. Additionally, DSR requires significantly more processing resources than most other protocols. In order to obtain routing information, each node must spend much more time processing any control data it receives, even if it is not the
intended recipient.
in its route cache. SIuch a nJode replies tSo the RREQ ER
with a route reply (RREP) packet that is routed
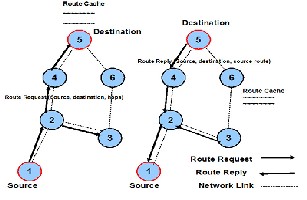
back to the original source. RREQ and RREP packets are also source routed. The RREQ builds up the path traversed across the network. The RREP routes itself back to the source by traversing this path backward. The route carried back by the RREP packet is cached at the source for future use.
If any link on a source route is broken, the source node is notified using a route error (RERR) packet. The source removes any route using this link from its cache. A new route discovery process must be initiated by the source if this route is still needed. DSR makes very aggressive use of source routing
Temporally Ordered Routing Algorithm
(TORA)
TORA is a distributed routing protocol based on a
‘link reversal’ algorithm. It is designed to discover routes on demand, provide multiple routes to a destination, establish routes quickly, and minimize communication overhead by localizing algorithmic reaction to topological changes when possible. Route optimality (shortest-path routing) is considered of secondary importance, and longer routes are often used to avoid the overhead of discovering newer routes.
The actions taken by TORA can be described in terms of water flowing downhill towards a destination node through a network of tubes that models the routing state of the real network. The tubes represent links between nodes in the network, the junctions of tubes represent the nodes, and the water in the tubes represents the packets flowing towards the destination. Each node has a height with respect to the destination that is computed by the routing protocol. If a tube between nodes A and B becomes blocked such that water can no longer flow through it, the height of
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 678
ISSN 2229-5518
A is set to a height greater than that of any of its
remaining neighbors, such that water will now flow back out of A (and towards the other nodes that had been routing packets to the destination via A).
from the sender to the destination in order of decreasing height. When a node discovers link failure, it sets its own height higher than that of its neighbors, and issues an Update to that effect reversing the direction of the link between them. If it finds that it has no downstream neighbors, the destination is presumed lost, and it issues a Clear packet to remove the invalid links from the rest of the network.
Comparison between AODV, DSR, TORA:

IJSEThe implemenRtation of AODV, DSR and TORA in
When a node discovers that a route to a destination
is no longer valid, it adjusts its height so that it is a local maximum with respect to its neighbors and transmits an UPDATE packet. If the node has no neighbors of finite height with respect to this destination, then the node instead attempts to discover a new route as described above. When a node detects a network partition, it generates a CLEAR packet that resets routing state and removes invalid routes from the network.
For a given destination, TORA uses a somewhat arbitrary ‘height’ parameter to determine the direction of a link between any two nodes. As a consequence of this multiple routes are often present for a given destination, but none of them are necessarily the shortest route. For a node to initiate a route, it broadcasts a Query to its neighbors. This is rebroadcast through the network until it reaches the destination, or a node that has a route to the destination. This node replies with an Update that contains its height with respect to the destination, which is propagated back to the sender. Each node receiving the Update sets its own height to one greater than that of the neighbor that sent it. This forms a series of directed links
this simulation is to mainly evaluate End-to-end
delay, Throughput and Media access delay.
End-to-end delay “The time it takes for a data packet to traverse from the source node to the destination node. End-to-end delay evaluates the ability of the protocol to use the network resources efficiently”·
Throughput “The amount of the data can be
transferred from one place to another or processed in a specific period of time”.
Media access delay “Describes the delay resulting from accessing the media during the data communication”.
4. Simulation Environment:
The simulation environment uses the NS-2 simulator and its wireless extensions. In the following section, we evaluate the impact of traffic load on AODV, DSR and TORA routed networks:
End-to-end delay (4 nodes)
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 679
ISSN 2229-5518
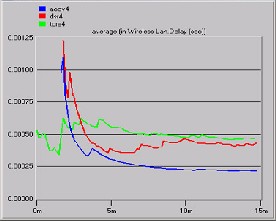
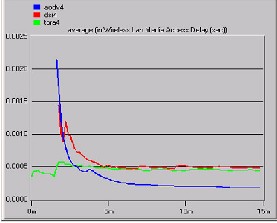
Fig A
End–to-end delay parameter is simulated here for four mobile nodes with different routing protocols as shown in Fig A. The graph shows that AODV has a rise in end-to-end delay during the start of simulation because of ideal broadcast, but with the passage of time, it becomes stable and the
delay is reduced, same behavior representation
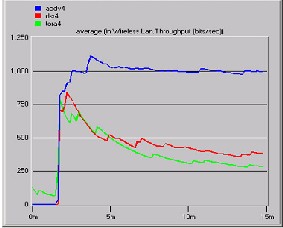
Fig B
It can be seen from Fig B. With four nodes employing TORA, respond instantly after starting the simulation whereas AODV remains with a high, almost constant throughput, which is nearly
1100 bits/sec. The throughput for DSR and
TORA increased up to 800 bits/sec accordingly
then followed by a drop in throughput. The drop
IJSER
from DSR shows its involvement in cache table
addressing. TORA behaved quite stable because of
its design to recover a route quickly and that is
why it sustains a more stable and an average delay. The end-to end delay varies from 0.00100 to
0.00025 for AODV after maintaining routing information. DSR started with highest delay of
0.00125, but after 3 minutes of simulation it drop
to minimal level of delay. Once AODV and DSR initialized, they easily manage their data traffic and touch the lower limits of End-to-end delay as compare to TORA.
Throughput (4 nodes)
in traffic throughput by DSR and TORA compared
to the AODV can be deduced by taking the difference in the traffic dropped by the AODV and the DSR or TORA results in the graph. This dominates the feature of AODV regarding throughput.
Media access delay (4 nodes)
Fig C
This is providing the results for the response for a received packet with a routing, Address Resolution Protocol (ARP) and control packet reply
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 680
ISSN 2229-5518
transmitted by MAC layer. It considers both routing overhead and the MAC control overhead.
Like normalized routing load, this metric also accounts for transmission at every hop. The routing load metric evaluates the efficiency of routing protocol. TORA is more stable because of its linear behavior as simulation results as in Fig C shows that AODV and DSR both took first two minutes of simulation for transmitting on the network. Gradually both protocols approach TORA for media access delay. All of the protocols are in the limits of applicable media access delay because the number of nodes are few.
their data traffic and touch the lower limits of
End-to-end delay as compared to TORA. So
TORA is going to cause more delays with respect to number of nodes.
Throughput (20 nodes)
End-to-end delay (20 nodes)
IJSEFig E R
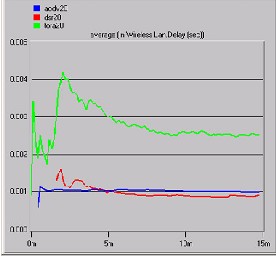
Fig D
End–to-end delay parameter is simulated here for twenty mobile nodes with different routing protocols as shown in Fig D. It is shown from graph that AODV shows quite different behavior as compared to simulation results in Fig A. Same behavior representation from DSR shows its involvement in cache table addressing. TORA behaved quite differently than expected, with high end-to-end delay because it is not well acquainted with supporting a fairly large number of nodes. The end-to end delay varies for
0.004 to 0.003 which is not an issue of attention,
but this graphical behavior shows the stability of AODV and DSR. The DSR begins with stable delay compared to the others that do not. Once AODV and DSR initialized, they easily manage
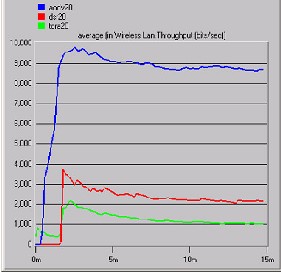
Fig E. shows twenty ad hoc nodes TORA respond
instantly after starting simulation, AODV raise to highest throughput linearly, which is nearly
10000 bits/sec. DSR and TORA reached up to
3000 bits/sec accordingly, which shows the traffic throughput for AODV goes to average
9000 bits/sec which is 3 times the throughput of other routing protocols. This dominates the feature of AODV regarding throughput and shows a stable traffic in great number of nodes. DSR simulation result present more efficient and better throughput as comparing to TORA. But noticeably all protocols stayed in consistent level of throughput.
Media access delay (20 nodes)
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 681
ISSN 2229-5518
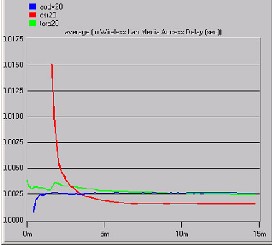
Fig F
In previous results for four nodes, DSR showed
less medium access delay but with twenty nodes it presents a leading medium access delay proportion. Whereas on the other hand, AODV starts and continues with a more or less
When number of nodes are 20
constant behavior, which leads to the point that
the AODV is an efficient media access protocol for a large number of nodes. The number of packets involved that are contributing to the effects of media access delay number of routing and control message packets are all transmitted by WLAN MAC layer for each data packet. The routing load metric evaluates the efficiency of routing protocol. TORA is also stable because of its smart link layer behavior, outcome shown in Fig F.
Here the medium access delay is defined as a
function of a routing protocol and traffic characteristics. Therefore, when comparing the protocols, it is necessary to compare them based on the same traffic parameters.
That is why all three routing protocols are simulated with same metrics. There are some other important considerations like channel characterization, power consumption, and time variation. AODV is very supportive regarding power consumption and fading particularly in large networks.
Comparative Study:
When number of nodes are 4
• TORA is going to cause more delays with
respect to no. of nodes.
• AODV shows a stable traffic in great no. of nodes regarding throughput.
• DSR simulation result present more efficient and better throughput as comparing to TORA.
• AODV is an efficient Media Access Protocol for
large number of nodes and is very supportive regarding power consumption and fading particularly in large networks.
5. Future Work:
With multiple air-interface support capabilities and higher cell densities, future cellular networks will offer a diverse spectrum of user services. The resulting dynamics in traffic load and resource demand will challenge present control loop algorithms. In addition, frequent upgrades in the
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 682
ISSN 2229-5518
network infrastructure will substantially increase the network operation costs if done using current
optimization methodology. This motivates the development of dynamic control algorithms that can automatically adjust the network to changes in both traffic and network conditions and autonomously adapt when new cells are added to the system. Bell Labs is pursuing efforts to realize such algorithms with research on near-term approaches that benefit present third-generation (3G) systems and the development of control features for future networks that perform dynamic parameter adjustment across protocol layers. Notwithstanding its widespread use, the static optimization approach is increasingly approaching its limits.
The growth of the wireless customer base and the introduction of various new data services mandate the consideration of new objectives such as throughput, delay, latency, and quality of service
(QoS). Indeed, the migration to IP Multimedia
aggregate demand variations, one observes that they typically occur on an interval from
intermediate to long-time scales (i.e., seconds and above). One further observes the coexistence of both predictable (periodic) and unpredictable (random) variations in aggregate demand. Predictable variations possess characteristic times of order hours, days, and weeks, and they can possess inter cell correlations.
Random fluctuations occur on practically all time scales, but because of intrinsic averaging, they tend to be most pronounced at shorter time scales.
They are typically uncorrelated between cells. Similar characterization occurs when one looks at spatial variations of the users within and between cells, which also contribute to demand fluctuations.
Control Algorithms for Future Network
One class of dynamic control mechanisms in future
IJSER
Subsystems (IMS) will promote the continuous
development of new services with different
resource requirements, QoS demands, and traffic characteristics. Furthermore, data services introduce demand fluctuations that are intrinsically larger than they are for voice services. The multidimensional nature of demand, its temporal dependence, and its increased dynamic range render optimization strategies based on a peak (albeit composite) loading progressively less effective at efficiently allocating and managing network resources. Additionally, the demand for increasing data rates and the falling costs for network hardware will drive network architectures toward micro-cellular structures. This development will create frequent infrastructure upgrades with the demand for fast, autonomous, and inexpensive cell integration.
Demand fluctuations have widely different origins,
correlations, and characteristic times, with important implications for how best to address them. Channel fluctuations (i.e., fast and shadow fading) for individual users typically range from milliseconds to tens of seconds. Arrival, departure, and handoff/ swap times for individual voice and data users typically inhabit the range between a few seconds to tens of minutes. When looking at
networks defines algorithms that respond to
fluctuations in both traffic load and channel
conditions while respecting network-wide
performance objectives.
For the development of this class of control mechanisms, it is important to understand the origins of fluctuations in traffic load and channel conditions, their impact on network resources, and the advantages and shortcomings of present mechanisms that were not designed to tackle dynamic phenomena comprehensively.
For example, fluctuations in traffic load and channel conditions translate into fluctuations in the demand for resources, which in turn affect network and/or cell capacity and QoS due to the limitation of resource supplies. Current networks provide a limited set of control algorithms that attempt to distribute the available resources appropriately. They reside at different protocol layers and network elements and perform operations locally. Examples for such control algorithms are power control, scheduling, handover, channel assignment, and congestion control.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 683
ISSN 2229-5518
Local control routines have the advantage that they can react quickly.
An example methodology we have used follows three discrete steps:
• Formulation of the optimization task. This addresses the determination of the adjustment parameters and network-wide objectives. Objectives need to be selected carefully since they critically determine the gain and relevance of the proposed mechanisms in the final implementation.
• Comparative simulation studies. A mathematical model is developed for the network objectives and with respect to the particular technologies of interest. This step allows an evaluation via simulation of the potential gains that are achievable through network optimization as compared to the (best)
performance of current systems. The latter is
paying particular attention to the performance of these networks.
The approach discussed in this paper looks promising in terms of the performance results presented. Our simulation results show the benefit of our framework under diverse traffic, and channel conditions. Currently we are implementing a number of MANET routing protocols using the NS2 simulator.
We have further demonstrated that real-time measurements are a fundamental ingredient to the development of dynamic control mechanisms since they reveal the inefficiencies in cellular networks and provide information on actual traffic characteristics and user behaviour. In addition, they identify important interrelations among network properties, such as per-call QoS, resource demand, and traffic load, which in turn drive the development of future control algorithms.
Information on actual traffic behaviour is already
IJSER
obtained through detailed dynamic simulations
that can capture the network-related aspect of
the objective being optimized. Ideally, the modelling should capture the relevant time scale of operation for the optimization process, which should represent an optimistic limit to what is achievable under best circumstances in practical implementations.
• Feature development. Feature development can
be guided by the knowledge gained from the
mathematical modelling and simulation stages. For example, a centralized optimization solution may be realized in a distributed form only, which allows approximating the optimum solution without excessive communication. Alternatively, good candidate algorithms can be “guessed” based on observable patterns in the optimum solution based on engineering experience.
6. Conclusion:
In this Paper, we have presented the design, implementation, and evaluation of the AODV, DSR, TORA QoS framework that supports the delivery of adaptive services in mobile ad hoc networks. We have evaluated our QoS framework
being applied in current dynamic network trials
for optimization of recurring traffic patterns.
ACKNOWLEDGEMENT:
I would like to dedicate my acknowledgment of gratitude toward the following important guides and contributors:
First and foremost, I would like to thank Dr. Vijay
Kumar and Ms. Khushboo Khanna for his support and encouragement. They kindly read my paper and offered invaluable detailed advices.
Second, I would like to thank Mr. Nishith Anand
and Mr. Vishnu Dhakad to read my paper and to
provide valuable advices on grammar, organization, and the theme of the paper as well as all the other professors who have taught me about the topic over the past two years of my pursuit of the master degree.
Finally, I sincerely thank to my parents, family, and friends, who provide the advice and financial support. And thank you to Shipra, Itisha, Kamlesh Singodia for their support.
The completion of this research paper would not be possible without all of them.
REFERENCES:
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 684
ISSN 2229-5518
[01] A. Alwan, R. Bagrodia, N. Bambos, M. Gerla,
L. Kleinrock, J.Short, and J. Villasenor, “Adaptive Mobile Multimedia Networks,” IEEE Personal Communications, vol. 3, no. 2, pp. 34-51, April
1996.
[02] T. Kwon, Y. Choi, and S.K. Das, “Bandwidth
Adaptation Algorithms for Adaptive Multimedia Services in Mobile Cellular Networks,” Wireless Personal Communications, vol. 22, no. 3, pp.337-
357, Sept. 2002
[03] J. Gomez, A.T. Campbell, and H. Morikawa,
“A Systems Approach to Prediction, Compensation and Adaptation in Wireless Networks,” Proceedings of the 1st ACM International Workshop on Wireless Mobile Multimedia, pp. 92-
100, Oct. 1998.
[04] R. Parry, “Overlooking 3G,” IEEE Potentials,
vol. 21, no. 4, pp. 6-9,Oct./Nov. 2002.
[05] J.E. Padgett, C.G. Gunther, and T. Hattori,
“Overview of Wireless Personal Communications,” IEEE Communications Magazine, vol. 33, no. 1, pp.
28-41, Jan. 1995.
[12] B. Li, D. Xie, S. Cheng, J. Chen, P. Zhang, W.
Zhu, and B. Li, “Recent Advances on TD-SCDMA
in China,” IEEE Communications Magazine, vol.
43, no. 1, pp. 30-37, Jan. 2005.
[06] A.-L. I. Semeia. Wireless Network Performance Analysis for Adaptive Bandwidth Resource Allocations. PhD Paper, Stevens Institute of Technology, USA, 2003.
[07] N.R. Prasad, “GSM Evolution Towards Third
Generation UMTS/IMT2000,” Proceedings of the IEEE International Conference on Personal Wireless Communication, pp.50 - 54, Feb.1999.
[08] Z. Zvonar, P. Jung, and K. Kammerlander.
GSM: Evolution Towards 3rd Generation Systems. Kluwer Academic Publishers, 1999
[09] T. Ojanpera and R. Prasad, “An Overview of
Third-Generation Wireless Personal Communications: A European Perspective,” IEEE Personal Communications, vol. 5, no. 6, pp. 59-65, Dec. 1998.
[10] N. Padovan, M. Ryan, and L. Godara, “An
Overview of Third Generation Mobile Communications Systems: IMT-2000,” the IEEE Region 10 International Conference on Global Connectivity in Energy, Computer, Communication and Control (TENCON ’98), vol. 2, pp. 360-364, Dec. 1998.
[11] D.N. Knisely, S. Kumar, S. Laha, and S.
Nanda, “Evolution of Wireless Data Services: IS-95 to CDMA2000,” IEEE Communications Magazine, vol. 36, no. 10, pp.140-149, Oct. 1998.
IJSER © 2013 http://www.ijser.org








