International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 708
ISSN 2229-5518
Color Based Segmentation Iris image for Secure
Distributed Systems
Ameer A. Mohammed Baqer, Hind Rostom Mohammed
Abstract— Credit card fraud is one of the crimes especially when it is used for web-based transaction. In this paper, a technical solution using Efficient and fast Iris authentication technique is proposed for protecting identity theft in e-commerce transactions. Therefore, this research proposes a web-based architecture which uses a combination of Image Processing and secure transmission of customers’ Iris templates along with credit card details for decreasing credit card frauds over Internet.
Iris image detection method based on color based segmentation and morphological operation is proposed. The color based segmentation takes in only two color spaces HSI and YCrCb, instead of three color spaces, followed by the morphological operations and a template matching. For each stage a novel algorithm which combines pixel and region based color segmentation techniques is used. The experimental results confirm the effectiveness of the proposed algorithm.
Index Terms— Secure Distributed Systems, Iris mage detection, Image Color, Morphology Operations, HSI color space, YCbCr color space, Components, Template matching.
—————————— ——————————
n reality, the Web represents a huge distributed system that appears as a single resource to the user available at the click
The paper is organized as follows; Section 2 deals with the
IJSER
of a button. There are several definitions and viewpoints on
what distributed systems are. Color is defines a distributed
system as “a system in which hardware or software compo-
nents located at networked computers communicate and co-
ordinate their actions only by message passing” [1]; and
Tanenbaum defines it as “A collection of independent com-
puters that appear to the users of the system as a single com- puter”[2]. Leslie Lamport – a famous researcher on timing, message ordering, and clock synchronization in distributed systems once said that “A distributed system is one on which I
cannot get any work done because some machine I have never heard of has crashed“ reflecting on the huge number of chal- lenges faced by distributed system designers. Despite these challenges, the benefits of distributed systems and applica- tions are many, making it worthwhile to pursue.
Various types of distributed systems and applications have been developed and are being used extensively in the real world. In this article, we present one of the main Application of distributed systems that is e-commerce transactions where in this paper we propose a web-based architecture to use en- crypted Iris pattern as biometric attribute for authentication of a customer for e-commerce transactions which includes a se- cure biometric templates transmission and a high performance algorithm for Iris recognition as human identification.
————————————————
• Hind Rostom Mohammed is currentlyAssistant Professor and Head of computer science department in Faculty of Mathematical and Computer Sciences at the University of kufa, Iraq. E-mail: hindrustum.shaaban
@uokufa.edu.iq
Physiological Biometrics, Section 3 deals with Proposed web-
based architecture using biometric authentication, Section 4
deals with the color based segmentation where different color
spaces, HSI and YCrCb , Section 5 deals with the Iris Feature
Extraction , Coding and Match, Section 6 deals with the Exper-
imental Results, section 7 deals with the design Secure Tem-
plate Transmission Schema 7.1. Cryptography Algorithm based on Chaos Theory, last section 8 ends the paper with conclusion.
Physiological biometrics depends upon the physical appear- ance of the human body or shape of the human like nose, chin, eyes, face and lips etc. Face recognition, finger print, iris tech- nology, retina technology, hand geometry, odour or DNA de- oxyribonucleic acid etc. are the examples of physiological bi- ometrics as shown in fig1.
Fig.1. Biometric traits
The human iris is an annular part between pupil (black por- tion) and cornea shown in. Iris is an inner organ part of hu-
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 709
ISSN 2229-5518
man body. The structure of human Iris contains five layers of fiber like tissues. These tissues are very complex and reveal in various forms. The surface of iris also contains a complex structure such as crystals, thin threads, spot con caves, radials, furrows, stripes etc. Iris is a place where our nerve systems are situated and it gives information about human body [10].
Fig.2. Iris Recognition Biometric
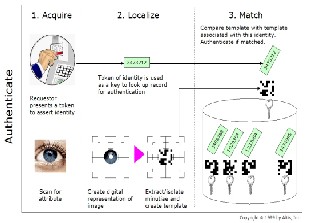
In this section we explain the proposed architecture for our system, that system contains two subsections: Image pro- cessing and secure template transmission scheme. In this pa- per, we are going to introduce good technique to choose shortest reliable path to sending Biometric Authentication
The encryption key that is sent to the server Issuer side to decrypt the iris template.
The steps for processing the biometric authentication packets are explained in fig4.
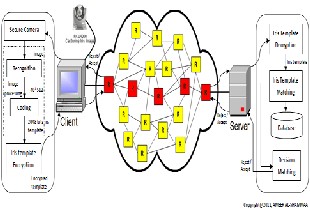
Fig.3 Proposed Web-based system for e-commerce transaction
packet to decrease the forgetting of this packets and the time that is require to arriving the packet from the source to desti- nation, also we explain the content of the biometric authentica- tion packet in our proposed system that is used fig2.
In this research, a technical solutions is proposed to prevent the losing biometric authentication packet and decrease the time that is require to sending the packet to destination, also this proposed system used to prevent credit card fraud in e- commerce transactions by using an Iris authentication tech- nique. This method necessitates the existence of standardized Iris image capture and encryption software along with the web camera that is built in the recent computer systems. Here, iris recognition algorithm is used to extract key characteristic features of Iris pattern of an individual. These features are encrypted using chaotic maps. The result of such a combina- tion provides not only a secure transmission of credit card details, but also achievement of high level authentication. A web-based architecture is proposed for implementing this so- lution. While issuing a credit card, the Iris details of an indi- vidual will be stored along with the credit card number and other personal details in the issuing agency’s database. A software need to be present in all the client systems so that while doing e-commerce transactions, the Iris image of the individual can also be captured, encrypted and sent along with the name, credit card number, and expiration date. At the time of transaction the Iris image of the customer is captured using a web camera built in the client system. The Iris image is preprocessed, normalized, enhanced, and the key features of the Iris are extracted using our high performance algorithm, fig3.
A biometric Authentication packet contains two parts:
Iris template that is encrypted by chaotic maps.
Fig.4 Biometric Authentication Process
Iris recognition has recently emerged as one of the top bio- metric authentication methods due to its accuracy and out- standing identification efficacy. It is also commonly believed that the pattern of iris tissue is highly stable throughout the human live, although recent scientific notifications start to surprisingly suggest the opposite hypothesis [11].
Segmentation is subdividing an image into its constituent re- gions or object. The level up to which the subdivision is car- ried out depends on the problem being solved. A human Iris color model is used to decide either a pixel is Iris color or non- Iris-color [5]. This model is characterized by a classification algorithm and color space used to represent pixel color. Color spaces used in Iris color segmentation include YCbCr, HSV and RGB [6]. A wide variety of them have been applied to the problem of Iris color modeling (Iridian Technologies). Because color is a powerful fundamental feature and because it is, un- der constant illumination, almost invariant to scale, orienta-
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 710
ISSN 2229-5518
tion and partial occlusion, we propose a method using color information to extract efficiently human Iris in images cap- tured in complex environmental conditions. Iris-color image segmentation is computationally inexpensive and is robust to cluttered background [7]. In this research, we use the HSV (hue, saturation, value) color representation because it is com- patible with the human color perception and because previous work has shown that this color space is one of the most adapted for Iris-color detection [12]. The HSV color space is obtained by a non-linear transformation of the fundamental RGB color space. We use the cone representation of the HSV color space, where H, S and V are all normalized in the range [0,1]. The H and S components represent the chromatic infor- mation, while V represents the luminance information [6]. In the literature [13],[14], there are many color based face detec- tion algorithm, but the proposed algorithm uses the two color spaces only namely, HSI and YCbCr. The bounding ranges calculated for the values of H, Y, Cb and Cr were used to gen- erate the binary images.
Hue-saturation based color spaces were introduced when there was a need for the user to specify color properties nu- merically. Describe color with intuitive values, based on the artist’s idea of tint, saturation and tone. Hue defines the domi- nant color (such as red, green, purple and yellow) of an area;
saturation measures the colorfulness of an area in proportion
chrominance components makes this color space attractive for Iris color modeling. In pursuing this goal, we looked at three color spaces that have been reported to be useful in the litera- ture, HSV and YCrCb spaces, as well as the more commonly seen RGB space. Below we will briefly describe what we found and how that knowledge was used in our system [9].
The possibility that the uniqueness of Iris of the eye could be used as a kind of optical fingerprint for personal identifica- tion was first suggested by ophthalmologists. However, John Daugman was the first person to use this idea for human iden- tification as an algorithm [8], [9], [10], [11]. In the previous papers, the extensive amount of research has been done on Daugman’s algorithm [12], the Boles's algorithm [14] and the Arian's and Wilds algorithm [15]. In this paper we are going to introduce an algorithm to improve the Daugman’s algorithm in both speed and accuracy.
Every Iris recognition algorithm consists of 3 main sections;
these sections are as follow:
1. The image is preprocessed to detect and separate Iris from the whole image.
2. Features representing the Iris patterns are extracted as a code.
3. Decision is made by means of matching.
to its brightness. Many applIicationsJuse the HSIScolor model. ER
Machine vision uses HSI color space in identifying the color of
different objects. Image processing applications such as histo-
gram operations, intensity transformations and convolutions
operate only on an intensity image. These operations are per-
formed with much ease on an image in the HIS color space.
For the HSI being modeled with cylindrical coordinates.
Iris color classification in HSI color space is the same as YCbCr
color space but here the responsible values are hue (H) and
saturation (S) [12]. YCrCb is an encoded nonlinear RGB sig-
nal, commonly used by European television studios and for image compression work. Color is represented by luma (which is luminance, computed from nonlinear RGB. RGB components convert to YCbCr components by Equation:
Y=0.299R+0.587G+0.114B Cb=-0.169R- 0.332G+0.500B
Cr=0.500R-0.419G-0.081B (1)
Different plots for Y, Cb and Cr values for face and non-Iris pixels were plotted and studied to find the range of Y, Cb and Cr values for face pixels. After experimenting with various thresholds the best result were found by using the following rule for detecting the Iris pixel:
135<Y<145
100<Cb<110
140<Cr<150 (2)
The results are shown in Fig .5 (A): Original Iris Image, (B) YCbCr Iris Image and results are shown in Fig.6 (A): Original Iris Image with Y Plane, Cb Plane and Cr Plane. The transfor- mation simplicity and explicit separation of luminance and
An iris image contains much detail texture, the texture is com- posed by many shape blocks such as strip and speckle, the gray differences are big and distribute unevenly, and these blocks with irregular shape can be as distinguish characteris- tics for iris recognition [16].
Firstly we need to determine the collective and effective cod- ing region of the entering iris and the registering iris, this re- gion does not contain noise such as eyelash, eyelid and facula. We suppose vertical coordinates of D point of the entering iris and the registering iris in the normalized image are rD Enroll , rD Register respectively, and determine the smaller value as rD Match between two values x1,xr, of the entering iris and the registering iris in the normalized image are x1Enroll , xrEnroll and x1Register , xrRegister respectively, determine the bigger value as x1Match , x1Enroll between and x1Register, and determine the smaller value as between xrMatch , xrEnroll between and xrRegister . So we determine collective and effective texture region of the entering iris and the registering iris.
Considering the block characteristics of iris texture, it first makes sub-block for the image, the size of the block is M*N(M and N are integers) and ensures not overlap between each block. The number of block is (ceil((xrMatch - x1Match)/N))*(ceil(xDMatch /M)) in the collective and effec- tive area of entering iris and registering iris, the horizontal number of block is Hnum= ceil((xrMatch - x1Match)/N) , the vertical number of block is Vnum=(ceil(xDMatch /M)).
In order to realize the compression code, it accumulates all the
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 711
ISSN 2229-5518
gray values in each block; the average of this accumulation is the gray value of the center point. During the feature extrac- tion, it makes code by taking the center point of each block image as the basic feature point. This code method plays well in the compression; what is more, this cannot lose feature points. In the collective and effective area of iris image, con- sidering the texture characteristics which are the strength of the edge and direction information of texture it takes the basic feature point as the center point and considers the eight neighborhood of each center point, these eight points corre- spond to the four directional texture of the center point such as 45°, 90°, 135° and 180°. Each direction corresponds to two adjacent points, the neighborhood relationship is shown in Table 1. In each direction it calculates the gray differences be- tween two adjacent points and the center point respectively, if two gray differences are bigger than zero, the corresponding code bit procodek( i , j) of the center point in this direction sets "1", otherwise sets "0". K(45,90,135,180) corresponds the direc- tion respectively.
TABLE 1
THE RELATIONAL OF ADJACENT POINTS
![]()
In the collective and effective area, we make match to the en- tering iris and registering iris. The corresponding codes of the entering iris and registering iris are Registercodei , Enrollcodei which correspond to the code of each directional output value Directiona respectively. i=1,2,3,4;
a=45,90,135,180; i=1 corresponds to the directional code of 45 degree, i=2 corresponds to the directional code of 90 degree, i=3 corresponds to the directional code of 135 degree, i=4 cor- responds to the directional code of 180 degree.
When we compare with two iris codes, because the anterior normalized operation cannot solve the revolving invariable problem, we need to carry on certain revolving match for reg- istering iris and entering iris. The revolving can be compen- sated even the corresponding code of the registering iris and the entering iris cannot correspond completely. This article solves the revolving invariable problem in the normalized image, this may transform the revolving operation in the an- nular iris to the translation operation in the rectangular iris. The concrete method is as follows: when it compares with two iris codes, maintains the code of the registering iris motionless, and the code of the entering iris is translated several pixels to left or right along horizontal direction (because the angles of rotation of image is not big, translation pixels are small), it
Texture of 90°
calculates a match value with the registering iris code after![]()
IJSER
point
![]()
Then according to the formula (3) it calculates four directional output values of each basic feature point[16]:![]()
Direction180(i,j)=(I(i,j – 1)+ I(i,j + 1) – 2 * I(i,j))/2
Direction135(i,j)=(I(i+1,j – 1)+ I(i – 1,j + 1) – 2 * I(i,j))/2
Direction45 (i,j)=(I(i – 1,j – 1)+ I(i + 1,j + 1) – 2 * I(i,j))/2 (3) Direction90 (i,j)=(I(i – 1,j)+ I(i + 1,j) – 2 * I(i,j))/2
Among them , i=0,1,…., ceil((xr Match –x1 Match)/N)-1, j=0,1,…, (ceil(rD Match /M))-1, I(i,j) expresses the correspond- ing gray value of each basic feature point.
Finally, it eliminates the false feature points, the detail meth- od is as follows: it records the directional number K(45,90,135,180) with the maximal directional out value of each basic feature point According to formula (4) it makes bi- nary code for each basic feature point, if a directional code of each basic feature point is “1” and this directional out value is bigger than three other directional out values, this directional code is still “1”, three other directional codes are set “0”; oth- erwise this directional code is set “0”. It makes similar opera- tion for four directional codes of each basic feature point [16]:
![]() (4) Among them, a expresses the corresponding directional code bit,
(4) Among them, a expresses the corresponding directional code bit,
so it gets:
(ceil ((xr Match – x1 Match)/N))* (ceil(r DMatch /M))*4 bits code.
translating one pixel, after the translation ends, we keep the
maximum of all the match values as the final match value of
the registering iris and the entering iris.
The final match distance Md is as following:
(5)
When we carry on the recognition experiment, we weigh the algorithm with false acceptance rate (FAR), false rejection rate (FRR), equal error rate (EER), and correct recognition rate (CRR). Simultaneously we inspect the algorithm with the exe- cution time, including feature extraction time, match time. We use the CASIA in the iris database [9], 567 images, including
81 different irises of eyes, each eye had 7 8-bit images, and the resolution is 320×280. We carry on the recognition experi- ments 160461 times, the inter-class experiments was 158760, the intra-class experiments was 1701.
When the size of block is 3*4, the experimental result is best. The threshold of match distance is 0.22922, CRR=99.685%, FAR=0.313051%, FRR=0.293945%, namely the correct recogni- tion results are 159959 times, the false rejection results are 5 times, the false acceptance results are 497 times. We carry on the duplicated experiments for two previous mentioned methods in the same image samples, the experimental results are listed in Table 2.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 712
ISSN 2229-5518
The CRR of this article under the threshold value is slightly low- er than the Daugman’s algorithm, but is higher than Boles’s algo- rithm and Arian's algorithm.
TABLE 2
THE ACCURATE RECOGNITION RATE OF DIFFERENT ALGORITHM
prove the security and secrecy of the transmitted iris tem- plates. Secret keys are generated by the biometric image and used as the parameter value and initial condition of the chaot- ic map, and each transaction session has different secret keys to protect from the attacks. Two chaotic maps are incorporated for the encryption to resolve the finite word length effect and to improve the system’s resistance against attacks. Encryption![]()
is applied on Iris codes. To transmit securely of Iris codes in e- commerce transactions, we have used cryptography to achieve highly secure Iris code transmission [15], In the Fig. 5; we can see the Iris code before and after we applying the encryption.
![]()
![]()
Proposed 99.68 0.28 6.0 5.0 11.999
The name "Chaos theory" comes from the fact that the systems that the theory describes are apparently disordered, but Chaos theory is really about finding the underlying order in appar- ently random data. Chaos theory attempts to explain the fact
that complex and unpredictable results can and will occur in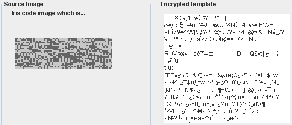
(a) (b)
Fig.5 a) Iris code Before Encryption. b) Iris code After Encryption
IJSER
systems that are sensitive to their initial conditions. In other
words, it is possible that a very small occurrence can produce
unpredictable and sometimes drastic results by triggering a
series of increasingly significant events. Among the most
promising applications of Chaos theory is its use in the field of
“chaotic encryption” where the utilization of nonlinearities
and forcing of the dynamical system to a chaotic state will ful-
fill the basic cryptographic requirements. Due to nonlinear
mechanisms that lead to a chaotic behavior, this one is too dif-
ficult to predict by analytical methods without the secret key
(initial conditions and/or parameters) being known. This would reduce a potential attack to one category that of a brute force attack, in which any attempt to crack the key depends directly upon how long the key is [17]. Classical cryptography
works on discrete values and discrete time, while the crucial point in chaotic cryptography is the usage of continuous-value systems that may operate in continuous or discrete time. Cha- otic maps and cryptographic algorithms have also some simi- lar properties: sensitivity to initial conditions and parameters, random like behavior and unstable orbits with long periods, depending upon the precision of the numerical implementa- tion. Encryption rounds of a cryptographic algorithm lead to the desired diffusion and confusion properties of the algo- rithm. In a similar manner, iterations of the chaotic map spread the initial region over the entire phase space while the parameters of the chaotic map may represent the key of the encryption algorithm [17].
After Iris pattern coding and getting iris template using pro- posed algorithm, a novel chaotic secure content based hidden transmission scheme of biometric data is used to secure transmission of it. Encryption data technique is used to im-
After capturing the eye image from the secure camera and performing the proposed algorithm for Iris coding the algo- rithm to extract the important features to be used to hide in the host image. To do this, two chaotic maps named Henon map and Logistic map are used to encrypt Iris code. Logistic map generates a secure pseudo random sequence, which is used as the sequence key and Henon map encrypts the Iris codes. It provides the following features: 1) resistant to the finite word length effect of the chaotic sequence; 2) very un- predictable; 3) robust against attacks; and 4) resistant to re- peated group attack. In addition, the secret keys used as pa- rameter value and initial condition of chaotic map are gener- ated by the biometric, because biometric is very random at each enrollment of the person [13].
To perform verification of a person’s claimed identity, the En- crypted Iris codes are sent to the authentication server over network. At the server end, the Encrypted Iris codes are re- ceived. After receiving the Encrypted Iris code, a chaotic se- quence is generated by the secret keys and applied on the ex- tracted data to decrypt it in its actual form.
Fig. 6 shown Original Iris Image, HSV Iris Image, and YCbCr Iris Image and Fig. 7 shown H Plane, S Plane and V Plane Y Plane, Cb Plane and Cr Plane.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013 713
ISSN 2229-5518
Fig.6 Original Iris Image, HSV Iris Image and YCbCr Iris Image.
technique that can used in our system, that is used to provide authentication and identification to the customers , they used the credit card.
[1] G. Couloris, J. Dollimore, T. Kinberg, Distributed Systems-Concepts and Design, 4th Edition, Addison-Wesley, Pearson Education, UK,
2001.
[2] A. Tanenbaum and M. Van Steen, Distributed Systems: Principles and Paradigms, Prentice Hall, Pearson Education, USA, 2002.
[3] Ganorkar, S. R., & Ghatol, A. A., “ Iris Recognition: An Emerging Biometric Technology”. International Conference on Signal Pro- cessing, Robotics and Automation, Corfu Island, Greece, pp. 91-96,
2007.
[4] Iridian Technologies. “Iris Recognition Basics”, science behind the technology, http://www.iriscan.com.
[5] Teerayoot Sawangsri, Vorapoj Patanavijit, and Somchai Jitapunkul, “Face Segmentation Using Novel Iris-Color Map And Morphological Technique”, World Academy of Science,2003, International Biometric Group. Biometric market by technology,2006, http://www.biometricgroup.com.
[6] Quan Huynh-Thu Mitsuhiko Meguro Masahide Kaneko, “Iris-Color- Based Image Segmentation and Its Application in Face Detection”, IAPR Workshop on Machine Vision Applications. Nara- ken New Public Hall, Nara, Japan, 2002.
[7] Y. RAMADEVI, “A novel threshold based edge detection algorithm”, International Journal of Engineering Science and Technology
Fig.7 H Plane, S Plane and V Plane Y Plane, CB Plane and Cr Plane
This paper has proposed a new model of architecture for online credit card transactions as example for using the dis- tributed systems in the applications. There are so many algo- rithms that have created to help human identification through Iris recognition. The most popular one is named “Daugman”. To prove this model, in this paper we introduced better per- formance of Iris recognition algorithm in compare with Daugman’s algorithm and the other algorithms are created. In the new Iris recognition method based on the natural-open eyes.
We use property of Iris color to set threshold for removing some noises that similar to Iris-color because the human Iris tend to have a predominance of red and non-predominance of blue and we use morphologic closing operations to smooth, fill in, and remove objects in an image sequence. Finally, the object tracking process performs as memory for collecting Iris- color objects obtained from previous frame to guide the next frame in order to remove Iris-color pixels that immediately appear from frame to frame.
This method can find the iris characteristic point in a short time, the recognition rate is high, and the recognition speed is guaranteed. And also we displayed in our paper how can pro- vide securely transmission of iris templates over Internet, it has been recognized that the chaos theory as appropriate
(IJEST),2011.
[8] Jianguo Wang *, Tieniu Tan, “A new face detection method based on shape information”, Pattern Recognition Letters 21,2000.
[9] M. Elad et al., “Rejection based classifier for face detection”, Pattern
Recognition Letters 23,2002.
[10] Zuraini Othman, Anton Satria Prabuwono, “Preliminary Study on Iris Recognition System: Tissues of Body Organ in Iridology,” IEEE EMBS Conference onBiomedical Engineering & Sciences (IEC- BES),2010.
[11] Adam Czajka and Krzysztof Piech, “Secure Biometric Verification Station Based on Iris Recognition”, Hournal of Telecommnications and information Technology, 2003.
[12] Yogesh, Moon Inder Singh and Ruchika Lamba, “Automatic Face Detection Using Color Based Segmentation & Face Recognition Us- ing Eigen Face”, Electronic Instrumentation and Control, Patiala,
147004, Punjab, India, 2012.
[13] Ming-Hsuan Yang et.al., “Detecting faces in Images: a survey”, IEEE
transaction on Pattern analysis and machine intelligene, 2002.
[14] W. Boles, B. Boashash,“A human identification technique using im- ages of the iris and wavelet transform, ” IEEE Transaction on Signal Processing, 46(4): 1185–1188, 1998.
[15] R. Wildes, “Iris recognition: an emerging biometric technology, ” Proc. IEEE, 85(9): 1348–1363, 1997.
[16] Daugman JG, “High confidence visual recognition of persons by a
test of statistical independence”. IEEE- PAMI, 15: 1148-1161, 1993. [17] Rajendra Reddy, Vangala Sreela Sasi, “Biometric Authentication for
E-Commerce Transaction”, IEEE IST 2004, International Workshop on Imaging Systems and Techniques, Stresa Italy, 2004.
IJSER © 2013 http://www.ijser.org