International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1728
ISSN 2229-5518
Call Admission Control Scheme to
Determine the Preference for WLAN
Samrin Shareef, P.Prasanna Murali Krishna
—————————— ——————————
ODERN wireless communication systems consist of cellular, WiMAX, and WLAN access networks, coexist- ing in so-called heterogeneous networks. Multi-mode
users can access multiple systems to get ubiquitous access in an efficient way in terms of cost and quality. From the net- work point of view, it is important to efficiently manage the resources, by considering vertical handoffs (VHOs) and call arrivals in the multiple-coverage area. Recently, the 3rd Gen- eration Partnership Project (3GPP) Long Term Evolution (LTE) system has gained lots of interest for future broadband wire- less networks. Consequently, its integration with Wireless Lo- cal Area Networks (WLANs), including seamless/vertical handoffs and Call Admission Control (CAC), has held the spotlight in the heterogeneous networks. Unlike WLANs, where broadband data transmission is available at low cost and features a simple control plane, 3GPP LTE systems can implement more complex resource management schemes to provide more efficient services and better Quality of Service (QoS) with a typical cell radius of less than 300 m [1].
There have been some works in cellular/WLAN integrated networks [4], [5]. A simple admission strategy is to have an unconditional preference to WLANs since WLANs are cheap- er and have more bandwidth compared to the early version of
3G networks [4]. However, in 3GPP LTE systems, the band- width and cost have become comparable to that of WLANs due to wider bandwidth adoption and flat-rate tariffs. Moreo- ver, WLANs may be over-crowded due to the WLAN first scheme, and thus a large portion of connection attempts to WLANs can fail.
In [5], the authors considered that users with high mobility tend to spend a short time in the double-coverage area and require an upward VHO back to the cellular network shortly after a downward VHO to the WLAN. This may cause unneces- sary VHO processing load in both networks. Therefore, by probabilistically rejecting VHOs for highly mobile cellular
users, the VHO processing load and VHO blocking probability can be reduced while maintaining reasonable throughput in the WLAN.
We proposed a ring-based cell model in [2], where the re- quired resources depend on which annular region of the cell the user occupies. Unlike conventional Frequen- cy/Time/Code Division Multiple Access. Networks, more resources are allocated to a user farther from the base station (BS) in terms of power, bandwidth, and time slots. We found that the ring-based model allows more accurate analysis of the system performance, especially with respect to handoff and mobility metrics.
It may not be beneficial for the cellular users in the dual cov- erage area to have a policy of choosing the WLAN with a fixed probability regardless of the load on the WLAN or the location of the user. For example, it is desirable that a user located far- ther from the BS access the WLAN since more resources would be released to the cellular network when the user mi- grates to the WLAN. In this paper, we develop a traffic man- agement policy which sets the probability of migrating to the WLAN based on the traffic load in the WLAN and the location of the user in the cellular system. Using the ring-based model with a single WLAN hotspot, we compute WLAN migration preference values as functions of the blocking and handoff failure probabilities as well as new call/handoff attempt fail- ure probabilities. The network can perform efficient call ad- mission control by adaptively changing the WLAN preference settings in heterogeneous wireless networks in response to changing traffic conditions.
The rest of this paper is organized as follows. In Section II, we describe the system model, where mobility-related parameters are obtained using a ring-based model and system perfor- mance is derived based on steady-state analysis. System per- formances are investigated through intensive simulations in Section III. Finally, we present our conclusions in Section IV.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1729
ISSN 2229-5518

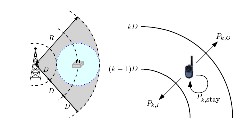
(a) A sector divided (b) Transition probabilities in the 𝑘th ring into rings, 𝐾=3, with a WLAN hotspot
Fig. 1. System model.
A cell has three sectors and each sector is divided into 𝐾 con- centric rings, each of whose width is 𝐷 m. Fig. 1(a) shows an
example sector with 3 rings, where a single WLAN AP, whose
depending on its distance from its BS, and guard channels are reserved for handoff and mobility [2]. In this paper, we consider CBR traffic for simplicity but extending the analysis to multiple traffic types is straightforward. W hen a call arrives
in the 𝑘th ring in the cellular network, it requires 𝑟𝑘
resources, while a user in the W LAN requires 𝑟𝑤 resources.
𝐶𝑐 and 𝐶𝑤 are the capacities of the cellular network and the
WLAN, respectively, and 𝐶𝑔 is the amount of guard
resources reserved by the cellular network. A fixed amount
of resource, 𝑛𝑤 is allocated to the W LAN users and the remaining resource of 𝐶𝑤 – 𝑛𝑤 can be assigned for the
cellular users who request connections to the W LAN.
Rc(S) and Rw(S) are the total resources being used in the cellular network and the W LAN, respectively, when the
system is in state 𝑆. They are denoted by
K
coverage radius is 𝐷 m, is located 2𝐷 m from the BS. In the
double coverage area, a cellular user can access either the cel-
lular network or a WLAN [4], and can perform handoffs to move from one to the other. These vertical handoffs (VHOs) can be categorized into downward VHOs and upward VHOs [5]. The downward VHO is a handoff from the cellular net-
work to the WLAN; the upward VHO is a handoff in the op-
Rc (S) = ∑ nkrk
k =1
Rw (S) = (n(K + 1) + nw ) rw
(3) (4)
posite direction.
Let ![]() be the number of mobile users in the 𝑘th ring in the cellular network, for 𝑘 = 1, . . .,.
be the number of mobile users in the 𝑘th ring in the cellular network, for 𝑘 = 1, . . .,. ![]() is the number of
is the number of
cellular users being serviced in the W LAN. The system state
𝑆 is denoted as (𝑛1, . . . , 𝑛𝐾, 𝑛𝐾+1). 𝐴𝑐 is the area covered by a 3G sector, and 𝐴𝑐,𝑘 is the area of the 𝑘th ring of a sector and 𝐴𝑤,𝑘 is the area of the W LAN that overlaps the
𝑘th ring, 𝑘 = 1, . . .,𝐾. We can define 𝑃𝑐, and 𝑃𝑤, as the probabilities that a user lies in the 𝑘th ring excluding the
region of overlap with the W LAN and in the intersection of
First, we consider the mobility of users between neighboring
rings. W hen a mobile enters a given ring, it is assumed to
reside there for an exponentially distributed residual time
whose mean is 1/𝛾. At the end of that time period, a user in the 𝑘th ring may move to the (𝑘 − 1)th or (𝑘 + 1)th rings with probabilities of 𝑃𝑘,𝐼 or 𝑃𝑘,𝑂, respectively (see Fig. 1(b)). Or the user may stay within the 𝑘th ring with probability 𝑃𝑘, stay,
which can be equivalently seen as the user moves within the
ring after a certain residual time. Assuming a user’s direction of movement is uniformly distributed, we can obtain that
𝑃𝑘,stay = 𝑃𝑘,𝐼+𝑃𝑘,𝑂 = 1/2.𝑃𝑘,o and 𝑃𝑘,I are determined in terms of the inner and outer circumferences of the 𝑘th ring,
𝑙𝑘,I and 𝑙𝑘,O. For 𝑘 > 1, the parameters are given by
the 𝑘th ring and the W LAN, respectively. Assuming a uniform
mobility, these probabilities can be written as![]()
P(k, I) = 1
2
1
l(k, I)/(l(k, I) + l(k, o) )
(5)
![]()
P(w, k) = A(w, k)
(1)
![]()
P(k, O ) = - P(k, I)
2
(6)
Ac
P(c, k) = (A(c, k) - A(w, k))
(2)
These results agree with those in [2], where the probabilities ![]() and
and ![]() have been calculated by using the
have been calculated by using the
alance equations to satisfy the condition that the average![]()
Ac
![]()
for and ![]() and therefore,
and therefore,
Let 𝜆𝑐 be the new call arrival rate in a sector for the cellular network and 𝜆ℎ be the handoff rate of users into the sector.
and the average call holding time for a user is denoted as
1/𝜇𝑐. Since W LAN users tend to remain stationary, it is
assumed that there is no handoff request for W LAN users. In
the W LAN, all users are assumed to require the same amount of resources for simplicity [5]. For the cellular
network, however, a user’s required resources vary
IJSER © 2013 http://www.ijser.org
b
inward-rate should be equal to the average outward-rate at each ring boundary. Exceptionally for the innermost “ring”
(i.e., 𝑘= 1), a user always moves out of the ring after a certain residual time, so 𝑃1,𝑂 is always 1 and other
probabilities become 0.
Now we consider the probabilities of moving between the cellular and W LAN areas. W hen a user moves out of the
WLAN’s coverage, it may move to the 𝑘th ring in the sector
or it may move to neighboring cells. The corresponding
probabilities are denoted as 𝛽𝑘 and 𝛽𝐾+1. Assuming the mobile’s direction is uniform over [0, 2𝜋], these probabilities
are respectively proportional to the length of the W LAN’s
boundary that lies within the 𝑘th ring or neighboring cell.
Generally, we require a degree of margin in the received
signal strength (RSS) for handoff to prevent ping-pong
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1730
ISSN 2229-5518
effects. Assuming a margin of 𝜉𝑡ℎ dB, 𝛽1 and 𝛽𝐾+1 can be
calculated assuming a given path loss. That is, for the first
ring and the 𝐾th ring, if a user leaves the W LAN and the path
loss difference from the W LAN boundary to the
corresponding sector/ring boundary is less than the margin, then the user moves to the first ring or to a neighboring cell.
For example, we consider a simple 3-ring case with 𝐷 = 100
m, where the path loss (in dB) is given by 39.95 + 43.375
log10 𝑑10 (𝑑in meters) and 𝜉𝑡ℎ = 1 dB. Then, 𝛽1 = 0.11, 𝛽2
= 0.31, 𝛽3 = 0.37, and 𝛽4 = 0.21.
We next consider the balance equations between the cellular
network and the W LAN. The users in the 𝑘th ring moves into the W LAN with a probability of 𝛼𝑘. On the boundary of the WLAN coverage within each of the 𝐾 rings, the average
move-in rate from the cellular network to the W LAN should
be equal to the average move-out rate from the W LAN to the
cellular network, i.e.,
successfully handed off to the W LAN, 𝑟𝑘 resources are released by the cellular network and 𝑟𝑤 resources are occupied in the W LAN. If Δ𝑟 = 𝑟𝑘 − 𝑟𝑤 > 0, it is beneficial to
initiate VHOs to reduce the overall resource usage. Larger
Δ𝑟 values indicate more efficient resource usage due to
VHOs. Users from neighboring cells enter the double-
coverage area with a probability of 𝛼𝐾+1 and request downward VHOs to the W LAN with a probability of 𝑤𝐾. If no
resources are available in the W LAN, their requests are
rejected and they try to access the cellular network.
We measure the system performance using the call blocking
probability 𝑃𝐵 and handoff failure probability 𝑃𝑓 [2]. The new
call may be blocked in the cellular network or the W LAN with
probabilities 𝑃𝐵,C and 𝑃𝐵,W, respectively, and 𝑃𝐵 =
𝑃𝐵,𝑐+𝑃𝐵,𝑤. Similarly, 𝑃𝑓 = 𝑃𝑓,c+𝑃𝑓,𝑤, where 𝑃𝑓,𝑐 and 𝑃𝑓,𝑤
are the probabilities of handover failure to the cell and
WLAN, respectively. The goal of the CAC is to find the optimum value for the vector of W LAN choice probabilities,
Pc1γ 1α1 = Pwγwβ1
Pc2γ 2α 2 = Pwγwβ 2
.
.
.
(7)
(8)
which we call the W LAN preference settings, 𝑊 = [𝑤1, . . . ,
𝑤𝐾], so that 𝑃𝐵 and 𝑃𝑓 are minimized. We introduce two
new probabilities, 𝑃′𝐵 and 𝑃′𝑓, as cost measures. 𝑃′𝐵 is the
new call attempt failure probability, and 𝑃′𝑓 is the handoff
attempt failure probability. W hen a new call or VHO call
attempts to connect to the W LAN, its attempt fails if no resources are available in the W LAN. However, it is not
blocked or lost unless there are no resources available in the cellular network as well. These attempt failures result in wasted resources in the control plane; thus it is also important to reduce these failure probabilities to minimize cost and complexity.
Pc(n - 1)γ (n - 1)α (n - 1) = Pwγwβ (n - 1) (9)
γra(k + 1) = Pwγwβ (k + 1)
(10)
The state transitions are investigated as follows;∙
• New call arrivals outside the W LAN: W hen a call
arrives in the non-overlapped 𝑘th ring at a rate of
𝜆𝑐,k = 𝜆𝑐𝑃𝑐,, 𝑛𝑘 → 𝑛𝑘 +1 if 𝑅𝑐(𝑆) + 𝑟𝑘 ≤ 𝐶𝑐 − 𝐶𝑔.
where 1/𝛾𝑤 and 1/𝛾1 are the mean residual times in the
WLAN and in the innermost ring, respectively3. 𝛼𝐾+1 is the
probability that a handoff call from a neighboring cell
requests a VHO to the W LAN. The residual time is assumed
to be proportional to the size of the region [2], [3], i.e., 1/𝛾𝑅 =
𝛼𝑅, 1/𝛾1 = 𝛼𝐷, and 1/𝛾 = 𝛼𝐷2 , where 1/𝛾𝑅 is the mean
residual time in a sector, 𝑅 is the cell radius, and 𝛼 is a
constant determined by the mobility characteristics of the
users.
In the W LAN, a fixed amount of resource, 𝑛𝑤 is allocated for
WLAN users and the W LAN’s remaining resource, 𝐶𝑤 − 𝑛𝑤
can be assigned to cellular users that newly appear in the
double-coverage area or that request downward VHOs. For
the cellular network, however, the resources that are used by a mobile depend on the mobile’s location, and guard resources are reserved to support handoff and mobility [2].
When a new call appears in the intersection of the W LAN
coverage area and the 𝑘th ring, it is serviced by the cellular network with a probability of 1 − 𝑤𝑘. W ith probability 𝑤𝑘, a
new call attempts to connect to the W LAN. If no resources
are available in the W LAN, the mobile tries to connect to the cellular network; the call is blocked only when resources are
not available in the cellular network and the W LAN.
For downward VHO requests by mobiles in the 𝑘th ring, they are processed in the W LAN with probability 𝑤𝑘. The call
continues to be serviced in the cellular network without
requesting a VHO with probability 1 − 𝑤𝑘. W hen the call is
Otherwise, it is blocked.
• New call arrivals in the double-coverage area:
When a new call appears in the 𝑘th ring at a rate
of 𝜆𝑐𝑃𝑤,, it attempts to connect to the W LAN or
the cellular network with probabilities of 𝑤𝑘 or 1 −
𝑤𝑘, respectively. W hen the new call uses the
WLAN, 𝑛𝐾+1 → 𝑛𝐾+1 + 1 if (𝑆)+𝑟𝑤 ≤ 𝐶𝑤.
Otherwise, 𝑛𝑘 → 𝑛𝑘+1 if (𝑆) +𝑟𝑘 ≤ 𝐶𝑐 − 𝐶𝑔.
When a call terminates, its resources are released to the
cellular network or the W LAN as follows.
• When a call terminates in the 𝑘th ring with a rate
of 𝑛𝑘𝜇𝑐, 𝑛𝑘 → 𝑛𝑘 − 1 for 𝑘 = 1, . . . , 𝐾.
• When a call terminates in the W LAN with a rate
of𝑛𝐾+1𝜇𝑐, 𝑛𝐾+1 → 𝑛𝐾+1 − 1.
Handoffs from adjacent cells can be categorized into two
cases. A handoff to a neighboring cell that arrives outside that cell’s embedded W LAN occurs with a probability of
1−𝛼𝐾+1; a handoff to a neighboring cell’s double-coverage area occurs with a probability of 𝛼𝐾+1. The mobile that is
handing off to the double-coverage area requests a VHO
with probability Handoffs from adjacent cells can be categorized into two cases. A handoff to a neighboring cell that arrives outside that cell’s embedded W LAN occurs with
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1731
ISSN 2229-5518
a probability of 1−𝛼𝐾+1; a handoff to a neighboring cell’s double-coverage area occurs with a probability of 𝛼𝐾+1. The
mobile that is handing off to the double-coverage area
requests a VHO with probability
The state transition rates can be obtained from the above investigation. And then, the steady-state probabilities,
denoted as (𝑆), can be obtained with the normalization
condition Σall 𝑆 (𝑆) = 1.
• Handoff calls move into the cellular-only area at a
rate of (1 − 𝛼𝐾+1)ℎ; when a handoff of this type happens, 𝑛𝐾 → 𝑛𝐾 + 1 if 𝑅𝑐(𝑆) + 𝑟𝐾 ≤ 𝐶𝑐.
• Calls perform VHOs to the W LAN in the double
coverage area with a rate of 𝜔𝐾𝛼𝐾+1𝜆ℎ; when this happens, 𝑛𝐾+1 → 𝑛𝐾+1 + 1 if 𝑅𝑤(𝑆) + 𝑟𝑤 ≤ 𝐶𝑤, or 𝑛𝐾 → 𝑛𝐾 + 1 if 𝑅𝑐(𝑆) + 𝑟𝐾 ≤ 𝐶𝑐.
The new call blocking probabilities for the W LAN and the
cell, 𝑃𝐵,𝑤 and 𝑃𝐵,𝑐 can be expressed as
PB, W = K∑k =1 ∑S ∈ Ω ∩ Ω(S )Pw, k
PB, C = K∑k =1 ∑ S ∈ Ω(S )Pc, k
Where
(11) (12)
• Calls perform horizontal handoffs to the cellular network from the double-coverage area at a rate
of (1 − 𝜔𝐾+1)ℎ; when one of these occurs, 𝑛𝐾 →
𝑛𝐾 + 1 if 𝑅𝑐(𝑆) + 𝑟𝐾 ≤ 𝐶𝑐.
During a downward VHO, a call in the 𝑘th ring attempts a
VHO to the W LAN with a probability of 𝑤𝑘. We must have
Rw(𝑆)+𝑟𝑤 ≤ 𝐶𝑤 in the W LAN, after accepting the request.
After the VHO completes, 𝑟𝑘 resources are released in the
cellular network. Therefore, the larger Δ𝑟 is, the greater 𝑤𝑘
should be. For upward VHOs, 𝑟𝑤 resources are released in
the W LAN and 𝑟𝑘 resources are occupied in the sector.
• Calls in the 𝑘th ring (𝑘 = 2, ...,) moves to the
Ω = {𝑆∣(𝑆) + 𝑟𝑤 > 𝐶𝑤}
Ω𝑘 = {𝑆∣(𝑆) + 𝑟𝑘 > 𝐶𝑐 − 𝐶𝑔}.
The overall blocking probability 𝑃𝐵 is 𝑃𝐵,c + 𝑃𝐵,w. The
handoff failure probability in the W LAN is
Pf, w = K∑∑s ∈T(S)Pwβk + ∑S ∈TKP(S )Pwβk +1
k =1
(13)
where Γ𝑘 = {𝑆∣𝑅𝑐(𝑆) + 𝑟𝑘 > 𝐶𝑐}. Similarly, the handoff failure
probability in the cellular network is
Pf = ∑S∈T (S){(1- α k +1 ) + α k +1 (1 - w k )}
(14)
+ ∑S∈Ω Γ P(S )α k +1 w k
1 k
double coverage area at a rate of 𝑛𝑘𝛼𝑘𝑤𝑘𝛾 and change 𝑆 as follows: 𝑛𝑘 → 𝑛𝑘−1 and 𝑛𝑤 → 𝑛𝑤+1,
and Pf
= Pf ,c + Pf ,w
if 𝑅𝑤(𝑆)+𝑟𝑤 ≤ 𝐶𝑤.
• Calls in the first ring move to the double-coverage
area at a rate of 𝑛1𝛼1𝑤1𝛾1, changes in 𝑆 are the
same as above.
A new call attempts to connect to the W LAN with a
probability of 𝑤𝑘 when it arrives in the double-coverage area.
Its attempt can fail when there are not enough resources
available in the W LAN, though the call may be serviced in
the cellular network if 𝑟𝑘 resources are available. The new call attempt failure probability, 𝑃′𝐵, is
Calls move out to the 𝑘th ring at a rate of 𝑛𝐾+1𝛾𝑤𝛽𝑘, 𝑘 = 1, .
. .,, and 𝑆 changes as follows: 𝑛𝐾+1 → 𝑛𝐾+1−1 and 𝑛𝑘 →
𝑛𝑘+1, if 𝑅𝑐(𝑆)+𝑟𝑘 ≤ 𝐶𝑐.
PB =
K
∑k =1 ∑
S∈Ω( S )
Pw,kWk
(15)
Calls are handed off to neighboring cells at a rate of
𝑛𝐾+1𝛾𝑤𝛽𝐾+1, and 𝑆 changes as follows: 𝑛𝐾+1 − 1.
When a user moves outward or inward between rings in the
cellular network, it requires more resources or fewer, respectively [2].
A downward VHO attempt to the W LAN fails when not
enough resources are available in the W LAN. It should be noted that the call requesting a VHO is not forced to be
terminate if its VHO attempt fails. An upward VHO attempt to the cellular network can fails and the call terminates when there are not enough resources in the target ring to support
the call, i.e., at least 𝑟𝑘 resources for the 𝑘th ring. The handoff attempt failure probability, 𝑃𝑓, is
• When a user in the 𝑘th ring (𝑘 = 1, . . .,𝐾 − 1)
moves outward, it requires more resources and
the state 𝑆changes as 𝑛𝑘 → 𝑛𝑘−1 and 𝑛𝑘+1 →
𝑛𝑘+1+1 with a rate of 𝑛1𝛾1 for the first ring and
𝑛𝑘𝑃𝑘,𝑂𝛾 for the other rings, respectively. If (𝑆) +
𝛿𝑟𝑘 ≥ 𝐶𝑐, the user can maintain its connection,
where 𝛿𝑟𝑘 = 𝑟𝑘+1 − 𝑟𝑘 is the additional resources
required by the user. In the outmost ring (the𝐾th
ring), the user can be handed off to a neighbor
cell, i.e., 𝑛𝐾 → 𝑛𝐾 − 1 with a rate of 𝑛𝐾𝑃𝐾.
• For a ring (𝑘 = 2, . . .,), when a user moves
inward,𝑛𝑘−1 → 𝑛𝑘−1 + 1 and 𝑛𝑘 → 𝑛𝑘 − 1 with a
rate of𝑛𝑘𝑃𝑘,𝐼𝛾.
IJSER © 2013 http://www.ijser.org
Pf =K ∑k =1 ∑s∈Ω (S )Pc ,kα kWk + K ∑k =1 ∑s∈Γk (S )Pw βk + ..
(16)
A call may be dropped when moving within a sector since a call moving outward requires more resources. W hen a user moves inward, there is no blocking because the amount of resources required by the user decreases. As shown in [2],
the call dropping probability due to mobility (𝑃𝐷) can be kept low when the reserved resources 𝐶𝑔 can be assigned to
outward moving calls as well as handoff calls, so we do not
examine 𝑃𝐷 here.
Table 1
Three cases
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1732
ISSN 2229-5518
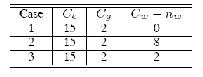
As shown in Fig. 1(a), a WLAN AP is located 200 m apart from the BS and its coverage radius is 100 m. The radius of coverage of the cellular network is set to 300 m and the cell coverage area is divided into three rings.
kept low due to guard resources. For Case 2, there are
sufficient resources in the W LAN; 𝑃′ 𝐵 and 𝑃′ 𝑓 are kept very
small e.g., less than 10−3 and 𝑃′𝑓 decreases as (𝑤2, 𝑤3)
approaches (1, 1). In this case, it is best to accommodate as
many cellular users as possible in the W LAN, i.e., 𝑃𝐵 and 𝑃𝑓 are minimized when 𝑊 = [111]. It should be noted that 𝑃𝐵 and 𝑃𝑓 are always smaller when a W LAN overlaps the cell.
Finally, if the available resources in the W LAN are small as
in Case 3, 𝑃′𝐵 and 𝑃′𝑓 become significant and they increase as 𝑊 → [1 1 1]unlike in Case 2.
Generally, the consequences of a handoff failure are worse than those of a new call blocking. We introduce an outage probability for all connections,
In order to get the required resources in each ring, the same assumptions have been used as in [2]. The path loss in dB at
Pout = PB + 3.5
(17)
a distance 𝑑 m from the BS is 39.95 + 43.375 log10𝑑 10. A
frequency selective fading channel is considered according
to a 3GPP typical case for an urban area with a receiver with
6 taps [6]. Simulation parameters are based on the 3GPP LTE system: A 5 GHz band contains 25 resource blocks (RBs), where each RB consists of 12 subcarriers with a spacing of 15 kHz. Total transmit power at the BS is 43dBm
where we use the weighting factor of 3.5 since 𝑃𝐵 is 3.5 times higher than 𝑃𝑓 without the W LAN. Similarly, the new connection attempt failure probability, 𝑃′ 𝑜𝑢𝑡, can be defined with 𝑃′𝐵 and 𝑃′𝑓 in the same way. Then, we define the
overall cost as
and the target BER is 0.1%. The data rate at RB 𝑗 of user 𝑖 is given by 𝑅𝑖 = 12log2 (1 + 𝛽SNR𝑖,j), where 12 is the number
Cost = Pout + f .......Pout
(18)
of subcarriers in an RB, 𝛽 = 1.5−ln(5BER) , and SNR𝑖,𝑗 is the SNR averaged over 12 subcarriers in RB 𝑗 of user 𝑖. The noise power density 𝑁𝑜 is -174 dBm/Hz. The target data rate
is 10 kb/s with single antenna configurations for both BS and
User Equipment (UE).
When the target data rate can be supported with a partial use of an RB, the RB doesn’t need to be used continuously in the time domain. The system can use time sharing in this case; the amount of resources for a user can be less than one and the remaining can be assigned to other users. Scheduling is based on the heuristic max-min method [7]. The required resources are measured by the portion of an RB required to support the target data rate, assuming an equal power distribution over the frequency band since it has been shown that water-filling has an insignificant impact after
multi-user scheduling. As found in [2], 𝑟𝑘 is independent of
the traffic load and cell size, and depends on the target data
rate. Interestingly, if 𝑟1 is normalized to be one, 𝑅 = (𝑟1, 𝑟2,
𝑟3) can be approximated as (1, 1.5, 2), i.e., a user in the 3rd
ring may require twice the resources of a user in the
innermost ring.
We use 𝑅 = (1, 1.5, 2) and set 𝑟𝑤 = 1. We consider three
cases for comparison as shown in Table 1. The capacity of
the cellular network (𝐶𝑐) is 15 and 𝐶𝑔 is 2. The available resources for the cellular users in the W LAN, 𝐶𝑤 − 𝑛𝑤, is varied. The preference 𝑤3 is set to 1 so that the call
requiring the most resources in the cellular network always
prefers the W LAN over the cellular network. 𝑤1 and 𝑤2 are each varied in the range [0, 1]. W hen there is no W LAN, 𝑃𝐵
= 0.14, 𝑃𝑓 = 0.04 and their ratio, 𝑃 , is 3.5. The mean call
duration 1/𝜇𝑐 is set at 100 s.
For Case 1, 𝑃′ 𝐵 increases as 𝑤2 increases and converges
to 1/3 which corresponds to 𝑃𝑤. 𝑃′𝑓 increases as well but is
where 𝑓 is the weighting factor for the new connection
attempt failure probability. Fig. 2 shows 𝐶𝑜𝑠𝑡 versus 𝑤1 and
𝑤2 with 𝑓 = 3.5 for Case 3. 𝑊 = [0 0.3 1] minimizes the cost
for this case. The cost increases most rapidly with respect to
𝑤2, and 𝑊 = [1 1 1], i.e., unconditional preference to the
WLAN by users in every ring, pays the largest cost. Thus, as
the remaining resources in the W LAN decrease, it is better to for the W LAN to give higher preference to the users who requiring the most resources in the cellular network.
TABLE 2
PREFERENCE SETTINGS TO MINIMIZE THE COST WITH VARIOUS VALUES FOR
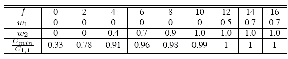
THE WEIGHTING FACTOR 𝑓 (𝑤3 =1).
To further investigate the impact of the weight 𝑓, Table 2 shows the optimum preference settings as well as the ratio of
the minimum value of 𝐶𝑜𝑠𝑡 over the value of 𝐶𝑜𝑠𝑡 when 𝑊 = [111]. With a small value of 𝑓, it is beneficial not to allow the cellular traffic to perform VHOs to the WLAN. Increasing 𝑓
reflects greater importance of the effect of new connection at-
tempt failures. In such a situation, more cellular traffic is al-
lowed to attempt to move to the WLAN, i.e., 𝑊 → [1 1 1]. We also note that in the considered scenario, 𝑤1 has an insignifi- cant impact on the gain in 𝐶𝑜𝑠𝑡 and can be set to 0.
We have proposed a new call admission control scheme for heterogeneous networks, where the users’ relative preference for the WLAN changes adaptively based on the available re- sources in the WLAN and the location distribution of the cel-
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 8, August-2013 1733
ISSN 2229-5518
lular users. By modifying our ring-based model of the cell, we derived performance measures such as call blocking/ handoff failure probabilities as well as new call/handoff attempt fail- ure probabilities. We investigated the effect of WLAN prefer- ence settings with various WLAN loading and cost weighting factors in a sector with 3 rings and a WLAN hotspot. Using the proposed CAC scheme the system cost can be greatly de- creased with respect to the case where users always prefer the
WLAN (i.e., 𝑊 = [1 1 1]).
[1] D. Astély, E. Dahlman, A. Furuskär, Y. Jading, M. Lindström, and S.Parkvall, “LTE: the evolution of mobile broadband," IEEE Com- mun.Mag., pp. 44-51, Apr. 2009.
[2] D. K. Kim, D. Griffith, and N. Golmie, “A novel ring-based perfor- mance analysis for call admission control in wireless networks," IEEE Commun. Lett., vol. 14, no. 4, pp. 324-326, Apr. 2010.
[3] D. K. Kim and D. K. Sung, “Characterization of soft handoff in
CDMA systems," IEEE Trans. Veh. Technol., vol. 48, no. 4, pp. 1195-
1202, July 1999.
[4] W. Song, H. Jiang, and W. Zhuang, “Performance analysis of the WLAN first scheme in cellular/WLAN interworking," IEEE Trans. Wireless Commun., vol. 6, no. 5, pp. 1932-1943, May 2007.
[5] S. Lee, K. Kim, K. Hong, D. Griffith, Y. H. Kim, and N. Golmie, “A probabilistic call admission control algorithm for WLAN in hetero- geneous wireless environment," IEEE Trans. Wireless Commun., vol.
8, no. 4, pp. 1672-1676, Apr. 2009.
[6] 3GPP TS45.005 v8.3.0, “Radio access network; radio transmission and reception (Release 8)," Nov. 2008.
[7] M. Tao, Y. C. Liang, and F. Zhang, “Resource allocation for delay differentiated traffic in multiuser OFDM systems," IEEE Trans. Wire- less Commun., vol. 7, no. 6, pp. 2190-2201, June 2008.

1. Samrin Shareef completed Bachelor of Technology (B.Tech) in Electronics & Communication Engineering from Jawaharlal Nehru Technological University, Hyderabad in 2008.and currently pursuing Masters of Technology (M.Tech) in Digital Electronics and Communication Systems from Jawaharlal Nehru Technological University, Kakinada.
2. P.Prasanna Murali Krishna is working as Associate Professor in ECE Department and is also Head of the Department with Dr.SGIET, Markapur- Jawaharlal Nehru Technological University, Kakinada from 2001 till date.
IJSER © 2013 http://www.ijser.org