International Journal of Scientific & Engineering Research, Volume 4, Issue 1ŗǰȱ ber-2013
ISSN 2229-5518
Access Control of Door and Home Security by
Raspberry Pi Through Internet
Md. Nasimuzzaman Chowdhury1, Md. Shiblee Nooman2, Srijon Sarker3
Abstract— In the present age Internet of things (IOT) has enterned a golden era of rapid growth. The Internet of things is a concept that aims to extend the benefits of the regular Internet—constant connectivity, remote control ability, data sharing, and so on—to goods in the physical world. Everyday things are getting connected with the internet. This concept can be used tomanage the security concerned issues in a cost effective way. In ths paper work a system is being developed to connect any door with the internet, so that the access control system can be controlled from any where in the world. In a case that one is not at home and a vistor is at his door steps then the authorized person will be notified about the visitor via twitter and the person can see the visitor from the web through the camera from any where and the system will take a picture of the visitor and keep a record by sending an attachment through E-mail or tweet in twitter. If the authorized person wants to give a message the visitor it can be sent easily through the internet and it will appear in a screen on the front face of the door. The door lock can be controlled through the internet. With the help of this system an evidence of the visitor can be kept as a record if any emergency case or situtaion occurs.
Index Terms— Internet of Things (IOT), Raspberri Pi, Wireless Door Control, Security Measures,Wi-Fi module, PIR Sensor, Human detection
550
1 INTRODUCTION
—————————— ——————————

In this modern world crime has become ultra modern too! In this current time a lot of incident occurs like robbery, stealing unwanted entrance happens abruptly. So the security does matters in this daily life. People always remain busy in their day to day work also wants to ensure their safety of their beloved things. Sometimes they forget to look after their necessary things like keys, wallet, credit cards etc. Without these, they are unable to access their home or any place they want. To prevent such incidents many scholars came into action and tried to pro- hibit them. Like YanboZhao ; ZhaohuiYe introduced “A GSM/GPRS based wireless home security system[2] but the system is not cost effective as the GSM/GPRS charges a fixed amount from each sms/call or data transfer. Ha- san,H. ; Bakar,R.A. ; Mokhtar,A.T.F. also introduced ” “Face recognition based on auto-switching magnetic door lock system using microcontroller”[3][5] but face recognition means com- plex algorithms and sometimes the system may be unable to detect the visitors identification correctly and keeps a computer chip busy for longer time. Assaf, M.H. ; Mootoo, R. ; Das, S.R. ; Petriu, E.M. ; Groza, V. ;Biswas, S. invented “Sensor based home automation and security system”[4] designed a sensor based system. Lots of paper work has been done so far. In this paper, a new system is designed which would control the door through the internet without any complexity. It’s very conve- nient and serves as a plug and play system. The user can see from anywhere in this world that who is at his door steps. The system keeps a picture of the visitor as evidence that would be needed if any unwanted situation occurs like stealing, robbery etc. The user can control the door with a single command through the internet by mobile, pc, tablets etc. This system can also be used for industrial automation wirelessly. Also for any kind of accident like fire, or stolen keys the door can be opened by a single and simple command. As a result the security is con-
firmed also the mental peace.
Author 1- Dept. of Electrical & Electronic Engineering, AIUB (American
International University-Bangladesh)
Email: mdnasimuzzaman.chowdhury.c@ieee.org
Author 2- Dept. of Electrical & Electronic Engineering, AIUB (American
International University-Bangladesh) Email: shiblee_nooman@hotmail.com
Author 3- Dept. of Electrical & Electronic Engineering, AIUB (American
International University-Bangladesh) Email: ankon@gmail.com
2. OVERALL PROJECT OUTLINE
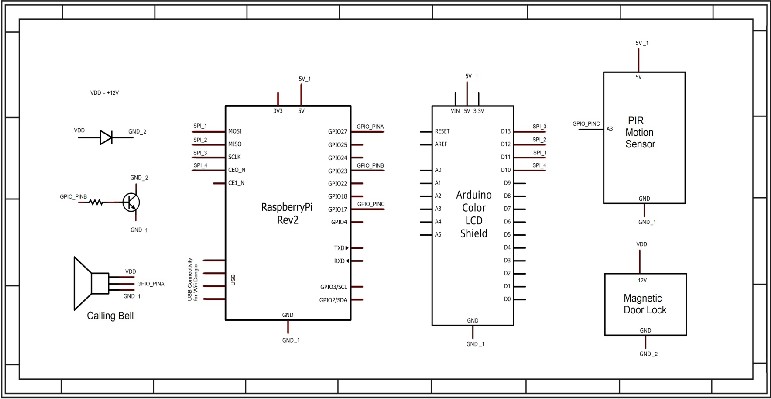
In this project with a minicomputer raspberry pi different input and output is interfaced. In input section there is calling bell, PIR sensor & wireless camera. In processing section a minicomputer raspberry pi is used. Raspberry pi is equipped with wifi dongle. And on the output terminal there are Lcd, magnetic door lock, emailing & tweeting services. A calling bell is placed on door so that if someone visits the user the person will press the bell and the bell will generate a signal to raspberry pi indicating presence of a person. There is also another way of sensing human and that is passive infra red human motion detection sensor. If any thief tries to break into the house PIR sensor will identify the motion of that human and will transmit an alarm to raspberry pi. Most im- portant input device is the wireless camera. It is used to see video stream and also whenever a person comes it takes a snapshot of that person and transmit it to raspberry pi. Raspberry pi process these inputs like whenever it gets a calling bell as input it trans- mits a signal to wireless camera to capture an image of the visitor. Within the time it receives the picture it generate a Tweet alerting the user that someone has arrived infront of door. After receiving the image raspberry pi sends a mail to user attaching the picture. User can control the magnetic lock through twiter. If user wants to permit the visitor access he can turn on the lock and if he wants to reject access for any reason user can show the reason to LCD tweeting a text for visitor
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518
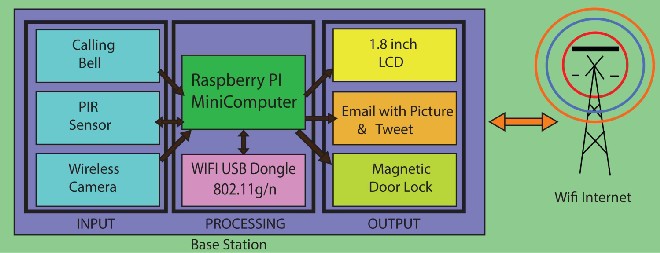
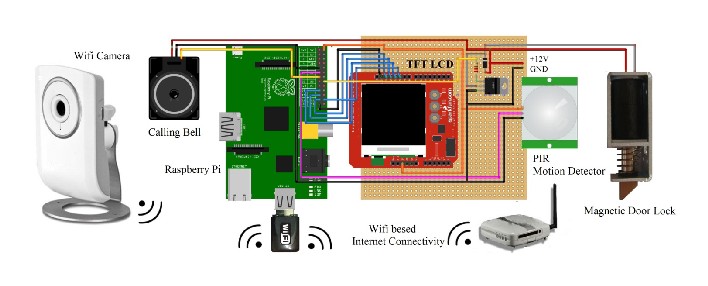
Figure 1. Main Project Outline
Figure 2. Prototype Design of Internet Controlled Door
551
2. HARDWARE PROTOTYPE
a) RASPBERRY PI:
Raspberry Pi Model B has 512Mb RAM, 2 USB ports and an Ethernet port. It has a Broadcom BCM2835 system on a chip which includes an ARM1176JZF-S
700 MHz processor, Video Core IV GPU, and an SD card. It has a fast 3D core accessed using the supplied OpenGL ES2.0 and Open VG libraries. The chip spe- cifically provides HDMI and there is no VGA sup- port. The foundation provides Debian and Arch Li- nux ARM distributions and also Python as the main programming language, with the support for BBC BASIC, C and Perl
b) WIFI –DONGLE:
Wifi dongle is connected through USB port. With wireless speeds of up to 300Mbps and advanced MI- MO technology, works seamlessly with existing IEEE
802.11b/g networks. This tiny adapter works as a vir-
tual wireless Access Point. Compatible with Wi-Fi Protected Setup (WPS), establish a WPA2 secure con- nection, more secure than WEP encryptions.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518


Fig.3. Raspberry pi
Fig.4. WiFi Dongle
552
PASSIVE INFRA RED SENSOR:-
The key of this project is Human sensing technology. In this projectPassive Infra Red sensor has been used to detect hu- man. Infrared radiation exists in the electromagnetic spectrum at a wavelength which is longer than visible light. it can be detected though it cannot be seen. Objects that generate heat also generate infrared radiation and those objects include an- imals and the human body whose radiation is strongest at a wavelength of 9.4um [6].PIR sensor is able to detect the change of radiation of these infrared radiation. A picture of working principle of PIR sensor is given below
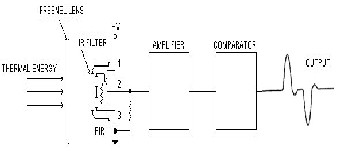
Figure.5. Typical configuration of PIR
PIR sensor generates +5v and -5v sine signal when any human or animal passes in front of the sensor or any movement is detected of human or animal in front of this. A breakout board is used to detect this signal and convert it into a longer digital signal. The output of PIR sensor can be adjusted. For max it can create an output signal for approximately 1.2 seconds [7]. This is more than enough to detect the signal.
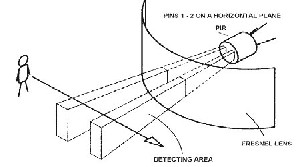
Fig.6. Working principle of PIR sensor
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518
Figure 7. Main Circuit Diagram
553
3. CIRCUIT ANALYSIS
Heart of this project is raspberry pi minicomputer. Wifi dongle is connected through USB port. The wifi module scans for the available network and connects to the network with pass- word. Calling bell is connected with GPIO of raspberry pi. Whenever someone come to home and press button the calling bell starts to transmit musics. A resister is connected to calling bell and whenever music plays it generates 5v signal. This causes an interrupt to raspberry pi. PIR sensor is also con- nected to GPIO. The pin is pulled down and pir sensor also generates a high voltage whenever it detects presence of any human. Raspberry pi is always scanning for pir sensor input or calling bell input. Here is also an indication which gene- rates an special alert. In the algorithm it is defined that if any visitor comes in and press the bell means both the interrupt
happened it is a common situation and indicating that a visitor
has arrived But if only one interruption happens like human motion then it’s indicates that a thief or robber might have come. An individual interrupt of calling bell indicates pir sen- sor has gone out of order. When the system received both the interrupts raspberry pi take a snap shot of the person through wifi camera. Here the camera is connected with raspberry pi through wifi network. Raspberry pi transmits the snapshot through gmail. And also generates a tweet that someone has arrived. But if only PIR sensor generates the interrupt then it generates an instant alerm that might have someone is trying to have unauthorized access or break into the house. It takes several snapshots and generates several tweets to the user as alert. The 1.8’ TFT LCD is connected through serial peripheral interface and the magnetic lock is controlled by a GPIO.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518
4. MAIN TECHNOLOGY USED
554
Here is the flow chart of the system. At first the system detects human and automatically raspberry pi take a snapshot which means the image acquisition part. After that image is attached and mailed to user that is the image processing, mail & tweet part. At last when user sends a re-tweet of door lock or open according to users command the magnetic lock gets open or close.
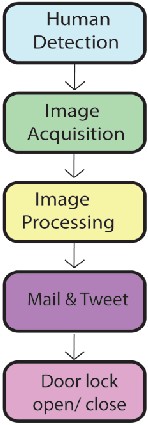
Fig.8. Flow chart of the designed System
Fswebcam is used to take the webcam snapshots by the Wi- Fi camera. Also this Wi-Fi camera is accessible from anywhere for a live view of the visitor.
sudo apt-get install fswebcam
Here is the interrupt portion. If interrupt from PIR sensor happens then the cam is commanded to take snapshot.
sudo apt-get install fswebcam if (GPIO.input(buttonPin)):
#this is the script that will be called (as root)
os.system("fswebcam -r 960x720 -d
/dev/video0 /home/pi/webcam.jpg")
os.system("python
/home/pi/sendnotify.py")
The system needs its own username and password so that it can access to the account and generate a mail automatically. The email address and password of the system is given bel- low.
USERNAME = "internetofdoor@gmail.com" PASSWORD = "awsedrft123"
server = smtplib.SMTP('smtp.gmail.com:587') server.ehlo_or_helo_if_needed() server.starttls() server.ehlo_or_helo_if_needed() server.login(USERNAME,PASSWORD) server.sendmail(USERNAME, to,
msg.as_string())
server.quit()
After connecting to the server the server needs the email address of the user. The users email address is given bellow.
sendMail( ["mdnasime@gmail.com"],
"Door Bell Alert! Visitor Snap-
shot",
"Someone is at your door and ringing
your door bell. Please See the Attached picture.",
["/home/pi/ Visitor at your
door.jpg "] )
The image is attached as Visitor at your door.jpg and mailed to mdnasime@gmail.com.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518
555
In order to tweet from Raspberry Pi to notify the user about the visitor Twython needs to be installed on the Raspberry Pi. It’s a a Python module for interfacing with Twitter. A OAuth access token is needed, this gives application to access the us- ers twitter account.
By default, the app is set to read-only, so user won’t be able to publish tweets without changing that to Read and Write. Need to change from Settings tab and change the Application type.
Fig.8. Application type changed to read and write

Fig.9. Access token for the Application on Twitter
On the twitter app page the followings needs to be replaced by user’s token information
import sys
from twython import Twython
CONSUMER_KEY = From Token
CONSUMER_SECRET=FromToken
ACCESS_KEY = From Token
ACCESS_SECRET = From Token
api=Twython(CONSUMER_KEY,CONSUMER_SECRET,ACC ESS_KEY,ACCESS_SECRET)
In addition the user can also have the picture of the visitor instantly on twitter. The following needs to be followed in order to tweet picture from raspberry pi to twitter account. Here pygame libraries are used to take picture from the cam- era.
import pygame
import pygame.camera
from pygame.locals import *
pygame.init()
pygame.camera.init()
cam = pygame.camera.Camera("/dev/video0",(640,480))
cam.start()
image = cam.get_image()
pygame.image.save(image,' Visitor at your door.jpg')
Then to update this status in twitter :
photo = open('visitor at the door.jpg','rb')
api.update_status_with_media(media=photo, status='Door
Bell Alert!Someone is at your door')
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518

Figure 10. Hardware of the designed System
5. HARDWARE IMPLEMENTATION
Here the figure of the implemented hardware is given. All the components and connected according to the main circuit diagram. When the PIR sensor is interrupted then the Wi-Fi camera takes a snapshot and E-mail that attachment to the respective E-mail account and generates a tweet in the twitter to notify the authorized person about the visitor with picture. The user can then see the visitor either from web from anywhere in the world by Wi-Fi camera. If the user wants to give a message to the visitor, user just tweets in the twitter and the visitor can see the message on the screen on the front face of the door or the user can send command via twitter to open the door.
IJSER © 2013 http://www.ijser.org
556
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518
6. OUTPUT OF THE SYSTEM
557
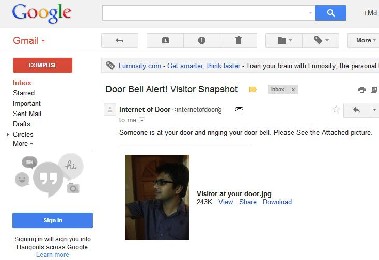
When the PIR sensor faces obsticles or detects human or the visitor rings the bell the camera takes a snapshot and send it via Email to the users account.
Figure 11. E-mail Received with Snapshot of the Visitor
An automatic tweet notification is generated in the twitter with picture of the visitor also. The user can choose wether to see the picture from the E-mail or Twitter
If the user wants to open the door for the visitor, user just needs to tweet from twitter and the command goes to raspberry and the door is opened
Figure 13. Confirmation from twitter
The user can commad to raspberry to close the door.

Fiure 14. Confirmation from twitter after closing the door
Figure 12. Visitor Alert from twitter
SER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 4, Issue 1ŗǰȱ -2013
ISSN 2229-5518
558
7. FURTHER APPLICATIONS
Internet of households where we can attach other devices of house with internet.
Industrial automation and control through internet.
Automated fire exit systems can be build
Improvement in the security issues in highly re- stricted areas
8. CONCLUSION
The system can be used in several places like banks, hospitals, labs and other sophisticated automated systems, which dramatically reduce the hazard of unauthorized entry. Evidence can be given to the security department if any robbery issue occurs. But the system needs to be monitor always that the internet bills are paid in due time to keep connected with own home.
9. REFERENCES
[1] Jae Hoon Lee ; Yong-Shik Kim ; Bong Keun Kim ; Ohba,K. ;Kawata,H. ; Ohya,A. ; Yuta,S. “Security Door System Using Human Tracking Method with Laser Range Finders” , IEEE- In- ternational Conference on Mechatronics and Automation 2007. ICMA
2007.
[2] YanboZhao ; ZhaohuiYe “A low cost GSM/GPRS based wireless home security system” IEEE Transactions on Consumer Electronics, (Vo- lume:54 , Issue: 2 )
[3] Hassan,H. ; Bakar,R.A. ; Mokhtar,A.T.F. ” “Face recognition based on auto-switching magnetic door lock system using microcontroller” IEEE-International Conference on System Engineering and Technology (ICSET), 2012
[4] Assaf, M.H. ; Mootoo, R. ; Das, S.R. ; Petriu, E.M. ; Groza, V. ;Biswas, S. “Sensor based home automation and security system” Instrumenta- tion and Measurement Technology Conference (I2MTC), 2012 IEEE In- ternational
[5] Ibrahim, R. ; Zin, Z.M. “Study of automated face recognition system for office door access control application” IEEE 3rd International Confe-
rence on Communication Software and Networks (ICCSN), 2011
[6] For figure.5 and information about PIR sensor http://www.glolab.com/pirparts/infrared.html
[7] For Figure.6 and information of PIR and lens http://www.ladyada.net/learn/sensors/pir.html
IJSER © 2013 http://www.ijser.org













