International Journal of Scientific & Engineering Research Volume 2, Issue 7, July-2011 1
ISSN 2229-5518
A Comparison of Data Dissemination
Protocols for Wireless Sensor Networks
Rakesh Kumar Yadav, Kusum Gupta, Ajay Singh Yadav
Abstract— Due to many constraints of nodes in wireless sensor networks, a variety of data dissemination protocols have been developed for data gathering in wireless sensor networks. Sensors extract useful information from environment; this information has to be routed through several intermediate nodes to reach the destination. Effective information dissemination is one of the most important tasks in sensor net- works. Directed Diffusion is a communication paradigm for information dissemination in W SNs based on data centric routing. In this paper we simulate three protocols using ns-2.33 simulator in terms of remaining energy and routing load.
Index Terms— W ireless Sensor Networks, Directed Diffusion, Data Centric, Routing, Energy, Efficiency, Ns-2
1 INTRODUCTION
—————————— • ——————————
IRELESS sensor network (WSNs) with limited computing and wireless communication capabili- ties becoming increasingly available for commer-
cial and military applications. The WSNs have the advan- tages of fault tolerance, easy deployment and accurate sensing, which can be applied in many fields, such as bat- tlefield surveillance, environment monitoring, industrial sensing and diagnostics, critical infrastructure protection and biological detection [1]. Once deployed, nodes in a WSN are stationary. In area of protocol design for WSNs there is extensive research going on. Communication in wireless sensor networks is data centric and must minim- ize the energy consumed by unattended battery-powered sensor nodes [2]. As a result of this many different data dissemination protocols have been proposed [2-8]. Each design is based on different assumptions and intuitions regarding the application scenarios of the network and its operational behavior. Each of the protocols aims to solve some of the challenges identified during the development process.
The routing protocols are classified into three groups:
flat routing protocols, hierarchical routing protocols and
location based routing protocols. Generally the flat routing protocols are suitable for small and mid-scale networks. The flat routing protocols are simple and robust. There is no hierarchy, nor additional power consumption for man- aging the clusters. While hierarchical routing protocols are complex and suitable for large scale networks. And loca- tion-based routing protocols, sensor nodes are addressed by means of their locations. The distance between neigh- boring nodes can be estimated on the basis of incoming
————————————————
• Rakesh Kumar Yadav is currently pursuing Ph.D degree program in Com- puter Science in Banasthali University, India,.E-mail: rky019@gmail.com
• Kusum Gupta is Aassociate Professor in computer science in Banasthali
University, Jaipur, India. E-mail: kusum.gupta@yahoo.com
• Ajay Singh Yadav is Assistant Professor in Mathematics Department in
SRM University,Ghaziabad, India E-mail: ajay290119842@gmail.com
signal strengths. [9].
In all above mentioned applications, the network con-
sists of tens to millions of tiny devices. Each device carries
one or more sensors and has limited signal processing and communication capabilities. Usually, the devices are po-
wered by batteries and can thus only operate for a limited time period. Key to implementing a network with such devices is that energy, computing power and communica- tion bandwidth. Therefore, lightweight, scalable, energy- conserving communication protocols are essential to the successful operation of the network. Fast deployment of such a network and robustness against device failures re- quire an ad-hoc network that is self-organizing. In general, radio communication (both transmitting and receiving) is generally the operation that consumes the most energy in a device. Conventional ad-hoc address oriented communi- cations protocols, such as IEEE 802.11 [10], generally con- sume too much energy or poorly support multi-hop net- works. In [11] and [12] the authors propose a new data centric approach for the dissemination of data in sensor networks. This paper concentrates on the comparison of three data dissemination protocols under a set of given scenarios: DD, OM and flooding protocols [2] [12].
The rest of the paper is organized as follows. A brief overview of the each protocol in this work is given in sec- tion II. Section III is devoted to an explanation of the simu- lation environment and metrics. The results are presents in section IV. Finally section V presents conclusion.
2 DATA DISSEMINATION PROTOCOLS FOR WSNS
2.1 Directed Diffusion
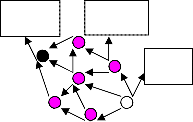
Directed Diffusion (DD), was proposes by Intanagonwi- wat et al. [2] [12], fgure 1 shows the operation of data cen- tric communication protocol for a WSN scenarios. Di- rected diffusion protocol based on query, where sink que- ries the sensors in an on-demand fashion by disseminat- ing an interest. Directed diffusion consists of three stages: interest propagation, initial gradient setup and data deli-
IJSER © 2011 http://www.ijser.org
International Journal of Scientific & Engineering Research Volume 2, Issue 7, July-2011 2
ISSN 2229-5518
very along reinforced path.
Source
Source
Interest
(a)
Gradient
Sink
first. Consequently, a path with maximum gradient is formed, so that in future received data packets can trans- mitted along best reinforced path. Finally the real data will send from the source, in selected path as shown in figure 1(c).
2.2 Omniscient Multicast
In the omniscient multicast scheme, each source transmits its events along a shortest path multicast tree to all sinks. Analysis of omniscient multicast, as well as do not ac- count for the cost of tree construction protocols. Rather centrally compute the distribution trees and do not assign energy costs to this computation. Omniscient multicast instead indicates the best possible performance achieva- ble in an IP-based sensor network without considering
Sink
overhead. Omniscient multicast is unrealistic as that it assumes all route information is available at no cost.

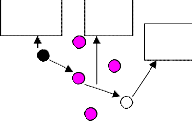
(b) Source Data
Sink
2.3 Flooding
In the flooding scheme, each sensor receiving a data packet broadcasts it to all of its neighbors and this process continues until the packet arrives at the destination or sources flood all events to every node in the network. Flooding is a contrary case for DD, if the DD does not perform better than Flooding. Flooding does, DD cannot be considered viable for sensor networks.
(c)
Fig.1. Directed Diffusion (a) Interest propagation (b) Initial gradient setup (c) Data delivery reinforced path
2.1.1 Interest Propagation
Sink node send out its query whenever it wants to obtain some information from sensor nodes. This query is car- ried by interest packet. The node which has received the interest packet can cache the packet temporarily and search for all of the matching target data as shown in fig- ure 1(a).
2.1.2 Initial Gradient Setup
3 SIMULATION METHODOLOGY
This section describes the simulation methodology and the performance metrics used for the comparison of data dissemination protocols.
3.1. Methodology
We have used Ns-2.33[13] for the simulation of protocols.. Each data dissemination protocol has used the same IEEE
802.11 MAC protocol. The same topology scenarios are used across different protocol simulations.
3.2. Simulation Parameters
Following simulation parameters are used in the simula- tion process.
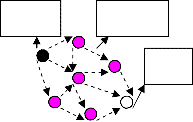
Using Gradient in directed diffusion, the data propaga- tion direction with minimum cost principle. Propagation of interest packets setup the gradient in the network for delivering data to the sink. Gradient is a reply link to a neighbor from which the interest was received as shown in figure 1(b).
2.1.3 Data Delivery Reinforced Path
Data propagation, source node sends data packets to sink node the initial setup gradient direction. Sink sends a reinforced packet to the neighbor node which is the first one receiving the target data. The neighbor node which receives the reinforced packet can also reinforce and se- lect the neighbor node which can receive the new data
IJSER © 2011 http://www.ijser.org
TABLE 1. SIMULATION PARAMETERS
International Journal of Scientific & Engineering Research Volume 2, Issue 7, July-2011 3
ISSN 2229-5518
3.3 Performance Metrics
Following metrics are used to evaluate and analyze the performance of data dissemination protocols.
3.1.1 Remaining Energy
The entire network remaining energy can indicate the lifetime of the sensor networks.
3.1.2 Routing Load
The ratio of the number of routing messages propagated by every node in the network and the number of data packets successfully delivered to all destination nodes. .
4 RESULTS
This section presents detailed simulation results for three data dissemination routing protocols, namely DD and two other traditional schemes namely Omniscient Multi- cast and Flooding protocols respectively.
4.1 Remaining Energy
Fig.4.1 presents the different changes of the entire net- work’s remaining energy with respect to simulation time
5 CONCLUSION
This paper presented the performance comparison of three routing protocols for wireless sensor networks namely: directed diffusion, omniscient multicast and flooding, results indicate that directed diffusion saves more energy than other two protocols in terms of remain- ing energy.
ACKNOWLEDGMENT
The authors would like to express sincere thanks to Dr. C.Rama Krishna (Associate Professor in CSE department NITTTR, Chandigarh) and Dr. R.P.Mahapatra, (Assistant Profesor in CSE Department SRM University, Modinagar) for support and valuable guidance.
REFERENCES
[1] I.F. Akyildiz, W. Su, Y. Sankarasubramaniam, and E.Cayirci, “W ireless Sensor Networks: A Survey,” Journal of Computer Networks 2002, vol.38, pp.393–422, 2002.
[2] C.Intanagonwiwat, R. Govindan and D. Estrin, “Directed diffu- sion: A scalable and robust communication paradigm for sen-
th
for DD, OM and Flooding protocols. It is shown that the
sor networks,” Proceeding of the 6
Annual ACM/IEEE Interna-
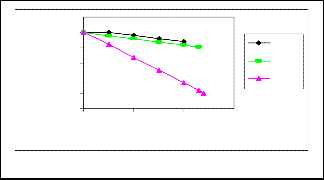
entire network remaining energy in DD is higher than other two protocols.
1001
1000
tional Conference on Mobile Computing and Networking (Mobi-
Com’2000), Boston, MA, pp.56-67, August 2000.
[3] F. Ye, H. Lou, J. Cheng, S. Lu and L. Zhang, “A two tier data
dissemination model for large-scale wireless sensor networks,” Proceeding of the ACM/IEEE MOBICOM, 2002, pp.148–159.
[4] S.Lu Fan Ye, G. Zhong and L. Zhang. “Gradient broadcast: A
robust data delivery protocol for large scale sensor networks”,.
999
998
997
996
995
0 10 20 30
Sim ulation Tim e(s ec)
Fig. 4.1. Time vs Remaining Energy
DD
OMNI FLOOD
In IPSN, Palo Alto, CA, USA, April 2003.
[5] W. Heinzelman, A. Chandrakasan. “Energy-efficient communi-
cation protocols for wireless sensor networks,”. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences (HICSS), Big Island, Hawaii, USA, pp. 3005–3014, Januaury 2000.
[6] W. Heinzelman, A. Chandrakasan. “Energy-efficient communi- cation protocols for wireless sensor networks,”. In Proceedings
of the 33rd Annual Hawaii International Conference on System Sciences (HICSS), Big Island, Hawaii, USA, pp. 3005–3014, Januaury 2000.
[7] L.Krishnamurthy, C.YihWan, A. Cambell. “A reliable transport
protocol for wireless sensors networks,”. In First Workshop on
4.2 Routing Load
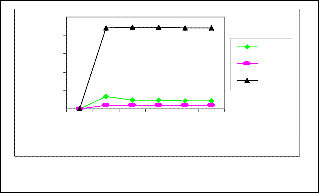
Figure 4.2 presents the routing load of the entire net- work with respect to simulation time for DD, OM and Flooding protocols.The entire network routing load in DD is higher than OM and lower than a Flooding protocol.
250
200
DD
150
OMNI
100
FLOOD
50
0
0 5 10 15 20 24
Simulation Time (sec)
Fig.4.2. Routing Load vs Simulation Time
Sensors Networks and Applications (W SNA), Atlanta, CA, USA, September 2002.
[8] A. Perrig, R. Szewczyck, V.Wen, D. Culler, and D.Tygar. “Spins: Security protocols for sensor networks,”. In Proceedings of the Seventh Annual International Conference on Mobile Computing and Networking (ACM MOBICOM ’01), pp. 189–199, Rome, Ita- ly, July 2001.
[9] N.Jamal, A.E.Kamal, “Routing Techniques in W ireless Sensor
Networks,” Proceeding of the W ireless Communications, IEEE
2004, vol.11, issues.6, pp.6-28, December 2004.
[10] LAN MAN Standards committee of the IEEE Computer Society,
IEEE Std 802.11-1999, W ireless LAN Medium Access Control
(MAC) and Physical Layer (PHY) specifications, IEEE,1999.
[11] J.Kulik, W. R. Heinzelman, and H. Balakrishnan, “Negotiation-
based protocols for disseminating information in wireless sen- sor networks,” Journal of W ireless Networks 2002, vol.8, pp.169-185, March 2002.
[12] C. Intanagonwiwat, R. Govindan, D. Estrin, J. Heidemann, F.Silva, "Directed Diffusion for W ireless Sensor Networking,” IEEE/ACM Transaction Networking 2003, vol.11, no.1, pp.2-16, February 2003.
[13] Network Simulator NS-2, http://www.isi.edu/nsnam/ns
IJSER © 2011 http://www.ijser.org




