The protocol implemented here is based on two password authentication between the tag and the reader.
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1150
ISSN 2229-5518
A survey on RFID Authentication with different protocols
Pushplata Sahu, Sadhna Mishra, Vineet Richariya
Abstract— Security is an important concept in the process of communicating data across network. Although there are many authentication protocols implemented for the security of message from the sender to the receiver. It is also necessary in various communication devices such as RFID where the data from the tag can be read be the reader wirelessly over network and stored in a server. Here we are implementing token based authentication protocol for the authentication of tag and the reader where the concept of secrete key generation is on the basis of tokens.
—————————— ——————————
An RFID system consists of three main components that enable it to operate and function properly, and those are: a reader, a set of tags, and a backend database or a server. The reader is a device that wirelessly queries the tags to identify them. RFID tags are simple and cheap devices that consist of small integrated circuits equipped with a radio antenna. These tags are given each a unique ID number and are mounted on all the objects that are intended to be identified [1].
Due to the benefits of the technology of RFID it is currently
employed in various commercial sectors to provide auto- mated assistance for mundane tasks. There are hospitals which have employed tagged bracelets to make sure that the maximum care is given to surgical patients. At various airports around the world, RFID is being utilized to track passengers’ bags to make sure that the position of the bags will be known at all times. Many of the pets contained RFID chips implanted to make sure of that, when it is get- ting lost, the authorities can find their owners’ information by simple searching the tag that are attached to the ob- jects. In so many cities and countries the RFID-enabled toll system designed for cars at RFID enabled toll booths which allow drivers to continue on their journey and avoid the ne- cessity of stopping to pay. Despite the advantages gained from RFID technology integration, various drawbacks pre- vent the wide-scale adoption into the majority of the com- mercial sector. There are three main issues concerning the integration of the architecture. The first issue is security when using the technology as tags are prone to various physical and virtual attacks upon the system. The second concern stems from the need of privacy surrounding the data collected as the observations recorded can be used for breaches in privacy. The third issue is that the data col- lected in various systems, generally in particular where passive tags are utilized, produces data characteristics that make the systems harder to use [2].
Before RFID can be utilized to its maximum potential, as opposed to the fraction in which it is presently in work defi-
nite issues need to be understood by the users, and cor- rected if possible. The three core obstacles include the concerns of security, the problems surrounding the privacy of the data captured and the characteristics associated with the nature of RFID. Additionally, we will further examine the specific problems associated with anomalies present within the captured observational records which are regarded as characteristics of RFID. When all of these issues are recti- fied to provide maximum security, privacy and integrity, RFID will be able to realize its full potential in massive wide-scale adoptions.
The issues associated with RFID Security, also known as Intrusion Detection, refer to the discovery of foreign attacks upon the system usually utilizing the tags that hinder the overall veracity of the data. There are various regarding the RFID, some of the most dominant with regard to RFID se- curity (et al., 2010; Thamilarasu & Sridhar, 2008):
• Eavesdropping: The data send from tag to the reader can’t be access from the external user.
• Unauthorized Tag Cloning: Copying tag data onto an addi- tional tag to gain the same privileges.
• Man-in-the-Middle (MIM) Attack: When an external object pretends to be either a tag or reader between actual tags and readers.
• Unauthorized Tag Disabling: When an external reader disables a tag not allowing it to be utilized again.
• Unauthorized Tag Manipulation: Manipulating the tag data using an external reader.
Privacy within the context of an RFID-enabled facility refers to either unknowingly releasing critical information (deriving specific knowledge or tracking meaningless data) (Langheinrich, 2009), and compile a list of all items current- ly found on a person (Juels, 2006). There have been sev- eral methodologies proposed in the past to ensure maxi- mum privacy of an individual, including the general ap-
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1151
ISSN 2229-5518
proaches of Encrypting/Rewriting and Hiding/Blocking Tags (Langheinrich, in 2009). According to the general solutions possible, there have been more specific and advanced ap- proaches suggested such as killing/sleeping the Tags, car- rying around a privacy-enforcing RFID device, releasing certain information based solely on distance from the read- er and introducing Government Legislations (Juels, 2006).
The protocols implemented for the authentication of the tag and the reader provides security of the data send from the tag to the reader. Although there are many security proto- cols implemented for the RFID authentication. A brief sur- vey is given in the papers.
Weis, Sarma, Rivest and Engels proposed in 2003 the use of hash-locks in RFID devices. A first approach, called De- terministic hash locks, was presented in. A tag is usually in a \locked" state until it is queried by a reader with a specific temporary meta-identifier Id. This is the result of hashing a random value (nonce) selected by the reader and stored into the tag. The reader stores the Id and the nonce in or- der to be able to interact with the tag. The reader can un- lock a tag by sending the nonce value. When a tag receives it, the value is checked [14].
Most of the security protocols implemented in RFID are based on cryptographic and hash functions. But these se- curity protocols are not much secure. The OSK protocol was proposed by Ohkubo, Suzuki and Kinoshita (OSK) in
2004 [8]. Its aim is to assure the valid answer of the tag even under an active attack. In this scheme each tag is ini- tialized with a secret value xi and two unidirectional func- tions h1 and h2. When a tag receives a request from a reader, it updates the value xi with the new value obtained from the computation of ht 1(xi) [7].
YA-TRAP (Yet-Another Trivial RFID Authentication Protocol) was proposed by Tsudik in 2006 [9]. This protocol describes a technique for the inexpensive untraceable identification of RFID tags. YA-TRAP involves minimal in- teraction between devices and a low computational load on the back-end server. With these features, this scheme is attractive for applications where the information is pro- cessed in data groups [7].
Weis, Sarma, Rivest and Engels proposed in 2003 [10] the use of hash-locks in RFID devices. A first ap- proach, called Deterministic hash locks, was presented in. A tag is usually in a \locked" state until it is queried by a reader with a specific temporary meta-identifier Id. This is the result of hashing a random value (nonce) selected by the reader and stored into the tag. The reader stores the Id and the nonce in order to be able to interact with the tag. The reader can unlock a tag by sending the nonce value. When a tag receives it, the value is checked [7].
In 2012, Dr.S.Suja proposed an RFID Authentica- tion protocol for security and privacy which is based on
Cyclic Redundancy Check (CRC) and Hamming Distance Calculation in order to achieve reader-to-tag authentication and the memory read command is used to achieve tag-to reader authentication. It will resist against tracing and clon- ing attacks in the most efficient way [5].
In 2011, Liangmin WANG, Xiaoluo YI, implies improved pro- tocol merely uses CRC and PRNG operations supported by Gen-2 that require very low communication and computa- tion loads. They also develop two methods based on BAN logic and AVISTA to prove the security of RFID protocol. BAN logic is used to give the proof of protocol correctness, and AVISTA is used to affirm the authentication and secre- cy properties [4].
In 2008, Tieyan Li analyze the security vulnerabili- ties of a family of ultra-lightweight RFID mutual authentica- tion protocols: LMAP, M2AP and EMAP [12]*, which are proposed by Peris-Lopez et al. Here they identify two suc- cessful attacks, such as de-synchronization attack and full discovery attack, against their protocols. The former per- manently disables the authentication capability of a RFID tag by destroying synchronization between the tag and the RFID reader [3].
The weakness of this authentication protocol comes from the fact that each round the adversary gets some information from the same key. So a quick way to counter our attack is to include a key-updating mechanism similar to OSK [13] at the end of the protocol using a one- way function. In this case, adversaries do not get more than P equations for each key so that the security proof and reduction to the SAT problem become sound. The resulting protocol is even forward-private providing that adversaries do not get side-channel information from the reader.
D. N. Duc, J Lee, and K. Kim. Enhancing security of EPCglobal gen-2 RFID tag against traceability and clone. In Symposium on Cryptography and Information Security — SCIS 2006, Hiroshima, Japan [6],
Hash-based Access Control (HAC), as defined by Weis et al. [11]*, is a scheme which involves locking a tag using a vone-way hash function. A locked tag uses the hash of a random key as its metaID. When locked, a tag responds to all queries with its metaID. However, the scheme allows a tag to be tracked because the same me- taID is used repeatedly [5].
In [8] Ohkubo, Suzki, and Kinoshita (OSK) pro- pose an RFID privacy protection scheme providing indistin- guishability and backward untraceability. This scheme uses a low-cost hash chain mechanism to update tag secret in- formation to provide these two security properties.
In August 2011 [] a new RFID verification procedure, calcu- lated for providing Strong Authentication and Strong Integri- ty. These protocols, suitable for passive Tags with limited computational control and storage space, involve simple bitwise operations such as or opaertion , exclusive or,
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1152
ISSN 2229-5518
modular totaling, and recurring shift operations.
SASI was explicitly proposed in [] as an improvement of the UMAP protocols, in order to provide authenticity and integ- rity and withstand all the possible attacks the UMAP proto- cols are subject to.
The SASI protocol is based on Strong Authentication and Strong Integrity of the data from the tag to the reader. Alt- hough this protocol and also many protocols are imple- mented for the authentication between the tag and the reader such as desynchronization attacks, identity disclo- sure attacks and many other attacks but in most of the pro- tocols only certain types of attacks have been removed and if any party can attack the server.
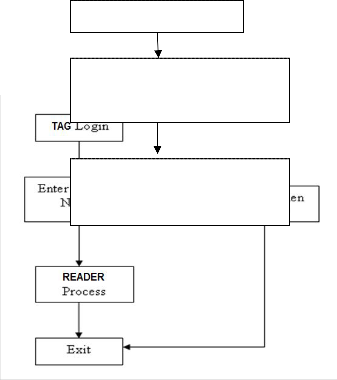
The protocol implemented here is based on two password authentication between the tag and the reader.
Tag Login
Reader
Token Number Generated using
SHA256 and BASE64 Algorithm
Step-1: New Tag account is created.
Step-2: Existing Tag is logged in by providing the identifica- tion of the Tag and entering the pin number.
Step-3: The token number is generated.
Step-4: The SHA256 algorithm is used for generating the
Hash message.
Step-5: This Hash message is taken and XOR operation is made.
Step-6: Then the XOR-ed message was encoded using
Base64 algorithm.
Step-7: From the encoded message a random six digit out- put is taken as token number.
Step-8: The generated token number is sent to the Tag and the server.
Step-9: With the help of the token number the Tag performs various operations like sending the data to the Reader over a secure channel.
In this paper a brief survey of the authentication techniques implemented for the security of RFID is given. Although there are many protocols implemented for the data security between tag and reader is given. A brief survey of these protocols is given along with the new technique of authenti- cation the tag and reader using tokens is proposed which is implemented in the future.
Figure 2.
Send the Generated Token Num- ber to the Tag and Server
en sis re- he ag r.
[1] Ramzi Bassil Wissam El-Beaino Ayman Kayssi Ali Chehab,” A PUF-Based Ultra-Lightweight Mutual- Authentication RFID Protocol”,2011.
[2] Peter Darcy, Prapassara Pupunwiwat and Bela Stantic,” The Challenges and Issues Facing the Deployment of RFID Tech”ology", 2010.
[3] security analysis on a family of ultra-lightweight rfid au- thentication protocols tieyan li, institute for infocomm re- search (i2r), 21 heng mui keng terrace, singapore 119613. [4] security improvement in authentication protocol for
generation based rfid system, liangmin wang, xiaoluo yi,
chao lv, yuanbo guo ,school of computer science and communication engineering, jiangsu university, zhenjiang
212013, china school of communication engineering, xidian
university, xi’an, 710071, china school of electronic technology, information engineering university of pla, zhengzhou, 450004, china doi:10.4156/jcit.vol6. issue1.18.
[5] an rfid authentication protocol for security and
As shown in the above figure is the authentication process between the tag and the reader.
privacy,dr.s.suja, m.e.,phd., associate professor, electrical and electronics engineering, coimbatore institute of technology, coimbatore. a. arivarasi, m.e, embedded and real time systems, coimbatore institute of technology, coimbatore.
IJSER © 2013 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1153
ISSN 2229-5518
[6] d. n. duc, j. park, h. lee, and k. kim. enhancing security of epcglobal gen-2 rfid tag against traceability and cloning. in symposium on cryptography and information security — scis 2006, hiroshima, japan, january 2006. the institute of electronics, information and communication engineers.
[7] a brief survey on rfid privacy and security j. aragones vilella_, a. martinez-ballest_e and a. solanas crises reserch
group unesco chair in data privacy dept. of computer
engineering and mathematics, rovira i virgili university.
[8] m. ohkubo, k. suzuki, and s. kinoshita. efficient hash chain based rfid privacy protection scheme. in international con- ference on ubiquitous computing - ubicomp, workshop privacy: current status and future directions, 2004.
[9] g. tsudik. ya-trap: yet another trivial rfid authentication protocol. in fourth annual ieee international conference on pervasive computing and communications work- shops (percomw'06), pages 640{643, 2006.
[10] weis, sarma, rivest and engels: a brief survey on rfid privacy and security. crises reserch groupunesco chair in data privacy,2003.
[11] boyeon song, chris j mitchell “rfid authentication protocol for low-cost tags” wisec’08, , alexandria, virginia, usa.copyright 2008 acm 978-1-59593-814-5/08/03 . march
31–april 2, 2008.
[12] tieyan li, guilin wang, robert h. deng,” security analysis on a family ofultra-lightweight rfid authentication protocols” journal of software, vol. 3, no. 3, march 2008.
[13] md. endadul hoque,” protecting privacy and ensuring security of rfid systems using private authentication protocols” marquette university, 2010.
[14] A Brief Survey on RFID Privacy and Security J. Arago- nes-Vilella_, A. Martinez-Ballest_e and A. Solanas CRISES Reserch Group UNESCO Chair in Data Privacy Dept. of Computer Engineering and Mathematics, Rovira I Virgili University.
IJSER © 2013 http://www.ijser.org