International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1182
ISSN 2229-5518
A Review of Routing Protocol In Manets
Cheenu Bala,Tania Nagpal
Abstract—In recent years, research has been seen going on in the field of Mobile Ad Hoc Networks (MANETs). Due to limited resources in MANETs, to design reliable and an efficient routing strategy is still open challenge. To overcome this problem a number of routing protocols have been developed and still increasing day by day. It is difficult to determine which protocols may perform well under different network scenarios such as topology and network size etc. In this paper we give an overview of the existing routing protocols with a particular focus on their characteristics and functionality. Further this study will help the researchers to get an overview of the existing protocols and suggest which protocols may perform better with respect to varying network scenarios.
Index Terms:-Manets, Proactive Protocol, Reactive Protocol, and Hybrid Protocol ,comparison of routing protocols, DSDV,AODV,ZRP.
—————————— ——————————
I. INTRODUCTION
In recent years the use of wireless technology has become increasing popular. The proliferation of communication devices and the innovation in wireless technology (e.g., cell phones, personal digital assistants,laptops, etc.) have modify the way of sharing information. A mobile adhoc network has mobile nodes that can communicate with other nodes through wireless links without any infrastructure. Infrastructure-less (ad hoc) networks they do not rely on any stationary infrastructure. The nodes in adhoc networks are mobile and can be connected dynamically in an arbitrary manner. The creation/deletion of nodes dynamically will leads to link breakage very fast and Nodes have to active at all the time either they are in the communication or not. Due to dynamic topology, nodes itself acts as a router as well as host. Mobile adhoc networks support dynamically changing topology, they are infrastructure less, they utilize multi hope routing, .Each node in networks takes part in discovery and maintenance of routes to other nodes
Fig 1: Example of MANET architecture
The rest of the paper is organized as follows: Section II presents routing in Mobile adhoc networks. Sections III, VI,V present the three categories of ad hoc routing protocols and
Section VI presents the overall comparison based on the
review presented. Finally Section VII concludes the paper
II. ROUTING IN MANETS
A Mobile Ad Hoc Network is an infrastructure less, self- organized and multi-hop network with rapidly changing topology causing the wireless links to be broken and re- established on-the-fly [1]. A key issue is the necessity that the Routing Protocol must be able to respond rapidly to the topological changes in the network. Major problems in routing are Dynamic Topology, Routing Overhead,Asymmetric links, and Interference. Routing in MANETs has been an active area of research and in recent years many protocols have been introduced for addressing the problems of routing, which are discussed in later sections. These protocols are divided into three categories– Reactive, Proactive and Hybrid. In Reactive or on- demand RPs the routes are created only when they are required. The application of this protocol can be seen in the Dynamic Source Routing Protocol (DSR) and the Ad-hoc On-demand Distance Vector Routing Protocol (AODV). Where in Proactive or Table-driven RPs the nodes keep updating their routing tables by sending messages. This can be seen in Optimized Link State Routing Protocol (OLSR) and Destination
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1183
ISSN 2229-5518
Sequenced Distance Vector Protocol (DSDV).Hybrid RPs aggregates a set of nodes into zones in the network.This can be seen in Zone Routing Protocol(ZRP),Zone Based Hierarchical Link State(ZHSL),Core Extraction Distributed adhoc Routing protocol( CEDAR)All these protocols are quite insecure because attackers can easily obtain information about the network topology [2].
Figure 2 gives categorization of the MANET routingprotocols.
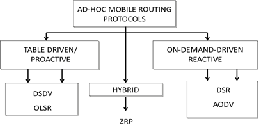
Fig 2 . Routing Protocols in MANETS
III. PROACTIVE (TABLE-DRIVEN )PROTOCOL
Proactive (Table-Driven):In pro-active routing protocols or Table-driven Routing Protocols the nodes keep updating their routing tables by sending messages. Some of the existing pro- active ad hoc routing protocols are: DSDV (Destination Sequenced Distance-Vector, 1994), WRP (Wireless Routing Protocol, 1996),OLSR(Optimized link State Protocol).
1) Destination-Sequenced Distance-Vector (DSDV) protocol The Table-driven DSDV protocol is a modified version of the Distributed Bellman-Ford (DBF) Algorithm that was used successfully in many dynamic packet switched networks [8]. In DSDV, each node is required to transmit a sequence number, which is periodically increased by two and transmitted along with any other routing update messages to all neighboring nodes. When a path becomes invalid,the node
that detected the broken link is required to inform the source,
which simply deletes the old path and searches for a new one for sending data. The advantages are loop-free path is guaranteed and latency for route discovery is low. The disadvantage is the large volume of control messages.
2) OLSR routing protocol
OLSR Clausen and Jacquet proposed the Optimized Link State Protocol, a point-to-point proactive protocol that employs an efficient link state packet forwarding mechanism called multipoint relaying [3,4]. It optimizes the pure link state routing protocol. Optimizations are done in two ways: by reducing the size of the control packets and by reducing the number of links used for forwarding the link state packets. Here each node maintains the topology information about the network by periodically exchanging link-state messages among the other nodes. OLSR is based on the following three mechanisms: neighbor sensing, efficient flooding and computation of an optimal route using the shortest-path algorithm. Neighbor sensing is the detection of changes in the neighborhood of node. Each node determines an optimal route to every known destination using this topology information and stores this information in a routing table. The shortest path algorithm is then applied for computing the optimal path.
3)Wireless Routing Protocol: The Wireless Routing Protocol, as proposed by Murthy and Garcia-Luna- Aceves [5], is a table-based protocol similar to DSDV that inherits the properties of Bellman-Ford Algorithm. The main goal is maintaining routing information among all nodes in the network regarding the shortest distance to every destination. Wireless routing protocols (WRP) is a loop free routing protocol. Each node in the network uses a set of four tables to maintain more accurate information: Distance table (DT), Routing table (RT), Link-cost table (LCT), Message retransmission list (MRL)
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1184
ISSN 2229-5518
table. TABLE 1 shows the comparison of some of the existing proactive routing protocols.
TABLE 1
COMPARISON OF PROACTIVE ROUTING PROTOCOLS
Parameters | DSDV | WRP | OLSR |
Route Update | Periodic | Periodic | Periodic |
Loop Free | Yes | Yes | Yes |
Routing overhead | High | High | Low |
Caching overhead | Medium | High | High |
Throughput | Low | Low | Medium |
Routing Table | 2 | 4 | 4 |
IV. REACTIVE PROTOCOL
Reactive (Source-Initiated On-Demand Driven):
These protocols try to overcome the conventional routing tables and consequently reduce the need for updating these tables to track changes in the network topology. Some of the existing re-active routing protocols are.DSR (Dynamic Source Routing, 1996), SSR (Signal Stability Routing, 1997), TORA (Temporally-Ordered Routing Algorithm, 1997),and AODV (ad hoc On- Demand Distance Vector Routing, 1999).
1) Ad Hoc On-demand Distance Vector Routing (AODV)
protocol:
The Ad Hoc On-demand Distance Vector Routing (AODV) protocol is a reactive unicast routing protocol for MANETs . In AODV, when a source wants to send packets to the destination but there no route is available, it starts a route discovery process. In the route discovery process, source broadcasts route request (RREQ) packets which includes
Destination Sequence Number. If a node or the destination node that has a route to the destination receives the RREQ, node will check the destination sequence numbers that it currently knows. To guarantee the freshness of the routing information, a route reply (RREP) packet is created and forwarded back to the source only if the destination sequence number is equal to or greater than the one specified in RREQ. The redundant packets will be discarded. The advantage of this protocol is low Connection setup delay and the disadvantage is more number of control overheads due to many route reply messages for single route request.
2) Dynamic Source Routing (DSR) Protocol
The Dynamic Source Routing (DSR) is a reactive unicast routing protocol which utilizes source routing algorithm . There are two phases in DSR such as:
• Route discovery
• Route maintenance
When a source node wants to send a packet, First of all it consults its route cache . If the route is available, then source node sends the packet . Otherwise, the source node initiates a route discovery process by broadcasting RREQ. On receiving RREQ, a node will checks its route cache and If the node doesn’t have information for the requested destination, it attached its own address to the route record field of the request packet.Then,the RREQ packet is forwarded to its neighbors. If the request packet reaches the destination or an intermediate node has routing information to the destination, then RREP packet is generated. Else, the RREP packet comprises the addresses of nodes the route request packet has traversed concatenated with the route in the intermediate node’s route cache.
Whenever the data link layer detects a link failure, a RRER
packet is sent backward to the source in order to maintain the route information. So that, all routes containing the broken link should be removed from the route caches of the
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1185
ISSN 2229-5518
immediate nodes when the ROUTE_ERROR packet is transmitted to the source node. The advantage of DSR protocol is reduction of route discovery control overheads with the use of route cache and the disadvantage is the increasing size of packet header with route length due to source routing.
3)Temporally-Ordered Routing Algorithm (TORA):TORA was developed by Park and Corson. Temporarily ordered routing algorithm (TORA) is, loop-free, distributed, highly adaptive
routing algorithm based on the concept of link reversal. It uses directed acyclic graphs (DAG) to define the routes either as downstream or upstream.This graph enables TORA to provide better route aid for networks with dense, large population of nodes [6]. However to provide this feature TORA needs synchronization of the nodes which limits the application of the protocol. TORA is a complicated protocol but what makes it unique and prominent is its main feature of propagation of control messages only around the point of failure when a link failure occurs. This feature allows TORA to scale up to larger networks but has higher overhead for smaller networks. TORA involves four functions: creating, maintaining, erasing and optimizing routes. TABLE 2 shows the comparison of some of the existing reactive routing protocols.
TABLE 2: COMPARISON OF REACTIVE ROUTING PROTOCOLS
V. HYBRID PROTOCOL
Hybrid Protocols: Hybrid routing protocols aggregates a set of nodes into zones in the network. Then, the network is partitioned into zones and proactive approach is used within each zone .While routing of packets between different zones, the reactive approach is used. In hybrid schemes, a route to a destination which is in the same zone is established without any delay, but a route discovery and a route maintenance procedure is required for destinations that are in different zones. So, the hybrid approach is an appropriate approach for routing in a huge network.
1). Zone Routing Protocol (ZRP): Haas and Pearlman proposed Zone Routing Protocol. ZRP [7] is a hybrid routing protocol for mobile ad hoc networks which localizes the nodes into sub-networks (zones). ZRP protocol inherits the merits of on- demand reactive and table driven proactive routing protocols. The inter-zone communication uses reactive (on- demand) routing to reduce unnecessary communication. Within each sub-networks, proactive(table driven) routing is adapted to speed up communication among neighbors. The network is divided into routing zones according to their distances between mobile nodes. An important issue of zone routing is to find the size of the zone. Additionally, some
local route optimization is performed at each node, which
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1186
ISSN 2229-5518
includes the following actions: removal of redundant routes, shortening of routes, detecting of link failures.
2). Zone Based Hierarchical link state(ZHLS): ZHLS is based on hierarchical structure in which the network is divided into non-overlapping zones. According to Joa and Lu [8], each node is assigned one unique node ID and a Zone ID, Which are calculated using geographical information. Hence the network follows a two-level topology structure: zone level and node level.There are two types of link state updates: the node level LSP(Link State Packet) and the Zone level LSP. A node level LSP have the node IDs of its neighbors in the same zone and the zone IDs of all zones. A node send its node level LSP to all remaining nodes in the same zone. So, by periodic node level LSP interchanges, all nodes in same zone keep similar node level link state information. Before transmission the source node will first checks its intra-zone routing table. If the destination lies in its zone, the routing information is already present. Otherwise, the source sends a location request to all other zones through gateway nodes, which in turn replies with a location response containing the zone ID of the desired destination.
3). Distributed Spanning tree(DST): The nodes in the network are grouped into many trees [10]. Every tree has two types of nodes; internal node and route node. The root controls the tree structure, whether the tree can merge with another tree, and remaining nodes of every tree are the regular nodes. Each node of the tree can be in one of three different states; router, merge and configure depending on the type of task that it trying to perform. DST defines two methods to determine a route between a source and a destination:
Hybrid Tree Flooding (HTF): In this scheme, the source sends the control packets to all the neighbors and adjoining bridges in the spanning tree. Each packet is remained static at these places for a specific holding time.
Distributed Spanning Tree (DST) shuttling: In this scheme, the source sends the control packets to the tree edges till each of them reaches a leaf node. When a packet reaches the leaf node, it is forwarded to a shuttling level. The drawback with such architecture is the existence of a single point of failure for the entire tree. If the root node fails, the entire routing structure falls apart. TABLE 3 shows the comparison of some of the existing hybrid routing protocols.
TABLE 3: COMPARISON OF HYBRID ROUTING PROTOCOLS
Parameters | ZRP | ZHLS | DST |
Routing Structure | Flat | Hierarchi cal | Hierarchic al |
Multiple Route | No | No | No |
Route Informatio n Stored in | Intrazone & Interzone | Intrazone & Interzone | Route table |
Route Metric | Shortest Path | Shortest Path | Forwardin g using the tree neighbors |
Advantage | Reduced Transmissi on | Low Control Overhead | Reduced Transmissi on |
Disadvanta ge | Overlappi ng Zone | Static Zone map required | Root node |
VII. COMPARISON OF PROTOCOLS
In this section we have presented a comparison between existing routing protocols. TABLE 4 below provides an overall comparison of the three categories of routing protocols. The comparisons basically consider the characteristic properties of routing protocols in high load
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1187
ISSN 2229-5518
networks. To make flat addressing more efficient, the routing overheads introduced in the networks must be reduced. Hybrid routing protocols employ both reactive and proactive properties by maintaining intra-zone information proactively and inter-zone information reactively. Another way to reduce routing overheads is by using conditional updates rather than periodic ones. In Reactive routing protocols, such as AODV and DSR will also have scalability problems. Hybrid routing protocols such as the ZHLS may also perform well in large networks. ZRP is another hybrid routing protocol which is designed to increase the scalability of MANETs.It maintains strong network connectivity (proactively) within the routing zones while determining remote route (outside the routing zone) quicker than flooding.
TABLE 4: COMPARISON BETWEEN THE THREE CATEGORIES OF ROUTING PROTOCOLS
VIII. CONCLUSION
In this paper, we have presented and discussed the taxonomy of routing protocols in mobile ad hoc networks and provided comparisons between them. For each of these classes, we reviewed and compared several representative protocols. While there are still many challenges facing Mobile ad hoc networks related to routing and security. Each routing protocol has unique features. Based on network environments, we have to choose the suitable routing protocol. The important differentiating factor between the protocols is the ways of finding and maintaining the routes between source destination pairs. The comparison we have presented between the routing protocols indicates that the design of a secure ad hoc routing protocol constitutes a challenging research problem against the existing security solutions. We hope that the taxonomy presented in this paper
will be helpful and provide researchers a platform for
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1188
ISSN 2229-5518
choosing the right protocol for their work. At last we have provided the overall characteristic features of all routing protocols and described which protocols may perform best in large networks. Still mobile ad hoc networks have posed a great challenge for the researchers due to changing topology and security attacks, and none of the protocols is fully secured and research is going on around the globe.
ACKNOWLEDGEMENT
The authors wish to thank the reviewers and editors for their valuable suggestions and expert comments that help improve the contents of paper.
REFERENCES .
[1] A. K. Gupta and H. Sadawarti, “Secure Routing Techniques for MANETs,” “International Journal of Computer Theory and Engineering”, vol. 1 no. 4, pp. 456-460, October 2009.
[2] Y. Hu, A. Perrig and D. Johnson, Ariadne: A Secure On- demand Routing Protocol for Ad Hoc Networks, “in Proceedings of ACM MOBICOM’02”, 2002.
[3] L. Abusalah, A. Khokhar and M. Guizani, “A Survey of Secure Mobile Ad Hoc Routing Protocols”, “IEEE Communications Surveys & Tutorials”, vol. 10 no. 4, 4th Quarter 2008.
[4] T. Clausen, P. Jacquet, A. Laouiti, P. Muhlethaler, A. Qayyum, L.Viennot, “Optimized link state routing protocol for ad hoc networks,” in: “Proceedings of IEEE INMIC”, December 2001, pp. 62–68.
[5] S. Murthy and J. J. Garcia-Luna-Aceves, “An Efficient Routing Protocol for Wireless Networks,” “ACM Mobile Networks and App. J., Special Issue on Routing in Mobile
Communication Networks”, Oct. 1996, pp. 183–97.
[6] A. K. Gupta, H. Sadawarti, and A. K. Verma, “Performance analysis of AODV, DSR & TORA Routing Protocols,” “IACSIT International Journal of Engineering and Technology”, vol.2, vo.2, April 2010.
[7] Z. J. Haas and M. R. Pearlman, .ZRP: a hybrid framework for routing in ad hoc networks, pp. 221.253, 2001.
[8] M. Joa-Ng, I.-T. Lu, “A peer-to-peer zone-based two-level link state routing for mobile ad hoc networks,” “IEEE Journal on Selected Areas in Communications 17 (8) (1999) 1415–
1425”. [17] R. Sivakumar, P. Sinha, and V. Bharghavan, “CEDAR: a Core- Extraction Distributed Ad hoc Routing algorithm,” “IEEE Journal on Selected Areas in Communications”, vol 17, no 8, August 1999.
[9] A. K. Gupta and H. Sadawarti,and Anil K.verma “Review of various Routing Protocols for MANETs,” “International Journal of information and Electronics Engineering”, vol. 1 no. 3, Nov 2011.
[10] S. Radhakrishnan, N. Rao, G. Racherla, C. Sekharan, and S. Batsell, “DST – a routing protocol for ad hoc networks using distributed spanning trees,” in: “Proceedings of IEEE WCNC”, September 1999, pp. 100–104.
IJSER © 2015 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 6, Issue 2, February-2015 1189
ISSN 2229-5518
IJSER © 2015 http://www.ijser.org

