International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1674
ISSN 2229-5518
A Novel Framework for Mitigating the DDoS
attacks
Upma Goyal1, Gayatri Bhatti2, Prabhdeep Singh3
123Computer Science Department, Punjab Technical University Kapurthala, Jalandhar, India. upmagoyal.pit789@gmail.com, Gayatribhatti.pit@gmail.com, ssingh.prabhdeep@gmail.com
Abstract— Distributed Denial of Service (DDoS) attacks are a destructive, relatively new type of attack on the availability of Internet services and resources, andamong the hardest security problems. Over the past few years, DDOS attacks have increased up to a large extent. As a result of which we need to fight against the severe effects of these attacks. In this paper, we will discuss different types of DDOS attacks, the way they affect the networks and the appropriate defence mechanisms for them. Also, a solution is proposed to mitigate these attacks which work in four steps including detection of DDOS attacks, diverting the attack traffic for treatment, monitori ng and filtering the attack traffic and finally forwarding the good traffic to the final destination.
Index Terms— Attacks,Defence, DDoS, DoS, Filtering, Mitigation,Traffic.
—————————— ——————————
1 INTRODUCTION
As the vast Internet is growing on a fast pace, its vul- nerabilities and weaknesses are achieving a faster pace. This gave rise to a flame of viruses, worms, website de- facement, and many attacks and so on. Anyone can take advantages of such vulnerabilities which results in deg- radation of the network. These severe attacks have led to the rise of various defense mechanisms. Since security refers to secrecy, integrity, authentication and non- repudiation, any proposed defense mechanism should be able to provide all these four features. But the attacks like DoS and DDoS have overpowered these security mecha- nisms, there by loading so much of attack traffic on the system. So following are discussed some of the types of DDoS attacks along with the effects they cause on the system and the defense mechanism proposed for them. sentence use the author names instead of “Reference [3],” e.g., “Smith and Smith [3] show ... .” Please note that references will be formatted by IJSER production staff in the same order provided by the author.
2 DIFFERENT TYPES OF DDOS ATTACKS AND THE
CONSEQUENCES
2.1 Bandwidth Attack
These attacks[1] have become a major security issue now days which led to the downfall of very high profile websites such as Microsoft, Yahoo resulting in a huge financial loss[2]. Bandwidth attack shuts off the services by throwing a huge amount of useless traffic there by resulting in the consumption of large number of host’s resources, network bandwidth, memory etc.
2.2 Typical DDoS Attack
It is one of the known types of DDoS attacks [1]. In this attack, the attacker installs all the relevant tools which leads to the advancement of the attack into all the sys- tems and turns those computers or systems into “zom-
bies”.
2.3 Reflector Attack
Reflector attack is one of the most serious type of DDoS attacks. Here, what happens is, the attacker goes for the help of a third party. This third party can be a per- son, system or a victim. The attacker will send the attack traffic to the third party and the third party will further bounce the attack traffic towards the target[1,2].
2.4 Protocol Attack
Since various networks involve the functionalities of various protocols such as TCP/IP [2,12] protocol, the vulnerabilities or weaknesses can reside in these proto- cols also. The attacker taking advantages of these vulner- abilities sends the attack traffic towards the target there by causing memory and resources loss[4].
2.5 SYN FLOOD Attack
Similar to the above mentioned protocol attack, this attack also exploits the vulnerabilities of TCP/IP[2,12] protocol performs a three way handshake as well[3]. In this handshake, large number of acknowledgements ac- cumulates to generate a high volume of harmful attack traffic. This traffic is then forwarded to the target sys- tem[5,6].
2.6 UDP FLOOD Attack
This type of attack occurs when the victim is unable to distinguish between the legitimate and illegitimate pack- et flows moving at a high sending rate. Since UDP has no flow control mechanisms, due to which the traffic results in congestion at the receiver end[5].
2.7 ICMP FLOOD Attack
It is a type of bandwidth attack which uses ICMP
packets. Here, the packet is directed to an individual ma-
IJSER © 2013
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1675
ISSN 2229-5518
chine which is then broadcast to the entire network re- sulting in the degraded network status[5,6].
3 SURVEY OF DDOS ATTACKS
The first most DoS attack was carried out by David Dennis, a thirteen year old student at University High School in 1974. In late 1990s, Internet Relay Chat (IRC) was very popular which caused IRC chat floods[7,11] there by forcing all the users within a channel to logout and they gain the access. In August 1999, a tool named Trinoo[8] was used to disable the University’s computer network for over two days which resulted in the first large scale DDoS attacks[9,10]. During February 2000, the most well-known websites[10, 11] including Yahoo, CNN, and Amazon came down due to these attacks. In
2002, another disastrous DDoS threat came into notice
which targeted all the thirteen Internet’s root domain
name service (DNS) servers. In 2003, the DDoS attacks
took hold on the web sites like Clickbank and Spamcop.
In 2004, Qatar-based Al-Jazeera News was took down by
DDoS attacks. In 2007-2008, DDoS attacks were used as a
part of cyber wars against Estonia and Georgia by Russia.
In 2009, many heavy DDoS attacks targeted South Kore-
an, Iranian Government and American web sites. In the
same year, Facebook, Twitter, Google were also targeted
by such attacks. In year 2010, some Anonymous, using
DDoS attacks took down the Operations Payback.in year
2011-2012, Hacktivists targeted Operation Tunishia, Op-
eration Sony, Operation Russia, Operation India, Opera-
tion Japan etc. using such attacks[13,14,15].
Over these years, it has also been surveyed that the
largest targets of the DDoS attacks are customers. Net-
work infrastructure and service infrastructure are also
influenced by these attacks. So here, a fig. 1 is drawn in
order to illustrate the target of DDoS attacks.
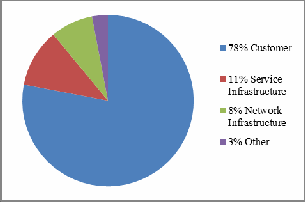
Fig 1.Victim of DDoS Attacks
Following TABLE I list some more kinds of DDoS at-
tacks along with the penalties they cause and the defense
procedures for them.
TABLE I
DDoS ATTACKS, THEIR EFFECTS AND DEFENSE
MECHANISMS
IJSER © 2013
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1676
ISSN 2229-5518
| | handshake | |
7. | Ping of death | Sends mul- tiple mal- formed or malicious pings to a computer. | Add checks for each incoming IP fragment telling whether the packet is invalid or valid. |
8. | Slowloris | Enables one web server to take down another server with- out affecting target net- work | Increasing the clients, limiting the connec- tions, restricting the length of time of a client. |
9. | Zero-Day DDOS | New attacks exploiting vulnerabili- ties of the computer | Using single packet authorization, keeping up-to-date software, white listing allowing good applications to access the system. |
10. | Amplification attack | Attacker makes a request that generates a larger re- sponse | Using high perfor- mance OS, load bal- ancer, limiting the connection, limiting the connection rate. |
11. | APT(Advanced Persistent Threat) | Powerful entity intents to gain ac- cess to a specific target such as political group or government | Using McAfee, which allows only the instal- lation or execution of important programs. |
12. | Booter Shell Scripts | Makes diffi- cult to dis- tinguish between legitimate and illegiti- mate traffic | Continues testing of web applications and known vulnerabilities in commercial applica- tions. |
IJSER © 2013
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1677
ISSN 2229-5518
19. | Infrastructure DDOS attack | Overloads the network infrastruc- ture by con- suming large amount of bandwidth | First Line of Defense provides corero’s DDS tool to inspect, detect and protect the infra- structure attacks. |
20. | Layer 3 and layer 4 DDOS attacks | Attackers send high flood of data to slow down the web server perfor- mance, degrades the access for legitimate users, con- sume band- width | Begin the application transactions, limit the rate of transaction. |
21. | Layer 7 DDOS attacks | Overloads the specific elements of an applica- tion server infrastruc- ture | Apache, shows the message request time out and IIS, limit the size of the request to each requirement. |
22. | Public Exploit | Released to the public via standard channels like mailing lists, exploit archives, mainly through JAVA | Either unplug JAVA from your browser or uninstall it from your computer completely. |
23. | TCP Flag Abuse Flood | Emerged from out of state re- quests or TCP mes- sages with odd combi- nations or modifica- tions to the | Install patches to guard against these attacks which will limit the ability of an intrud- er to take advantage of these attacks. |
IJSER © 2013
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1678
ISSN 2229-5518
is coming from a collection of systems i.e. distributed systems.
Any defense mechanism should be designed by keeping in view the following principles.
1. The defence mechanism should be followed at every
stage of the entire network.
2. The defence procedure should preserve the legitimate traffic as much as possible there by preventing the damage.
3. Defence method should facilitate a complete, secure
and authenticated communication channel.
4. A defence method should take care of the scalability
issues as per further requirements in the future.
5. A defence mechanism should not only detect but mit- igate the attack as well.
4 SOLUTION PROPOSED FOR DDOS MITIGATION
In order to mitigate the DDoS attacks this paper has proposed the following defense scenario which involves the four steps. These are as follows:
1. The Detection of DDoS attack.
2. Sending the attack traffic first for the treatment and not to the target.
3. Monitoring and filtering the illegitimate packets from the legitimate packets there by allowing the legitimate traffic to complete the transactions and preventing the illegitimate traffic.
4. Forwarding the good traffic to the target or the re- ceiver end.
This mechanism will provide complete protection not only against the known DDoS attack but those that have never been examined before also. This defense architec- ture will deliver an immediate response to DDoS which will be measured in seconds and not hours. This mecha- nism will be throwing light on two components:
1. The Detector
2. The Guard
Following fig 2, is a flowchart depicting all the above mentioned steps in order to specify how each and every phase of this defense mechanism works.
All, the above listed defense procedures along with their respective attacks are able to mitigate the DoS at- tacks up to some extent. But when it comes to DDoS at- tacks i.e. Distributed Denial of Service attacks, these de- fense mechanisms fail to cop up. This is because now the attack traffic is not coming from a single source; instead it
IJSER © 2013
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1679
ISSN 2229-5518
Detec-
Detecting the
DDOS attacks
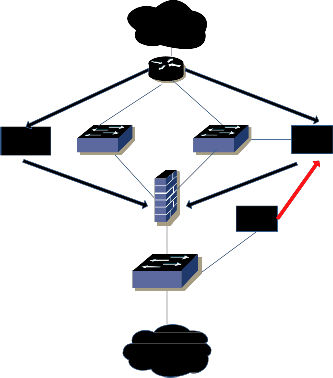
The fig. 3 shows how detector and guard detect and mit- igates the attack.
Int ernet
Diverting the data traffic to an appliance for treatment
Rout er
Guard Guard
Guard
Swit ch Swit ch
Analyzing and filtering the bad data packets
Firewall
Det ect or
Alert
Guard
Swit ch
Forwarding the good data pack- ets to the target
Int ernal Net work
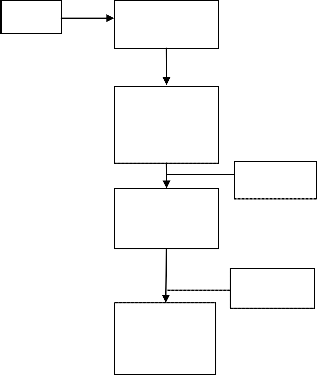
Fig. 2 Flowchart for Solution Set against DDoS Attacks
The components, Detector and Guard by working hand in hand will ensure a complete DDoS protection against all type of DDoS attack. A brief description of these compo- nents is given below.
4.1 Detector
This component will give a complete analysis of com- plex DDoS attack. It will examine the network traffic. If any misbehavior or deviation from the normal behavior is found in the traffic, it will immediately indicate a DDoS attack. After the attack’s indication, the detector alerts the guards, the other component, to quickly react to the at- tack.
4.2 Guard
It is a DDoS mitigation device deployed upstream at the data center which gives a high performance output. When the guard is indicated of the attack, the malicious traffic which was to be forwarded to the target is diverted to the guard and is subjected to a five stage analysis to separate the legitimate and the illegitimate packets. The guard provides instant protection without causing any impact on the data traffic flow of other systems.
Fig. 3 Modified Architecture for DDoS Mitigation
The five steps purification of the malicious traffic is as follows:
4.3 Purification Process
4.3.1 Filtering
Static and dynamic DDoS filters for the purpose of filtering of malicious traffic. To block the non-essential traffic from reaching the victim, static filters are used. In order to have real time updates of suspicious flows or block sources, dynamic filters are used. Dynamic filters are deployed by other modules on the basis of complete analysis of traffic flows and behaviour.
4.3.2 Anti-Spoofing
This process helps to check that packets entering the system are not spoofed. The guard mentioned above, uses a numerous authentication procedures to stop the spoofed packets from reaching the victim. This module also verifies the proper identification of the good traffic there by removing the risk of good packets being dis- carded.
4.3.3 Anomaly Recognition
IJSER © 2013
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1680
ISSN 2229-5518
This stage of the purification process monitors all the traffic which is not stopped by filtering and anti-spoofing module. It will again check the normal behaviour of the packets which was recorded again and again over time. If any deviation from the normal behaviour is found, it will detect the malicious packet.
4.3.4 Protocol Analysis
This phase manages the flows of the traffic which were found suspicious in the above phase in order to identify attacks like HTTP-Error attacks. This phase also prevents any sort of misbehaviour in the protocol transactions.
4.3.5 Rate Limiting
This part of the purification procedure stops the mali- cious flows from increasing the rate with which they are heading towards the target.
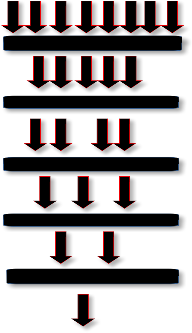
The following fig. 4 shows how malicious attack traffic is purified through above steps.
P acket Filt ering
Ant i-Spoofing
Anomaly Recognit ion
P rot ocol Analysis
Rat e Limit ing
Fig 4. Purification Architecture for Malicious Traffic
5 CONCLUSIONS
The Distributed Denial-of-Service attacks have led to the decline of numerous web sites and networks there by resulting in the proposition of different defense mecha- nisms. Therefore, this paper had proposed a four step solution to defeat the DDoS attacks. These four steps in- cluded the detection and deviation of the attack traffic by the Detector, first for the treatment instead to the target, then the traffic is sent to the Guard for further sending it
for filtering and finally forwarding the legitimate traffic to the target.
ACKNOWLGMENT
Foremost, we Upma Goyal and Gayatri Bhatti would like to express our sincere gratitude to our Head of the Department, Mr Rajdeep Singh and our guide Mr Prabhdeep Singh for their continuous support, their patience, motivation, immense knowledge and their complete guidance for this research paper.
REFERENCES
[1] C. Douligeris and A. Mitrokotsa, “DDoS attacks and defense mechanisms: Classification and state-of-the-art,” Computer Networks: the Int. J. Computer and Telecommunications Networking, Vol. 44, No. 5, April 2004, pp. 643–666.
[2] J. Mirkovic, S. Dietrich, D. Dittrich, and P. Reiher, “Internet Denial of Service: Attack and Defense Mechanisms,” Prentice Hall PTR, December 2004.
[3] A. Sperotto, G. Schaffrath, R. Sadre, C.Morariu, A. Pras and B.
Stiller, ”An Overview of IP Flow-Based Intrusion Detection,” IEEE Communications Surveys & Tutorials, Vol. 12, No. 3, Third Quarter 2010.
[4] M. Sung and J. Xu, “IP Traceback-Based Intelligent Packet Filtering: A Novel Technique for Defending against Internet DDoS Attacks,” IEEE Transactions on Parallel and Distributed Systems, Vol. 14, No. 9, September 2003.
[5] R. K. C. Chang, “Defending against Flooding-Based Distributed Denial-of-Service Attacks: A Tutorial,” IEEE Communications Magazine, pp. 42-51, October 2002.
[6] J. Jung, B. Krishnamurthy, and M. Rabinovich, “Flash crowds and denial of service attacks: Characterization and implica- tions for cdns and web sites,” in Proceedings of the Interna- tional World Wide Web Conference, May 2002, pp. 252–262.
[7] S. Tanachaiwiwat and K. Hwang, “Differential packet filtering against DDoS flood attacks,” ACM Conference on Computer and Communications Security (CCS), Washington, DC, Octo- ber 2003.
[8] C. Douligeris and A. Mitrokotsa, “DDoS attacks and defense mechanisms: Classification and state-of-the-art,” Computer Networks: the Int. J. Computer and Telecommunications Networking, Vol. 44, No. 5, pp. 643–666, April 2004.
[9] M. Robinson, J. Mirkovic, M. Schnaider, S Michel, and P. Rei-
her, “Challenges and principles of DDoS defense,” SIGCOMM
2003.
[10] B. Bencsath and I. Vajda, “Protection against DDoS attacks based on traffic level measurements,” Western Simulation MultiConference, San Diego, California, USA, January 2004.
IJSER © 2013
http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 4, Issue 4, April-2013 1681
ISSN 2229-5518
[11] N. Noureldien, “Protecting web servers from DoS/DDoS flooding attacks: a technical overview,” International Confe r- ence on Web-Management for International Organisations. Geneva, October 2002.
[12] G.Bhatti, R.Singh and P.Singh, “A look back at Issues in the layers of TCP/IP Model,” International Journal of Enhanced Research in Management & Computer Applications, Vol. 1, Is-
sue 2, November 2012.
[13] Y. He, T. Liu, and Q. Cao, “A survey of low-rate denial-of-service
attacks,” Journal of Frontiers of Computer Science & Technology,
2008.
[14] T. Peng, C. Leckie, and K. Ramamohanarao, “Survey of Network- Based Defense Mechanisms Countering the DoS and DDoS Prob- lems,” ACM Computing Surveys 39.
[15] K. Hoffman, D. Zage, and C. Nita-Rotaru, “A survey of attack and defense techniques for reputation systems,” ACM Computing Sur- vey 42, 2010.
IJSER © 2013
http://www.ijser.org



