—————————— ——————————
International Journal of Scientific & Engineering Research, Volume 4, Issue 12, December-2013
ISSN 2229-5518
A New Mobile Application for Encrypting
SMS / Multimedia Messages on Android
Hazem M. El bakry, Ali E. Taki_El_Deen, Ahmed Hussein Ali El tengy
Abstract— Mobile communication devices have become popular tools for communicating among people. This paper is a launcher for sending/receiving secured SMS/Multimedia files using Blowfish algorithm. A smart mobile application on android platform is introduced as an application that helps the user to encrypt the message (SMS/Multimedia files) before it is transmitted over the mobile network. The new idea of the program is to transmit encrypted messages and multimedia files or any other type of files via mobile networks or the internet as an alternative mean. Utilizing the internet takes place through a secured hosting website with a user name and password integrated in the program. To maintain intensive security, a private key encrypts the files and another private key encrypts file name. The transferring media is maintained online in the absence of mobile network coverage.
Index Terms— Mobile Communication Devices, Secure SMS, Cryptography, SMS Encryption, MMS Encryption, File Encryption, Blowfish.

—————————— ——————————
300
Mmonplace during the past few years, integrating multi- ple wireless networking technologies to support addi-
tional functionality and services. One of the most important developments that have emerged from communications tech-
No En- cryption
for Mobile communicationsI(GSM)J[3]. Banks wSorldwide are ER
using SMS to conduct some of their banking services [4]. For
example, clients are able to query their bank balances via SMS
or conduct mobile payments. In addition, people sometimes
exchange confidential information such as passwords or sensi- tive data amongst each other [5]. SMS technology suffers from
some risks such as vulnerabilities, eavesdroppers and unau- thorized access [6].Therefore, we need to secure SMS messages and keep their contents private, without increasing their size. This paper provides a solution to this SMS security problem. Our approach is to secure the SMS/Multimedia message using an encryption (Blowfish) system [7]. The proposed technique encrypts SMS with 16-round Feistel cipher and uses large key- dependent S-boxes.
Section 2 Gives an overview of Short Message Service (SMS) Section 3 Provides some details of Blowfish algorithm Section 4 Simulation of program screens
Section 5 Conclusion.
No De- cryption
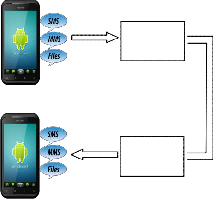
Fig.1 Send SMS/MMS/Files via network normally
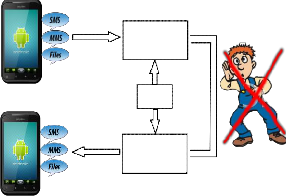
Figure (1) shows the normal way to send text messages or multimedia files over mobile phone networks, which exposes them to eavesdropping operations and overhearing of infor- mation.
Blowfish
Encrytion
Key
————————————————
Hazem M. El bakry is currently pursuing Mansoura University, Egypt, E- mail: Helbakry5@yahoo.com
Blowfish
Decrypion
Fig.2 Send SMS/MMS/Files via network with Encryption
Figure (2) the method proposed here is to encrypt the data before sending it over the mobile phone networks, whenever is the encrypted data among the transmission channel is vul- nerable. Hence, the receiver can attain authenticated data after decrypting it.
IJSER © 2013
International Journal of Scientific & Engineering Research Volume 4, Issue 11, November-2013
ISSN 2229-5518
![]()
SMS is a communication service standardized in the GSM mo- bile communication systems [8]. It can be sent and received simultaneously with GSM voice, data and fax calls. This is possible because whereas voice, data and fax calls take over a
dedicated radio channel for the duration of the call, short mes- P1
sages travel over and above the radio channel using the signal-
ling path [9].
SMS contains some meta-data [10]:
Information about the senders (Service center number,
sender number). F
Protocol information (Protocol identifier, Data coding
scheme).
Timestamp.
301
An encryption algorithm [11] plays an important role in secur- ing the data while storing or transferring it. The encryption algorithms are categorized into Symmetric (secret) and Asymmetric (public) keys encryption [12].
14 more rounds
P16
IJSER
only one key is used for both encryption and decryption of
data. For example Data encryption standard (DES), Triple
DES, Advanced Encryption Standard (AES) and Blowfish En- cryption Algorithm [13].
Blowfish [15] is a 64-bit cipher and its key length extended from 32 bits to 448 bits, it has 16 rounds and uses large key- dependent S-boxes.
F
P18 P17
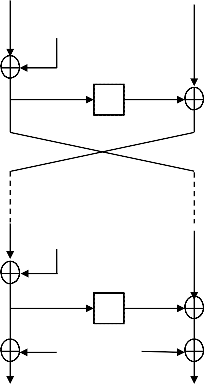
Fig.4 F-function Blowfish
The diagram [19] in figure (4) shows Blowfish's F-function. It follows the Feistel network .This algorithm is divided into two parts.
Key is converted from 448 bits to several sub-key arrays to- taling 4168 bytes. The keys are generated before data encryp-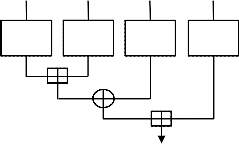
8 bits
S-box
1
32 bits
8 bits
S-box
2
32 bits
8 bits
S-box
3
32 bits
8 bits
S-box
4
32 bits
tion or decryption.
The p-array consists of 18, 32-bit sub-keys:
P1, P2,………….......P18
Four 32-bit S-Boxes consist of 256 entries each: S1, 0, S1, 1,……….. S1, 255
S2, 0, S2, 1,……….. S2, 255
S3, 0, S3, 1,……….. S3, 255
S4, 0, S4, 1,……….. S4, 255
In total, 521 iterations are required to generate all required
sub-keys [21].
Fig.3 Substitution box of Blowfish
The diagram [16] in figure (3) shows a Function that uses four arrays S1,..., S4 derived from the encryption key. Each array contains 32-bit words. The arrays act as substitution boxes or S-boxes [17], replacing an 8-bit input with a 32-bit output. F splits its 32-bit input into four 8-bit bytes. It replaces each byte by the contents of an S-box, and combines the results as fol- lows [18]:
In this function, there are 16 rounds. Each round consists of a key-dependent permutation and a key and data-dependent substitution. All operations are XORs and additions on 32-bit words. The only additional operations are four indexed array data lookup tables for each round [23].
IJSER © 2013
International Journal of Scientific & Engineering Research Volume 4, Issue 11, November-2013
ISSN 2229-5518
302
the "Encrypt" button, the result cipher text displayed in third textbox.
Decryption cipher text by inserting private key into first textbox, when pressing "Get Inbox SMS" button then the pro- gram opens the SMS inbox of the smart phone and picking out the income cipher message, it returns in the second textbox, when pressing the "Decrypt" button the result decrypted text message displayed in the third textbox.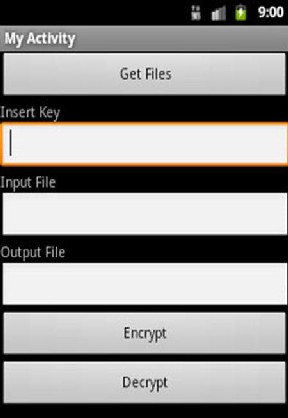
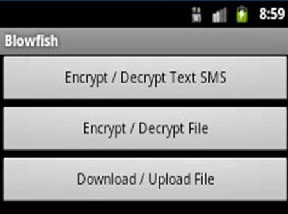
Fig.5 First screen of Blowfish program
Figure (5) shows the first screen in the application which has three buttons, the first button is used for encrypting and de- crypting text messages, the second one is for encrypting and decrypting all files types on the mobile, the third is used for uploading or download files via Internet.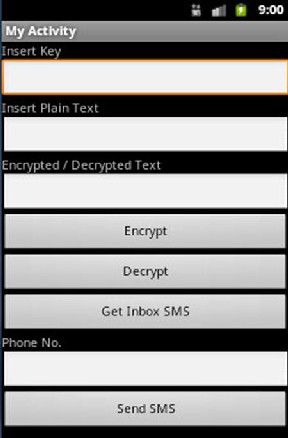
IJSER
Fig.7 Main screen of encrypt/decrypt File
Fig.6 Main screen of encrypt/decrypt SMS
Figure (7) shows how to encrypt or decrypt multimedia or any type of files.
Encrypting files by inserting private key in the first textbox then when pressing the "Get Files" button, the program ex- plores the mobile phone files and picks the file, its name and path returns in the second textbox, when pressing the "En- crypt" button, the encryption process starts, then the encrypt- ed file name and path will be displayed in the third textbox.
Decrypting files by inserting private key into first textbox then when pressing the "Get Files" button, the program ex- plore the mobile phone files and picks the encrypted file, its name and path returns in the second textbox, when pressing the "Decrypt" button, the decryption process starts, then the decrypted file name and path will be displayed in the third textbox.
Figure (6) shows how to encrypt or decrypt text messages. Encrypting text by inserting private key into first textbox
then the message inserted to second textbox, when pressing
IJSER © 2013
International Journal of Scientific & Engineering Research Volume 4, Issue 11, November-2013
ISSN 2229-5518
303
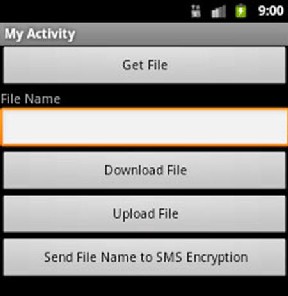
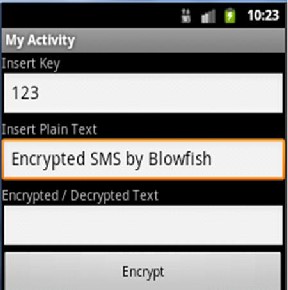
Fig.8 Alternative way to upload/download encrypted file Fig.9 Input text
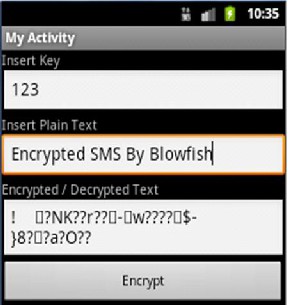
Figure (8) shows alternative way to upload/download files to a secured website with a username and password within the program to maintain more security so that the user has nothing to do with this information.
Uploading encrypted files: by pressing the "Get File" but- ton, the program explores the mobile phone files and picks the file, its name and path returns in the first textbox, then when pressing the "Upload File", the program uploads the file to a secured website on the internet. When uploading completed, a notification message appears.
For high strength in the complexity of encryption, press the "Send File Name to SMS Encryption" button, as a result of that the program sends only the file name without path to the SMS encrypting screen to encrypt then send it.
Downloading encrypted files: by opening the "Main screen of encrypt/decrypt SMS" window, pressing the "Get Inbox SMS" button, choosing the message including the encrypted file name, pressing the "decrypt" button to decrypt the file name, copying this file name to the clipboard, then switching back to the "Upload/download" screen, pasting the file name in the first textbox. By pressing the "Download File" button, the pro-
gram will download the file from the secured website on the
internet, and then when downloading process is completed, a confirming message appears.
Sample of encrypting plain text to cipher text
Example:
Figure (9) shows input text "Encrypted SMS by Blowfish" and private key "123"
Fig.10 Output of cipher text
Figure (10) shows Cipher text as a result by pressing the "En- crypt" button, the result appears in the third text box.
In this paper, the importance of encrypting data in practical life is discussed, as the number of intruders, and spying at- tempts on private messages have recently been increased. Thus, it is mandatory to think of new ways to overcome this problem as designing a program with a simple user interface that encodes, by certain code keys, the text messages, image, voice, video files, and sends them via mobile networks. Two ways have been considered to send a message from one mo-
IJSER © 2013
International Journal of Scientific & Engineering Research Volume 4, Issue 11, November-2013
ISSN 2229-5518
304
bile to another; the first, the program sends messages via GSM networks as text messages or multi-media ones, the second, by connecting the mobile to internet through the mobile network or a wireless internet network, where the program uploads the files to a specific file hosting site that requires a user name and a pass word already created and hidden, to maintain more security, in the program. The receiver using the same program will be able to download the files. It is clear that alternative communicating means are considered to overcome weakness or losing mobile network signals and shifting to internet con- nections, for instance.
[1] Chin, E., Felt, A. P., Greenwood, K., and Wagner, D. "Analyzing Inter-Application Communication in Android". In Proc. of the Annu- al International Conference on Mobile Systems, Applications, and Services (2011).
[2] Marko Hassinen, "SafeSMS - End-to-End Encryption for SMS Mes- sages", IEEE International Conference on Telecommunications, 2008, 359-
365.
[3] S. Jahan, M. M. Hussain,M. R.Amin and S. H. Shah Newaz, "A Pro- posal for Enhancing the Security System of Short Message Service in GSM", IEEE International Conference on Anti-counterfeiting Security and Identification, 2008, 235-240.
using extended MSA method: DJSSA symmetric key algorithm", Jounal of Computing, Vol 3, issue-2, Page 66-71, Feb(2011).
[15] Trisha Chatterjee, Tamodeep Das, Joyshree Nath, Shayan Dey and Asoke Nath, "Symmetric key cryptosystem using combined crypto- graphic algorithms- generalized modified vernam cipher method, MSA method and NJJSAA method: TTJSA algorithm", Proceedings of IEEE International conference: World Congress WICT-2011 t held at Mumbai University 11-14 Dec, 2011, Page 1179-1184(2011).
[16] Somdip Dey, Asoke Nath, "Modern Encryption Standard (MES) Ver- sion-I: An Advanced Cryptographic Method", Proceedings of IEEE
2nd World Congress on Information and Communication Technolo- gies (WICT- 2012), pp. 242-247.
[17] Dripto Chatterjee, Joyshree Nath, Sankar Das, Shalabh Agarwal and Asoke Nath, "Symmetric key Cryptography using modified DJSSA symmetric key algorithm", Proceedings of International conference Worldcomp 2011 held at LasVegas 18-21 July 2011, Page-306-311, Vol
1(2011).
[18] E. Barker and A. Roginsky, "Recommendation for the Transitioning of Cryptographic Algorithms and Key Sizes", NIST SP 800-131, 2010, Technical Report.
[19] Somdip Dey, Joyshree Nath, Asoke Nath, "An Integrated Symmetric Key Cryptographic Method - Amalgamation of TTJSA Algorithm, Advanced Caeser Cipher Algorithm, Bit Rotation and reversal Meth- od : SJA Algorithm", International Journal of Modern Education and Computer Science (IJMECS), ISSN: 2075- 0161 (Print), ISSN: 2075-
017X (Online), Vol 4, No 5, Page 1- 9, 2012.
IJSER
[4] Mary Agoyi and Devrim Seral, "SMS Security: An Asymmetric En-
cryption Approach", IEEE International Conference on Wireless and Mo- bile Communications, 2010, 448-452.
[5] P. Traynor, W. Enck, P. McDaniel and T. La Porta. "Mitigating At- tacks on Open Functionality in SMS-Capable Cellular Networks", IEEE/ACM Transactions on In Networking, 17(1):40-53, 2009.
[6] Mary Agoyi, Devrim Seral, "SMS Security: An Asymmetric Encryp- tion Approach", Sixth International Conference on Wireless and Mo- bile Communications, 2010 IEEE, pp 448-452.
[7] Ferguson, N., Schneier, B. and Kohno, "Cryptography Engineering:
Design Principles and Practical Applications", T. Indianapolis: Wiley
Publishing, Inc. 2010.
[8] Roland Schloglhofer, "Secure and Usable Authentication on Mobile
Devices", MoMM2012, 3-5 December, 2012, Bali, Indonesia. ACM
978-1-4503-1307-0/12/12 (pp 257-262).
[9] M. Toorani and A. A. Behesti, "SSMS – A Secure SMS Messaging Protocol for the M-Payment Systems", IEEE Symposium on Comput- ers and Communications, 2012, 700-705.
[10] Marko Hassinen, "SafeSMS- End-to-End Encrption for SMS Messag- es", IEEE International Conference on Telecommunications, 2008,
359-365.
[11] Kuo-Tsang Huang, Jung-Hui Chiu, and Sung-Shiou Shen, "A Novel Structure with Dynamic Operation Mode for Symmetric-Key Block Ciphers". International Journal of Network Security & Its Applica- tions (IJNSA) 5 (1): 19, (January 2013).
[12] Mary Agoyi and Devrim Seral, "SMS Security: An Asymmetric En- cyrption Approach", IEEE International Conference on Wireless and Mobile Communication, 2010, 448-452.
[13] Jawahar Thakur and Nagesh Kumar, "DES, AES and Blowfish: Sym- metric Key Cryptography Algorithms Simulation Based Performance Analysis", International Journal of Emerging Technology and Ad- vanced Engineering, (ISSN 2250-2459, Volume 1, Issue 2, December
2011)
[14] Dripto Chatterjee, Joyshree Nath, Soumitra Mondal, Suvadeep Das- gupta and Asoke Nath, " Advanced Symmetric key Cryptography
[20] Debanjan Das, Joyshree Nath, Megholova Mukherjee, Neha
Chaudhury and Asoke Nath, "An Integrated symmetric key cryptog- raphy algorithm using generalized vernam cipher method and DJSA method: DJMNA symmetric key algorithm", Proceedings of IEEE In- ternational conference: World Congress WICT-2011 to be held at Mumbai University 11-14 Dec, 2011, Page 1203-1208(2011).
[21] Jiao Wentao, "Cloud computing environments cryptographic applica- tions", Chinese Association for Cryptologic Research, vol. 5, no. 1, pp.20-29, 2011.
[22] Satyaki Roy, Navajit Maitra, Joyshree Nath, Shalabh Agarwal and
Asoke Nath, "Ultra Encryption Standard(UES) Version-I: Symmetric Key Cryptosystem using generalized modified Vernam Cipher method, Permutation method and Columnar Transposition method", Proceedings of IEEE sponsored National Conference on Recent Ad- vances in Communication, Control and Computing Technology- RACCCT 2012, 29-30 March held at Surat, Page 81- 88(2012).
[23] Asoke Nath, Saima Ghosh, Meheboob Alam Mallik, "Symmetric Key Cryptography using Random Key generator", Proceedings of Inter- national conference on security and management (SAM'10) held at Las Vegas, USA Jull 12-15, 2010, Vol 2, Page: 239-244(2010).
IJSER © 2013